Framing Digital Image Credibility: Image Manipulation Problems, Perceptions and Solutions
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Bosco Palazzi
SHILAP Revista de Lepidopterología ISSN: 0300-5267 ISSN: 2340-4078 [email protected] Sociedad Hispano-Luso-Americana de Lepidopterología España Bella, S; Parenzan, P.; Russo, P. Diversity of the Macrolepidoptera from a “Bosco Palazzi” area in a woodland of Quercus trojana Webb., in southeastern Murgia (Apulia region, Italy) (Insecta: Lepidoptera) SHILAP Revista de Lepidopterología, vol. 46, no. 182, 2018, April-June, pp. 315-345 Sociedad Hispano-Luso-Americana de Lepidopterología España Available in: https://www.redalyc.org/articulo.oa?id=45559600012 How to cite Complete issue Scientific Information System Redalyc More information about this article Network of Scientific Journals from Latin America and the Caribbean, Spain and Journal's webpage in redalyc.org Portugal Project academic non-profit, developed under the open access initiative SHILAP Revta. lepid., 46 (182) junio 2018: 315-345 eISSN: 2340-4078 ISSN: 0300-5267 Diversity of the Macrolepidoptera from a “Bosco Palazzi” area in a woodland of Quercus trojana Webb., in southeastern Murgia (Apulia region, Italy) (Insecta: Lepidoptera) S. Bella, P. Parenzan & P. Russo Abstract This study summarises the known records of the Macrolepidoptera species of the “Bosco Palazzi” area near the municipality of Putignano (Apulia region) in the Murgia mountains in southern Italy. The list of species is based on historical bibliographic data along with new material collected by other entomologists in the last few decades. A total of 207 species belonging to the families Cossidae (3 species), Drepanidae (4 species), Lasiocampidae (7 species), Limacodidae (1 species), Saturniidae (2 species), Sphingidae (5 species), Brahmaeidae (1 species), Geometridae (55 species), Notodontidae (5 species), Nolidae (3 species), Euteliidae (1 species), Noctuidae (96 species), and Erebidae (24 species) were identified. -

Desktop Biodiversity Report
Desktop Biodiversity Report Land at Balcombe Parish ESD/14/747 Prepared for Katherine Daniel (Balcombe Parish Council) 13th February 2014 This report is not to be passed on to third parties without prior permission of the Sussex Biodiversity Record Centre. Please be aware that printing maps from this report requires an appropriate OS licence. Sussex Biodiversity Record Centre report regarding land at Balcombe Parish 13/02/2014 Prepared for Katherine Daniel Balcombe Parish Council ESD/14/74 The following information is included in this report: Maps Sussex Protected Species Register Sussex Bat Inventory Sussex Bird Inventory UK BAP Species Inventory Sussex Rare Species Inventory Sussex Invasive Alien Species Full Species List Environmental Survey Directory SNCI M12 - Sedgy & Scott's Gills; M22 - Balcombe Lake & associated woodlands; M35 - Balcombe Marsh; M39 - Balcombe Estate Rocks; M40 - Ardingly Reservior & Loder Valley Nature Reserve; M42 - Rowhill & Station Pastures. SSSI Worth Forest. Other Designations/Ownership Area of Outstanding Natural Beauty; Environmental Stewardship Agreement; Local Nature Reserve; National Trust Property. Habitats Ancient tree; Ancient woodland; Ghyll woodland; Lowland calcareous grassland; Lowland fen; Lowland heathland; Traditional orchard. Important information regarding this report It must not be assumed that this report contains the definitive species information for the site concerned. The species data held by the Sussex Biodiversity Record Centre (SxBRC) is collated from the biological recording community in Sussex. However, there are many areas of Sussex where the records held are limited, either spatially or taxonomically. A desktop biodiversity report from SxBRC will give the user a clear indication of what biological recording has taken place within the area of their enquiry. -

Fall 2002 Issue of Spires, the Washington University Chapter Received Over 140 Submissions of Literature and Art from 16 Different Universities
inter collegia te ar ts & liter ar y mag azine mag y ar liter & ts ar te collegia inter S – – – f all all f – – V olume VIII, Issue II Issue VIII, olume V – 2002 P I R E S f a l l 2 0 0 2 S PIRES S PIRES intercollegiate arts & literary magazine ! f all 2002 " Copyright 2002 of Spires Volume VIII, Issue II 12345 First Edition 67890 All rights reserved. No part of this magazine may be reproduced or transmitted in any form or by any means, electronic or mechanical, including photocopying, recording, or by any information storage and r etrieval system, without prior written permission from Spires and the author. Critics, however, are welcome to quote brief passages b y way of criticism and review. F or ways to support Spires check out http://kwur.wustl.edu/~spires/support/ or write to us at: S p i r e s Campus Box 52 Contract Station 24 One Brookings Drive Washington University Saint Louis, Missouri 63130 A one-year subscription to Spires costs only $15.00. Make checks payable to: Spires Intercollegiate Arts and Literary Magazine Washington University [email protected] http://kwur.wustl.edu/~spires/ F r ont Cover “Trading Places” by Nathan Ratcliffe from Washington University Back Cover photography by Juliet L. Fong from Washington University CONTENTS Danny Marcus cosmos . 9 F a ye Gleisser he was not . 10 Erin Harkless Untitled . 11 Erin Harkless Untitled . 11 Sam Eddington Night by the Ocean . 14 Michhael Parks Alberquerque, NM . 16 Eric Van Cleve Neapolitan . 18 Lauren Harte Untitled . -

Content Authentication for Neural Imaging Pipelines: End-To-End Optimization of Photo Provenance in Complex Distribution Channels
Content Authentication for Neural Imaging Pipelines: End-to-end Optimization of Photo Provenance in Complex Distribution Channels Pawe lKorus1,2 and Nasir Memon1 New York University1, AGH University of Science and Technology2 http://kt.agh.edu.pl/~korus Abstract which exploits inherent statistical properties result- ing from the photo acquisition pipeline. While the Forensic analysis of digital photo provenance relies former provides superior performance and allows for on intrinsic traces left in the photograph at the time advanced protection features (like precise tampering of its acquisition. Such analysis becomes unreliable af- localization [38], or reconstruction of tampered con- ter heavy post-processing, such as down-sampling and tent [25]), it failed to gain widespread adoption due to re-compression applied upon distribution in the Web. the necessity to generate protected versions of the pho- This paper explores end-to-end optimization of the en- tographs, and the lack of incentives for camera vendors tire image acquisition and distribution workflow to fa- to modify camera design to integrate such features [4]. cilitate reliable forensic analysis at the end of the dis- Passive forensics, on the other hand, relies on our tribution channel. We demonstrate that neural imag- knowledge of the photo acquisition pipeline, and statis- ing pipelines can be trained to replace the internals of tical artifacts introduced by its successive steps. While digital cameras, and jointly optimized for high-fidelity this approach is well suited for potentially analyzing photo development and reliable provenance analysis. In any digital photograph, it often falls short due to the our experiments, the proposed approach increased im- complex nature of image post-processing and distribu- age manipulation detection accuracy from 45% to over tion channels. -
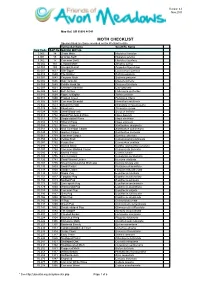
MOTH CHECKLIST Species Listed Are Those Recorded on the Wetland to Date
Version 4.0 Nov 2015 Map Ref: SO 95086 46541 MOTH CHECKLIST Species listed are those recorded on the Wetland to date. Vernacular Name Scientific Name New Code B&F No. MACRO MOTHS 3.005 14 Ghost Moth Hepialus humulae 3.001 15 Orange Swift Hepialus sylvina 3.002 17 Common Swift Hepialus lupulinus 50.002 161 Leopard Moth Zeuzera pyrina 54.008 169 Six-spot Burnet Zygaeba filipendulae 66.007 1637 Oak Eggar Lasiocampa quercus 66.010 1640 The Drinker Euthrix potatoria 68.001 1643 Emperor Moth Saturnia pavonia 65.002 1646 Oak Hook-tip Drepana binaria 65.005 1648 Pebble Hook-tip Drepana falcataria 65.007 1651 Chinese Character Cilix glaucata 65.009 1653 Buff Arches Habrosyne pyritoides 65.010 1654 Figure of Eighty Tethia ocularis 65.015 1660 Frosted Green Polyploca ridens 70.305 1669 Common Emerald Hermithea aestivaria 70.302 1673 Small Emerald Hemistola chrysoprasaria 70.029 1682 Blood-vein Timandra comae 70.024 1690 Small Blood-vein Scopula imitaria 70.013 1702 Small Fan-footed Wave Idaea biselata 70.011 1708 Single-dotted Wave Idaea dimidiata 70.016 1713 Riband Wave Idaea aversata 70.053 1722 Flame Carpet Xanthorhoe designata 70.051 1724 Red Twin-spot Carpet Xanthorhoe spadicearia 70.049 1728 Garden Carpet Xanthorhoe fluctuata 70.061 1738 Common Carpet Epirrhoe alternata 70.059 1742 Yellow Shell Camptogramma bilineata 70.087 1752 Purple Bar Cosmorhoe ocellata 70.093 1758 Barred Straw Eulithis (Gandaritis) pyraliata 70.097 1764 Common Marbled Carpet Chloroclysta truncata 70.085 1765 Barred Yellow Cidaria fulvata 70.100 1776 Green Carpet Colostygia pectinataria 70.126 1781 Small Waved Umber Horisme vitalbata 70.107 1795 November/Autumnal Moth agg Epirrita dilutata agg. -

Biodiversity Response to Land Use Change Across Scales
Biodiversity response to land use change across scales Dissertation zur Erlangung des Doktorgrades der Naturwissenschaften (Dr. rer. nat.) der Naturwissenschaftlichen Fakultät I - Biowissenschaften - der Martin-Luther-Universität Halle Wittenberg, vorgelegt von Herr Murilo Dantas de Miranda, M.Sc. geboren am 16.05.1986 in Ribeira do Pombal, Brasilien Namen der Gutacher: (1) Prof. Dr. Henrique Pereira - Martin-Luther-Universität Halle-Wittenberg, Deutschland (2) Prof. Dr. Ulrich Brose - Friedrich Schiller Universität Jena, Deutschland (3) Prof. Dr. Paulo Borges - Universidade dos Açores, Portugal Datum der Verteidigung: 04 Juli 2017 Dedico as minhas mainhas e a meu painho Contents List of Tables 5 List of Figures 7 Summary 9 Chapter 1: Introduction 11 Land use change and biodiversity . 11 Diversity components: alpha, beta and gamma diversity . 12 Species abundance distribution . 14 Chapter overview . 16 Chapter 2: Testing the habitat amount hypothesis 23 Chapter 3: Moth diversity patterns under farmland abandonment 60 Chapter 4: Species traits shape the relationship between local and regional SADs 84 Chapter 5: Synthesis 112 Habitat amount, not patch size and isolation . 112 Moth diversity patterns under farmland abandonment . 114 Species traits shape the relationship between local and regional SADs 115 Appendix 121 Curriculum Vitae . 121 List of publications and conference participations . 123 Authors’ contributions . 125 Eigenständigkeitserklärung . 126 List of Tables 1 Fit output of both classic and countryside species-area relationship (SAR) models. 32 2 Ranking and autocovariate model output following the Information-Theoretic approach of five statistical models explaining species richness for forest (A) and meadow (B) species as a function of forest habitat amount (Hab) at the 160 and 320 m radius scale, respectevily, patch size (Size), distance to nearest patch (Dist), and their interactions with habitat amount (Hab:Size and Hab:Dist), both with (A/B1) and without (A/B2) spatial autocorrelation (AS) . -

Image Forensics Techniques for Robust Image Security: a Brief Survey
International Journal of Research Studies in Computer Science and Engineering (IJRSCSE) Volume 4, Issue 3, 2017, PP 23-29 ISSN 2349-4840 (Print) & ISSN 2349-4859 (Online) DOI: http://dx.doi.org/10.20431/2349-4859.0403004 www.arcjournals.org Image Forensics Techniques for Robust Image Security: A Brief Survey Harsh Mathur1, Dr. S. Veenadhari2 1PhD Scholar, Aisect University 2Associate Professor, Aisect University, India *Corresponding Author: Harsh Mathur, PhD Scholar, Aisect University. India Abstract : The rising of Cyber Crime has drawn attention toward Digital Forensics and cyber security. it is a branch of forensic science which deals with cyber crime. It essentially includes the detection, recovery and investigation of material found in digital hardware. Digital images and recordings expect most basic part in digital crime scene investigation. They are the prime affirmations of any cyber-crime scene. So the commitment of the image is basic. Digital Photography is having a fast and constantly developing scattering as of late, since it licenses anyone to take a subjective number of good quality images, rapidly and at no cost, and to store them effortlessly on a significant number of digital support, or share them on the Internet. At the same time, with the wide availability of advanced tools for editing image like (e.g. Adobe Photoshop, Gimp), modifying a digital photo, with little or no obvious signs of tampering have become also very easy and widespread. A digitally modified image can be vague from a bona fide image. The altering, be that as it may, may bother some fundamental factual properties of the image. -

United States Patent (19) 11 Patent Number: 6,114,138 Adang (45) Date of Patent: Sep
USOO6114138A United States Patent (19) 11 Patent Number: 6,114,138 Adang (45) Date of Patent: Sep. 5, 2000 54 INSECTICIDAL PROTEIN FRAGMENTS Wong et al 1983 J Biol Chem v 258 1960-67. Yamamoto et al 1981 Bioch Biophy's Res Comm v. 103 75 Inventor: Michael J. Adang, Madison, Wis. 414-21. Schnepf et al 1985 “Delineation of a Toxin-Encoding Seg 73 Assignee: Mycogen Plant Science, Inc., San ment of a Bacillus thuringiensis Crystal Protein Gene' v 260 Diego, Calif. 6273-80. Chestukhina et al 1982 “The Main Features of Bacillus 2 1. Appl. No.: 06/617,321 thuringiensis of O-Endotoxin Molecular Strucutre' Arch 22 Filed: Jun. 4, 1984 Micro V 132 159-162. 5 1. Int. Cl." ........................... C12P 21/06; CO7H 21/04; Primary Examiner Karen Cochrane Carlson C12N 1/20; C12N 15/00 ASSistant Examiner-Devesh Srivastava 52 U.S. Cl. .................. 435/69.1; 536/23.71; 435/252.3; Attorney, Agent, or Firm-Saliwanchik, Lloyd & 435/252.33; 435/252.5; 435/419; 435/320.1 Saliwanchik 58 Field of Search .................................... 435/172.3, 68, 57 ABSTRACT 435/317, 252.31, 252.53, 69.1, 320.1; 935/9, 10, 29, 56, 74, 73; 536/23.71 The Bacillus thuringiensis var. kurStaki HD-73 crystal pro tein gene was cloned into pBR322. E. coli cells harboring 56) References Cited this recombinant plasmid produced a 130 kD protoxin that was toxic to Manduca Sexta (tobacco hornworm) larvae. U.S. PATENT DOCUMENTS Plasmids having the 3'-end of the protoxin gene deleted 4,448.885 5/1984 Schnepf et al. -

Unit 9 Photo Editing
UNIT 9 PHOTO EDITING Structure 9.0 Introduction 9.1 Learning Outcomes 9.2 What is Photo Editing? 9.3 History of Photo Editing 9.4 Digital Workflow 9.5 Basic Image Editing 9.5.1 Types of Graphics 9.5.2 Photo Editing Software 9.5.3 Editing Tools 9.5.4 Digital Image File Formats 9.6 Digital Art 9.7 Ethical Issues 9.8 Let Us Sum Up 9.9 Key Words 9.10 Further Readings 9.11 Check Your Progress: Possible Answers 9.0 INTRODUCTION In this unit you will learn about the what and how of Photo Editing. You will be introduced to basic image editing techniques employed during the era of film photography and will be taken through its evolution over the years, till today, the era of digital photography. You will also read about various features of a photo editing software and their uses in photo editing. You will also be apprised of the process that is followed in order to edit digital photographs. Lastly, we shall discuss the impact and the socio-psychological repercussions arising due to photograph manipulation around the world in the social media along with other ethical issues. 9.1 LEARNING OUTCOMES After going through this unit, you will be able to: ● discuss the evolution of photo editing; ● describe the use of various features of a photo editing software; and ● ascertain the use and impact of photo editing in digital era. 9.2 WHAT IS PHOTO EDITING? You may recall seeing images in newspapers with text on them. These could be advertisements or simple posters or banners. -

Tiger-Moths of Iran 481-525 Atalanta (Dezember 2005) 36 (3/4): 481-525, Würzburg, ISSN 0171-0079
ZOBODAT - www.zobodat.at Zoologisch-Botanische Datenbank/Zoological-Botanical Database Digitale Literatur/Digital Literature Zeitschrift/Journal: Atalanta Jahr/Year: 2005 Band/Volume: 36 Autor(en)/Author(s): Dubatolov Vladimir V., Zahiri Reza Artikel/Article: Tiger-moths of Iran 481-525 Atalanta (Dezember 2005) 36 (3/4): 481-525, Würzburg, ISSN 0171-0079 Tiger-moths o f Iran (Lepidoptera, Arctiidae: Arctiinae) by V l a d im ir V. D u b a t o l o v & R e z a Z a h ir i received 26.X.2005 Abstract: Based on the vast material from the collection of the Hayk Mirzayans Insect Museum (HMIM) and literature data, 28 species are recorded from Iran. Callimorpha dominula rossica K o l ., Axiopoena kareliniMtu., Utetheisa lotrixCr ., Watsonarctia deserta B a r t ., Diaphora mendica C l . are recorded from this country for the first time. Four new subspecies, Arctia caja mazandarana subspec. nov. from the Caspian Coast, Eucharia festiva hormozgana subspec. nov. from South Iran, Watsonarctia deserta elbursica subspec. nov. from the Alburz Mts., and Pbragmatobia placida mirzayansi subspec. nov. with a pale coloration, from the high mountains of the Albourz are described. The analysis of the Arctiinae fauna shows that the fauna of South-Eastern Iran is the Oriental, and not Palearctic. Zusammenfassung: Mit Hilfe des reichhaltigen Materials des Hayk Mirzayans Insect Museum (HMIM) und aufgrund von Literaturangaben können 28 Arten für den Iran angegeben werden. Callimorpha dominula rossica K o l ., Axiopoena kareliniM £ n ., Utetheisa lotrix C r ., Watsonarctia deserta B a r t ., Diaphora mendica C l . werden erstmals für dieses Land gemeldet. -

Moth Moniioring Scheme
MOTH MONIIORING SCHEME A handbook for field work and data reporting Environment Data Centre 1/1/1/ National Boord of Waters and the Environment Nordic Council of Ministers /////// Helsinki 1 994 Environmental Report 8 MOTH MONITORING SCHEME A handbook for field work and data reporting Environment Data Centre National Board of Waters and the Environment Helsinki 1994 Published by Environment Data Centre (EDC) National Board of Waters and the Environment P.O.BOX 250 FIN—001 01 Helsinki FINLAND Tel. +358—0—73 14 4211 Fax. +358—0—7314 4280 Internet address: [email protected] Edited by Guy Söderman, EDC Technical editng by Päivi Tahvanainen, EDC This handbook has been circulated for comments to the members of the project group for moth monitoring in the Nordic countries under the auspices of the Monitoring and Data Group of the Nordic Council of Ministers. Cover photo © Tarla Söderman Checking of installation of light trap at Vilsandi National Park in Estonia. Printed by Painotalo MIKTOR Ky, Helsinki 1 994 ISBN 951—47—9982—8 ISSN 0788—3765 CONTENTS .4 INTRODUCTION 5 PART 1: OBJECTIVES 7 1 Short term objectives 7 2 Medium-long term objectives 8 3 Additional objectives 8 4 Specific goals 9 5 Network design 9 5.1 Geographical coverage 9 5.2 Biotopes coverage 10 PART II: METRODOLOGY 11 1 Technical equipments and use 11 1.1 Structure of Iight traps 11 1.2 Field installation 13 1.3 Structure ofbait trap 14 1.4 Documentation of sites 15 1.5 Timing the light traps 15 1.6 Sampling procedures 15 2 Sample handling 16 2.1 Prestoring 16 2.2 Posting 16 -

The Lepidoptera of Bucharest and Its Surroundings (Romania)
Travaux du Muséum National d’Histoire Naturelle © 30 Décembre Vol. LIV (2) pp. 461–512 «Grigore Antipa» 2011 DOI: 10.2478/v10191-011-0028-9 THE LEPIDOPTERA OF BUCHAREST AND ITS SURROUNDINGS (ROMANIA) LEVENTE SZÉKELY Abstract. This study presents a synthesis of the current knowledge regarding the Lepidoptera fauna of Bucharest and the surrounding areas within a distance up to 50 kilometers around the Romanian capital. Data about the fauna composition are presented: the results of the research work beginning with the end of the 19th century, as well the results of the research work carried out in the last 15 years. The research initiated and done by the author himself, led to the identification of 180 species which were unknown in the past. Even if the natural habitats from this region have undergone through radical changes in the 20th century, the area still preserves a quite rich and interesting Lepidoptera fauna. The forests provide shelter to rich populations of the hawk moth Dolbina elegans A. Bang-Haas, 1912, one of the rarest Sphingidae in Europe, and some other species with high faunistical and zoogeographical value as: Noctua haywardi (Tams, 1926) (it is new record for the Romanian fauna from this area), Catocala dilecta (Hübner, 1808), Tarachidia candefacta (Hübner, [1831]), Chrysodeixis chalcites (Esper, [1789]), Aedia leucomelas (Linnaeus, 1758), and Hecatera cappa (Hübner, [1809]). We also present and discuss the current status of the protected Lepidoptera species from the surroundings of the Romanian capital for the first time. Résumé. Ce travail représente une synthèse des connaissances actuelles concernant la faune de lépidoptères de Bucarest et de ses zones limitrophes sur un rayon de 50 km autour de la capitale de la Roumanie.