Mastering Sap Security & Risk
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Property Portfolio 30 June 2020 About Stockland We Have a Long and Proud History of Creating Places That Meet the Needs of Our Customers and Communities
Stockland Stockland PropertyPortfolio PropertyPortfolio Property Portfolio 30 June 2020 30 June 2020 30 June 2020 For personal use only stockland.com.au About Stockland We have a long and proud history of creating places that meet the needs of our customers and communities. OUR STORY When Stockland was founded in 1952, Ervin Graf had a vision “to not merely achieve growth and profits, but to make a worthwhile contribution to the development of our cities and great country”. Pursuing that vision has seen Stockland grow to become one of Australia’s largest diversified property groups. We develop and manage retail town centres, logistics, workplace properties, residential communities and retirement living villages. With the benefit of our diverse property skills, we connect different types of properties in shared locations, to create places that inspire people to gather, to share and to live life. We recognise our responsibilities to the environment and are a leader in sustainable business practices. For over 65 years, we have worked hard to grow our portfolio of assets and projects. We have a long and proud history of creating places that meet the needs of our customers and communities. OUR PROPERTY PORTFOLIO Stockland is one of Australia’s leading diversified property groups. We’re active in retail, logistics, workplace properties, residential communities and retirement living villages. This portfolio identifies all of our properties across Australia. More information on Stockland’s activities For personal use only and an online version of the portfolio data is available at www.stockland.com.au Image: Green Hills, NSW Property Portfolio Commercial Property .................................................................................................................................................................................................................................................................. -

Socially Conscious Australian Equity Holdings
Socially Conscious Australian Equity Holdings As at 30 June 2021 Country of Company domicile Weight COMMONWEALTH BANK OF AUSTRALIA AUSTRALIA 10.56% CSL LTD AUSTRALIA 8.46% AUST AND NZ BANKING GROUP AUSTRALIA 5.68% NATIONAL AUSTRALIA BANK LTD AUSTRALIA 5.32% WESTPAC BANKING CORP AUSTRALIA 5.08% TELSTRA CORP LTD AUSTRALIA 3.31% WOOLWORTHS GROUP LTD AUSTRALIA 2.93% FORTESCUE METALS GROUP LTD AUSTRALIA 2.80% TRANSURBAN GROUP AUSTRALIA 2.55% GOODMAN GROUP AUSTRALIA 2.34% WESFARMERS LTD AUSTRALIA 2.29% BRAMBLES LTD AUSTRALIA 1.85% COLES GROUP LTD AUSTRALIA 1.80% SUNCORP GROUP LTD AUSTRALIA 1.62% MACQUARIE GROUP LTD AUSTRALIA 1.54% JAMES HARDIE INDUSTRIES IRELAND 1.51% NEWCREST MINING LTD AUSTRALIA 1.45% SONIC HEALTHCARE LTD AUSTRALIA 1.44% MIRVAC GROUP AUSTRALIA 1.43% MAGELLAN FINANCIAL GROUP LTD AUSTRALIA 1.13% STOCKLAND AUSTRALIA 1.11% DEXUS AUSTRALIA 1.11% COMPUTERSHARE LTD AUSTRALIA 1.09% AMCOR PLC AUSTRALIA 1.02% ILUKA RESOURCES LTD AUSTRALIA 1.01% XERO LTD NEW ZEALAND 0.97% WISETECH GLOBAL LTD AUSTRALIA 0.92% SEEK LTD AUSTRALIA 0.88% SYDNEY AIRPORT AUSTRALIA 0.83% NINE ENTERTAINMENT CO HOLDINGS LIMITED AUSTRALIA 0.82% EAGERS AUTOMOTIVE LTD AUSTRALIA 0.82% RELIANCE WORLDWIDE CORP LTD UNITED STATES 0.80% SANDFIRE RESOURCES LTD AUSTRALIA 0.79% AFTERPAY LTD AUSTRALIA 0.79% CHARTER HALL GROUP AUSTRALIA 0.79% SCENTRE GROUP AUSTRALIA 0.79% ORORA LTD AUSTRALIA 0.75% ANSELL LTD AUSTRALIA 0.75% OZ MINERALS LTD AUSTRALIA 0.74% IGO LTD AUSTRALIA 0.71% GPT GROUP AUSTRALIA 0.69% Issued by Aware Super Pty Ltd (ABN 11 118 202 672, AFSL 293340) the trustee of Aware Super (ABN 53 226 460 365). -

Westpac Online Investment Loan Acceptable Securities List - Effective 3 September2021
Westpac Online Investment Loan Acceptable Securities List - Effective 3 September2021 ASX listed securities ASX Code Security Name LVR ASX Code Security Name LVR A2M The a2 Milk Company Limited 50% CIN Carlton Investments Limited 60% ABC Adelaide Brighton Limited 60% CIP Centuria Industrial REIT 50% ABP Abacus Property Group 60% CKF Collins Foods Limited 50% ADI APN Industria REIT 40% CL1 Class Limited 45% AEF Australian Ethical Investment Limited 40% CLW Charter Hall Long Wale Reit 60% AFG Australian Finance Group Limited 40% CMW Cromwell Group 60% AFI Australian Foundation Investment Co. Ltd 75% CNI Centuria Capital Group 50% AGG AngloGold Ashanti Limited 50% CNU Chorus Limited 60% AGL AGL Energy Limited 75% COF Centuria Office REIT 50% AIA Auckland International Airport Limited 60% COH Cochlear Limited 65% ALD Ampol Limited 70% COL Coles Group Limited 75% ALI Argo Global Listed Infrastructure Limited 60% CPU Computershare Limited 70% ALL Aristocrat Leisure Limited 60% CQE Charter Hall Education Trust 50% ALQ Als Limited 65% CQR Charter Hall Retail Reit 60% ALU Altium Limited 50% CSL CSL Limited 75% ALX Atlas Arteria 60% CSR CSR Limited 60% AMC Amcor Limited 75% CTD Corporate Travel Management Limited ** 40% AMH Amcil Limited 50% CUV Clinuvel Pharmaceuticals Limited 40% AMI Aurelia Metals Limited 35% CWN Crown Limited 60% AMP AMP Limited 60% CWNHB Crown Resorts Ltd Subordinated Notes II 60% AMPPA AMP Limited Cap Note Deferred Settlement 60% CWP Cedar Woods Properties Limited 45% AMPPB AMP Limited Capital Notes 2 60% CWY Cleanaway Waste -

ESG Reporting by the ASX200
Australian Council of Superannuation Investors ESG Reporting by the ASX200 August 2019 ABOUT ACSI Established in 2001, the Australian Council of Superannuation Investors (ACSI) provides a strong, collective voice on environmental, social and governance (ESG) issues on behalf of our members. Our members include 38 Australian and international We undertake a year-round program of research, asset owners and institutional investors. Collectively, they engagement, advocacy and voting advice. These activities manage over $2.2 trillion in assets and own on average 10 provide a solid basis for our members to exercise their per cent of every ASX200 company. ownership rights. Our members believe that ESG risks and opportunities have We also offer additional consulting services a material impact on investment outcomes. As fiduciary including: ESG and related policy development; analysis investors, they have a responsibility to act to enhance the of service providers, fund managers and ESG data; and long-term value of the savings entrusted to them. disclosure advice. Through ACSI, our members collaborate to achieve genuine, measurable and permanent improvements in the ESG practices and performance of the companies they invest in. 6 INTERNATIONAL MEMBERS 32 AUSTRALIAN MEMBERS MANAGING $2.2 TRILLION IN ASSETS 2 ESG REPORTING BY THE ASX200: AUGUST 2019 FOREWORD We are currently operating in a low-trust environment Yet, safety data is material to our members. In 2018, 22 – for organisations generally but especially businesses. people from 13 ASX200 companies died in their workplaces. Transparency and accountability are crucial to rebuilding A majority of these involved contractors, suggesting that this trust deficit. workplace health and safety standards are not uniformly applied. -

Business Leadership: the Catalyst for Accelerating Change
BUSINESS LEADERSHIP: THE CATALYST FOR ACCELERATING CHANGE Follow us on twitter @30pctAustralia OUR OBJECTIVE is to achieve 30% of ASX 200 seats held by women by end 2018. Gender balance on boards does achieve better outcomes. GREATER DIVERSITY ON BOARDS IS VITAL TO THE GOOD GOVERNANCE OF AUSTRALIAN BUSINESSES. FROM THE PERSPECTIVE OF PERFORMANCE AS WELL AS EQUITY THE CASE IS CLEAR. AUSTRALIA HAS MORE THAN ENOUGH CAPABLE WOMEN TO EXCEED THE 30% TARGET. IF YOUR BOARD IS NOT INVESTING IN THE CAPABILITY THAT DIVERSITY BRINGS, IT’S NOW A MARKED DEPARTURE FROM THE WHAT THE INVESTOR AND BROADER COMMUNITY EXPECT. Angus Armour FAICD, Managing Director & Chief Executive Officer, Australian Institute of Company Directors BY BRINGING TOGETHER INFLUENTIAL COMPANY CHAIRS, DIRECTORS, INVESTORS, HEAD HUNTERS AND CEOs, WE WANT TO DRIVE A BUSINESS-LED APPROACH TO INCREASING GENDER BALANCE THAT CHANGES THE WAY “COMPANIES APPROACH DIVERSITY ISSUES. Patricia Cross, Australian Chair 30% Club WHO WE ARE LEADERS LEADING BY EXAMPLE We are a group of chairs, directors and business leaders taking action to increase gender diversity on Australian boards. The Australian chapter launched in May 2015 with a goal of achieving 30% women on ASX 200 boards by the end of 2018. AUSTRALIAN 30% CLUB MEMBERS Andrew Forrest Fortescue Metals Douglas McTaggart Spark Group Ltd Infrastructure Trust Samuel Weiss Altium Ltd Kenneth MacKenzie BHP Billiton Ltd John Mulcahy Mirvac Ltd Stephen Johns Brambles Ltd Mark Johnson G8 Education Ltd John Shine CSL Ltd Paul Brasher Incitec Pivot -

Stoxx® Australia 150 Index
STOXX® AUSTRALIA 150 INDEX Components1 Company Supersector Country Weight (%) Commonwealth Bank of Australia Banks Australia 8.37 CSL Ltd. Health Care Australia 7.46 BHP GROUP LTD. Basic Resources Australia 7.23 National Australia Bank Ltd. Banks Australia 4.37 Westpac Banking Corp. Banks Australia 4.09 Australia & New Zealand Bankin Banks Australia 3.75 Wesfarmers Ltd. Retail Australia 3.30 WOOLWORTHS GROUP Personal Care, Drug & Grocery Australia 2.87 Macquarie Group Ltd. Financial Services Australia 2.84 Rio Tinto Ltd. Basic Resources Australia 2.48 Fortescue Metals Group Ltd. Basic Resources Australia 2.27 Transurban Group Industrial Goods & Services Australia 2.20 Telstra Corp. Ltd. Telecommunications Australia 2.05 Goodman Group Real Estate Australia 1.77 AFTERPAY Industrial Goods & Services Australia 1.54 Coles Group Personal Care, Drug & Grocery Australia 1.39 Woodside Petroleum Ltd. Energy Australia 1.28 Newcrest Mining Ltd. Basic Resources Australia 1.27 Aristocrat Leisure Ltd. Travel & Leisure Australia 1.11 XERO Technology Australia 1.00 SYDNEY AIRPORT Industrial Goods & Services Australia 0.93 Brambles Ltd. Industrial Goods & Services Australia 0.91 Sonic Healthcare Ltd. Health Care Australia 0.90 ASX Ltd. Financial Services Australia 0.82 SCENTRE GROUP Real Estate Australia 0.80 Cochlear Ltd. Health Care Australia 0.74 QBE Insurance Group Ltd. Insurance Australia 0.73 SUNCORP GROUP LTD. Insurance Australia 0.71 South32 Australia Basic Resources Australia 0.71 Santos Ltd. Energy Australia 0.68 Ramsay Health Care Ltd. Health Care Australia 0.66 Insurance Australia Group Ltd. Insurance Australia 0.65 Mirvac Group Real Estate Australia 0.60 DEXUS Real Estate Australia 0.59 SEEK Ltd. -

High Growth Model High Growth Core High Growth Core Portfolio | March 2021
Mulcahy High Growth Model High Growth Core High Growth Core Portfolio | March 2021 Holdings at March 2021 Sub-Asset Class Weight Australian Equities 57.75% Direct Australian Equites Direct AEQ 57.75% International Equities 37.03% Vanguard Global Value Equity Active ETF Developed Equities 9.73% Vanguard Total Stock Market ETF United States 5.00% Vanguard FTSE All World Ex-US ETF World ex US 14.35% iShares MSCI Emerging Markets ETF Emerging Markets 2.50% Vanguard MSCI International Small Companies Index ETF Global Small Caps 5.45% Property & Infrastructure 3.21% Vanguard Australian Property Securities Index ETF Australian REITs 3.21% Cash 2.01% Cash Cash 2.01% Australian Equities International Equities Property & Infrastructure Cash Active Asset Allocation Underweight Overweight The portfolio has Australian Equities maintained an overweight to Australian equities and alternatives, International Equities predominantly funded by an underweight to Property & Infrastructure alternatives. Fixed Interest Alternatives Cash -10.0% -5.0% 0.0% 5.0% 10.0% 15.0% 20.0% WealthO2 | March 2021 Australian Equities Component Top 10 Holdings Characteristics COMPANY WEIGHT ESTIMATED ESTIMATED FWD DIVIDEND YIELD P/E RATIO AUST AND NZ BANKING GROUP 13.9% 4.0% 25 WESTPAC BANKING CORP 12.4% 20 BHP GROUP LTD 7.3% 3.0% WOODSIDE PETROLEUM LTD 5.4% 15 BLACKMORES LTD 4.2% 2.0% 10 ORORA LTD 4.1% 1.0% WEBJET LTD 4.1% 5 RAMSAY HEALTH CARE LTD 4.1% 0.0% 0 STOCKLAND 4.0% Aus Equity Component Aus Equity Component CHALLENGER LTD 3.9% S&P/ASX 300 S&P/ASX 300 Sector Exposures Financials Materials Health Care Consumer Staples Real Estate Industrials Energy Consumer Discretionary Communication Services Information Technology Utilities Cash Aus Equity Component S&P/ASX 300 0.0% 5.0% 10.0% 15.0% 20.0% 25.0% 30.0% 35.0% Market Cap Exposures The portfolio's Australian equity component maintains an Top 50 underweight to the 'Top 50' of the market, in favour of mid-cap securities. -

Aon Non Executive Director Survey Participating Organisations (Pdf, 181.66Kb)
Proprietary and Confidential Constituent Organisations . Abacus Property Group . Bendigo and Adelaide Bank Limited . Accent Group Limited . BHP Group Limited . Adelaide Brighton Ltd. Bingo Industries Ltd. Afterpay Touch Group Limited . Blackmores Limited . AGL Energy Limited . Blue Sky Alternative Investments Ltd. Alacer Gold Corp. Bluescope Steel Limited . ALS Ltd. Boral Limited . Altium Limited . Brambles Limited . Altura Mining Ltd. Bravura Solutions Limited . Alumina Ltd. Breville Group Limited . AMA Group Ltd. Brickworks Ltd. amaysim Australia Ltd. Bubs Australia Ltd. Amcor Plc . BWX Ltd. AMP Ltd. Caltex Australia Ltd. Ansell Limited . Cardno Limited . APA Group . Carnarvon Petroleum Limited . APN Industria REIT . Carsales.Com Limited . Appen Ltd. Cedar Woods Properties Limited . ARB Corp. Ltd. Centuria Capital Group . Ardent Leisure Group Ltd. Challenger Limited . Arena REIT . Champion Iron Ltd. Aristocrat Leisure Limited . Charter Hall Group . Arq Group Ltd. Charter Hall Long WALE REIT . Asaleo Care Ltd. Charter Hall Retail REIT . ASX Limited . Chorus Ltd. Atlas Arteria . CIMIC Group Ltd. AUB Group Limited . Class Ltd. (Australia) . Auckland International Airport Ltd. Clean Teq Holdings Limited . Audinate Group Ltd. Cleanaway Waste Management Ltd. Aurelia Metals Limited . Clinuvel Pharmaceuticals Limited . Aurizon Holdings Ltd. Coca-Cola Amatil Ltd. AusNet Services Ltd. Cochlear Limited . Austal Limited . Codan Limited . Australia & New Zealand Banking Group . Coles Group Ltd. Ltd. Collins Foods Limited . Australian Agricultural Co. Ltd. Commonwealth Bank of Australia . Australian Pharmaceutical Industries Ltd. Computershare Limited . Australian Scholarships Group . Cooper Energy Limited . Automotive Holdings Group Ltd. Coopers Brewery Ltd . Avanti Finance Limited . Corporate Travel Management Limited . Aventus Group . Costa Group Holdings Ltd. Aveo Group . Credit Corp. Group Ltd. Avita Medical Ltd. Cromwell Property Group . Baby Bunting Group Ltd. -
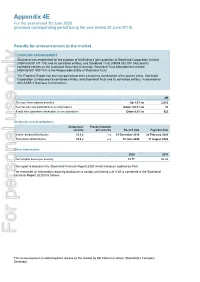
2020 (Previous Corresponding Period Being the Year Ended 30 June 2019)
Appendix 4E For the year ended 30 June 2020 (previous corresponding period being the year ended 30 June 2019) Results for announcement to the market STAPLING ARRANGEMENT Stockland was established for the purpose of facilitating a joint quotation of Stockland Corporation Limited (ABN 43 000 181 733) and its controlled entities, and Stockland Trust (ARSN 092 897 348) and its controlled entities on the Australian Securities Exchange. Stockland Trust Management Limited (ABN 86 001 900 741) is the Responsible Entity of Stockland Trust. The Financial Report has been prepared based on a business combination of the parent entity, Stockland Corporation Limited and its controlled entities, and Stockland Trust and its controlled entities, in accordance with AASB 3 Business Combinations. $M Revenue from ordinary activities Up 1.6% to 2,812 Net loss after tax attributable to securityholders Down 104.3% to 14 Funds from operations attributable to securityholders Down 8.0% to 825 Dividends and distributions Amount per Franked amount security per security Record date Payment date Interim dividend/distribution 13.5 ¢ – ¢ 31 December 2019 28 February 2020 Final dividend/distribution 10.6 ¢ – ¢ 30 June 2020 31 August 2020 Other information 2020 2019 Net tangible assets per security $3.77 $4.04 This report is based on the Stockland Financial Report 2020 which has been audited by PwC. The remainder of information requiring disclosure to comply with listing rule 4.3A is contained in the Stockland Financial Report 2020 that follows. For personal use only This announcement is authorised for release to the market by Ms Katherine Grace, Stockland’s Company Secretary. -

1. Shareholdings in Public and Private Companies (Including Holding
Form A 3 March 2020 Surname: Mclachlan Other names: Andrew State/Territory: SA Date: 3/03/2020 1. Shareholdings in public and private companies (including holding companies) indicating the name of the company or companies (Note: It is NOT necessary to declare the size or value of the shareholding) Name of company – (including holding and subsidiary companies if applicable) OATMILL HOLDINGS PTY LTD AUSTOFIX GROUP LTD VITRO SOFTWARE HOLDINGS (Designated Activity Company) ALUMINA LIMITED ANTIPODES GLOBAL INVESTMENT COMPANY LTD ANZ BANKING GROUP LIMITED AP EAGERS LIMITED ARISTOCRAT LEISURE LIMITED BHP GROUP LIMITED BORAL LIMITED CLEANAWAY WASTE MANAGEMENT LTD COMMONWEALTH BANK OF AUSTRALIA CORPORATE TRAVEL MANAGEMENT LIMITED COSTA GROUP HOLDINGS LIMITED GRAINCORP LIMITED ILUKA RESOURCES LIMITED LI LONG SHORT FUND LIMITED MACQUARIE GROUP LIMITED MINERAL RESOURCES LIMITED Form A NAOS EMERG OPP CO LTD NINE ENTERTAINMENT co HLDGS LTD OOH!MEDIA LIMITED ORIGIN ENERGY LIMITED ORORA LIMITED QBE INSURANCE GROUP LIMITED QUBE HOLDINGS LIMITED RELIANCE WORLDWIDE CORPORATION LIMITED SIMS LIMITED SONIC HEALTHCARE LIMITED SOUTH32 LIMITED S32 THE STAR ENTERTAINMENT GROUP LTD TPG TELECOM LIMITED TPM WAM LEADERS LIMITED WAM MICROCAP LIMITED WESFARMERS LIMITED WESTPAC BANKING CORPORATION WOODSIDE PETROLEUM LIMITED WORLEY LIMITED NATIONAL STORAGE REIT STPLD SEC AMCOR PLC JANUS HENDERSON GROUP PLC SPARK NEW ZEALAND LIMITED VIRGIN MONEY UK PLC ANZ BANK UNSEC NON-CUM PARADICE GLOBAL SMALL CAP FUND PLATINUM EUROPEAN FUND WESTPAC CAPITAL NOTES 2. Family and business -

Building Sustainability a Review of Company Performance in the Commercial Real Estate and Property Sector
BUILDING SUSTAINABILITY A REVIEW OF COMPANY PERFORMANCE IN THE COMMERCIAL REAL ESTATE AND PROPERTY SECTOR A CATALYST REPORT Electronic copy available at: http://ssrn.com/abstract=2745012 ABOUT CATALYST Catalyst is a not for profit policy network established in 2007. We work closely with trade unions, non-Government organisations and academics to promote social and economic equality and improved standards of corporate social responsibility. Our founding principle is to produce work that promotes good lives, good work and good communities. RESEARCH TEAM Martijn Boersma Jenni Downes (community investment) Tui Swinnen CONTRIBUTING AUTHORS Martijn Boersma Jo-anne Schofield Tui Swinnen December 2013 Catalyst Australia Incorporated Suite 109, 4 Goulburn Street, Sydney Tel: +61 (0) 2 8090 1177 www.catalyst.org.au @CatalytAus Electronic copy available at: http://ssrn.com/abstract=2745012 1. EXECUTIVE SUMMARY The commercial real estate and property sector is a vital part of the Australian economy. Compared to global peers, property companies in Australia and New Zealand are considered to be at the front of the pack in terms of acknowledging, measuring and managing Environment, Social and Governance (ESG) risks (also referred to as sustainability risks). This research report looks at performance of the sector, utilising several sustainability indicators developed by Catalyst Australia in 2013 to rate company reporting and performance. These cover gender equality, environmental impact, labour standards, supply chains, community investment and sustainability engagement. The results of this review are presented visually in the Catalyst Property Sector Sustainability Dashboard and discussed in this report. The 19 commercial real estate and property companies comprising the sample are listed on the Australian Securities Exchange (ASX) 200 index and are companies classified by the Global Industry Classification Standard as belonging to the ‘real estate’ industry group. -

Ngs Super Portfolio Holdings Disclosure
NGS SUPER PORTFOLIO HOLDINGS DISCLOSURE DEFENSIVE - ACCUMULATION Effective date: 31 DEC 2020 AUSTRALIAN SHARES A2 MILK CO LTD ABACUS PROPERTY GROUP REIT ACCENT GROUP LTD ADAIRS LTD ADBRI LTD AFTERPAY LTD AGL ENERGY LTD AINSWORTH GAME TECHNOLOGY LTD ALACER GOLD CORP ALE PROPERTY GROUP REIT ALS LTD ALTIUM LTD ALUMINA LTD AMA GROUP LTD AMCOR PLC AMP LTD ANSELL LTD APA GROUP STAPLED SECURITY APPEN LTD ARB CORP LTD ARISTOCRAT LEISURE LTD ASALEO CARE LTD ASX LTD ATLAS ARTERIA STAPLED SECURITY AUB GROUP LTD AUCKLAND INTL AIRPORT LTD AURELIA METALS LTD AUSNET SERVICES AUSSIE BROADBAND Issued by NGS Super Pty Limited ABN 46 003 491 487 AFSL No 233 154 the trustee of NGS Super ABN 73 549 180 515 ngssuper.com.au 1300 133 177 NGS SUPER – PORTFOLIO HOLDINGS DISCLOSURE 1 DEFENSIVE - ACCUMULATION Effective date: 31 DEC 2020 AUST AND NZ BANKING GROUP AUSTAL LTD AUSTRALIAN FINANCE GROUP LTD AUSTRALIAN PHARMA INDUS LTD AUSTRALIAN VINTAGE LTD AVENTUS GROUP REIT AVITA MEDICAL INC BABY BUNTING GROUP LTD BANK OF QUEENSLAND LTD BAPCOR LTD BEACH ENERGY LTD BEACON LIGHTING GROUP LTD BEGA CHEESE LTD BENDIGO AND ADELAIDE BANK BHP GROUP LTD BINGO INDUSTRIES LTD BLACKMORES LTD BLUESCOPE STEEL LTD BORAL LTD BRAMBLES LTD BRAVURA SOLUTIONS LTD BREVILLE GROUP LTD BRICKWORKS LTD BWP TRUST REIT CALTEX AUSTRALIA LTD CAPITOL HEALTH LTD CAPRAL LTD CAPRICORN METALS LTD CARDNO LTD CARNARVON PETROLEUM LTD CARSALES.COM LTD CASH CEDAR WOODS PROPERTIES LTD CENTURIA INDUSTRIAL REIT CENTURIA METROPOLITAN REIT CHALLENGER LTD CHAMPION IRON LTD CHARTER HALL GROUP REIT CHARTER HALL LONG