Interval Mathematics, Algebraic Equations and Optimization
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Interval Notation and Linear Inequalities
CHAPTER 1 Introductory Information and Review Section 1.7: Interval Notation and Linear Inequalities Linear Inequalities Linear Inequalities Rules for Solving Inequalities: 86 University of Houston Department of Mathematics SECTION 1.7 Interval Notation and Linear Inequalities Interval Notation: Example: Solution: MATH 1300 Fundamentals of Mathematics 87 CHAPTER 1 Introductory Information and Review Example: Solution: Example: 88 University of Houston Department of Mathematics SECTION 1.7 Interval Notation and Linear Inequalities Solution: Additional Example 1: Solution: MATH 1300 Fundamentals of Mathematics 89 CHAPTER 1 Introductory Information and Review Additional Example 2: Solution: 90 University of Houston Department of Mathematics SECTION 1.7 Interval Notation and Linear Inequalities Additional Example 3: Solution: Additional Example 4: Solution: MATH 1300 Fundamentals of Mathematics 91 CHAPTER 1 Introductory Information and Review Additional Example 5: Solution: Additional Example 6: Solution: 92 University of Houston Department of Mathematics SECTION 1.7 Interval Notation and Linear Inequalities Additional Example 7: Solution: MATH 1300 Fundamentals of Mathematics 93 Exercise Set 1.7: Interval Notation and Linear Inequalities For each of the following inequalities: Write each of the following inequalities in interval (a) Write the inequality algebraically. notation. (b) Graph the inequality on the real number line. (c) Write the inequality in interval notation. 23. 1. x is greater than 5. 2. x is less than 4. 24. 3. x is less than or equal to 3. 4. x is greater than or equal to 7. 25. 5. x is not equal to 2. 6. x is not equal to 5 . 26. 7. x is less than 1. 8. -

Interval Computations: Introduction, Uses, and Resources
Interval Computations: Introduction, Uses, and Resources R. B. Kearfott Department of Mathematics University of Southwestern Louisiana U.S.L. Box 4-1010, Lafayette, LA 70504-1010 USA email: [email protected] Abstract Interval analysis is a broad field in which rigorous mathematics is as- sociated with with scientific computing. A number of researchers world- wide have produced a voluminous literature on the subject. This article introduces interval arithmetic and its interaction with established math- ematical theory. The article provides pointers to traditional literature collections, as well as electronic resources. Some successful scientific and engineering applications are listed. 1 What is Interval Arithmetic, and Why is it Considered? Interval arithmetic is an arithmetic defined on sets of intervals, rather than sets of real numbers. A form of interval arithmetic perhaps first appeared in 1924 and 1931 in [8, 104], then later in [98]. Modern development of interval arithmetic began with R. E. Moore’s dissertation [64]. Since then, thousands of research articles and numerous books have appeared on the subject. Periodic conferences, as well as special meetings, are held on the subject. There is an increasing amount of software support for interval computations, and more resources concerning interval computations are becoming available through the Internet. In this paper, boldface will denote intervals, lower case will denote scalar quantities, and upper case will denote vectors and matrices. Brackets “[ ]” will delimit intervals while parentheses “( )” will delimit vectors and matrices.· Un- derscores will denote lower bounds of· intervals and overscores will denote upper bounds of intervals. Corresponding lower case letters will denote components of vectors. -

General Topology
General Topology Tom Leinster 2014{15 Contents A Topological spaces2 A1 Review of metric spaces.......................2 A2 The definition of topological space.................8 A3 Metrics versus topologies....................... 13 A4 Continuous maps........................... 17 A5 When are two spaces homeomorphic?................ 22 A6 Topological properties........................ 26 A7 Bases................................. 28 A8 Closure and interior......................... 31 A9 Subspaces (new spaces from old, 1)................. 35 A10 Products (new spaces from old, 2)................. 39 A11 Quotients (new spaces from old, 3)................. 43 A12 Review of ChapterA......................... 48 B Compactness 51 B1 The definition of compactness.................... 51 B2 Closed bounded intervals are compact............... 55 B3 Compactness and subspaces..................... 56 B4 Compactness and products..................... 58 B5 The compact subsets of Rn ..................... 59 B6 Compactness and quotients (and images)............. 61 B7 Compact metric spaces........................ 64 C Connectedness 68 C1 The definition of connectedness................... 68 C2 Connected subsets of the real line.................. 72 C3 Path-connectedness.......................... 76 C4 Connected-components and path-components........... 80 1 Chapter A Topological spaces A1 Review of metric spaces For the lecture of Thursday, 18 September 2014 Almost everything in this section should have been covered in Honours Analysis, with the possible exception of some of the examples. For that reason, this lecture is longer than usual. Definition A1.1 Let X be a set. A metric on X is a function d: X × X ! [0; 1) with the following three properties: • d(x; y) = 0 () x = y, for x; y 2 X; • d(x; y) + d(y; z) ≥ d(x; z) for all x; y; z 2 X (triangle inequality); • d(x; y) = d(y; x) for all x; y 2 X (symmetry). -

Multidisciplinary Design Project Engineering Dictionary Version 0.0.2
Multidisciplinary Design Project Engineering Dictionary Version 0.0.2 February 15, 2006 . DRAFT Cambridge-MIT Institute Multidisciplinary Design Project This Dictionary/Glossary of Engineering terms has been compiled to compliment the work developed as part of the Multi-disciplinary Design Project (MDP), which is a programme to develop teaching material and kits to aid the running of mechtronics projects in Universities and Schools. The project is being carried out with support from the Cambridge-MIT Institute undergraduate teaching programe. For more information about the project please visit the MDP website at http://www-mdp.eng.cam.ac.uk or contact Dr. Peter Long Prof. Alex Slocum Cambridge University Engineering Department Massachusetts Institute of Technology Trumpington Street, 77 Massachusetts Ave. Cambridge. Cambridge MA 02139-4307 CB2 1PZ. USA e-mail: [email protected] e-mail: [email protected] tel: +44 (0) 1223 332779 tel: +1 617 253 0012 For information about the CMI initiative please see Cambridge-MIT Institute website :- http://www.cambridge-mit.org CMI CMI, University of Cambridge Massachusetts Institute of Technology 10 Miller’s Yard, 77 Massachusetts Ave. Mill Lane, Cambridge MA 02139-4307 Cambridge. CB2 1RQ. USA tel: +44 (0) 1223 327207 tel. +1 617 253 7732 fax: +44 (0) 1223 765891 fax. +1 617 258 8539 . DRAFT 2 CMI-MDP Programme 1 Introduction This dictionary/glossary has not been developed as a definative work but as a useful reference book for engi- neering students to search when looking for the meaning of a word/phrase. It has been compiled from a number of existing glossaries together with a number of local additions. -
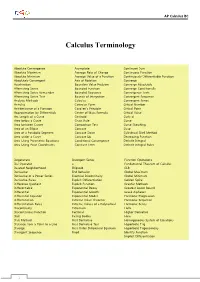
Calculus Terminology
AP Calculus BC Calculus Terminology Absolute Convergence Asymptote Continued Sum Absolute Maximum Average Rate of Change Continuous Function Absolute Minimum Average Value of a Function Continuously Differentiable Function Absolutely Convergent Axis of Rotation Converge Acceleration Boundary Value Problem Converge Absolutely Alternating Series Bounded Function Converge Conditionally Alternating Series Remainder Bounded Sequence Convergence Tests Alternating Series Test Bounds of Integration Convergent Sequence Analytic Methods Calculus Convergent Series Annulus Cartesian Form Critical Number Antiderivative of a Function Cavalieri’s Principle Critical Point Approximation by Differentials Center of Mass Formula Critical Value Arc Length of a Curve Centroid Curly d Area below a Curve Chain Rule Curve Area between Curves Comparison Test Curve Sketching Area of an Ellipse Concave Cusp Area of a Parabolic Segment Concave Down Cylindrical Shell Method Area under a Curve Concave Up Decreasing Function Area Using Parametric Equations Conditional Convergence Definite Integral Area Using Polar Coordinates Constant Term Definite Integral Rules Degenerate Divergent Series Function Operations Del Operator e Fundamental Theorem of Calculus Deleted Neighborhood Ellipsoid GLB Derivative End Behavior Global Maximum Derivative of a Power Series Essential Discontinuity Global Minimum Derivative Rules Explicit Differentiation Golden Spiral Difference Quotient Explicit Function Graphic Methods Differentiable Exponential Decay Greatest Lower Bound Differential -

Calculus Formulas and Theorems
Formulas and Theorems for Reference I. Tbigonometric Formulas l. sin2d+c,cis2d:1 sec2d l*cot20:<:sc:20 +.I sin(-d) : -sitt0 t,rs(-//) = t r1sl/ : -tallH 7. sin(A* B) :sitrAcosB*silBcosA 8. : siri A cos B - siu B <:os,;l 9. cos(A+ B) - cos,4cos B - siuA siriB 10. cos(A- B) : cosA cosB + silrA sirrB 11. 2 sirrd t:osd 12. <'os20- coS2(i - siu20 : 2<'os2o - I - 1 - 2sin20 I 13. tan d : <.rft0 (:ost/ I 14. <:ol0 : sirrd tattH 1 15. (:OS I/ 1 16. cscd - ri" 6i /F tl r(. cos[I ^ -el : sitt d \l 18. -01 : COSA 215 216 Formulas and Theorems II. Differentiation Formulas !(r") - trr:"-1 Q,:I' ]tra-fg'+gf' gJ'-,f g' - * (i) ,l' ,I - (tt(.r))9'(.,') ,i;.[tyt.rt) l'' d, \ (sttt rrJ .* ('oqI' .7, tJ, \ . ./ stll lr dr. l('os J { 1a,,,t,:r) - .,' o.t "11'2 1(<,ot.r') - (,.(,2.r' Q:T rl , (sc'c:.r'J: sPl'.r tall 11 ,7, d, - (<:s<t.r,; - (ls(].]'(rot;.r fr("'),t -.'' ,1 - fr(u") o,'ltrc ,l ,, 1 ' tlll ri - (l.t' .f d,^ --: I -iAl'CSllLl'l t!.r' J1 - rz 1(Arcsi' r) : oT Il12 Formulas and Theorems 2I7 III. Integration Formulas 1. ,f "or:artC 2. [\0,-trrlrl *(' .t "r 3. [,' ,t.,: r^x| (' ,I 4. In' a,,: lL , ,' .l 111Q 5. In., a.r: .rhr.r' .r r (' ,l f 6. sirr.r d.r' - ( os.r'-t C ./ 7. /.,,.r' dr : sitr.i'| (' .t 8. tl:r:hr sec,rl+ C or ln Jccrsrl+ C ,f'r^rr f 9. -

Assignment 5
Differential Topology Assignment 5 Exercise 1: Classification of smooth 1-manifolds Let M be a compact, smooth and connected 1−manifold with boundary. Show that M is either diffeomorphic to a circle or to a closed interval [a; b] ⊂ R. This then shows that every compact smooth 1−manifold is build up from connected components each diffeomorphic to a circle or a closed interval. To prove the result, show the following steps: 1. Consider a Morse function f : M ! R. Let B denote the set of boundary points of M, and C the set of critical points of f. Show that M n (B[C) consists of a finite number of connected 1−manifolds, which we will call L1;:::;LN ⊂ M. 2. Prove that fk = fjLk : Lk ! f(Lk) is a diffeomorphism from Lk to an open interval f(Lk) ⊂ R. 3. Let L ⊂ M be a subset of a smooth 1−dimensional manifold M. Show that if L is diffeomorphic to an open interval in R, then there are at most two points a, b 2 L such that a, b2 = L. Here, L is the closure of L. 4. Consider a sequence (Li1 ;:::;Lik ) 2 fL1;:::;LN g. Such a sequence is called a chain if for every j 2 f1; : : : ; k − 1g the closures Lij and Lij+1 have a common boundary point. Show that a chain of maximal length m contains all of the 1−manifolds L1;:::;LN defined above. 5. To finish the proof, we will need a technical lemma. Let g :[a; b] ! R be a smooth function with positive derivative on [a; b] n fcg for c 2 (a; b). -

DISTANCE SETS in METRIC SPACES 2.2. a = I>1
DISTANCE SETS IN METRIC SPACES BY L. M. KELLY AND E. A. NORDHAUS 1. Introduction. In 1920 Steinhaus [lOjO) observed that the distance set of a linear set of positive Lebesgue measure contains an interval with end point zero (an initial interval). Subsequently considerable attention was de- voted to this and related ideas by Sierpinski [9], Ruziewicz [8], and others. S. Piccard in 1940 gathered together many of these results and carried out an extensive investigation of her own concerning distance sets of euclidean subsets, particularly linear subsets, in a tract entitled Sur les ensembles de distances (des ensembles de points d'un espace euclidien) [7]. Two principal problems suggest themselves in such investigations. First, what can be said of the distance set of a given space, and secondly, what can be said of the possible realizations, in a specified class of distance spaces, of a given distance set (that is, of a set of non-negative numbers including zero). The writers mentioned above have been principally concerned with the first problem, although Miss Piccard devotes some space to the second. In [4] efforts were made to improve and extend some of her results concerning the latter problem. By way of completing a survey of the literature known to us, we observe that Besicovitch and Miller [l ] have examined the influence of positive Carathéodory linear measure on distance sets of subsets of E2, while Coxeter and Todd [2] have considered the possibility of realizing finite distance sets in spaces with indefinite metrics. Numerous papers of Erdös, for example [3], contain isolated but interesting pertinent results. -

METRIC SPACES and SOME BASIC TOPOLOGY
Chapter 3 METRIC SPACES and SOME BASIC TOPOLOGY Thus far, our focus has been on studying, reviewing, and/or developing an under- standing and ability to make use of properties of U U1. The next goal is to generalize our work to Un and, eventually, to study functions on Un. 3.1 Euclidean n-space The set Un is an extension of the concept of the Cartesian product of two sets that was studied in MAT108. For completeness, we include the following De¿nition 3.1.1 Let S and T be sets. The Cartesian product of S and T , denoted by S T,is p q : p + S F q + T . The Cartesian product of any ¿nite number of sets S1 S2 SN , denoted by S1 S2 SN ,is j b ck p1 p2 pN : 1 j j + M F 1 n j n N " p j + S j . The object p1 p2pN is called an N-tuple. Our primary interest is going to be the case where each set is the set of real numbers. 73 74 CHAPTER 3. METRIC SPACES AND SOME BASIC TOPOLOGY De¿nition 3.1.2 Real n-space,denotedUn, is the set all ordered n-tuples of real numbers i.e., n U x1 x2 xn : x1 x2 xn + U . Un U U U U Thus, _ ^] `, the Cartesian product of with itself n times. nofthem Remark 3.1.3 From MAT108, recall the de¿nition of an ordered pair: a b a a b . def This de¿nition leads to the more familiar statement that a b c d if and only if a bandc d. -

Notes on Metric Spaces
Notes on Metric Spaces These notes introduce the concept of a metric space, which will be an essential notion throughout this course and in others that follow. Some of this material is contained in optional sections of the book, but I will assume none of that and start from scratch. Still, you should check the corresponding sections in the book for a possibly different point of view on a few things. The main idea to have in mind is that a metric space is some kind of generalization of R in the sense that it is some kind of \space" which has a notion of \distance". Having such a \distance" function will allow us to phrase many concepts from real analysis|such as the notions of convergence and continuity|in a more general setting, which (somewhat) surprisingly makes many things actually easier to understand. Metric Spaces Definition 1. A metric on a set X is a function d : X × X ! R such that • d(x; y) ≥ 0 for all x; y 2 X; moreover, d(x; y) = 0 if and only if x = y, • d(x; y) = d(y; x) for all x; y 2 X, and • d(x; y) ≤ d(x; z) + d(z; y) for all x; y; z 2 X. A metric space is a set X together with a metric d on it, and we will use the notation (X; d) for a metric space. Often, if the metric d is clear from context, we will simply denote the metric space (X; d) by X itself. -

Lecture 3 Vector Spaces of Functions
12 Lecture 3 Vector Spaces of Functions 3.1 Space of Continuous Functions C(I) Let I ⊆ R be an interval. Then I is of the form (for some a < b) 8 > fx 2 Rj a < x < bg; an open interval; <> fx 2 Rj a · x · bg; a closed interval; I = > fx 2 Rj a · x < bg :> fx 2 Rj a < x · bg: Recall that the space of all functions f : I ¡! R is a vector space. We will now list some important subspaces: Example (1). Let C(I) be the space of all continuous functions on I. If f and g are continuous, so are the functions f + g and rf (r 2 R). Hence C(I) is a vector space. Recall, that a function is continuous, if the graph has no gaps. This can be formulated in di®erent ways: a) Let x0 2 I and let ² > 0 . Then there exists a ± > 0 such that for all x 2 I \ (x0 ¡ ±; x0 + ±) we have jf(x) ¡ f(x0)j < ² This tells us that the value of f at nearby points is arbitrarily close to the value of f at x0. 13 14 LECTURE 3. VECTOR SPACES OF FUNCTIONS b) A reformulation of (a) is: lim f(x) = f(x0) x!x0 3.2 Space of continuously di®erentiable func- tions C1(I) Example (2). The space C1(I). Here we assume that I is open. Recall that f is di®erentiable at x0 if f(x) ¡ f(x0) f(x0 + h) ¡ f(x0) 0 lim = lim =: f (x0) x!x0 x ¡ x0 h!0 h 0 exists. -

2.3 Vector Spaces
2.3. VECTOR SPACES 25 2.3 Vector Spaces MATH 294 FALL 1982 PRELIM 1 # 3a 2.3.1 Let C[0, 1] denote the space of continuous functions defined on the interval [0,1] (i.e. f(x) is a member of C[0, 1] if f(x) is continuous for 0 ≤ x ≤ 1). Which one of the following subsets of C[0, 1] does not form a vector space? Find it and explain why it does not. MATH 294 SPRING 1982 PRELIM 1 # 3 2.3.2 a) R 1 i) The subset of functions f which belongs to C[0, 1] for which 0 f(s)ds = 0. ii) The set of functions f in C[0, 1] which vanish at exactly one point (i.e. f(x) = 0 for only one x with 0 ≤ x ≤ 1). Note different functions may vanish at different points within the interval. iii) The subset of functions f in C[0, 1] for which f(0) = f(1). 3 0 b) Let f(x) = x + 2x + 5. Consider the four vectors ~v1 = f(x), ~v2 = f (x) 00 000 0 df ,~v3 = f (x), ~v4 = f (x), f means dx . i) What is the dimension of the space spanned by the vectors? Justify your answer. 2 ii) Express x + 1 as a linear combination of the ~vi’s. MATH 294 FALL 1984 FINAL # 1 2.3.3 a) Determine which of the following subsets are subspaces of the indicated vector spaces, and for each subspace determine the dimension of th- space.