Bootable Media and Images Preparation Guide with How-To
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Analyzing Code for KDE/Qt && Other Open Source Software
Analyzing code for KDE/Qt && other open source software http://leetcode.cn/2016/11/analyzing-code-for-kde-qt-open-source-components.html Leslie Zhai 普华——操作系统整合解决方案专家 Senior Software Engineer iSOFT Infrastructure Software co., Ltd; KDE developer KDE-China.org && Leetcode.cn 1 WHY 目录 HOWTO Contents 2 3 REFERENCE Part1 WHY? VULNERABILITIES OPTIMIZATION WHY -VULNERABILITIES 普华——操作系统整合解决方案专家 WHY - OPTIMIZATION 普华——操作系统整合解决方案专家 Identifying potential bottlenecks; Detecting problems in memory management; Detecting problems in C/C++ via static/dynamic analyzer source code analysis tool; Analyzing the CPU usage of embedded applications and Linux desktop applications; Part 2 HOWTO Static Analyzer Sanitizer libFuzzer CFI Safe Stack HOWTO – static analyer for k3b v2.10.0 普华——操作系统整合解决方案专家 HOWTO - static analyzer for k3b v2.10.0 普华——操作系统整合解决方案专家 scan-build -k -v -V cmake .. -DCMAKE_INSTALL_PREFIX=/usr \ -DKDE_INSTALL_LIBDIR=lib \ -DKDE_INSTALL_LIBEXECDIR=lib \ -DKDE_INSTALL_USE_QT_SYS_PATHS=ON \ -DK3B_BUILD_API_DOCS=ON \ -DK3B_ENABLE_PERMISSION_HELPER=ON \ -DK3B_DEBUG=ON scan-build -k -v -V make HOWTO - static analyzer for k3b v2.10.0 普华——操作系统整合解决方案专家 HOWTO - static analyzer for k3b v2.10.0 普华——操作系统整合解决方案专家 HOWTO - static analyzer for k3b v2.10.0 普华——操作系统整合解决方案专家 Q_UNUSED(dialogOpen); HOWTO - static analyzer for k3b v2.10.0 普华——操作系统整合解决方案专家 HOWTO - static analyzer for k3b v2.10.0 普华——操作系统整合解决方案专家 HOWTO - static analyzer for k3b v2.10.0 普华——操作系统整合解决方案专家 http://clang-analyzer.llvm.org/annotations.html#custom_assertions HOWTO - static analyzer for -
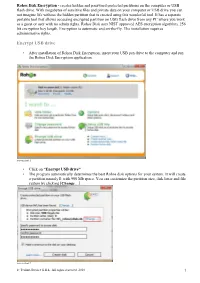
Rohos Disk Encryption Tutorial
Rohos Disk Encryption - creates hidden and password protected partitions on the computer or USB flash drive. With megabytes of sensitive files and private data on your computer or USB drive you can not imagine life without the hidden partition that is created using this wonderful tool. It has a separate portable tool that allows accessing encrypted partition on USB flash drive from any PC where you work as a guest or user with no admin rights. Rohos Disk uses NIST approved AES encryption algorithm, 256 bit encryption key length. Encryption is automatic and on-the-fly. The installation requires administrative rights. Encrypt USB drive • After installation of Rohos Disk Encryption, insert your USB pen drive to the computer and run the Rohos Disk Encryption application. screen shot 1 • Click on “Encrypt USB drive” • The program automatically determines the best Rohos disk options for your system. It will create a partition namely I: with 900 Mb space. You can customize the partition size, disk letter and file system by clicking [ Change …]. screen shot 2 © Tesline-Service S.R.L. All rights reserved. 2010 1 screen shot 3 Remember Rohos Disk Encryption has no encrypted disk size limit. Thus you may change disk size in this window. Notice that Rohos Disk displays your flash drive’s available free space. Also file system may be changed. By default, Rohos Disk Encryption creates disk in NTFS but it may be changed to FAT/FAT32. • After all disk settings are adjusted you may insert a password to Rohos disk, confirm it and click on “ Create disk ”. -

Chapter 3. Booting Operating Systems
Chapter 3. Booting Operating Systems Abstract: Chapter 3 provides a complete coverage on operating systems booting. It explains the booting principle and the booting sequence of various kinds of bootable devices. These include booting from floppy disk, hard disk, CDROM and USB drives. Instead of writing a customized booter to boot up only MTX, it shows how to develop booter programs to boot up real operating systems, such as Linux, from a variety of bootable devices. In particular, it shows how to boot up generic Linux bzImage kernels with initial ramdisk support. It is shown that the hard disk and CDROM booters developed in this book are comparable to GRUB and isolinux in performance. In addition, it demonstrates the booter programs by sample systems. 3.1. Booting Booting, which is short for bootstrap, refers to the process of loading an operating system image into computer memory and starting up the operating system. As such, it is the first step to run an operating system. Despite its importance and widespread interests among computer users, the subject of booting is rarely discussed in operating system books. Information on booting are usually scattered and, in most cases, incomplete. A systematic treatment of the booting process has been lacking. The purpose of this chapter is to try to fill this void. In this chapter, we shall discuss the booting principle and show how to write booter programs to boot up real operating systems. As one might expect, the booting process is highly machine dependent. To be more specific, we shall only consider the booting process of Intel x86 based PCs. -
Linux Software Für Jeden Zweck Linux Days Dortmund 2017
Linux Software für jeden Zweck Linux Days Dortmund 2017 FOSS-AG Dortmund Vortragender: @draget (Michael Gajda) 25. Juni 2017 1 There’s an App a Package for that! 68829! (2016-12-01) wget http://packages.ubuntu.com/xenial/allpackages?format=txt.gz -q -O - | zcat | tail -n +6 | wc -l 2 Hinweis • Die hier vorgestellte Software ist eine persönliche Auswahl des Vortragenden • Vorschläge oder Fragen gewünscht! 3 GPL, Fuck Yeah! Fast jede hier vorgestellte Software ist: • kostenlos! • quelloffen! • aus Spaß am Entwickeln entstanden! 4 Mit Winows zu Linux WinSCP Dateiaustausch zwischen Windows und Linux • Wer Angst vor der Kommandozeile hat… • Unterstützt SFTP und SCP Praktisch um Dateien von Zuhause mit entfernten Server. URL: https://winscp.net/ 5 Putty Windows SSH • Wer Angst vor GUIs hat… • De facto Standard • Netzwerktunnel Bitte darauf achten den korrekte Installer herunterzuladen. Angriffs-Gefahr! URL: http://www.putty.org/ 6 Produktivität TeXstudio LaTeX Editor • Gute Autovervollständigung • Vorschau für Bilder und Dateien Ubuntu, Mint, etc. > apt install texstudio URL: http://www.texstudio.org/ 7 Brasero Das Gnome Brennprogramm • Benutzerfreundlich • CD/DVD/BR usw. • Integrierter Cover-Editor • Unterstütze Backends: cdrtools, cdrkit, growisofs und libburn. Ubuntu, Mint, etc. > apt install brasero URL: https://wiki.gnome.org/Apps/Brasero 8 K3B Das KDE Brennprogramm • KDE Burn Baby, Burn! • Umfangreicher als Brasero • Viele Funktionen • CD/DVD/BR usw. • Abbild-Verwaltung Ubuntu, Mint, etc. > apt install k3b URL: http://k3b.plainblack.com/ 9 VirtualBox Virtuelle PCs per Knopfdruck • Performante Emulation von kompletten PCs • Software ausprobieren • Betriebssysteme ausprobieren • Viren ausprobieren • Snapshots • Alternativen: qemu + libvirt/virt- manager, VMWare Workstation Ubuntu, Mint, etc. > apt install virtualbox-qt 10 URL: https://www.virtualbox.org/ Marble Virtueller Globus • Nicht hübsch, aber vielfältig • Zugriff auf OSM • Viele weitere Datenquellen • Routing Ubuntu, Mint, etc. -

Guide How to Protect Your Private Data with Rohos Disk Encryption
Guide how to protect your private data with Rohos Disk Encryption 1 Content 1. Encrypt USB drive - Portable Application 2. Encrypt HDD 3. Hide folder 4. Have USB Key for access control 5. Rohos disk options 6. Steganography 7. Other Rohos Disk features 8. Integrated File-Shredder 9. Access your portable partition on a PC without Admin rights - Virtual keyboard 10. How to delete encrypted disk 11. How to delete all Rohos files from you USB flash drive 2 Rohos Disk Encryption - program creates hidden and protected partitions on the computer or USB flash drive. Those who have megabytes of sensitive files and seriously concerned with data security, can not imagine their computer or USB drive without the hidden partition that is created using this wonderful data encryption tool. Rohos Disk uses NIST approved AES encryption algorithm, 256 bit encryption key length. Encryption is automatic and on-the-fly. The installation requires administrative rights. Encrypt USB drive • After installation of Rohos Disk Encryption, insert your USB pen drive to the computer and run the Rohos Disk Encryption application. screen shot 1 • Click on “Encrypt USB drive” • The program automatically determines the best Rohos disk options for your system. It will create a partition namely G: with 2000 Mb space. You can customize the partition size, disk letter and file system by clicking [ Change …]. 3 screen shot 2 screen shot 3 Remember Rohos Disk Encryption has no encrypted disk size limit. Thus you may change disk size in this window. Notice that Rohos Disk displays your flash drive’s available free space. -

The Linux Command Line
The Linux Command Line Fifth Internet Edition William Shotts A LinuxCommand.org Book Copyright ©2008-2019, William E. Shotts, Jr. This work is licensed under the Creative Commons Attribution-Noncommercial-No De- rivative Works 3.0 United States License. To view a copy of this license, visit the link above or send a letter to Creative Commons, PO Box 1866, Mountain View, CA 94042. A version of this book is also available in printed form, published by No Starch Press. Copies may be purchased wherever fine books are sold. No Starch Press also offers elec- tronic formats for popular e-readers. They can be reached at: https://www.nostarch.com. Linux® is the registered trademark of Linus Torvalds. All other trademarks belong to their respective owners. This book is part of the LinuxCommand.org project, a site for Linux education and advo- cacy devoted to helping users of legacy operating systems migrate into the future. You may contact the LinuxCommand.org project at http://linuxcommand.org. Release History Version Date Description 19.01A January 28, 2019 Fifth Internet Edition (Corrected TOC) 19.01 January 17, 2019 Fifth Internet Edition. 17.10 October 19, 2017 Fourth Internet Edition. 16.07 July 28, 2016 Third Internet Edition. 13.07 July 6, 2013 Second Internet Edition. 09.12 December 14, 2009 First Internet Edition. Table of Contents Introduction....................................................................................................xvi Why Use the Command Line?......................................................................................xvi -

Boxedapp Complete Guide
APPLICATION VIRTUALIZATION SOLUTIONS BoxedApp Application Virtualization Solutions from Softanics Complete Guide c Softanics, All rights reserved BoxedApp.com APPLICATION VIRTUALIZATION SOLUTIONS THE COMPLETE GUIDE Contents Table of contents 2 Introduction 3 Which Product to Choose 3 System Requirements 3 Virtual File System 4 Introduction................................................4 Creating Virtual Files..........................................4 Custom Virtual Files: IStream-Based Files...............................4 Virtual Registry 5 Processes that Share Virtual Environment5 Attached Processes............................................5 How Attachment Works.........................................6 Virtual Process..............................................6 Shared Memory..............................................6 Typical Use Scenarios for BoxedApp SDK6 Loading DLL from Memory.......................................6 Using COM / ActiveX Object without Registering It in the Registry................7 Starting Application Directly from Memory..............................7 Intercepting Functions..........................................7 BoxedApp SDK 9 BoxedApp SDK Functions........................................9 BoxedAppSDK_Init....................................... 11 BoxedAppSDK_Exit....................................... 11 BoxedAppSDK_EnableDebugLog............................... 11 BoxedAppSDK_SetLogFile................................... 12 BoxedAppSDK_WriteLog.................................... 12 BoxedAppSDK_EnableOption................................ -

The Complete Freebsd
The Complete FreeBSD® If you find errors in this book, please report them to Greg Lehey <grog@Free- BSD.org> for inclusion in the errata list. The Complete FreeBSD® Fourth Edition Tenth anniversary version, 24 February 2006 Greg Lehey The Complete FreeBSD® by Greg Lehey <[email protected]> Copyright © 1996, 1997, 1999, 2002, 2003, 2006 by Greg Lehey. This book is licensed under the Creative Commons “Attribution-NonCommercial-ShareAlike 2.5” license. The full text is located at http://creativecommons.org/licenses/by-nc-sa/2.5/legalcode. You are free: • to copy, distribute, display, and perform the work • to make derivative works under the following conditions: • Attribution. You must attribute the work in the manner specified by the author or licensor. • Noncommercial. You may not use this work for commercial purposes. This clause is modified from the original by the provision: You may use this book for commercial purposes if you pay me the sum of USD 20 per copy printed (whether sold or not). You must also agree to allow inspection of printing records and other material necessary to confirm the royalty sums. The purpose of this clause is to make it attractive to negotiate sensible royalties before printing. • Share Alike. If you alter, transform, or build upon this work, you may distribute the resulting work only under a license identical to this one. • For any reuse or distribution, you must make clear to others the license terms of this work. • Any of these conditions can be waived if you get permission from the copyright holder. Your fair use and other rights are in no way affected by the above. -

Nápověda Programu Infra Recorder
Infra Recorder Úvod Vítejte Děkujeme, že jste si nainstalovali Infra Recorder! Infra Recorder je bezplatné řešení pro vypalování CD/DVD pod Microsoft Windows. Rychlá navigace Přehled funkcí Licenční ujednání Systémové požadavky Quick Start Copyright Poděkování Co je nového Instalace Infra Recorder Přehled funkcí Na této stránce naleznete seznam nejpodstatnějších funkcí Infra Recorder. Hlavní funkce Tvorba datových, hudebních a mixed-mode projektů a jejich záznam na kompaktní disky nebo do obrazů. Tvorba a vypalování obrazů disků. Přímé kopírování disků on the fly nebo za pomoci dočasného obrazu disku. Mazání přepisovatelných disků s možností výběru ze čtyř režimů mazání. Import sekcí multisession disků a přidávání dalších sekcí na tyto disky. Uzavírání disků (zápis lead-out pro znemožnění přidávání dalších dat). Vyhledávání mechanik připojených k SCSI/IDE řadičům a detekce funkcí, které tyto mechaniky podporují. Zobrazení detailních informací o vloženém disku. Čtení a ukládání zvukových a datových stop do souborů (wav. a .iso) Vyhledávání chyb. Prostředí Moderní přizpůsobitelné prostředí podobající se Průzkumníkovi Windows. Podpora drag and drop pro přetahování souborů do projektu z interního průzkumníka i Průzkumníka Windows. Rozdílné rozvržení rozhraní podle typu aktivního projektu usnadňující práci s programem. Samostatná express aplikace navržená k rychlému a snadnému navedení uživatele k těm správným nástrojům. Kompletně přeložitelné rozhraní hlavní aplikace, express aplikace a rozšíření průzkumníka. Integrace do Průzkumníka Integrace do Průzkumníka přidává nové položky kontextové nabídky. Zápis uložených projektů a obrazů disků. Otevírání a editace projektů. Přizpůsobitelné, může být zobrazeno jako podnabídka a s nebo bez ikon. Rozšíření může být zaregistrováno pro kteroukoliv příponu souboru. InfraRecorder License Agreement GNU GENERAL PUBLIC LICENSE Version 3, 29 June 2007 Copyright © 2007 Free Software Foundation, Inc. -

Lecture 5: Feb 4Th, 2020 5.1 OS Boot Process
CMPSCI 577 Operating Systems Design and Implementation Spring 2020 Lecture 5: Feb 4th, 2020 Lecturer: Prashant Shenoy Scribe: Serena Chan 5.1 OS Boot Process While seemingly mundane and not directly relevant to the modifications we will be making in this course, understanding the OS boot process is important for modifying the kernel. There are six steps that take the machine to a running state from when it is first turned on. 5.1.1 Step 1: BIOS (Basic Input/Output System) The BIOS is a small piece of code that lives in the firmware and is the first software that runs upon boot. When the computer is turned on, the BIOS runs the Power-on Self Test, where the RAM is initialized and hardware such as disks and peripherals are identified and checked. Once the disk is found, the BIOSwill start the boot process from the disk (‘bootstrapping’). The BIOS is often stored on EEPROM/ROM (read-only memory); because of its hardware-specific nature, it is not designed to be easily user modifiable. In addition, since the BIOS is the lowest level of softwarein the PC, it also acts as an interface for the OS to perform I/O and communicate with hardware. 5.1.2 Step 2: MBR (Master Boot Record) The MDR is the first 512 bytes of memory and consists of three components. In particular, thefirst440 bytes contain the bootstrap code that is used to continue the boot process, or the 1st stage boot loader; this is executed by the BIOS. The functionality of the code is to simply search through the partition table and find the root partition, where is where the OS resides. -

Virus Infection Techniques: Boot Record Viruses
Virus Infection Techniques: Boot Record Viruses Bill Harrison CS4440/7440 Malware Analysis and Defense Reading } Start reading Chapter 4 of Szor 2 Virus Infection Techniques } We will survey common locations of virus infections: MBR (Master Boot Record) Boot sector Executable files (*.EXE, *.COM, *.BAT, etc.) } Most of the examples of these viruses, especially the first two types, are from the DOS and floppy disk era 3 Why Study Older Viruses? } Vulnerabilities remain very similar over time, along with the means to exploit them and defend against them } Modern Internet worms differ mainly in the use of the internet for transport, and are otherwise similar to older viruses } Older viruses illustrate the virus vs. antivirus battle over many generations 4 Boot-up Infections and the PC Boot-up Sequence } PC boot-up sequence: 1. BIOS searches for boot device (might be a diskette, hard disk, or CD-ROM) 2. MBR (Master Boot Record) is read into memory from the beginning of the first disk partition; execution proceeds from memory 5 Master Boot Record Structure Boot-up Sequence cont’d. 3. Beginning of MBR has tiny code called the boot- strap loader 4. Data area within MBR has the disk PT (partition table) 5. Boot-strap loader reads PT and finds the active boot partition 6. Boot-strap loader loads the first sector of the active partition into memory and jumps to it; this is called the boot sector 7 Boot-up Sequence cont’d. } MBR is always at BIOS the very first sector of the hard MBR: Expanded View MBR Boot-strap loader code (446 disk (first 512 -

Virtualization and Containerization of Application Infrastructure: a Comparison Mathijs Jeroen Scheepers University of Twente P.O
Virtualization and Containerization of Application Infrastructure: A Comparison Mathijs Jeroen Scheepers University of Twente P.O. Box 217, 7500AE Enschede The Netherlands [email protected] ABSTRACT Modern cloud infrastructure uses virtualization to isolate applications, optimize the utilization of hardware resources and provide operational flexibility. However, conventional virtualization comes at the cost of resource overhead. Container-based virtualization could be an alternative as it potentially reduces overhead and thus improves the uti- lization of datacenters. This paper presents the results of a marco-benchmark performance comparison between the two implementations of these technologies, namely Xen Figure 1. A schematic overview of virtual ma- and LXC, as well as a discussion on their operational flex- chines in a datacenter. ibility. Keywords et al. [7], expects hypervisors to provide isolation and portability. The Xen [4] hypervisor is a popular technol- Hypervisor, Virtualization, Cloud computing, Application ogy and widely used at the moment. infrastructure, LXC, Xen, Container-based virtualization With recent developments around Docker [2] and LXC [3] there now seems to be a viable alternative to the hyper- 1. INTRODUCTION visor and traditional virtualization for application infras- According to Zhang et al. [20] virtualization technology tructures. Linux Containers (LXC) is a kernel technol- is an essential part of modern cloud infrastructure, such ogy that is able to run a multitude of processes, each in as Amazon's Elastic Compute Cloud (EC2) and Google's their own isolated environment. This technique is called App Engine. These days, most cloud computing datacen- container-based virtualization. Docker is a tool that makes ters run hypervisors on top of their physical machines.