Toolkit 2012-05 Trinity Rescue Kit TRK Is a Free Live Linux Distribution
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
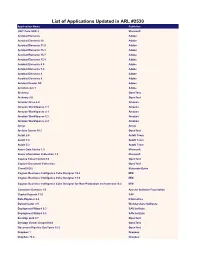
List of Applications Updated in ARL #2530
List of Applications Updated in ARL #2530 Application Name Publisher .NET Core SDK 2 Microsoft Acrobat Elements Adobe Acrobat Elements 10 Adobe Acrobat Elements 11.0 Adobe Acrobat Elements 15.1 Adobe Acrobat Elements 15.7 Adobe Acrobat Elements 15.9 Adobe Acrobat Elements 6.0 Adobe Acrobat Elements 7.0 Adobe Application Name Acrobat Elements 8 Adobe Acrobat Elements 9 Adobe Acrobat Reader DC Adobe Acrobat.com 1 Adobe Alchemy OpenText Alchemy 9.0 OpenText Amazon Drive 4.0 Amazon Amazon WorkSpaces 1.1 Amazon Amazon WorkSpaces 2.1 Amazon Amazon WorkSpaces 2.2 Amazon Amazon WorkSpaces 2.3 Amazon Ansys Ansys Archive Server 10.1 OpenText AutoIt 2.6 AutoIt Team AutoIt 3.0 AutoIt Team AutoIt 3.2 AutoIt Team Azure Data Studio 1.9 Microsoft Azure Information Protection 1.0 Microsoft Captiva Cloud Toolkit 3.0 OpenText Capture Document Extraction OpenText CloneDVD 2 Elaborate Bytes Cognos Business Intelligence Cube Designer 10.2 IBM Cognos Business Intelligence Cube Designer 11.0 IBM Cognos Business Intelligence Cube Designer for Non-Production environment 10.2 IBM Commons Daemon 1.0 Apache Software Foundation Crystal Reports 11.0 SAP Data Explorer 8.6 Informatica DemoCreator 3.5 Wondershare Software Deployment Wizard 9.3 SAS Institute Deployment Wizard 9.4 SAS Institute Desktop Link 9.7 OpenText Desktop Viewer Unspecified OpenText Document Pipeline DocTools 10.5 OpenText Dropbox 1 Dropbox Dropbox 73.4 Dropbox Dropbox 74.4 Dropbox Dropbox 75.4 Dropbox Dropbox 76.4 Dropbox Dropbox 77.4 Dropbox Dropbox 78.4 Dropbox Dropbox 79.4 Dropbox Dropbox 81.4 -

LPS-Public Quick Start Guide
LPS-Public Quick Start Guide This guide is for the beginner user to create and use a Lightweight Portable Security – Public Edition (LPS- Public) CD to more securely browse the Internet and access CAC-enabled websites. For more information on LPS-Public, see http://www.spi.dod.mil/lipose.htm. LPS-Public focuses on safe browsing; it supports thumb drives but intentionally lacks drivers (support) for hard drives and printers. 1. Create a bootable CD from the ISO image (*.iso, an image file of an optical disc). a) Download and save the LPS-Public ISO image from http://www.spi.dod.mil/lipose.htm. b) Burn the image to a blank CD using ISO software (e.g., UltraISO, ISO Maker, K3b, CDBurnerXP, Easy CD Creator, ImgBurn, CDBurn, Nero Burning ROM, Roxio Creator, or one of many others but ATSPI endorses none). This is not the same as just saving the file to a CD. c) Write the LPS version number on the CD. 2. Connect your PC or Intel-based Mac to a wired Ethernet network with DHCP service, or have a wireless (WiFi) or broadband cellular network available. 3. Connect a USB CCID-compliant CAC reader to your PC. Many built-in readers are not supported. Insert your CAC into the reader. If you have an old or non-CCID reader, you may need new firmware from the OEM. LPS contains a Firmware Updating utility that you should run. 4. Insert the LPS-Public CD into the CD drive. Restart your computer. It may take a few minutes to boot LPS. -

'DIY' Digital Preservation for Audio Identify · Appraise · Organise · Preserve · Access Plan + Housekeeping
'DIY' Digital Preservation for Audio Identify · Appraise · Organise · Preserve · Access Plan + housekeeping Part 1 (10:00am-10:50am) Part 2 (11:00am-11:45am) 10:00am-10:10am Intros and housekeeping 10:50am-11:00am [10-minute comfort break] 10:10am-10:30am Digital Preservation for audio 11:00am-11:15am Organise (Migrate) What material do you care 11:15am-11:45am Store, Maintain, Access about and hope to keep?_ Discussion & Questions 10:30am-10:50am Locate, Appraise, Identify What kind of files are you working with?_ Feel free to Using Zoom swap to ‘Grid View’ when slides are not in use, to gage ‘the room’. Please use the chat Please keep function to your mic on ask questions ‘mute’ when while slides not speaking. are in use. Who are we? • Bridging the Digital Gap traineeship scheme • UK National Archives (National Lottery Heritage Fund) • bringing ‘digital’ skills into the archives sector Why are we doing these workshops? • agitate the cultural record to reflect lived experience • embrace tools that support historical self-determination among non- specialists • raise awareness, share skills, share knowledge What is digital preservation? • digital material is vulnerable in different ways to analog material • digital preservation = “a series of managed activities undertaken to ensure continued access to digital materials for as long as necessary.” Audio practices and technological dependency Image credit: Tarje Sælen Lavik Image credit: Don Shall Image credit: Mk2010 Image credit: Stahlkocher Image credit: JuneAugust Digital preservation and ‘born-digital’ audio Bitstream File(s) Digital Content Rendered Content • codecs (e.g. LPCM) • formats and containers (e.g. -

Amateur Computer Group of New Jersey NEWS Volume 39, Number 01 January 2014
Amateur Computer Group of New Jersey NEWS Volume 39, Number 01 January 2014 Main Meeting/Election Report ACGNJ Meetings Brenda Bell, ACGNJ For the very latest news on ACGNJ meetings, please On December 6, 2013, we held our Annual Business visit the ACGNJ Website (www.acgnj.org). Meeting, with 8 persons attending. Having reached a Board of Directors Meeting: December 31, 7:00 PM quorum, the meeting was called to order at 9:09 PM. MOVED to Friday, January 3, 7:00 PM. Mike Redlich presented a President's Report. (Due to the New Year's Holiday) Malthi Masurekar presented a Treasurer's Report. Board of Directors Meeting: Friday, Jan 3, 7:00 PM Several topics were raised for discussion, including Mike Redlich (president (at) acgnj.org) membership issues and outreach to other clubs. Main Meeting: Friday, January 3. 8:00 PM Election results. Without discussion, and with no Mike Redlich (president (at) acgnj.org) additional candidates being nominated for our two Lunics (Linux/UNIX): Monday, January 6, 8:00 PM still open Director positions, John Raff moved that Andreas Meyer (lunics (at) acgnj.org) the Secretary cast one vote for the pat slate. The Investing: Thursday, January 9, 8:00 PM motion was seconded and carried. Jim Cooper (jim (at) thecoopers.org). President: Michael Redlich NJ Gamers: Friday, January 10, 6:00 PM Vice-President: Wendy Bell Gregg McCarthy (greggmajestic (at) gmail.com) Secretary: Brenda Bell Treasurer: Malthi Masurekar Layman’s Forum: Monday, January 13, 8:00 PM Directors (Two year term, through end of 2015): Matt Skoda (som359 (at) gmail.com) Gregg McCarthy Java: Tuesday, January 14, 7:30 PM John Raff Mike Redlich (mike (at) redlich.net) Frank Warren Window Pains: Friday, January 17, 7:00 PM Directors (From last year, through end of 2014): !!!WARNING!!! This meeting will NOT be held in Bob Hawes our usual location. -

Forensics Evaluation of Privacy of Portable Web Browsers
International Journal of Computer Applications (0975 – 8887) Volume 147 – No. 8, August 2016 Forensics Evaluation of Privacy of Portable Web Browsers Ahmad Ghafarian Seyed Amin Hosseini Seno Department of Computer Science Department of Computer Engineering and Information Systems Faculty of Engineering University of North Georgia Ferdowsi University of Mashhad Dahlonega, GA 30005, USA Mashhad, Iran ABSTRACT relation to a computer forensic investigation is that the latter is Browsers claim private mode browsing saves no data on the a less tangible source of evidence [3]. host machine. Most popular web browsers also offer portable A study of tools and techniques for memory forensics can be versions of their browsers which can be launched from a found in [4]. The author has evaluated several command line removable device. When the removable device is removed, it and graphical user interface tools and provide the steps is claimed that traces of browsing activities will be deleted needed for memory forensics. Retrieving portable browsing and consequently private portable browsers offer better forensics artifacts left behind from main memory have privacy. This makes the task of computer forensics recently attracted some attention [5, 6]. The authors used investigators who try to reconstruct the past browsing history, limited memory forensics to retrieve forensics artifacts left in case of any computer incidence, more challenging. after a private portable browsing session. They argue that However, whether or not all data is deleted beyond forensic memory forensics is very promising in establishing a link recovery is a moot point. This research examines privacy of between the suspect and the retrieved data. -

(Hardening) De Navegadores Web Más Utilizados
UNIVERSIDAD DON BOSCO VICERRECTORÍA DE ESTUDIOS DE POSTGRADO TRABAJO DE GRADUACIÓN Endurecimiento (Hardening) de navegadores web más utilizados. Caso práctico: Implementación de navegadores endurecidos (Microsoft Internet Explorer, Mozilla Firefox y Google Chrome) en un paquete integrado para Microsoft Windows. PARA OPTAR AL GRADO DE: MAESTRO EN SEGURIDAD Y GESTION DEL RIESGO INFORMATICO ASESOR: Mg. JOSÉ MAURICIO FLORES AVILÉS PRESENTADO POR: ERICK ALFREDO FLORES AGUILAR Antiguo Cuscatlán, La Libertad, El Salvador, Centroamérica Febrero de 2015 AGRADECIMIENTOS A Dios Todopoderoso, por regalarme vida, salud y determinación para alcanzar un objetivo más en mi vida. A mi amada esposa, que me acompaño durante toda mi carrera, apoyó y comprendió mi dedicación de tiempo y esfuerzo a este proyecto y nunca dudó que lo concluiría con bien. A mis padres y hermana, que siempre han sido mis pilares y me enseñaron que lo mejor que te pueden regalar en la vida es una buena educación. A mis compañeros de trabajo, que mediante su esfuerzo extraordinario me han permitido contar con el tiempo necesario para dedicar mucho más tiempo a la consecución de esta meta. A mis amigos de los que siempre he tenido una palabra de aliento cuando la he necesitado. A mi supervisor y compañeros de la Escuela de Computación de la Universidad de Queens por facilitarme espacio, recursos, tiempo e información valiosa para la elaboración de este trabajo. A mi asesor de tesis, al director del programa de maestría y mis compañeros de la carrera, que durante estos dos años me han ayudado a lograr esta meta tan importante. Erick Alfredo Flores Aguilar INDICE I. -

Give Windows a Tuneup
Tune-up Your Windows PC Jere Minich Jminich (at) apcug.org APCUG Advisor, Region 5 - FL, GA, SC, AL Program Director - Lake Sumter Computer Society ProgramLSCS (at) gmail.com 1 This Presentation covers Windows 7 & 8.1,10 2 Overview of Windows Tune Up Slide Index • Computer Wear & Tear - 4 • Clean Up ‘Startup’ Folder - 33 • Start a System Backup - 5 • Delete Programs - 40 • Check Hard Drive - 9 • Set a Restore Point – 45 • Update & Downloads -13 • PC Security- 51 • Check Defenses - 18 • Logging on to the PC – 55 • Free up Drive Space – 22 • Recommendations - 70 • Disk Cleanup - 25 3 Aspects of Computer Wear and Tear • Windows Update - added dozens of patches to the operating system • Installed some new third-party software • Uninstalled other programs • Upgraded or patched apps and utilities • Altered, tuned, and tweaked various aspects of the system's user interface and software settings • Created and deleted myriad new: • emails, documents, photos, MP3s, videos, spreadsheets, etc. 4 System Backup System Image System Backup • Done for personal data – the data created and downloaded. Documents, movies, music, Photoshop files, work data, etc. • For personal data, do more regular backups, because documents and other personal data get changes and new additions frequently. System Image • An exact copy of the entire hard drive, including every single piece of data: operating system, hardware drivers, apps installed, settings, preferences, etc. Both will copy corrupted files and viruses 5 To back up programs, system settings, and files Go To: -

MX Linux Benutzerhandbuch V
MX Linux Benutzerhandbuch v. 20210327 manual AT mxlinux DOT org MX Linux Webseite MX Linux deutschsprachiges Forum Strg-F = Dieses Handbuch durchsuchen Pos1 / Home = Zum Anfang des Dokuments Translation: Sigi Vranšak – SpinBit Informatik Schaan, 27.03.2021 Tools: LibreOffice 7.0.4, deepl.com Rückmeldungen zu diesem deutschsprachigen Handbuch bitte an: [email protected] OpenPGP 51F0D5C53CF46E29 Titel des englischen Originals: MX Linux Users Manual v. 20200801 Inhalt 1 Einleitung.........................................................................................................................................7 1.1 Über MX Linux..........................................................................................................................7 1.2 Über dieses Handbuch.............................................................................................................7 1.3 Systemanforderungen..............................................................................................................8 1.4 Unterstützung und «Lebensdauer» (EOL, End Of Life)...........................................................8 1.5 Fehler, Probleme und Anfragen, Anträge.................................................................................9 1.6 Migration, Upgrade (Aktualisierung nächste Hauptversion)..................................................10 1.7 Unsere Standpunkte...............................................................................................................10 1.7.1 Systemd..........................................................................................................................10 -

Sicurezza Informatica Cominciando a Parlare Di Ciò Che Può Rallentare I Nostri Computers
SEC 1 - Ma quanto pesa il mio computer? … diventa ‘il miglior amico’, lo si configura secondo le proprie necessità professionali e non solo, lo si arricchisce con lo screen saver più simpatico e lo sfondo per il desktop più rilassante, lo si stipa di cartelle e icone che possano contenere files di vario tipo … Già! Dobbiamo pure fare attenzione al sovrappeso del computer … Considerazione che vale soprattutto quando lo si usa per fare trading on line. Le Piattaforme Tol generalmente non occupano troppo spazio sul disco. Sono applicazioni che si scaricano da internet linkandosi direttamente nel sito web della Banca o della Sim prescelta ma, la corretta visualizzazione delle stesse, la risposta da parte dei vari pulsanti e icone, nonché la velocità delle transazioni dipendono moltissimo dalla quantità di software, applicazioni e files che, prima di loro, hanno preso posto sul nostro personal computer e i cui processi vengono attivati ad ogni accensione della macchina. Non sono molte le persone che utilizzano macchine diverse per usi diversi e va detto che, anche quando si possiedono più computer, si tende quasi sempre a personalizzarne e ad usarne uno soltanto: questo diventa ‘il miglior amico’, lo si configura secondo le proprie necessità professionali e non solo, lo si arricchisce con lo screen saver più simpatico e lo sfondo per il desktop più rilassante, lo si stipa di cartelline e icone che possano contenere files di vario tipo. Dai documenti alle fotografie, dai brani musicali ai filmatini … latte, pane e uova. A parte gli scherzi, dopo pochi mesi di utilizzo, qualsiasi personal computer è già in sovrappeso. -

False Alarm Test February 2011
Anti-Virus Comparative - Appendix – February 2011 www.av-comparatives.org Details about Discovered False Alarms Appendix to the Anti-Virus Comparative February 2011 Language: English February 2011 Last Revision: 29th March 2011 www.av-comparatives.org - 1 - Anti-Virus Comparative - Appendix – February 2011 www.av-comparatives.org Details about the discovered false alarms With AV testing it is important to measure not only detection capabilities but also reliability - one of reliability aspects is certainly product's tendency to flag clean files as infected. No product is immune from false positives (FP’s) but there are differences among them and the goal is to measure them. Nobody has all legitimate files that exist and so no "ultimate" test of FP’s can be done. What can be done and is reasonable, is to create and use a set of clean files which is independent. If on such set one product has e.g. 50 FP’s and another only 10, it is likely that the first product is more prone to FP’s than the other. It doesn't mean the product with 10 FP’s doesn't have more than 10 FP’s globally, but important is the relative number. All listed false alarms were reported and sent to the Anti-Virus vendors for verification and should now be already fixed. False alarms caused by unencrypted data blocks in Anti-Virus related files were not counted. If a product had several false alarms belonging to the same software, it is counted here as only one false alarm. Cracks, keygens, etc. -

Xerox Disc Duplicator User Guide
Disc Duplicator User Guide Version x.10 Xerox Disc Duplicator User Guide Table of Contents Safety Introduction . 4 Notices and Safety . 4 Marks, Labels . 4 FCC Notices For The USA. 5 Operational Safety Information . 6 Operational Safety Information . 6 Electrical Safety Information . 7 Electrical Supply . 7 Disconnect Device . 8 Emergency Power Off . 8 Maintenance Information. 8 Product Safety Certification . 9 Regulatory Information . 9 Certifications in Europe . 9 Product Recycling & Disposal . 10 USA & Canada . 10 European Union . 10 Xerox EH&S Contact Information . 11 Contact Information. 11 Operation 12 Before You Start . 12 Controls and Display . 14 LCD Front Panel . 15 Tutorial Guide . 16 Making Disc-to-Disc Copies . 16 Making Hard Drive-to-Disc Copies. 22 Loading a CD-ROM/DVD Master onto the Hard Drive . 23 Loading a Master Disc Image from the Computer . 27 How to make a Copy from the Hard Drive . 29 How to Select the Duplication Speed . 35 How to Rename a Hard Drive Partition Name from the Front Panel . 37 How to Rename a Hard Drive Partition Name from the Computer. 39 How to Delete an Existing Hard Drive Partition Permanently . 40 How to Change the Setup Settings . 42 Audio CD Editing. 43 Introduction to the Account Management Feature. 50 Account Management Feature Overview . 51 Using Autocopy. 53 Setup Guide 56 Menu Overview . 56 Troubleshooting 61 Trouble Shooting . 61 Error Messages . 63 Software Installation Guide for Accessing the Hard Drive on a Computer 66 Minimum Requirements. 66 Hardware . 66 Operating System . 66 Installing the File System Driver and Utility. 66 Using the File System Utility: . -

The Imgburn Functions
The ImgBurn Functions ImgBurn Support ForumImgBurn Support Forum: The ImgBurn Functions ImgBurn Support ForumJump to content Sign In » New user? Register Now! Help Search This topicSearch section: This topic This forumForumsMembersHelp FilesCalendar Advanced ImgBurn WebsiteForumsMembersCalendarImgBurn Support Forum> General> GuidesView New Content Community Calendar Page 1 of 1 You cannot start a new topicYou cannot reply to this topicThe ImgBurn Function s Everything you ever wanted to know about the program and its settings #1 Cynthia ISF Newbie Group: Beta Team Members Posts: 5,954 Joined: 10September 05 Gender:Female Location:Sweden Posted 22 March 2008 03:48 PM The ImgBurn Functions This guide explains the various functions that can be found in ImgBurn and it's structured in the same way as the ImgBurn menus. Guide Contents 1. File 1.1 Browse for a source file 1.2 Browse for a source folder 1.3 Remove all items 1.4 Browse for a destination file 1.5 Calculate 1.6 Build 1.7 Read 1.8 Write 1.9 Verify 1.10 New Project 1.11 Load Most Recent Project 1.12 Load Project 1.13 Save Project 1.14 Load Most Recent Queue 1.15 Load Queue 1.16 Save Queue 1.17 Export Graph Data 1.18 Display Graph Data 1.19 Recent Files 1.20 Exit 2. View 2.1 Disc Layout Editor 2.2 Drop Zone 2.3 Log 2.4 Queue 2.5 Refresh 3. Mode 3.1 EzMode Picker 3.2 Read 3.2.1 Options And Settings 3.2.1.1 Source 3.2.1.2 Destination 3.2.1.3 Graph Data 3.2.1.4 Settings 3.2.2 Read 3.2.2.1 Options 3.2.3 Available Guides for the 'Read' mode 3.3 Build 3.3.1 Input Modes 3.3.1.1 Standard