User's Guide to NIST Biometric Image Software (NBIS)
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Image Data Martin Spitaler
Imperial College London MICROSCOPY DAY 2011: Understanding and handling image data Martin Spitaler Understanding Images (Martin Spitaler) • What’s in an image file: •Pixel data • metadata • Getting the data into the file: Image acquisition • Image file formats • Using images: Image visualisation and presentation Handling Images (Chris Tomlinson & Mark Woodbridge) • Omero image database • Xperimenter experiment annotation system What’s in an image file: Pixel data Pixel (or binary) data with information about the sample • One or more frames of pixels (XY, XZ) • Each frame typically consists of a two-dimensional array of pixel values • Pixel values can be: • light intensity • array of intensities (PALM, STORM) • array of fluorescence lifetimes • in the future: correlated data, e.g. exposure times (CMOS), mass spectra, … • Frames are stacked in one or more specific orders: • Channel (colour, lifetime, …) •Z stack •Time • XY position in a plate MICROSCOPY DAY 2011: Understanding & handling image data Martin Spitaler What’s in an image file: Meta data Meta data make sense of the pixel information • Image type (TIFF, LSM, CXD, …) • pixel dimensions (size, time point, focus position) • Hardware settings: •objective lens • excitation light source: • type (laser, lamp) •intensity • excitation and dichroic filters •… • emission settings: • emission filters • detector gain and offset • pinhole size • sampling speed / exposure time •… MICROSCOPY DAY 2011: Understanding & handling image data Martin Spitaler What’s NOT in an image file: Experimental -

Image File Formats
Glossary Image File Formats Glossary of File Formats and Imaging Terminology JPEG: stands for “Joint Photographic Experts Group.” It’s the most common format for storing digital camera photographs or scanned images. It is a “lossy” compression format, meaning it shrinks the files by discarding the information that the human eye cannot perceive. JPEGs are widely supported and used on the web, for example when sharing images through email. They have several compression level options. TIFF: stands for “Tagged Image File Format” and is one of the most widely supported file formats for storing bit-mapped images on personal computers (both PCs and Macintosh computers). TIFF files can be any resolution, and can be black and white, gray-scaled, or color. Used for high-quality images (lossless compression). TIFF format is widely supported by image-manipulation applications such as Photoshop by Adobe. GIF(F): stands for “Graphics Interchange Format.” A bit-mapped file format used for graphics as opposed to photographic images. GIF supports 8-bit color (maximum of 256 colors, compared to JPEGs 16 million colors.) They are widely used on the Web because the files compress well. GIFs include a color table including the most representative 256 colors used. Not recommended for files with a lot of color shading! PNG: stands for “Portable Network Graphics.” PNG files contain a bitmap of indexed colors and use lossless compression. They are similar to GIF files, but differ in that they do not have copyright limitations. PNG files are typically used to store graphics for web images and also have the ability to preserve transparency. -
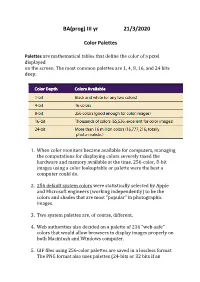
BA(Prog) III Yr 21/3/2020
BA(prog) III yr 21/3/2020 Color Palettes Palettes are mathematical tables that define the color of a pixel displayed on the screen. The most common palettes are 1, 4, 8, 16, and 24 bits deep: 1. When color monitors became available for computers, managing the computations for displaying colors severely taxed the hardware and memory available at the time. 256-color, 8-bit images using a color lookuptable or palette were the best a computer could do. 2. 256 default system colors were statistically selected by Apple and Microsoft engineers (working independently) to be the colors and shades that are most “popular” in photographic images. 3. Two system palettes are, of course, different. 4. Web authorities also decided on a palette of 216 “web-safe” colors that would allow browsers to display images properly on both Macintosh and Windows computer. 5. GIF files using 256-color palettes are saved in a lossless format. The PNG format also uses palettes (24-bits or 32 bits if an “alpha” mask is included for transparency), and is lossless. It was developed for the Internet(it supports only the RGB color space) to expand GIF’s limited 256 colors to millions of colors. 6. In 24-bit color systems, your computer works with three channels of 256 discrete shades of each color (red, green, and blue) represented as the three axes of a cube. This allows a total of 16,777,216 colors (256 256 256). Image File Formats Most applications on any operating system can manage JPEG, GIF, PNG, and TIFF image formats. -

Digital Preservation Guidance Note: Graphics File Formats
Digital Preservation Guidance Note: 4 Graphics File Formats Digital Preservation Guidance Note 4: Graphics file formats Document Control Author: Adrian Brown, Head of Digital Preservation Research Document Reference: DPGN-04 Issue: 2 Issue Date: August 2008 ©THE NATIONAL ARCHIVES 2008 Page 2 of 15 Digital Preservation Guidance Note 4: Graphics file formats Contents 1 INTRODUCTION .....................................................................................................................4 2 TYPES OF GRAPHICS FORMAT........................................................................................4 2.1 Raster Graphics ...............................................................................................................4 2.1.1 Colour Depth ............................................................................................................5 2.1.2 Colour Spaces and Palettes ..................................................................................5 2.1.3 Transparency............................................................................................................6 2.1.4 Interlacing..................................................................................................................6 2.1.5 Compression ............................................................................................................7 2.2 Vector Graphics ...............................................................................................................7 2.3 Metafiles............................................................................................................................7 -

Guide to Image File Formats
Guide to Image File Formats JPEG WebP PNG-8 GIF • Supported on all browsers • NOT supported on Safari • Limited to 256 colors • Supports animation and • No support for animation • Limited animation support • No support for animation transparency or transparency • Uses Lossy compression • Supports transparency • Produces larger file than = = PNG-8 • Best for photography & that also supports • Best for screenshots or large hero images transparency logos with limited color • For animation, WebM or • Uses lossy compression • 25-34% smaller than JPEG palette MP4 produce smaller file WebP Lossless PNG-24 LOSSY VS. LOSSLESS • NOT supported on Safari • Supports transparency • Limited animation support • Produces images with COMPRESSION • Best for reserving full millions of colors without With lossy compression, image detail = loss of detail some of your data will be • 26% smaller than • 3x larger image file than lost forever. Lossy image comparable PNGs compressed JPEG compression permanently removes image data and degrades the image in the WebP produces smaller PNG-32 process. file size than JPEG & SVG PNG equivalent • Supported on all browsers This is not as bad as it • Uses an extra 8-bit alpha sounds, as some detail • Supported on all browsers channel for advanced might not be perceivable transparency capabilities to the human eye. • XML-based markup language used to describe geometric • Useful for creating Lossless compression, shapes and positions in image transparency gradients by contrast, preserves • Produces vector graphics that data so nothing is lost. can be animated with CSS = FUNCTIONAL Lossless algorithms keep • Not allowed by default SIMILARITIES all the necessary data in WordPress due to to recreate the image security risks exactly. -

GPU Implementation of JPEG2000 for Hyperspectral Image Compression
GPU Implementation of JPEG2000 for Hyperspectral Image Compression Milosz Ciznickia, Krzysztof Kurowskia and bAntonio Plaza aPoznan Supercomputing and Networking Center Noskowskiego 10, 61-704 Poznan, Poland. bHyperspectral Computing Laboratory, Department of Technology of Computers and Communications, University of Extremadura, Avda. de la Universidad s/n. 10071 C´aceres, Spain ABSTRACT Hyperspectral image compression has received considerable interest in recent years due to the enormous data volumes collected by imaging spectrometers for Earth Observation. JPEG2000 is an important technique for data compression which has been successfully used in the context of hyperspectral image compression, either in lossless and lossy fashion. Due to the increasing spatial, spectral and temporal resolution of remotely sensed hyperspectral data sets, fast (onboard) compression of hyperspectral data is becoming a very important and challenging objective, with the potential to reduce the limitations in the downlink connection between the Earth Observation platform and the receiving ground stations on Earth. For this purpose, implementation of hyperspectral image compression algorithms on specialized hardware devices are currently being investigated. In this paper, we develop an implementation of the JPEG2000 compression standard in commodity graphics processing units (GPUs). These hardware accelerators are characterized by their low cost and weight, and can bridge the gap towards on-board processing of remotely sensed hyperspectral data. Specifically, we develop GPU implementations of the lossless and lossy modes of JPEG2000. For the lossy mode, we investigate the utility of the compressed hyperspectral images for different compression ratios, using a standard technique for hyperspectral data exploitation such as spectral unmixing. In all cases, we investigate the speedups that can be gained by using the GPU implementations with regards to the serial implementations. -

Various Raster and Vector Image File Formats
ISSN (Online) 2278-1021 ISSN (Print) 2319-5940 International Journal of Advanced Research in Computer and Communication Engineering Vol. 4, Issue 3, March 2015 Various Raster and Vector Image File Formats Sakshica1, Dr. Kusum Gupta2 Banasthali Vidyapith, Jaipur campus (Jaipur)1,2 Abstract: Image File Format is one of the standardized ways of storing digital images, with a large number of image file formats available it would be very difficult and challenging for the user to select appropriate image format for storing the images. Choosing the proper image file format according to the demand of the project or according to a specific parameter is of vital importance. Therefore, in this paper we provide a brief review on most common and different image file formats in order to ease the user to choose appropriate file formats while working with files. Keywords: Graphics Interchange Format (GIF), Joint Photographic Expert Group(JPEG), Portable Network Graphics(PNG), Tagged Image File Format(TIFF), Encapsulated PostScript (ESP), Portable Document Format (PDF), Adobe Illustrator (AI), Drawing eXchange Format (DXF). I. INTRODUCTION Images are an important part of today's digital world. File A. Resolution formats are essential when it comes to compatibility and Raster graphics depend upon having a resolution, which is storing images. An image file format is a standard way to counted in .dpi (dots per inch).The lower the resolution the organize and store image data. It defines how the data is smaller the file size [6]. arranged and the type of compression (if any) to be used. Low-resolution raster graphics would normally be set to There are several dozens of different image file formats 72 dpi and are used very often for web sites and presenta- [1]. -

High Efficiency Image File Format Implementation
LASSE HEIKKILÄ HIGH EFFICIENCY IMAGE FILE FORMAT IMPLEMENTATION Master of Science thesis Examiner: Prof. Petri Ihantola Examiner and topic approved by the Faculty Council of the Faculty of Computing and Electrical Engineering on 4th of May 2016 i ABSTRACT LASSE HEIKKILÄ: High Efficiency Image File Format implementation Tampere University of Technology Master of Science thesis, 49 pages, 1 Appendix page June 2016 Master’s Degree Programme in Electrical Engineering Technology Major: Embedded systems Examiner: Prof. Petri Ihantola Keywords: High Efficiency Image File Format, HEIF, HEVC During recent years, methods used to encode video have been developing quickly. However, image file formats commonly used for saving still images, such as PNG and JPEG, are originating from the 1990s. Therefore it is often possible to get better image quality and smaller file sizes, when photographs are compressed with modern video compression techniques. The High Efficiency Video Coding (HEVC) standard was finalized in 2013, and in the same year work for utilizing it for still image storage started. The resulting High Efficiency Image File Format (HEIF) standard offers a competitive image data compression ratio, and several other features such as support for image sequences and non-destructive editing. During this thesis work, writer and reader programs for handling HEIF files were developed. Together with an HEVC encoder the writer can create HEIF compliant files. By utilizing the reader and an HEVC decoder, an HEIF player program can then present images from HEIF files without the most detailed knowledge about their low-level structure. To make development work easier, and improve the extensibility and maintainability of the programs, code correctness and simplicity were given special attention. -

Image File Format Standards
Image File Format Standards Betsy Fanning 03/29/2006 TIFF, JPEG, and PDF. Different formats for different jobs. When one thinks of enterprise content management (ECM), one tends to focus more on the management of content in an organization. As AIIM defines ECM, there is a whole lot more to it that includes the technologies used to capture, manage, store, preserve, and deliver content and documents. Even though a majority of the information organizations handle today is born digitally and stays that way, a lot of information still enters organizations as paper. While paper continues to be useful in business, digital information enables an organization to respond more rapidly to changing circumstances. In the late 1980s, the buzz in the business world circulated around digital document imaging. It was the point solution many organizations implemented to gain some level of control over their documents. As recently as 10 years ago (according to AIIM research), industry solutions were typically departmental in scope with a particular business focus. As our survey indicates, 82% of end users now see ECM technologies— imaging is one—as a core element in their overall IT infrastructure.* Today, organizations don’t think twice about imaging as imaging technology is integrated in most products. Image viewers are prevalent. Image file format standards have helped move along the widespread adoption of imaging technology. Image file formats provide a standardized method of organizing and storing image data. A scanned document or image consists of picture elements, or pixels, that represent the brightness and color of the information on the page. -

Web Development & Interactive Media Instructor
Web Development & Interactive Media Instructor: Tony McEachern, Assistant Professor What is an Interactivity? Interactivity is the relationship between media users and the medium that allows each individual user to influence and react to the media source. The following are some examples ways users can interact with online media: • Text Links, • Graphic Buttons, • Email, • Online Forms • Web Logs (Blogs) What is an Interface? A graphical user interface (GUI or Goo–ee) is the 1st point of contact with the website by the site visitor. GUI uses icons and symbols to establish visual representation with user interactivity. Images are used to instead of simple text to communicate functions to the site user. What is an Interface? Typical types of GUI: • The Home Page • Each Front Page • All interior pages What is Navigation? Term navigation refers the act of moving from location to location within a web site, or between web sites. Navigation is accomplished by clicking on text links or navigation buttons. Navigation: The Path of Least Resistance Whether accomplished through text links or graphic buttons, Navigation must be intuitive to the user. CAUTION: An over-fancifully designed interface can make it difficult for users to find their desired information on your website. Be sure to use clear and consistent navigational elements. The 3 Degrees of Navigation? There are 3 main types or degrees of navigation within a website: • Global – allows the site visitor to move between the main sections of a particular site. Global Navigation should be present on every page of the site. • Parallel – allows the visitor to move in a parallel manner between the subsections of a particular site section. -

Image Compression: JPEG and JPEG 2000 Abstract
Image Compression: JPEG and JPEG 2000 Maria Loginova Jie (Kerry) Zhan Abstract How to save an image file efficiently without losing the quality? JPEG has been one of the answers for quite some years. JPEG stands for Joint Photographic Experts Group, and these are the people who developed the standards of JPEG image compression. Over the past few years, JPEG has been a quite popular format for images, especially when working with the booming Internet. Using DCT (Discrete Cosine Transform) algorithms and related quantization method, JPEG can compress the original image file to a relative reasonable size without losing much detail. In this report, we will be exploring, with simulations and coding, the technical details of JPEG. As time passed by, JPEG is gradually becoming insufficient in some applications due to its “block effects.” Therefore, there is a need to develop new standards for better performance in image compression. That’s original goal of JPEG 2000, that is, to represent an image using even less bytes while not losing the details and also not creating “artifacts” like JPEG did. So, followed by discussion of JPEG, there will be a description part for this new image compression standard. Project Plan Week 1 (Sun, Feb 2 - Sun, Feb 9) Primary Resp. Status Initial Look on Image Coding Maria/Kerry Done Search for Relevant Literature Maria/Kerry Done Overall Project Plan Decisions and Project Plan Report Writing Maria/Kerry Done Weeks 2,3 (Sun, Feb 9 - Sun, Feb 23) Primary Resp. Status Overview of DCT and Quantization and their use in JPEG coding Maria Done Overview of wavelets and their use in JPEG2000 coding Kerry Done Weeks 4,5 (Sun, Feb 23 - Sun, March 9) Primary Resp. -

Glossary Image File Formats
Glossary Image File Formats Glossary of File Formats and Imaging Terminology JPEG: stands for “Joint Photographic Experts Group.” It’s the most common format for storing digital camera photographs or scanned images. It is a “lossy” compression format, meaning it shrinks the files by discarding the information that the human eye cannot perceive. JPEGS are widely supported and used on the web and sharing images through email, and have several compression level options. TIFF: stands for “Tagged Image File Format” and is one of the most widely supported file formats for storing bit-mapped images on personal computers (both PCs and Macintosh computers). TIFF files can be any resolution, and can be black and white, gray-scaled, or color. Used for high-quality images (loss-less compression). TIFF format is widely supported by image-manipulation applications such as Photoshop by Adobe. GIF(F): stands for “Graphics Interchange Format.” A bit-mapped file format used for graphics as opposed to photographic images. GIF supports 8-bit color (maximum of 256 colors, compared to Jpegs 16 million colors.) It’s widely used on the Web because the files compress well. GIFs include a color table that includes the most representative 256 colors used. Not recommended for files with a lot of color shading! PDF: stands for “Portable Document Format.” PDF files are most appropriately used to encode the exact look of a document in a device-independent way. While the PDF format can describe very simple one page documents, it may also be used for many pages, complex documents that use a variety of different fonts, graphics, colors, and images.