GPU Implementation of JPEG2000 for Hyperspectral Image Compression
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Exploring the .BMP File Format
Exploring the .BMP File Format Don Lancaster Synergetics, Box 809, Thatcher, AZ 85552 copyright c2003 as GuruGram #14 http://www.tinaja.com [email protected] (928) 428-4073 The .BMP image standard is used by Windows and elsewhere to represent graphics images in any of several different display and compression options. The .BMP advantages are that each pixel is usually independently available for any alteration or modification. And that repeated use does not normally degrade the image. Because lossy compression is not used. Its main disadvantage is that file sizes are usually horrendous compared to JPEG, fractal, GIF, or other lossy compression schemes. A comparison of popular image standards can be found here. I’ve long been using the .BMP format for my eBay and my other phototography, scanning, and post processing. I firmly believe that… All photography, scanning, and all image post-processing should always be done using .BMP or a similar non-lossy format. Only after all post-processing is complete should JPEG or another compressed distribution format be chosen. Some current examples of my .BMP work now do include the IMAGIMAG.PDF post-processing tutorial, the Bitmap Typewriterthat generates fully anti-aliased small fonts, the Aerial Photo Combiner, and similar utilities and tutorials found on our Fonts & Images, PostScript, and on our Acrobat library pages. A few projects of current interest involving .BMP files include true view camera swings and tilts for a digital camera, distortion correction, dodging & burning, preventing white punchthrough on knockouts, and emphasis vignetting. Mainly applied to uncompressed RGBX 24-bit color .BMP files. -

TS 101 499 V2.2.1 (2008-07) Technical Specification
ETSI TS 101 499 V2.2.1 (2008-07) Technical Specification Digital Audio Broadcasting (DAB); MOT SlideShow; User Application Specification European Broadcasting Union Union Européenne de Radio-Télévision EBU·UER 2 ETSI TS 101 499 V2.2.1 (2008-07) Reference RTS/JTC-DAB-57 Keywords audio, broadcasting, DAB, digital, PAD ETSI 650 Route des Lucioles F-06921 Sophia Antipolis Cedex - FRANCE Tel.: +33 4 92 94 42 00 Fax: +33 4 93 65 47 16 Siret N° 348 623 562 00017 - NAF 742 C Association à but non lucratif enregistrée à la Sous-Préfecture de Grasse (06) N° 7803/88 Important notice Individual copies of the present document can be downloaded from: http://www.etsi.org The present document may be made available in more than one electronic version or in print. In any case of existing or perceived difference in contents between such versions, the reference version is the Portable Document Format (PDF). In case of dispute, the reference shall be the printing on ETSI printers of the PDF version kept on a specific network drive within ETSI Secretariat. Users of the present document should be aware that the document may be subject to revision or change of status. Information on the current status of this and other ETSI documents is available at http://portal.etsi.org/tb/status/status.asp If you find errors in the present document, please send your comment to one of the following services: http://portal.etsi.org/chaircor/ETSI_support.asp Copyright Notification No part may be reproduced except as authorized by written permission. -
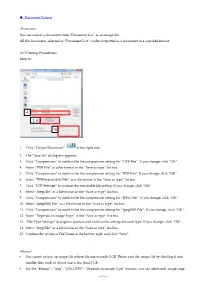
51 Document Output
◆ Document Output <Function> You can output a document from “Document List” as an image file. All the documents selected in “Document List” can be outputted as a document in a specified format. <ICP Setting Procedures> Refer to 4 3, 6 15 1. Click “Output Document” at the right side. 2. The “Save As” dialog box appears. 3. Click “Compression” to confirm the file compression setting for “TIFF File”. If you change, click “OK”. 4. Select “PDF File” as a file format in the “Save as type” list box. 5. Click “Compression” to confirm the file compression setting for “PDF File”. If you change, click “OK”. 6. Select “PDF(Searchable) File” as a file format in the “Save as type” list box. 7. Click “OCR Settings” to confirm the searchable file setting. If you change, click “OK”. 8. Select “Jpeg File” as a file format in the “Save as type” list box. 9. Click “Compression” to confirm the file compression setting for “JPEG File”. If you change, click “OK”. 10. Select “Jpeg2000 File” as a file format in the “Save as type” list box. 11. Click “Compression” to confirm the file compression setting for “Jpeg2000 File”. If you change, click “OK”. 12. Select “Depends on Image Type” in the “Save as type” list box. 13. “File Type Settings” dialog box appears and confirm the settings for each type. If you change, click “OK”. 14. Select “Jpeg File” as a file format in the “Save as type” list box. 15. Confirm the setting of File Name at the bottom right and click “Save”. -

Effects of JPEG2000 on the Information and Geometry Content of Aerial Photo Compression
03-082.qxd 1/11/05 5:17 PM Page 157 Effects of JPEG2000 on the Information and Geometry Content of Aerial Photo Compression Jung-Kuan Liu, Houn-Chien Wu, and Tian-Yuan Shih Abstract evaluated the effects of compression on geometric accuracy. Li The standardization effort of the next ISO standard for et al., (2002) indicated that when compression ratios are less compression of the still image, JPEG2000, has recently than a factor of 10, the compressed image is near-lossless with reached International Standard (IS) status. This wavelet- JPEG. In other words, the visual quality of JPEG compressed based standard outperforms the Discrete Cosine Transform images remains excellent and the accuracy of manual image (DCT) based JPEG in terms of compression ratio, as well mensuration is, essentially, not influenced. Paola et al. (1995) as, quality. In this study, the performance of JPEG2000 is and Schmanske and Loew (2001) concentrated on the classifi- evaluated for aerial image compressions. Different com- cation accuracies of compressed images. Paola et al. (1995) pression ratios are applied to scanned aerial photos at the revealed that high quality classifications could be obtained for 1:5 000 scale. Both the image quality measurements and the images with JPEG compression ratios approaching 10:1 or even accuracy of photogrammetric point determination aspects higher. The classification result retains its overall appearance, are examined. The evaluation of image quality is based but the smoothing effect of high compression tends to elimi- on visual analysis of the objects in the scene and on the nate much of the pixel-to-pixel detail. -

Image Data Martin Spitaler
Imperial College London MICROSCOPY DAY 2011: Understanding and handling image data Martin Spitaler Understanding Images (Martin Spitaler) • What’s in an image file: •Pixel data • metadata • Getting the data into the file: Image acquisition • Image file formats • Using images: Image visualisation and presentation Handling Images (Chris Tomlinson & Mark Woodbridge) • Omero image database • Xperimenter experiment annotation system What’s in an image file: Pixel data Pixel (or binary) data with information about the sample • One or more frames of pixels (XY, XZ) • Each frame typically consists of a two-dimensional array of pixel values • Pixel values can be: • light intensity • array of intensities (PALM, STORM) • array of fluorescence lifetimes • in the future: correlated data, e.g. exposure times (CMOS), mass spectra, … • Frames are stacked in one or more specific orders: • Channel (colour, lifetime, …) •Z stack •Time • XY position in a plate MICROSCOPY DAY 2011: Understanding & handling image data Martin Spitaler What’s in an image file: Meta data Meta data make sense of the pixel information • Image type (TIFF, LSM, CXD, …) • pixel dimensions (size, time point, focus position) • Hardware settings: •objective lens • excitation light source: • type (laser, lamp) •intensity • excitation and dichroic filters •… • emission settings: • emission filters • detector gain and offset • pinhole size • sampling speed / exposure time •… MICROSCOPY DAY 2011: Understanding & handling image data Martin Spitaler What’s NOT in an image file: Experimental -

Image Formats
Image Formats Ioannis Rekleitis Many different file formats • JPEG/JFIF • Exif • JPEG 2000 • BMP • GIF • WebP • PNG • HDR raster formats • TIFF • HEIF • PPM, PGM, PBM, • BAT and PNM • BPG CSCE 590: Introduction to Image Processing https://en.wikipedia.org/wiki/Image_file_formats 2 Many different file formats • JPEG/JFIF (Joint Photographic Experts Group) is a lossy compression method; JPEG- compressed images are usually stored in the JFIF (JPEG File Interchange Format) >ile format. The JPEG/JFIF >ilename extension is JPG or JPEG. Nearly every digital camera can save images in the JPEG/JFIF format, which supports eight-bit grayscale images and 24-bit color images (eight bits each for red, green, and blue). JPEG applies lossy compression to images, which can result in a signi>icant reduction of the >ile size. Applications can determine the degree of compression to apply, and the amount of compression affects the visual quality of the result. When not too great, the compression does not noticeably affect or detract from the image's quality, but JPEG iles suffer generational degradation when repeatedly edited and saved. (JPEG also provides lossless image storage, but the lossless version is not widely supported.) • JPEG 2000 is a compression standard enabling both lossless and lossy storage. The compression methods used are different from the ones in standard JFIF/JPEG; they improve quality and compression ratios, but also require more computational power to process. JPEG 2000 also adds features that are missing in JPEG. It is not nearly as common as JPEG, but it is used currently in professional movie editing and distribution (some digital cinemas, for example, use JPEG 2000 for individual movie frames). -

About Graphics/Digital Images
About Graphics/Digital Images Digital images are found in lots of file formats (types) that are used for various reasons. I liken the file formats to flavors of ice-cream, which you might or might not choose to consume on any given day. One day chocolate is more important than mint; another day you might use vanilla, and on another day you might decide to combine more than one flavor in the same bowl. Likewise, you might choose one type of graphic file for a particular project, but it might be completely inappropriate for another project. What works well for display purposes (keeping it on the computer, or for publication to the internet) might not print well. Something that prints well might be too big a file to post to the internet, or may make your program run too slowly. Also, some authoring programs (like Boardmaker or Classroom Suite) might be written to only understand certain types of image files. Some file types are more common than others, and are more likely to be recognized by the “parent” program (the one you use to display, edit or print your image). Whatever type you pick ultimately depends on how you plan to use the image. The more technical definitions provided below are taken from the glossary found at http://www.photoshopelementsuser.com/glossary.php?letter=B The additional comments I have added, and hopefully let you know why you would care about any of this, anyway. The two biggest types of images I describe here fall loosely into two categories: vector images and bitmap images. -

User's Guide to NIST Biometric Image Software (NBIS)
NISTIR 7392 2007 User's Guide to NIST Biometric Image Software (NBIS) Craig I. Watson ([email protected]) Michael D. Garris ([email protected]) Elham Tabassi ([email protected]) Charles L. Wilson ([email protected]) R. Michael McCabe ([email protected]) Stanley Janet ([email protected]) Kenneth Ko ([email protected]) National Institute of Standards and Technology Bldg. 225, Rm. A216 100 Bureau Drive, Mail Stop 8940 Gaithersburg, MD 20899-8940 i ACKNOWLEDGEMENTS We would like to acknowledge the Federal Bureau of Investigation and the Department of Homeland Security who provided funding and resources in conjunction with NIST to support the development of this fingerprint image software. NOTE TO READER This document provides guidance on how the NIST Biometric Image Software (NBIS) non- export controlled packages are installed and executed. Its content and format is one of user's guide and reference manual. Some algorithmic overview is provided, but more details can be found in the cited references. The Table of Contents provides the reader a map into the document, and the hyperlinks in the electronic version enable the reader to effectively navigate the document and locate desired information. These hyperlinks are unavailable when using a paper copy of the document. Any updates to this software will be posted NIST Image Group’s Open Source Sever (NIGOS). ii TABLE OF CONTENTS 1. INTRODUCTION ...................................................................................................................................................... 1 2. -

Image File Formats
Glossary Image File Formats Glossary of File Formats and Imaging Terminology JPEG: stands for “Joint Photographic Experts Group.” It’s the most common format for storing digital camera photographs or scanned images. It is a “lossy” compression format, meaning it shrinks the files by discarding the information that the human eye cannot perceive. JPEGs are widely supported and used on the web, for example when sharing images through email. They have several compression level options. TIFF: stands for “Tagged Image File Format” and is one of the most widely supported file formats for storing bit-mapped images on personal computers (both PCs and Macintosh computers). TIFF files can be any resolution, and can be black and white, gray-scaled, or color. Used for high-quality images (lossless compression). TIFF format is widely supported by image-manipulation applications such as Photoshop by Adobe. GIF(F): stands for “Graphics Interchange Format.” A bit-mapped file format used for graphics as opposed to photographic images. GIF supports 8-bit color (maximum of 256 colors, compared to JPEGs 16 million colors.) They are widely used on the Web because the files compress well. GIFs include a color table including the most representative 256 colors used. Not recommended for files with a lot of color shading! PNG: stands for “Portable Network Graphics.” PNG files contain a bitmap of indexed colors and use lossless compression. They are similar to GIF files, but differ in that they do not have copyright limitations. PNG files are typically used to store graphics for web images and also have the ability to preserve transparency. -

Package 'Tiff'
Package ‘tiff’ March 31, 2021 Version 0.1-8 Title Read and Write TIFF Images Author Simon Urbanek <[email protected]> [aut, cre], Kent Johnson <[email protected]> [ctb] Maintainer Simon Urbanek <[email protected]> Depends R (>= 2.9.0) Description Functions to read, write and display bitmap images stored in the TIFF for- mat. It can read and write both files and in-memory raw vectors, including native image repre- sentation. License GPL-2 | GPL-3 SystemRequirements tiff and jpeg libraries URL https://www.rforge.net/tiff/ NeedsCompilation yes Repository CRAN Date/Publication 2021-03-31 15:10:02 UTC R topics documented: readTIFF . .1 writeTIFF . .4 Index 6 readTIFF Read a bitmap image stored in the TIFF format Description Reads an image from a TIFF file/content into a raster array. 1 2 readTIFF Usage readTIFF(source, native = FALSE, all = FALSE, convert = FALSE, info = FALSE, indexed = FALSE, as.is = FALSE, payload = TRUE) Arguments source Either name of the file to read from or a raw vector representing the TIFF file content. native logical, determines the image representation - if FALSE (the default) then the result is an array, if TRUE then the result is a native raster representation (suitable for plotting). all logical scalar or integer vector. TIFF files can contain more than one image. If all=TRUE then all images are returned in a list of images. If all is a vector, it gives the (1-based) indices of images to return. Otherwise only the first image is returned. convert logical, if TRUE then first convert the image into 8-bit RGBA samples and then to an array, see below for details. -
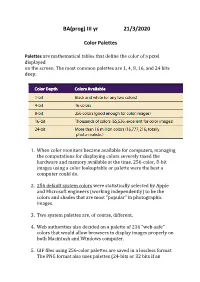
BA(Prog) III Yr 21/3/2020
BA(prog) III yr 21/3/2020 Color Palettes Palettes are mathematical tables that define the color of a pixel displayed on the screen. The most common palettes are 1, 4, 8, 16, and 24 bits deep: 1. When color monitors became available for computers, managing the computations for displaying colors severely taxed the hardware and memory available at the time. 256-color, 8-bit images using a color lookuptable or palette were the best a computer could do. 2. 256 default system colors were statistically selected by Apple and Microsoft engineers (working independently) to be the colors and shades that are most “popular” in photographic images. 3. Two system palettes are, of course, different. 4. Web authorities also decided on a palette of 216 “web-safe” colors that would allow browsers to display images properly on both Macintosh and Windows computer. 5. GIF files using 256-color palettes are saved in a lossless format. The PNG format also uses palettes (24-bits or 32 bits if an “alpha” mask is included for transparency), and is lossless. It was developed for the Internet(it supports only the RGB color space) to expand GIF’s limited 256 colors to millions of colors. 6. In 24-bit color systems, your computer works with three channels of 256 discrete shades of each color (red, green, and blue) represented as the three axes of a cube. This allows a total of 16,777,216 colors (256 256 256). Image File Formats Most applications on any operating system can manage JPEG, GIF, PNG, and TIFF image formats. -

JP2 Format Preservation Assessment
Digital Date: 03/09/2015 Preservation Assessment: Preservation JP2 Format Team Version: 1.3 Document History Date Version Author(s) Circulation 10/12/2014 1.1 Paul Wheatley, Peter May, External Maureen Pennock 23/02/2015 1.2 Peter May External 03/09/2015 1.3 Simon Whibley External British Library Digital Preservation Team [email protected] This work is licensed under the Creative Commons Attribution 4.0 International License. Page 1 of 10 Digital Date: 03/09/2015 Preservation Assessment: Preservation JP2 Format Team Version: 1.3 1. Introduction This document provides a high level, non-collection specific assessment of the JP2 file format with regard to preservation risks and the practicalities of preserving data in this format. This format assessment is one of a series of assessments carried out by the British Library’s Digital Preservation Team. An explanation of criteria used in this assessment is provided in italics below each heading. 1.1 Scope This document will primarily focus on JP2 (JPEG2000 Part 1, core coding system) defined by ISO/IEC 15444-1:2000, but will reference other parts of the JPEG2000 standard(s) where context is necessary. A separate (or extended) assessment for JPX1 and JPM2, and indeed Motion JPEG2000 (Part 3), may be necessary depending on British Library needs. Issues of both preserving deposited JP2s and preserving JP2s created by the British Library as part of digitisation activities will be considered. Note that this assessment considers format issues only, and does not explore other factors essential to a preservation planning exercise, such as collection specific characteristics, that should always be considered before implementing preservation actions.