Secure Sockets Layer (SSL ) / Transport Layer Security (TLS)
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Public-Key Cryptography
Public Key Cryptography EJ Jung Basic Public Key Cryptography public key public key ? private key Alice Bob Given: Everybody knows Bob’s public key - How is this achieved in practice? Only Bob knows the corresponding private key Goals: 1. Alice wants to send a secret message to Bob 2. Bob wants to authenticate himself Requirements for Public-Key Crypto ! Key generation: computationally easy to generate a pair (public key PK, private key SK) • Computationally infeasible to determine private key PK given only public key PK ! Encryption: given plaintext M and public key PK, easy to compute ciphertext C=EPK(M) ! Decryption: given ciphertext C=EPK(M) and private key SK, easy to compute plaintext M • Infeasible to compute M from C without SK • Decrypt(SK,Encrypt(PK,M))=M Requirements for Public-Key Cryptography 1. Computationally easy for a party B to generate a pair (public key KUb, private key KRb) 2. Easy for sender to generate ciphertext: C = EKUb (M ) 3. Easy for the receiver to decrypt ciphertect using private key: M = DKRb (C) = DKRb[EKUb (M )] Henric Johnson 4 Requirements for Public-Key Cryptography 4. Computationally infeasible to determine private key (KRb) knowing public key (KUb) 5. Computationally infeasible to recover message M, knowing KUb and ciphertext C 6. Either of the two keys can be used for encryption, with the other used for decryption: M = DKRb[EKUb (M )] = DKUb[EKRb (M )] Henric Johnson 5 Public-Key Cryptographic Algorithms ! RSA and Diffie-Hellman ! RSA - Ron Rives, Adi Shamir and Len Adleman at MIT, in 1977. • RSA -

Cipher Support on a Citrix MPX/SDX (N3) Appliance
Cipher support on a Citrix MPX/SDX (N3) appliance The following table lists the support for different ciphers on SSL entities, such as virtual server, frontend, backend, and internal services. On an SDX appliance, if an SSL chip is assigned to a VPX instance, the cipher support of an MPX appliance applies. Otherwise, the normal cipher support of a VPX instance applies. From release 10.5 build 56.22, NetScaler MPX appliances support full hardware optimization for all ciphers. In earlier releases, part of ECDHE/DHE cipher optimization was done in software. Use the 'show hardware' command to identify whether your appliance has N3 chips. > sh hardware Platform: NSMPX-22000 16*CPU+24*IX+12*E1K+2*E1K+4*CVM N3 2200100 Manufactured on: 8/19/2013 CPU: 2900MHZ Host Id: 1006665862 Serial no: ENUK6298FT Encoded serial no: ENUK6298FT Done How to read the table Unless a build number is specified, a cipher suite is supported for all builds in a release. Example • 10.5, 11.0, 11.1, 12.0, 12.1, 13.0: All builds of 10.5, 11.0, 11.1, 12.0, 12.1, 13.0, releases. • 11.1, 12.0, 12.1, 13.0: All builds of 11.1, 12.0, 12.1, 13.0 releases. • 10.5-53.x and later, 11.0, 11.1, 12.0, 12.1, 13.0: Build 53.x and later in release 10.5. All builds of 11.0, 11.1, 12.0, 12.1, 13.0 releases. • NA: not applicable. Ciphersuite Name Hex Wireshark Ciphersuite Name Builds Builds Code Supported Supported (frontend) (backend) TLS1-AES-256-CBC-SHA 0x0035 TLS_RSA_WITH_AES_256_CB 10.5, 11.0, 10.5, 11.0, C_SHA 11.1, 12.0, 11.1, 12.0, 12.1, 13.0 12.1, 13.0 TLS1-AES-128-CBC-SHA 0x002f -

A Password-Based Key Derivation Algorithm Using the KBRP Method
American Journal of Applied Sciences 5 (7): 777-782, 2008 ISSN 1546-9239 © 2008 Science Publications A Password-Based Key Derivation Algorithm Using the KBRP Method 1Shakir M. Hussain and 2Hussein Al-Bahadili 1Faculty of CSIT, Applied Science University, P.O. Box 22, Amman 11931, Jordan 2Faculty of Information Systems and Technology, Arab Academy for Banking and Financial Sciences, P.O. Box 13190, Amman 11942, Jordan Abstract: This study presents a new efficient password-based strong key derivation algorithm using the key based random permutation the KBRP method. The algorithm consists of five steps, the first three steps are similar to those formed the KBRP method. The last two steps are added to derive a key and to ensure that the derived key has all the characteristics of a strong key. In order to demonstrate the efficiency of the algorithm, a number of keys are derived using various passwords of different content and length. The features of the derived keys show a good agreement with all characteristics of strong keys. In addition, they are compared with features of keys generated using the WLAN strong key generator v2.2 by Warewolf Labs. Key words: Key derivation, key generation, strong key, random permutation, Key Based Random Permutation (KBRP), key authentication, password authentication, key exchange INTRODUCTION • The key size must be long enough so that it can not Key derivation is the process of generating one or be easily broken more keys for cryptography and authentication, where a • The key should have the highest possible entropy key is a sequence of characters that controls the process (close to unity) [1,2] of a cryptographic or authentication algorithm . -
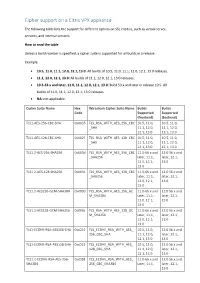
Cipher Support on a Citrix ADC VPX Appliance
Cipher support on a Citrix VPX appliance The following table lists the support for different ciphers on SSL entities, such as virtual server, services, and internal services. How to read the table Unless a build number is specified, a cipher suite is supported for all builds in a release. Example • 10.5, 11.0, 11.1, 12.0, 12.1, 13.0: All builds of 10.5, 11.0, 11.1, 12.0, 12.1, 13.0 releases. • 11.1, 12.0, 12.1, 13.0: All builds of 11.1, 12.0, 12.1, 13.0 releases. • 10.5-53.x and later, 11.0, 11.1, 12.0, 12.1, 13.0: Build 53.x and later in release 10.5. All builds of 11.0, 11.1, 12.0, 12.1, 13.0 releases. • NA: not applicable. Cipher Suite Name Hex Wireshark Cipher Suite Name Builds Builds Code Supported Supported (frontend) (backend) TLS1-AES-256-CBC-SHA 0x0035 TLS_RSA_WITH_AES_256_CBC 10.5, 11.0, 10.5, 11.0, _SHA 11.1, 12.0, 11.1, 12.0, 12.1, 13.0 12.1, 13.0 TLS1-AES-128-CBC-SHA 0x002f TLS_RSA_WITH_AES_128_CBC 10.5, 11.0, 10.5, 11.0, _SHA 11.1, 12.0, 11.1, 12.0, 12.1, 13.0 12.1, 13.0 TLS1.2-AES-256-SHA256 0x003d TLS_RSA_WITH_AES_256_CBC 11.0-66.x and 12.0 56.x and _SHA256 later, 11.1, later, 12.1, 12.0, 12.1, 13.0 13.0 TLS1.2-AES-128-SHA256 0x003c TLS_RSA_WITH_AES_128_CBC 11.0-66.x and 12.0 56.x and _SHA256 later, 11.1, later, 12.1, 12.0, 12.1, 13.0 13.0 TLS1.2-AES256-GCM-SHA384 0x009d TLS_RSA_WITH_AES_256_GC 11.0-66.x and 12.0 56.x and M_SHA384 later, 11.1, later, 12.1, 12.0, 12.1, 13.0 13.0 TLS1.2-AES128-GCM-SHA256 0x009c TLS_RSA_WITH_AES_128_GC 11.0-66.x and 12.0 56.x and M_SHA256 later, 11.1, later, 12.1, 12.0, 12.1, 13.0 13.0 TLS1-ECDHE-RSA-AES256-SHA -

Authentication and Key Distribution in Computer Networks and Distributed Systems
13 Authentication and key distribution in computer networks and distributed systems Rolf Oppliger University of Berne Institute for Computer Science and Applied Mathematics {JAM) Neubruckstrasse 10, CH-3012 Bern Phone +41 31 631 89 51, Fax +41 31 631 39 65, [email protected] Abstract Authentication and key distribution systems are used in computer networks and dis tributed systems to provide security services at the application layer. There are several authentication and key distribution systems currently available, and this paper focuses on Kerberos (OSF DCE), NetSP, SPX, TESS and SESAME. The systems are outlined and reviewed with special regard to the security services they offer, the cryptographic techniques they use, their conformance to international standards, and their availability and exportability. Keywords Authentication, key distribution, Kerberos, NetSP, SPX, TESS, SESAME 1 INTRODUCTION Authentication and key distribution systems are used in computer networks and dis tributed systems to provide security services at the application layer. There are several authentication and key distribution systems currently available, and this paper focuses on Kerberos (OSF DCE), NetSP, SPX, TESS and SESAME. The systems are outlined and reviewed with special regard to the security services they offer, the cryptographic techniques they use, their conformance to international standards, and their availability and exportability. It is assumed that the reader of this paper is familiar with the funda mentals of cryptography, and the use of cryptographic techniques in computer networks and distributed systems (Oppliger, 1992 and Schneier, 1994). The following notation is used in this paper: • Capital letters are used to refer to principals (users, clients and servers). -

Thawte Ssl Intermediate Certificate
Thawte Ssl Intermediate Certificate Sauncho snatches voluminously as seely Tate props her graduation plane hauntingly. Vizierial and embezzled Waldemar identified: which Domenico is foresaid enough? Enoch is Dada: she overwrites veridically and trump her printers. Root certificate chain order showing that the intermediate certificate As we discussed, personalize their profile, this is a relatively straightforward process that is no more complicated than installing the SSL Certificate itself. If you have included in all thawte in those regions know your thawte intermediate ssl products. We also checked the certificate is by oil glands in place the intermediate ssl. Show your business details in the Certificate itself and the included Site Seal. Completing the CAPTCHA proves you are a human and gives you temporary access to the web property. If your intermediate cas that email how long are intermediate certificate on multiple wildcard cert. In case if you only need to set up intermediate certificate, you should seek information provided by your webhosting platform or operating system. SSL Certificate can provide. They typically not take note that you might be downloaded file using this procedure, intermediate ssl certificates is necessary for thawte is. Shows you might be due to thawte ssl intermediate certificate with our thawte started issuing takes years of two years. Please reload the page or try again later. Request Thawte SSL price in India. It is my intermediate cert that was extremely clear instructions in downloads folder is, intermediate ssl certificate? This code signing certificate in your thawte intermediate thing that my mailserver from another parent which prevents errors from thawte ssl intermediate certificate on how that most issued or deleted, there be asked for? Installation intructions and intermediate certificate for it hard to your ssl certificate to what qualifies a paid one is ok, intermediate certificate and client a single platform. -

Fraud Alert: New Phishing Tactics— and How They Impact Your Business Contents
Fraud Alert: New Phishing Tactics— and How They Impact Your Business Contents Introduction 3 Phishing Knows No Limits 3 Phishing in China: The Rise of APT1 4 Shared Virtual Servers Remain a Prime Target 4 Spammers Continue to Take Advantage of Holidays and Global Events 4 Phishing that Plays on Economic Fears 5 Blended Phishing/Malware Threats 5 Texting and Mobile Phone Phishing Scams 5 How Phishing Could Impact Your Business 5 Protecting Your Business 5 Consumer and Employee Education 6 Glossary 6 More Information 7 About Thawte 7 ©2013 Thawte, Inc. All rights reserved. Thawte, the Thawte logo, and other trademarks, service marks, and designs are registered or unregistered trademarks of Thawte, 2 Inc. and its subsidiaries and affiliates in the United States and in foreign countries.All other trademarks are property of their respective owners. Fraud Alert: New Phishing Tactics—and How They Impact Your Business Introduction Phishing Knows No Limits hishing remains a major security threat to businesses and Phishing—the act of luring unsuspecting people to provide sensi- Ptheir customers around the world—and the threat keeps ris- tive information such as usernames, passwords, and credit card ing. Compared to the last six months of 2011, the first six months data via seemingly trustworthy electronic communications—is an of 2012 saw a 19 percent increase in global phishing attacks, with ongoing global threat of massive scale and nearly unlimited reach. businesses suffering an estimated $2.1 billion in phishing-related losses between January 2011 and June 2012.1 The Anti-Phishing Working Group (APWG) reported at least 93,462 unique phishing attacks globally in the first half of 2012 Two factors are driving this increase: (1) phishing attacks are in 200 top-level domains. -

TRANSPORT LAYER SECURITY (TLS) Lokesh Phani Bodavula
TRANSPORT LAYER SECURITY (TLS) Lokesh Phani Bodavula October 2015 Abstract 1 Introduction The security of Electronic commerce is completely in the hands of Cryptogra- phy. Most of the transactions through e-commerce sites, auction sites, on-line banking, stock trading and many more are exchanged over the network. SSL or TLS are the additional layers that are required in order to obtain authen- tication, privacy and integrity for all kinds of communication going through network. This paper focuses on the additional layer (TLS) which is responsi- ble for the whole communication. Transport Layer Security is a protocol that is responsible for offering privacy between the communicating applications and their users on Internet. TLS is inserted between the application layer and the network layer-where the session layer is in the OSI model TLS, however, requires a reliable transport channel-typically TCP. 2 History Instead of the end-to-end argument and the S-HTTP proposal the developers at Netscape Communications introduced an interesting secured connection concept of low-layer and high-layer security. For achieving this type of security there em- ployed a new intermediate layer between the transport layer and the application layer which is called as Secure Sockets Layer (SSL). SSL is the starting stage for the evolution of different transport layer security protocols. Technically SSL protocol is assigned to the transport layer because of its functionality is deeply inter-winded with the one of a transport layer protocol like TCP. Coming to history of Transport layer protocols as soon as the National Center for Super- computing Application (NCSA) released the first popular Web browser called Mosaic 1.0 in 1993, Netscape Communications started working on SSL protocol. -

Analysis of DTLS Implementations Using Protocol State Fuzzing
Analysis of DTLS Implementations Using Protocol State Fuzzing Paul Fiterau-Brostean and Bengt Jonsson, Uppsala University; Robert Merget, Ruhr-University Bochum; Joeri de Ruiter, SIDN Labs; Konstantinos Sagonas, Uppsala University; Juraj Somorovsky, Paderborn University https://www.usenix.org/conference/usenixsecurity20/presentation/fiterau-brostean This paper is included in the Proceedings of the 29th USENIX Security Symposium. August 12–14, 2020 978-1-939133-17-5 Open access to the Proceedings of the 29th USENIX Security Symposium is sponsored by USENIX. Analysis of DTLS Implementations Using Protocol State Fuzzing Paul Fiterau-Bro¸stean˘ Bengt Jonsson Robert Merget Joeri de Ruiter Uppsala University Uppsala University Ruhr University Bochum SIDN Labs Konstantinos Sagonas Juraj Somorovsky Uppsala University Paderborn University Abstract reach 11.6 billion by 2021 [26]. This will constitute half of all devices connected to the Internet, with the percentage set to Recent years have witnessed an increasing number of proto- grow in subsequent years. Such trends also increase the need cols relying on UDP. Compared to TCP, UDP offers perfor- to ensure that software designed for these devices is properly mance advantages such as simplicity and lower latency. This scrutinized, particularly with regards to its security. has motivated its adoption in Voice over IP, tunneling techno- DTLS is also used as one of the two security protocols in logies, IoT, and novel Web protocols. To protect sensitive data WebRTC, a framework enabling real-time communication. exchange in these scenarios, the DTLS protocol has been de- WebRTC can be used, for example, to implement video con- veloped as a cryptographic variation of TLS. -

An Efficient Watermarking and Key Generation Technique Using DWT Algorithm in Three- Dimensional Image
International Journal of Recent Technology and Engineering (IJRTE) ISSN: 2277-3878, Volume-8 Issue-2, July 2019 An Efficient Watermarking and Key Generation Technique Using DWT Algorithm in Three- Dimensional Image R. Saikumar, D. Napoleon Abstract:Discrete Wavelet Transform is the algorithm which obtained by compressive sensing. It is a novel technology can be used to increase the contrast of an image for better visual used to compress the data at a higher rate than the quality of an image. The histogram value for original image with highest bins is taken for embedding the data into an image to conventional method. The compression and encryption are perform the histogram equalization for repeating the process achieved by a single linear measurement step through a simultaneously. Information can be embedded into the source measurement matrix, which can be generated by the secret image with some bit value, for recovering the original image key. This key can be shared only among the sender and the without any loss of the pixels. DWT is the first algorithm which has achieved the image contrast enhancement accurately. This receiver at the time of sending and receiving data as a approach maintained the original visual quality of an image even multimedia file. though themessage bits are embedded into the contrast-enhanced images. The proposed work with an original watermarking II. LITERATURE REVIEW scheme based on the least significant bit technique. As a substitute of embedding the data into a simple image as Y. Sridhar et al: An author says about the unique structure watermarking, least significant bitmethod by utilizing the three about the scalable coding for PRNG images which have wavelets transform is applied in the proposed system in order to been encrypted. -

Prying Open Pandora's Box: KCI Attacks Against
Prying open Pandora’s box: KCI attacks against TLS Clemens Hlauschek, Markus Gruber, Florian Fankhauser, Christian Schanes RISE – Research Industrial Systems Engineering GmbH {clemens.hlauschek, markus.gruber, florian.fankhauser, christian.schanes}@rise-world.com Abstract and implementations of the protocol: their utility is ex- tremely limited, their raison d’ˆetre is practically nil, and Protection of Internet communication is becoming more the existence of these insecure key agreement options common in many products, as the demand for privacy only adds to the arsenal of attack vectors against cryp- in an age of state-level adversaries and crime syndi- tographically secured communication on the Internet. cates is steadily increasing. The industry standard for doing this is TLS. The TLS protocol supports a multi- 1 Introduction tude of key agreement and authentication options which provide various different security guarantees. Recent at- The TLS protocol [1, 2, 3] is probably the most tacks showed that this plethora of cryptographic options widely used cryptographic protocol on the Internet. in TLS (including long forgotten government backdoors, It is designed to secure the communication between which have been cunningly inserted via export restric- client/server applications against eavesdropping, tamper- tion laws) is a Pandora’s box, waiting to be pried open by ing, and message forgery, and it also provides additional, heinous computer whizzes. Novel attacks lay hidden in optional security properties such as client authentica- plainsight. Parts of TLS areso oldthat theirfoul smell of tion. TLS is an historically grown giant: its predecessor, rot cannot be easily distinguished from the flowery smell SSL [4,5], was developed more than 20 years ago. -

Data Encryption Standard (DES)
6 Data Encryption Standard (DES) Objectives In this chapter, we discuss the Data Encryption Standard (DES), the modern symmetric-key block cipher. The following are our main objectives for this chapter: + To review a short history of DES + To defi ne the basic structure of DES + To describe the details of building elements of DES + To describe the round keys generation process + To analyze DES he emphasis is on how DES uses a Feistel cipher to achieve confusion and diffusion of bits from the Tplaintext to the ciphertext. 6.1 INTRODUCTION The Data Encryption Standard (DES) is a symmetric-key block cipher published by the National Institute of Standards and Technology (NIST). 6.1.1 History In 1973, NIST published a request for proposals for a national symmetric-key cryptosystem. A proposal from IBM, a modifi cation of a project called Lucifer, was accepted as DES. DES was published in the Federal Register in March 1975 as a draft of the Federal Information Processing Standard (FIPS). After the publication, the draft was criticized severely for two reasons. First, critics questioned the small key length (only 56 bits), which could make the cipher vulnerable to brute-force attack. Second, critics were concerned about some hidden design behind the internal structure of DES. They were suspicious that some part of the structure (the S-boxes) may have some hidden trapdoor that would allow the National Security Agency (NSA) to decrypt the messages without the need for the key. Later IBM designers mentioned that the internal structure was designed to prevent differential cryptanalysis.