Application of Neural Network on PLC-Based Automation Systems for Better Fault Tolerance and Error Detection
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Neural Networks
AIAI andand thethe NetNet •• Buyer’sBuyer’s GuideGuide 19.1 Where Intelligent Technology Meets the Real World www.pcai.com IntelligentIntelligent Applications Applications TThehe ModernModern RoboticRobotic Also:Also: “Movement”“Movement” Agents, Business Applications, TThehe StateState ofof AIAI Today:Today: TheThe Business Intelligence, WWeb:eb: AI’sAI’s NewNew PlaygroundPlayground Computational Intelligence, Data Analysis & Mining, Robotics:Robotics: RobotsRobots ThatThat Intelligent Applications, Intelligent Tools, MimicMimic AnimalsAnimals Intelligent Tutoring, Intelligent Web Searching, TThehe NationalNational ScienceScience Neural Networks, Foundation:Foundation: EncouragingEncouraging Robotics, tthehe ResearchersResearchers ofof Speech Recognition, TTomorrowomorrow Web Based Expert Systems, Plus:Plus: AIAI andand thethe Net,Net, Training, Bookzone,Bookzone, Buyer’sBuyer’s Guide,Guide, AI Conferences, ProductProduct UUpdatespdates and more! PC AI 2 19.1 Quantities Limited Buy PC AI Back Issues 1995 1999 A Great Resource 9 #1 Intelligent Tools 13 #1 Intelligent Tools & Languages 9 #2 Fuzzy Logic / Neural Networks (Knowledge Verification) for AI Research 9 #3 Object Oriented Development 13 #2 Rule and Object Oriented 9 #4 Knowledge-Based Systems Development (Data Mining) $8.00/Issue - US 9 #5 AI Languages 13 #3 Neural Nets & Fuzzy Logic (For Us and Canadian and 9 #6 Business Applications (Searching) Foreign Postage 13 #4 Knowledge-Based Systems contact PC AI or visit the 1996 (Fuzzy Logic) 10 #1 Intelligent Applications PC AI web site) 13 #5 Data Mining (Simulation and 10 #2 Object Oriented Development Modeling) Order online at 10 #3 Neural Networks / Fuzzy Logic 13 #6 Business Applications www.pcai.com 10 #4 Knowledge-Based Systems (Machine Learning) Total amount enclosed 10 #5 Genetic Algorithm & Modeling 10 #6 Business Applications 2000 $____________. -

Artificial Neural Networks
ARTIFICIAL NEURAL NETWORKS: A REVIEW OF TRAINING TOOLS Darío Baptista, Fernando Morgado-Dias Madeira Interactive Technologies Institute and Centro de Competências de Ciências Exactas e da Engenharia, Universidade da Madeira Campus da Penteada, 9000-039 Funchal, Madeira, Portugal. Tel:+351 291-705150/1, Fax: +351 291-705199 Abstract: Artificial Neural Networks became a common solution for a wide variety of problems in many fields. The most frequent solution for its implementation consists of building and training the Artificial Neural Network within a computer. For implementing a network in an efficient way, the user can access a large choice of software solutions either commercial or prototypes. Choosing the most convenient solution for the application according to the network architecture, training algorithm, operating system and price can be a complex task. This paper helps the Artificial Neural Network user by providing a large list of solution available and explaining their characteristics and terms of use. The paper is confined to reporting the software products that have been developed for Artificial Neural Networks. The features considered important for this kind of software to have in order to accommodate its users effectively are specified. The development of software that implements Artificial Neural is a rapidly growing field driven by strong research interests as well as urgent practical, economical and social needs. Copyright CONTROLO2012 Keywords: Artificial Neural Networks, Training Tools, Training Algorithms, Software. 1. INTRODUCTION commercialization of new ANN tools. With the purpose to inform which tools are available at present Nowadays, in different areas, it is important to and make the choice of which tool to use, this paper analyse nonlinear data to do prediction, classification contains the description of software that has been or to build models. -

Comparativa De Tecnologías De Deep Learning
Universidad Carlos III de Madrid Departamento de Informática Proyecto Final de Carrera Comparativa de Tecnologías de Deep Learning Author: Alberto Lozano Benjumea Supervisors: Alejandro Baldominos Gómez Ignacio Navarro Martín Leganés.Septiembre de 2017 Alberto Lozano Benjumea Universidad Carlos III de Madrid Avenida de la Universidad, 30 28911 Leganés, Madrid (Spain) Email: [email protected] “Just because it’s not nice doesn’t mean it’s not miraculous” Terry Pratchett This page has been intentionally left blank. Abstract Este proyecto se localiza en la rama de aprendizaje automático del campo de la in- teligencia artificial. El objetivo del mismo es realizar una comparativa de los diferentes frameworks y bibliotecas existentes en el mercado, a día de la realización del presente documento, sobre aprendizaje profundo. Esta comparativa, pretende compararlos us- ando diferentes métricas y una batería heterogénea de pruebas. Adicionalmente se realizará un detallado estudio del arte indicando las técnicas sobre las que sustentan dichas bibliotecas. Se indicarán con ejemplos cómo usar cada una de estas técnicas, las ventajas e inconvenientes de las mismas y sus relaciones. Keywords: aprendizaje profundo, aprendizaje automático frameworks, comparativa v This page has been intentionally left blank. Agradecimientos Probablemente se podría escribir la mitad del documento con agradecimientos a las personas que han influido en que este documento pueda existir. Podría partir de mi abuelo quién me enseñó la informática y lo que se podía lograr con el Amstrad y de ahí hasta el día de hoy, a familia, compañeros, amigos que te influyen, incluso las personas que influyen negativamente, con los que ves que que camino no debes escoger. -

The Nnlib2 Library and Nnlib2rcpp R Package for Implementing Neural Networks
The nnlib2 library and nnlib2Rcpp R package for implementing neural networks Vasilis N Nikolaidis1 1 University of Peloponnese DOI: 10.21105/joss.02876 Software • Review Summary • Repository • Archive Artificial Neural Networks (ANN or NN) are computing models used in various data-driven applications. Such systems typically consist of a large number of processing elements (or Editor: Kakia Chatsiou nodes), usually organized in layers, which exchange data via weighted connections. An ever- increasing number of different neural network models have been proposed and used. Among Reviewers: the several factors differentiating each model are the network topology, the processing and • @schnorr training methods in nodes and connections, and the sequences utilized for transferring data • @MohmedSoudy to, within and from the model etc. The software presented here is a C++ library of classes and templates for implementing neural network components and models and an R package Submitted: 22 October 2020 that allows users to instantiate and use such components from the R programming language. Published: 23 May 2021 License Authors of papers retain copyright and release the work Statement of need under a Creative Commons Attribution 4.0 International A significant number of capable, flexible, high performance tools for NN are available today, License (CC BY 4.0). including frameworks such as Tensorflow (Abadi et al., 2016) and Torch (Collobert et al., 2011), and related high level APIs including Keras (Chollet & others, 2015) and PyTorch (Paszke et al., 2019). Ready-to-use NN models are also provided by various machine learning platforms such as H2O (H2O.ai, 2020) or libraries, SNNS (Zell et al., 1994) and FANN (Nissen, 2003). -

Neural Network FAQ, Part 1 of 7
Neural Network FAQ, part 1 of 7: Introduction Archive-name: ai-faq/neural-nets/part1 Last-modified: 2002-05-17 URL: ftp://ftp.sas.com/pub/neural/FAQ.html Maintainer: [email protected] (Warren S. Sarle) Copyright 1997, 1998, 1999, 2000, 2001, 2002 by Warren S. Sarle, Cary, NC, USA. --------------------------------------------------------------- Additions, corrections, or improvements are always welcome. Anybody who is willing to contribute any information, please email me; if it is relevant, I will incorporate it. The monthly posting departs around the 28th of every month. --------------------------------------------------------------- This is the first of seven parts of a monthly posting to the Usenet newsgroup comp.ai.neural-nets (as well as comp.answers and news.answers, where it should be findable at any time). Its purpose is to provide basic information for individuals who are new to the field of neural networks or who are just beginning to read this group. It will help to avoid lengthy discussion of questions that often arise for beginners. SO, PLEASE, SEARCH THIS POSTING FIRST IF YOU HAVE A QUESTION and DON'T POST ANSWERS TO FAQs: POINT THE ASKER TO THIS POSTING The latest version of the FAQ is available as a hypertext document, readable by any WWW (World Wide Web) browser such as Netscape, under the URL: ftp://ftp.sas.com/pub/neural/FAQ.html. If you are reading the version of the FAQ posted in comp.ai.neural-nets, be sure to view it with a monospace font such as Courier. If you view it with a proportional font, tables and formulas will be mangled. -
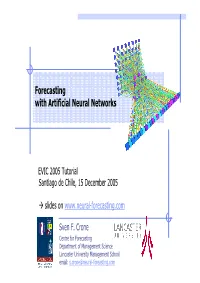
Forecasting with Artificial Neural Networks
Forecasting with Artificial Neural Networks EVIC 2005 Tutorial Santiago de Chile, 15 December 2005 Æ slides on www.neural-forecasting.com Sven F. Crone Centre for Forecasting Department of Management Science Lancaster University Management School email: [email protected] EVIC’05 © Sven F. Crone - www.bis-lab.com Lancaster University Management School? EVIC’05 © Sven F. Crone - www.bis-lab.com What you can expect from this session … Simple back propagation algorithm [Rumelhart et al. 1982] ∂C(t pj ,o pj ) E p = C(t pj , o pj ) o pj = f j (net pj ) Δ p w ji ∝ − ∂w ji ∂C(t ,o ) ∂C(t ,o ) ∂net pj pj = pj pj pj ∂w ji ∂net pj ∂w ji ∂C(t ,o ) Æ „How to …“ on Neural δ = − pj pj pj ∂net pj Network Forecasting ∂C(t ,o ) ∂C(t ,o ) ∂o δ = − pj pj = pj pj pj pj with limited maths! ∂net pj ∂opj ∂net pj ∂o pt ' = f j (net pj ) ∂net pj ∂C(t pj ,opj ) ' δ pj = f j (net pj ) Æ CD-Start-Up Kit for ∂o pj ∂ w o ∂C(t ,o ) ∂net ∂C(t ,o ) ∑ ki pi Neural Net Forecasting pj pj pk = pj pj i ∑ ∂net ∂o ∑ ∂net ∂o k pk pj k pk pj Æ 20+ software simulators ∂C(t pj ,opj ) = ∑ wkj = − ∑δ pj wkj k ∂net pk k Æ datasets ' δ pj = f j (net pj )∑δ pj wkj Æ literature & faq k ⎧∂C(t pj ,opj ) ' ⎪ f j (net pj ) if unit j is in the output layer ⎪ ∂opj Æ slides, data & additional info on δ pj = ⎨ ⎪ ' f j (net pj )∑δ pk wpjk if unit j is in a hidden layer www.neural-forecasting.com ⎩⎪ k EVIC’05 © Sven F. -

Uhm Ms 3812 R.Pdf
UNIVERSITY OF HAWAI'I LIBRARY ADVANCED MARINE VEIDCLE PRODUCTS DATABASE -A PRELIMINARY DESIGN TOOL A THESIS SUBMITTED TO THE GRADUATE DMSION OF THE UNIVERSITY OF HAWAI'I IN PARTIAL FULFILLMENT OF THE REQUIREMENTS FOR THE DEGREE OF MASTER OF SCIENCE IN OCEAN ENGINEERING AUGUST 2003 By Kristen A.L.G. Woo Thesis Committee: Kwok Fai Cheung, ChaiIperson Hans-Jurgen Krock John C. Wiltshire ACKNOWLEDGEMENT I would like to thank my advisor Prof. Kwok Fai Cheung and the other committee members Prof. Hans-Jiirgen Krock and Dr. John Wiltshire for the time and effort they spent with me on this project. I would also like to thank the MHPCC staff, in particular, Mr. Scott Splean for their advice and comments on the advanced-marine-vehicle products database. Thanks are also due to Drs. Woei-Min Lin and JUll Li of SAIC for their advice on the neural network and preliminary ship design tools. I would also like to thank Mr. Yann Douyere for his help with MatLab. The work described in this thesis is a subset of the project "Environment for Design of Advanced Marine Vehicles and Operations Research" supported by the Office of Naval Research, Grant No. NOOOI4-02-1-0903. iii ABSTRACT The term advanced marine vehicle encompasses a broad category of ship designs typically referring to multihull ships such as catamarans, trimarans and SWATH (small waterplane area twin hull) ships, but also includes hovercrafts, SES (surface effect ships), hydrofoils, and advanced monohulls. This study develops an early stage design tool for advanced marine vehicles that provides principal particulars and additional parameters such as fuel capacity and propulsive power based on input ship requirements. -

Machine Learning
1 LANDSCAPE ANALYSIS MACHINE LEARNING Ville Tenhunen, Elisa Cauhé, Andrea Manzi, Diego Scardaci, Enol Fernández del Authors Castillo, Technology Machine learning Last update 17.12.2020 Status Final version This work by EGI Foundation is licensed under a Creative Commons Attribution 4.0 International License This template is based on work, which was released under a Creative Commons 4.0 Attribution License (CC BY 4.0). It is part of the FitSM Standard family for lightweight IT service management, freely available at www.fitsm.eu. 2 DOCUMENT LOG Issue Date Comment Author init() 8.9.2020 Initialization of the document VT The second 16.9.2020 Content to the most of chapters VT, AM, EC version Version for 6.10.2020 Content to the chapter 3, 7 and 8 VT, EC discussions Chapter 2 titles 8.10.2020 Chapter 2 titles and Acumos added VT and bit more to the frameworks Towards first full 16.11.2020 Almost every chapter has edited VT version First full version 17.11.2020 All chapters reviewed and edited VT Addition 19.11.2020 Added Mahout and H2O VT Fixes 22.11.2020 Bunch of fixes based on Diego’s VT comments Fixes based on 24.11.2020 2.4, 3.1.8, 6 VT discussions on previous day Final draft 27.11.2020 Chapters 5 - 7, Executive summary VT, EC Final draft 16.12.2020 Some parts revised based on VT comments of Álvaro López García Final draft 17.12.2020 Structure in the chapter 3.2 VT updated and smoke libraries etc. -

Big Data Management of Hospital Data Using Deep Learning and Block-Chain Technology: a Systematic Review
EAI Endorsed Transactions on Scalable Information Systems Research Article Big Data Management of Hospital Data using Deep Learning and Block-chain Technology: A Systematic Review Nawaz Ejaz1, Raza Ramzan1, Tooba Maryam1,*, Shazia Saqib1 1 Department of Computer Science, Lahore Garrison University, Lahore, Pakistan Abstract The main recompenses of remote and healthcare are sensor-based medical information gathering and remote access to medical data for real-time advice. The large volume of data coming from sensors requires to be handled by implementing deep learning and machine learning algorithms to improve an intelligent knowledge base for providing suitable solutions as and when needed. Electronic medical records (EMR) are mostly stored in a client-server database and are supported by enabling technologies like Internet of Things (IoT), Sensors, cloud, big data, Deep Learning, etc. It is accessed by several users involved like doctors, hospitals, labs, insurance providers, patients, etc. Therefore, data security from illegal access is crucial especially to manage the integrity of data . In this paper, we describe all the basic concepts involved in management and security of such data and proposed a novel system to securely manage the hospital’s big data using Deep Learning and Block-Chain technology. Keywords: Electronic medical records, big data, Security, Block-chain, Deep learning. Received on 23 December 2020, accepted on 16 March 2021, published on 23 March 2021 Copyright © 2021 Nawaz Ejaz et al., licensed to EAI. This is an open access article distributed under the terms of the Creative Commons Attribution license, which permits unlimited use, distribution and reproduction in any medium so long as the original work is properly cited. -

Outline of Machine Learning
Outline of machine learning The following outline is provided as an overview of and topical guide to machine learning: Machine learning – subfield of computer science[1] (more particularly soft computing) that evolved from the study of pattern recognition and computational learning theory in artificial intelligence.[1] In 1959, Arthur Samuel defined machine learning as a "Field of study that gives computers the ability to learn without being explicitly programmed".[2] Machine learning explores the study and construction of algorithms that can learn from and make predictions on data.[3] Such algorithms operate by building a model from an example training set of input observations in order to make data-driven predictions or decisions expressed as outputs, rather than following strictly static program instructions. Contents What type of thing is machine learning? Branches of machine learning Subfields of machine learning Cross-disciplinary fields involving machine learning Applications of machine learning Machine learning hardware Machine learning tools Machine learning frameworks Machine learning libraries Machine learning algorithms Machine learning methods Dimensionality reduction Ensemble learning Meta learning Reinforcement learning Supervised learning Unsupervised learning Semi-supervised learning Deep learning Other machine learning methods and problems Machine learning research History of machine learning Machine learning projects Machine learning organizations Machine learning conferences and workshops Machine learning publications -

European Journal of Computer Science and Information
European Journal of Computer Science and Information Technology Vol.9, No.2, pp.21-28, 2021 Print ISSN: 2054-0957 (Print), Online ISSN: 2054-0965 (Online) COMPARING THE TECHNOLOGIES USED FOR THE APPLICATION OF ARTIFICIAL NEURAL NETWORKS Elda Xhumari PhD Candidate, University of Tirana, Faculty of Natural Sciences, Department of Informatics ABSTRACT: In the past few years, artificial neural networks (ANNs) have become a practice wherever it is necessary to solve problems of forecasting, classification, or control. ANNs are intuitively attractive because they are based on a primitive biological model of nervous systems. In the future, the development of such neurobiological models may lead to the creation of truly thinking computers. The areas of application of neural networks are very diverse - these are text and speech recognition, semantic search, expert systems, and decision support systems, prediction of stock prices, security systems, text analysis, etc. Based on the wide application of artificial neural networks, the application of numerous and diverse technologies can be inferred. In this research paper, a comparative approach towards the above-mentioned technologies will be undertaken in order to identify the optimal technology for each problem area in accordance with their respective advantages and disadvantages. KEYWORDS: artificial neural networks, applications, modules INTRODUCTION Artificial Neural Network (ANN) is a computational method that integrates the concepts of the human biological brain to computers for machine learning. The main purpose is to enable computers to adapt and learn the exact behaviour of human beings. As such, machine learning facilitates the continued processing of information that leads to the capacity to solve complex problems and equations that are beyond human ability (Goncalves et al., 2013). -

Machine Learning Technique Used in Enhancing Teaching Learning Process in Education Sector and Review of Machine Learning Tools Diptiverma #1, Dr
International Journal of Scientific & Engineering Research Volume 9, Issue 6, June-2018 ISSN 2229-5518 741 Machine Learning Technique used in enhancing Teaching Learning Process in education Sector and review of Machine Learning Tools DiptiVerma #1, Dr. K. Nirmala#2 MCA Department, SavitribaiPhule Pune University DYPIMCA, Akurdi, Pune , INDIA [email protected], [email protected] Abstract: Machine learning is one of the widely rigorous study that teaching learning process has used research area in today’s world is artificial been changing over the time. The traditional intelligence and one of the scope full area is protocol of classroom teaching has been taken to Machine Learning (ML). This is study and out of box level, where e-learning, m-learning, analysis of some machine learning techniques Flipped Classroom, Design Thinking (Case used in education for particularly increasing the Method),Gamification, Online Learning, Audio & performance in teaching learning process, along Video learning, “Real-World” Learning, with review of some machine learning tools. Brainstorming, Classes Outside the Classroom learning, Role Play technique, TED talk sessions Keyword:Machine learning, Teaching Learning, are conducted to provide education beyond text Machine Learning Tools, NLP book and syllabus. I. INTRODUCTION II. MACHINE LEARNING PROCESS: Machine Learning is a science making system Machine Learning is a science of making system (computers) to understand from the past behavior smart. Machine learning we can say has improved of data or from historic data to behave smartly in the lives of human being in term of their successful every situation like human beings do. Without implementation and accuracy in predicting having the same type of situation a human can results.[11] behave or can react to the condition smartly.