Temtum™ & the Temporal Blockchain
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Galaxy Digital Announces Launch of Decentralized Finance (Defi) Index Fund
NEWS RELEASE Galaxy Digital Announces Launch of Decentralized Finance (DeFi) Index Fund 8/19/2021 The Fund seeks to track the newly launched Bloomberg Galaxy DeFi Index NEW YORK, Aug. 19, 2021 /CNW/ - Galaxy Digital Holdings Ltd. (TSX: GLXY) ("Galaxy Digital" or the "Company"), the pre-eminent global provider of blockchain and cryptocurrency nancial services for institutions, today announced the launch of the Galaxy DeFi Index Fund, a passively managed fund that seeks to track the performance of the newly-launched Bloomberg Galaxy DeFi Index (ticker: DEFI). As one of the fastest growing sectors in crypto, DeFi brings nancial services on-chain, enabling participants to borrow, lend, and exchange assets on blockchains governed by smart contracts instead of through centralized intermediaries. DeFi is distinct because it expands the use of blockchain from simple value transfer to more complex nancial use cases. At the time of writing, users have deposited over $80.7 billion worth of crypto into DeFi smart contracts up from $4.7 billion one year ago today. The Galaxy DeFi Index Fund seeks to provide institutional investors access to returns based on the performance of DeFi through a simple, secure vehicle with exposure to the largest, most liquid portion of the decentralized nance crypto market, one of the fastest-growing segments of the crypto ecosystem. The fund is seeded by NZ Funds, a wealth management rm that manages over $2bn of New Zealanders' savings. "Galaxy continues to pioneer inroads for institutions seeking exposure to the innovation happening within the crypto ecosystem," said Steve Kurz, Partner and Head of Asset Management at Galaxy Digital. -

Galaxy Digital Holdings Ltd. Management's Discussion And
Galaxy Digital Holdings Ltd. Management’s Discussion and Analysis November 12, 2020 Introduction This Management’s Discussion and Analysis (“MD&A”), dated November 12, 2020, relates to the financial condition and results of operations of Galaxy Digital Holdings Ltd. (“GDH Ltd.” or together with its consolidated subsidiary, the “Company”) as of November 12, 2020, and is intended to supplement and complement the Company’s condensed consolidated interim financial statements for the three and nine months ended September 30, 2020. The Company's only significant asset is a minority interest in Galaxy Digital Holdings LP ("GDH LP" or the "Partnership"), an operating partnership that is building a diversified financial services and investment management business in the cryptocurrency and blockchain space (See Transaction section). GDH LP has separately filed its condensed consolidated interim financial statements and MD&A for the three and nine months ended September 30, 2020, which are available on the Company's SEDAR profile at www.sedar.com. The Company's MD&A should be read in conjunction with GDH LP's condensed consolidated interim financial statements and MD&A. The Company has included GDH LP's MD&A as an appendix to this MD&A. This MD&A, when read in conjunction with GDH LP's MD&A, was written to comply with the requirements of National Instrument 51-102 – Continuous Disclosure Obligations (“NI 51-102”). The condensed consolidated interim financial statements and MD&A are presented in US dollars, unless otherwise noted and have been prepared in accordance with International Financial Reporting Standards (“IFRS”). In the opinion of management, all adjustments (which consist only of normal recurring adjustments) considered necessary for a fair presentation have been included. -
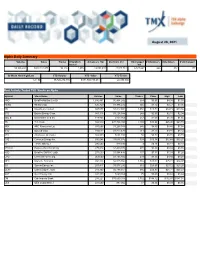
August 26, 2021 Alpha Daily Summary
August 26, 2021 Alpha Daily Summary Volume Value Trades # Symbols Advancers Vol Decliners Vol Unchanged # Advancers # Decliners # Unchanged traded Vol 53,396,832 $823,112,875 96,116 1,655 19,051,433 27,817,712 6,527,687 646 832 177 52-Week New High/Low YTD Volume YTD Value YTD Trades 68 / 36 15,720,274,735 $171,700,733,631 22,890,300 Most Actively Traded TSX Stocks on Alpha Symbol Stock Name Volume Value Trades Close High Low HND BetaProNatGas Lev Br 1,686,497 $6,404,242 664 $3.65 $4.09 $3.59 HEXO HEXO Corp. 636,320 $1,986,272 545 $3.12 $3.27 $3.05 BB BlackBerry Limited 567,077 $7,812,991 1,052 $13.72 $14.15 $13.36 BTE Baytex Energy Corp. 543,118 $1,128,584 248 $2.07 $2.10 $2.04 BBD.B Bombardier Cl B SV 449,865 $755,069 257 $1.69 $1.70 $1.65 TD T.D. Bank 388,529 $32,788,298 2,200 $83.86 $85.98 $83.70 ARX ARC Resources Ltd. 387,696 $3,208,743 646 $8.46 $8.46 $7.98 BTO B2Gold Corp. 382,047 $1,817,670 714 $4.77 $4.81 $4.72 ATH Athabasca Oil Corp J 368,900 $261,193 50 $0.72 $0.72 $0.70 CVE Cenovus Energy Inc. 350,548 $3,637,676 533 $10.34 $10.48 $10.27 TV Trevali Mining J 280,500 $49,090 9 $0.18 $0.18 $0.18 BTCC.B Purpose BitcnCA NCHg 275,816 $2,439,270 472 $8.86 $8.89 $8.76 HSD BetaPro S&P500 -2xBr 273,000 $1,994,438 107 $7.33 $7.33 $7.26 CPG Crescent Point Corp. -

Galaxy Digital Expands Galaxy Fund Management with Acquisition of Vision Hill Group
NEWS RELEASE Galaxy Digital Expands Galaxy Fund Management with Acquisition of Vision Hill Group 5/24/2021 NEW YORK, May 24, 2021 /CNW/ - Galaxy Digital Holdings Ltd. (TSX: GLXY) ("Galaxy Digital" or the "Company") today announced that it has acquired Vision Hill Group, a premier investment consultant and asset manager in the digital asset sector that provides sophisticated investors with access to institutional-caliber investment products, data, benchmarks, and analytics for more informed investment decisions. The acquisition adds to Galaxy Fund Management's leading platform for institutions looking to unlock investment opportunities across the digital asset class. "As the institutionalization of digital assets accelerates, so does the need for comprehensive, institutional-grade platforms to support it and that's precisely what we're building at Galaxy," said Damien Vanderwilt, Co-President, and Head of Global Markets. "The powerful data capabilities that Scott Army, Dan Zuller, and the Vision Hill team have developed are the perfect addition to our full suite of technology-driven nancial services and investment management solutions, fostering the broader mainstream adoption of digital assets." The transaction will further expand Galaxy Fund Management's growing product suite and enable institutional clients to access an even broader array of data and intelligence to streamline research and inform investment decisions. Vision Hill Group's family of crypto hedge fund indices, leading crypto-market intelligence database VisionTrack, and sophisticated asset management capabilities with a crypto-focused fund of funds product sit at the intersection of information (data), expertise (strategies), and access (opportunities). "Galaxy Fund Management is rapidly expanding its capabilities to ultimately provide institutional-grade exposure to every investable corner of digital assets so that institutions can easily get involved in this booming industry," said Steve Kurz, Partner and Head of Asset Management at Galaxy Digital. -

Galaxy Digital Asset Management: August 2021 Month End AUM
NEWS RELEASE Galaxy Digital Asset Management: August 2021 Month End AUM 9/2/2021 NEW YORK, Sept. 2, 2021 /CNW/ - Galaxy Digital Holdings Ltd. (TSX: GLXY) ("Galaxy Digital") announced that its aliate, Galaxy Digital Asset Management ("GDAM") reported preliminary assets under management of $2,130.8 million as of August 31, 2021. Assets Under Management ("AUM")(a)(In millions) 8/31/21 7/31/21 6/30/21 5/31/21 (b) (b) (b) (b) 4/30/21 3/31/21 2/28/21 1/31/21 12/31/20 11/30/20 10/31/20 9/30/20 8/31/20 Total $2,130.8 $1,628.2 $1,423.5 $1,357.8 $1,615.8 $1,275.0 $1,051.9 $834.7 $807.3 $572.7 $446.3 $407.4 $404.9 (a) All gures through 12/31/20 are audited; and all other gures are unaudited. AUM is inclusive of sub-advised funds, committed capital closed-end vehicles, seed investments by aliates, and fund of fund products. Changes in AUM are generally the result of performance, contributions, withdrawals, and acquisitions. (b) Preliminary, AUM associated with GVH Multi-Strategy FOF LP is as of April 30, 2021. Additional information regarding GDAM funds can be found on our website at https://www.galaxydigital.io/services/asset-management. About Galaxy Digital Asset Management 1 Galaxy Digital Asset Management is a diversied asset management rm dedicated to the digital assets and blockchain technology industry. The rm manages capital on behalf of external clients in two distinct business lines: Galaxy Fund Management and Galaxy Interactive. -

Fintech Monthly Market Update | May 2021
Fintech Monthly Market Update MAY 2021 EDITION Leading Independent Advisory Firm Houlihan Lokey is the trusted advisor to more top decision-makers than any other independent global investment bank. Corporate Finance Financial Restructuring Financial and Valuation Advisory 2020 M&A Advisory Rankings 2020 Global Distressed Debt & Bankruptcy 2001 to 2020 Global M&A Fairness All U.S. Transactions Restructuring Rankings Advisory Rankings Advisor Deals Advisor Deals Advisor Deals 1,500+ 1 Houlihan Lokey 210 1 Houlihan Lokey 106 1 Houlihan Lokey 956 2 JP Morgan 876 Employees 2 Goldman Sachs & Co 172 2 PJT Partners Inc 63 3 JP Morgan 132 3 Lazard 50 3 Duff & Phelps 802 4 Evercore Partners 126 4 Rothschild & Co 46 4 Morgan Stanley 599 23 5 Morgan Stanley 123 5 Moelis & Co 39 5 BofA Securities Inc 542 Refinitiv (formerly known as Thomson Reuters). Announced Locations Source: Refinitiv (formerly known as Thomson Reuters) Source: Refinitiv (formerly known as Thomson Reuters) or completed transactions. No. 1 U.S. M&A Advisor No. 1 Global Restructuring Advisor No. 1 Global M&A Fairness Opinion Advisor Over the Past 20 Years ~45% Top 5 Global M&A Advisor 1,400+ Transactions Completed Valued Employee-Owned at More Than $3.0 Trillion Collectively 1,000+ Annual Valuation Engagements Leading Capital Markets Advisor ~$4.5 Billion Market Cap North America Europe and Middle East Asia-Pacific Atlanta Miami Amsterdam Madrid Beijing Sydney >$1 Billion Boston Minneapolis Dubai Milan Hong Kong Tokyo Annual Revenue Chicago New York Frankfurt Paris Singapore Dallas -

PRS Radio Dec 2018.Xlsx
No of Days in Total Per Amount from Amount from Domain StationId Station UDC Performance Date Period Minute Rate Broadcast Public Reception RADIO BR ONE BBC RADIO 1 B0001 31/12/2099 92 £12.2471 £7.3036 £4.9435 RADIO BR TWO BBC RADIO 2 B0002 31/12/2099 92 £25.4860 £25.3998 £0.0862 RADIO BR1EXT BBC 1XTRA CENSUS B0106 31/12/2099 92 £2.8113 £2.7199 £0.0914 RADIO BRASIA BBC ASIAN NETWORK (CENSUS) B0064 31/12/2099 92 £3.6951 £3.3058 £0.3892 RADIO BRBEDS BBC THREE COUNTIES RADIO (CENSUS) B0065 31/12/2099 92 £0.2445 £0.2442 £0.0003 RADIO BRBERK BBC RADIO BERKSHIRE (CENSUS) B0103 31/12/2099 92 £0.1436 £0.1435 £0.0002 RADIO BRBRIS BBC RADIO BRISTOL (CENSUS) B0066 31/12/2099 92 £0.1532 £0.1531 £0.0002 RADIO BRCAMB BBC RADIO CAMBRIDGESHIRE (CENSUS) B0067 31/12/2099 92 £0.1494 £0.1493 £0.0002 RADIO BRCLEV BBC RADIO TEES (CENSUS) B0068 31/12/2099 92 £0.1478 £0.1477 £0.0002 RADIO BRCMRU BBC RADIO CYMRU B0011 31/12/2099 92 £0.5707 £0.5690 £0.0017 RADIO BRCORN BBC RADIO CORNWALL (CENSUS) B0069 31/12/2099 92 £0.1535 £0.1534 £0.0002 RADIO BRCOVN BBC RADIO COVENTRY AND WATWICKSHIRE(CENSUS) B0070 31/12/2099 92 £0.1023 £0.1022 £0.0001 RADIO BRCUMB BBC RADIO CUMBRIA (CENSUS) B0071 31/12/2099 92 £0.1085 £0.1084 £0.0001 RADIO BRCYMM BBC RADIO CYMRU 2 B0114 31/12/2099 92 £0.5707 £0.5690 £0.0017 RADIO BRDEVN BBC RADIO DEVON (CENSUS) B0072 31/12/2099 92 £0.2421 £0.2419 £0.0003 RADIO BRDRBY BBC RADIO DERBY (CENSUS) B0073 31/12/2099 92 £0.1535 £0.1534 £0.0002 RADIO BRESSX BBC ESSEX (CENSUS) B0074 31/12/2099 92 £0.2091 £0.2089 £0.0002 RADIO BRFIVE BBC FIVE LIVE B0005 -

Galaxy Digital to Acquire Bitgo to Form Pre-Eminent Global Provider of Digital Asset Financial Services for Institutions
Galaxy Digital to Acquire BitGo to Form Pre-Eminent Global Provider of Digital Asset Financial Services for Institutions Acquisition Makes Galaxy Digital the First Full-Service Financial Platform for Digital Assets Adding BitGo's Innovative Infrastructure Solutions to Our Industry-Defining Product Suite Galaxy to Undergo a Domestication Process on Intended Path to U.S. Listing Later this Year NEW YORK AND SAN FRANCISCO, May 5, 2021 /PRNewswire/ - Galaxy Digital Holdings Ltd. (TSX: GLXY) ("Galaxy Digital" or the "Company"), a financial services and investment management innovator in the digital asset, cryptocurrency, and blockchain technology sectors, announced today that it has agreed to acquire BitGo, the leading independent digital assets infrastructure provider. The acquisition will position Galaxy Digital as a leading global full-service platform for institutions seeking access to the crypto economy, offering an unparalleled breadth of industry-leading products and services at scale. "The acquisition of BitGo establishes Galaxy Digital as a one-stop-shop for institutions and significantly accelerates our mission to institutionalize digital asset ecosystems and blockchain technology," said Mike Novogratz, CEO and Founder of Galaxy Digital. "The power of the technology, solutions, and people we will have as a result of this acquisition will unlock unique value for our clients and drive long- term growth for our combined business. We are excited to welcome Mike Belshe and the talented BitGo team to Galaxy Digital." BitGo was the first independent regulated custodian, purpose-built for digital assets. Since its founding in 2013, BitGo has been a pioneer in developing leading custody and wallet infrastructure products, financial products including prime lending, trading, and portfolio management, as well as tax solutions that mitigate risk and optimize capital efficiency. -
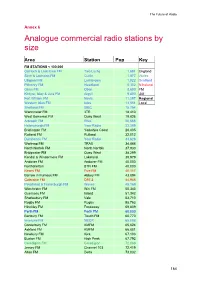
Annexes6-12.Pdf (PDF File, 473.0
The Future of Radio Annex 6 6 Analogue commercial radio stations by size Area Station Pop Key FM STATIONS < 100,000 Gairloch & Loch Ewe FM Two Lochs 1,681 England Skye & Lochalsh FM Cuillin 1,877 Wales Ullapool FM Lochbroom 1,922 Scotland Pitlochry FM Heartland 5,352 N Ireland Oban FM Oban 8,690 FM Kintyre, Islay & Jura FM Argyll 9,400 AM Fort William FM Nevis 11,257 Regional Western Isles FM Isles 13,551 Local Shetland FM SIBC 15,754 Warminster FM 3TR 18,410 West Somerset FM Quay West 19,826 Arbroath FM RNA 20,568 Helensburgh FM Your Radio 22,389 Bridlington FM Yorkshire Coast 28,405 Rutland FM Rutland 32,012 Dumbarton FM Your Radio 33,628 Worksop FM TRAX 34,848 North Norfolk FM North Norfolk 37,930 Bridgwater FM Quay West 38,299 Kendal & Windermere FM Lakeland 39,979 Andover FM Andover FM 40,000 Northallerton BTN FM 40,000 Newry FM Five FM 40,117 Barrow in Furness FM Abbey FM 43,894 Coleraine FM Q97.2 44,948 Peterhead & Fraserburgh FM Waves 45,169 Winchester FM Win FM 50,343 Guernsey FM Island 51,342 Shaftesbury FM Vale 53,710 Rugby FM Rugby 58,763 Hinckley FM Fosseway 59,809 Perth FM Perth FM 60,000 Banbury FM Touch FM 60,770 Inverurie FM NECR 65,008 Canterbury FM KMFM 65,624 Ashford FM KMFM 66,801 Newbury FM Kick 67,103 Buxton FM High Peak 67,792 Ceredigion FM Ceredigion 72,088 Jersey FM Channel 103 72,419 Alton FM Delta 73,032 184 The Future of Radio Weston-super-Mare FM Star 73,478 Mid Ulster FM Six FM 74,471 Salisbury FM Spire 74,802 Fenland FM Fen 75,972 Loughborough FM Oak 80,499 Bridgend FM Bridge 80,939 Omagh & Enniskillen -

CECIL COUNY, MARYLAND; COUNTY CODE CHAPTER 21-2; MONTHLY STATEMENT of EXPENSES OVER $500 -December 2018 Name Description Invoice
CECIL COUNY, MARYLAND; COUNTY CODE CHAPTER 21-2; MONTHLY STATEMENT OF EXPENSES OVER $500 -December 2018 Name Description Invoice Net 3M TRAFFIC CONTROL DIVISION SUPPLIES 7,269.75 ACF ENVIRONMENTAL FACILITIES MAINT 4,750.00 ACTION UNLIMITED RESOURCES, INC SUPPLIES 1,354.28 A-DEL CONSTRUCTION CO ASPHALT OVERLAY 682,536.15 AHOLD USA PHARMACY SUPPLIES 549.90 ALL CARE ASSISTED LIVING LLC HOUSING SUBSIDY 2,600.00 ALLAN MYERS MD, INC. ASPHALT 146,911.88 ALLAN MYERS MD, INC. RACINE SCHOOL ROAD CONSTRUCT 126,394.14 ALLEGIS GROUP HOLDINGS INC PROFESSIONAL SERVICES 9,473.00 ALLIANT TECHSYSTEMS OPERATIONS, LLC TRAINING & EDU 1,000.00 ALTENERGY, INC. CONSTRUCT NERAWWTP 18,652.90 ALTRA, INC SUPPLIES 1,100.00 AMERIGAS PROPANE 2,442.94 AMS ELECTRONIC MONITORING 1,029.60 APG MEDIA OF CHESAPEAKE LLC ADVERTISING 657.05 APPLE FORD LINCOLN MERCURY VEHICLES 146,886.00 AQUALAW, PLC. LEGAL 962.75 ARROW INTERNATIONAL INC SUPPLIES 1,115.50 AT&T TELEPHONE 5,536.64 ATLANTIC DIAGNOSTIC LABORATORIES URINALYSIS LABORATORY TESTING 1,243.70 ATLANTIC TACTICAL SUPPLIES 3,134.40 ATLAS GEOGRAPHIC DATA INC PARCEL GEODATABASE 880.00 AUSTON CONTRACTING, INC. RECYCLYING 2,663.50 AYERS WELDING & FABRICATION BUILDING & IMPROVEMENTS 7,760.00 BAI GROUP, INC PROFESSIONAL SERVICES 26,989.32 BANC OF AMERICA LEASING & CAPITAL, LLC DEBT PAYMENT 181,245.91 BANK OF AMERICA SUPPLIES 58,196.73 BAYLAND CONSULTANTS & DESIGNERS, INC. CONSTRUCTION 5,800.00 BAYSIDE COMMUNITY NETWORK INC HOUSING SUBSIDY 4,823.00 BAYSIDE COMMUNITY NETWORK INC RIGHT OF WAY 2,650.00 BECKER LOCKSMITH SERVICES, INC. PROFESSIONAL SERVICES 670.00 BELNORD MANOR LLC HOUSING SUBSIDY 650.00 BENNER, CHARLES & KELSEY RIGHT OF WAY 775.00 BINNS CONSULTING LLC PROFESSIONAL SERVICES 600.00 BOARD OF EDUCATION OF CECIL COUNTY ALLOCATION 6,871,961.00 BOB BARKER CO SUPPLIES 7,758.83 BRADFORD, EARL TRAVEL COST 693.24 BYLER BUILDERS NOTTINGHAM YARD CONSTRUCT 218,250.00 C.N. -

Top 10 Deals Lexpert Magazine's
SPECIAL EDITION ON CANADA'S LEADING CORPORATE LAWYERS MAY 2019 Lexpert Magazine’s Top 10 Deals Starting with the Gordie Howe International Bridge CLOCKWISE: Linda Brown; McCarthy Tétrault LLP Chris Bennett; Osler, Hoskin & Harcourt LLP Brian Kelsall and Tom Barlow; Fasken Martineau DuMoulin LLP Vicky Tuquero; Windsor-Detroit Bridge Authority Mark Johnson; Blake, Cassels & Graydon LLP Greg Southam; Davies Ward Phillips & Vineberg LLP Brand-15417-Lexpert-ROB-full-page-ad-for-Corporate-print.pdf 1 2019-03-19 11:52 AM C M Y CM MY CY CMY K CONTENTS LEXPERT-RANKED CORPORATE LAWYERS Welcome to the Lexpert® Special Edition on Canada’s Leading Corporate Lawyers. In this issue, alongside of the biographical information about Lexpert-ranked lawyers, we bring you articles on Cryptocurrency (p. 20), Cannabis (p. 32) and Insolvency (p. 26). As for our cover story, we bring you Lexpert® Magazine’s Top 10 Deals of 2018 (p. 4). This Top 10 list is based on commentary from Lexpert-ranked lawyers. The quantum of the deal is important, but not the governing factor. Lawyers tell Lexpert about the challenges they faced on particular deals — challenges that stood in the way of their clients’ goals. To be a Top 10 deal, these challenges were met, and resolved. Usually, there was compromise involved; the resulting transaction may look quite different than the initial announcement. M&A, Corporate, Tax and many other lawyers flex their skills on these Deals. And can’t wait Jean Cumming Editor-in-Chief for the next opportunity to do so again. fortuna favet fortibus MAY 2019 Special Edition Editor-in-Chief Jean Cumming Product Development & Process Lead Jill Grove Art Director Brianna Freitag Cover Photography Christinne Muschi Director/Group Publisher, Media Solutions Karen Lorimer Sales Manager Paul Burton Business Development Consultants Ivan Ivanovitch Kimberlee Pascoe Account Executive Steffanie Munroe Account Manager Colleen Austin Production Editor Alina Leigh Marketing & Circulation Mohammad Ali This Lexpert Insert is published once a year by Thomson Reuters Canada Limited. -

Ruffer Investment Company Limited
Ruffer Investment Company Limited Investment Manager’s Year End Review for the year ended 30 June 2021 (unaudited) Contents Key performance indicators (unaudited) 3 Financial highlights (unaudited) 3 Investment Manager’s report (unaudited) 4 Portfolio statement (unaudited) 18 Appendix 24 2 Ruffer Investment Company Limited Key performance indicators 30 June 2021 % 30 June 2020 % Share price total return over 12 months1 19.5 12.4 NAV total return per share over 12 months1 15.3 10.1 Premium/(discount) of share price to NAV 2.0 (1.5) Dividends per share over 12 months2 1.90p 1.85p Annualised dividend yield3 0.7 0.8 Annualised NAV total return per share since launch1 7.9 7.4 Ongoing charges ratio4 1.08 1.08 Financial highlights 30 June 2021 30 June 2020 Share price 287.00p 242.00p NAV £575,913,008 £444,389,282 Market capitalisation £587,541,854 £437,507,967 Number of shares in issue 204,718,416 180,788,416 NAV per share5 281.32p 245.81p 1 Assumes reinvestment of dividends 2 Dividends paid during the period 3 Dividends paid during the year divided by closing share price 4 Calculated in accordance with AIC guidance 5 NAV per share as released on the London Stock Exchange RIC total return NAV 360 FTSE All-Share TR 320 Twice Bank Rate 280 240 200 160 120 80 2004 2006 2008 2010 2012 2014 2016 2018 2020 Source: RAIFM Ltd, FTSE International (FTSE). Data to 30 June 2021. All figures include reinvested income. Ruffer performance is shown after deduction of all fees and management charges.