Inversion of Control SOLID | DIP | Ioc | DI | Ioc Containers | Made Easy
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

What Is Spring Framework?
Software Engineering a.a. 2019-2020 Introduction to Spring Framework Prof. Luca Mainetti Università del Salento Roadmap ■ Introduction to Spring ■ Dependency Injection and IoC ■ Bean ■ AoP ■ Module Architecture Introduction to Spring Framework 2 Luca Mainetti What Is Spring Framework? ■ Spring is the most popular application development framework for Java enterprise ■ Open source Java platform since 2003. ■ Spring supports all main application servers and JEE standards ■ Spring handles the infrastructure so you can focus on your application ■ Current version: 5.0.X Introduction to Spring Framework 3 Luca Mainetti What does Spring offer? ■ Dependency Injection – Also known as IoC (Inversion of Control) ■ Aspect Oriented Programming – Runtime injection-based ■ Portable Service Abstractions – The rest of spring • ORM, DAO, Web MVC, Web, etc. • Allows access to these without knowing how they actually work Introduction to Spring Framework 4 Luca Mainetti Dependency Injection ■ The technology that actually defines Spring (Heart of Spring). ■ Dependency Injection helps us to keep our classes as indepedent as possible. – Increase reuse by applying low coupling – Easy testing – More understandable An injection is the passing of a dependency (a service) to a dependent object (a client). Passing the service to the client, rather than allowing a client to build or find the service, is the fundamental requirement of the pattern. Introduction to Spring Framework 5 Luca Mainetti Dependency Injection and Inversion of Control (IoC) In software engineering, inversion of control (IoC) describes a design in which custom-written portions of a computer program receive the flow of control from a generic, reusable library. ■ The Inversion of Control (IoC) is a general concept, and it can be expressed in many different ways and dependency Injection is merely one concrete example of Inversion of Control. -

Ioc Containers in Spring
301AA - Advanced Programming Lecturer: Andrea Corradini [email protected] http://pages.di.unipi.it/corradini/ AP-2018-11: Frameworks and Inversion of Control Frameworks and Inversion of Control • Recap: JavaBeans as Components • Frameworks, Component Frameworks and their features • Frameworks vs IDEs • Inversion of Control and Containers • Frameworks vs Libraries • Decoupling Components • Dependency Injection • IoC Containers in Spring 2 Components: a recap A software component is a unit of composition with contractually specified interfaces and explicit context dependencies only. A software component can be deployed independently and is subject to composition by third party. Clemens Szyperski, ECOOP 1996 • Examples: Java Beans, CLR Assemblies • Contractually specified interfaces: events, methods and properties • Explicit context dependencies: serializable, constructor with no argument • Subject to composition: connection to other beans – Using connection oriented programming (event source and listeners/delegates) 3 Towards Component Frameworks • Software Framework: A collection of common code providing generic functionality that can be selectively overridden or specialized by user code providing specific functionality • Application Framework: A software framework used to implement the standard structure of an application for a specific development environment. • Examples: – GUI Frameworks – Web Frameworks – Concurrency Frameworks 4 Examples of Frameworks Web Application Frameworks GUI Toolkits 5 Examples: General Software Frameworks – .NET – Windows platform. Provides language interoperability – Android SDK – Supports development of apps in Java (but does not use a JVM!) – Cocoa – Apple’s native OO API for macOS. Includes C standard library and the Objective-C runtime. – Eclipse – Cross-platform, easily extensible IDE with plugins 6 Examples: GUI Frameworks • Frameworks for Application with GUI – MFC - Microsoft Foundation Class Library. -

Design Pattern Interview Questions
DDEESSIIGGNN PPAATTTTEERRNN -- IINNTTEERRVVIIEEWW QQUUEESSTTIIOONNSS http://www.tutorialspoint.com/design_pattern/design_pattern_interview_questions.htm Copyright © tutorialspoint.com Dear readers, these Design Pattern Interview Questions have been designed specially to get you acquainted with the nature of questions you may encounter during your interview for the subject of Design Pattern. As per my experience good interviewers hardly plan to ask any particular question during your interview, normally questions start with some basic concept of the subject and later they continue based on further discussion and what you answer: What are Design Patterns? Design patterns represent the best practices used by experienced object-oriented software developers. Design patterns are solutions to general problems that software developers faced during software development. These solutions were obtained by trial and error by numerous software developers over quite a substantial period of time. What is Gang of Four GOF? In 1994, four authors Erich Gamma, Richard Helm, Ralph Johnson and John Vlissides published a book titled Design Patterns - Elements of Reusable Object-Oriented Software which initiated the concept of Design Pattern in Software development. These authors are collectively known as Gang of Four GOF. Name types of Design Patterns? Design patterns can be classified in three categories: Creational, Structural and Behavioral patterns. Creational Patterns - These design patterns provide a way to create objects while hiding the creation logic, rather than instantiating objects directly using new opreator. This gives program more flexibility in deciding which objects need to be created for a given use case. Structural Patterns - These design patterns concern class and object composition. Concept of inheritance is used to compose interfaces and define ways to compose objects to obtain new functionalities. -

Inversion of Control in Spring – Using Annotation
Inversion of Control in Spring – Using Annotation In this chapter, we will configure Spring beans and the Dependency Injection using annotations. Spring provides support for annotation-based container configuration. We will go through bean management using stereotypical annotations and bean scope using annotations. We will then take a look at an annotation called @Required, which allows us to specify which dependencies are actually required. We will also see annotation-based dependency injections and life cycle annotations. We will use the autowired annotation to wire up dependencies in the same way as we did using XML in the previous chapter. You will then learn how to add dependencies by type and by name. We will also use qualifier to narrow down Dependency Injections. We will also understand how to perform Java-based configuration in Spring. We will then try to listen to and publish events in Spring. We will also see how to reference beans using Spring Expression Language (SpEL), invoke methods using SpEL, and use operators with SpEL. We will then discuss regular expressions using SpEL. Spring provides text message and internationalization, which we will learn to implement in our application. Here's a list of the topics covered in this chapter: • Container configuration using annotations • Java-based configuration in Spring • Event handling in Spring • Text message and internationalization [ 1 ] Inversion of Control in Spring – Using Annotation Container configuration using annotation Container configuration using Spring XML sometimes raises the possibility of delays in application development and maintenance due to size and complexity. To solve this issue, the Spring Framework supports container configuration using annotations without the need of a separate XML definition. -

Dependency Injection with Unity
D EPEN DEPENDENCY INJECTION WITH UNITY Over the years software systems have evolutionarily become more and more patterns & practices D ENCY complex. One of the techniques for dealing with this inherent complexity Proven practices for predictable results of software systems is dependency injection – a design pattern that I allows the removal of hard-coded dependencies and makes it possible to Save time and reduce risk on your NJECT assemble a service by changing dependencies easily, whether at run-time software development projects by or compile-time. It promotes code reuse and loosely-coupled design which incorporating patterns & practices, I leads to more easily maintainable and flexible code. Microsoft’s applied engineering ON guidance that includes both production The guide you are holding in your hands is a primer on using dependency quality source code and documentation. W I injection with Unity – a lightweight extensible dependency injection TH DEPENDENCY INJECTION container built by the Microsoft patterns & practices team. It covers The guidance is designed to help U software development teams: various styles of dependency injection and also additional capabilities N I of Unity container, such as object lifetime management, interception, Make critical design and technology TY and registration by convention. It also discusses the advanced topics of selection decisions by highlighting WITH UNITY enhancing Unity with your custom extensions. the appropriate solution architectures, technologies, and Microsoft products The guide contains plenty of trade-off discussions and tips and tricks for for common scenarios managing your application cross-cutting concerns and making the most out of both dependency injection and Unity. These are accompanied by a Understand the most important Dominic Betts real world example that will help you master the techniques. -

Designpatternsphp Documentation Release 1.0
DesignPatternsPHP Documentation Release 1.0 Dominik Liebler and contributors Jul 18, 2021 Contents 1 Patterns 3 1.1 Creational................................................3 1.1.1 Abstract Factory........................................3 1.1.2 Builder.............................................8 1.1.3 Factory Method......................................... 13 1.1.4 Pool............................................... 18 1.1.5 Prototype............................................ 21 1.1.6 Simple Factory......................................... 24 1.1.7 Singleton............................................ 26 1.1.8 Static Factory.......................................... 28 1.2 Structural................................................. 30 1.2.1 Adapter / Wrapper....................................... 31 1.2.2 Bridge.............................................. 35 1.2.3 Composite............................................ 39 1.2.4 Data Mapper.......................................... 42 1.2.5 Decorator............................................ 46 1.2.6 Dependency Injection...................................... 50 1.2.7 Facade.............................................. 53 1.2.8 Fluent Interface......................................... 56 1.2.9 Flyweight............................................ 59 1.2.10 Proxy.............................................. 62 1.2.11 Registry............................................. 66 1.3 Behavioral................................................ 69 1.3.1 Chain Of Responsibilities................................... -

Monadic Functional Reactive Programming
Monadic Functional Reactive Programming Atze van der Ploeg Centrum Wiskunde & Informatica [email protected] Abstract FRP is based on the notion of a reactive computation: a monadic Functional Reactive Programming (FRP) is a way to program reac- computation which may require the occurrence of external events tive systems in functional style, eliminating many of the problems to continue. The Monadic FRP variant of a signal is a signal that arise from imperative techniques. In this paper, we present an computation: a reactive computation that may also emit values alternative FRP formulation that is based on the notion of a reac- during the computation. tive computation: a monadic computation which may require the This novel formulation has two differences with other FRP occurrence of external events to continue. A signal computation approaches: is a reactive computation that may also emit values. In contrast to • In contrast to signals in other FRP formulations, signal compu- signals in other FRP formulations, signal computations can end, tations can end. This leads to a simple, monadic interface for leading to a monadic interface for sequencing behavioral changes. sequencing behavioral changes. This interface has several advantages: routing is implicit, sequencing • behaviors is easier and more intuitive than the switching combina- In other FRP approaches, either the entire FRP expression is tors found in other FRP approaches, and dynamic lists require much re-evaluated on each external stimulus, or impure techniques less boilerplate code. In other FRP approaches, either the entire are used to prevent redundant re-computations: re-computing FRP expression is re-evaluated on each external stimulus, or impure the current value of signal while the input it depends on has not techniques are used to prevent redundant re-computations. -
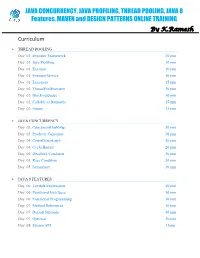
JAVA CONCURRENCY ONLINE TRAINING – Java2aspire
JAVA CONCURRENCY, JAVA PROFILING, THREAD POOLING, JAVA 8 Features, MAVEN and DESIGN PATTERNS ONLINE TRAINING By K.Ramesh Curriculum THREAD POOLING Day 01: Executor Framework 20 min Day 01: Java Profiling 10 min Day 01: Executor 10 min Day 01: ExecutorService 10 min Day 01: Executors 15 min Day 02: ThreadPoolExecutor 20 min Day 02: BlockingQueue 10 min Day 02: Callable vs Runnable 15 min Day 02: Future 15 min JAVA CONCURRENCY Day 03: ConcurrentHashMap 30 min Day 03: Producer Consumer 30 min Day 04: CountDownLatch 20 min Day 04: CyclicBarrier 20 min Day 04: Deadlock Condition 20 min Day 05: Race Condition 30 min Day 05: Semaphore 30 min JAVA 8 FEATURES Day 06: Lambda Expressions 40 min Day 06: Functional Interfaces 10 min Day 06: Functional Programming 10 min Day 07: Method References 10 min Day 07: Default Methods 40 min Day 07: Optional 10 min Day 08: Stream API 1 hour MAVEN Day 09: Project Object Model (POM) 20 min Day 09: Project Description 10 min Day 09: Public Repository 10 min Day 09: Dependency Management 10 min Day 09: Build Configuration 10 min Day 10: Installation 15 min Day 10: Dependency Scope 15 min Day 10: Proprietary Dependencies 15 min Day 10: Project Inheritance 15 min Day 11: Maven life cycle 20 min Day 11: Maven Directory Structure 20 min Day 11: Archetypes 20 min Day 12: Applications 1 hour DESIGN PATTERNS Day 13: Factory Pattern 20 min Day 13: Abstract Factory Pattern 10 min Day 13: Single Pattern 20 min Day 13: Prototype Pattern 10 min Day 14: Composite Pattern 10 min Day 14: Facade Pattern 15 min Day 14: DAO -

Semantic Description of Services and Service Factories for Ambient Intelligence Rémi Emonet
Semantic Description of Services and Service Factories for Ambient Intelligence Rémi Emonet To cite this version: Rémi Emonet. Semantic Description of Services and Service Factories for Ambient Intelligence. Soft- ware Engineering [cs.SE]. Institut National Polytechnique de Grenoble - INPG, 2009. English. tel- 00450479 HAL Id: tel-00450479 https://tel.archives-ouvertes.fr/tel-00450479 Submitted on 26 Jan 2010 HAL is a multi-disciplinary open access L’archive ouverte pluridisciplinaire HAL, est archive for the deposit and dissemination of sci- destinée au dépôt et à la diffusion de documents entific research documents, whether they are pub- scientifiques de niveau recherche, publiés ou non, lished or not. The documents may come from émanant des établissements d’enseignement et de teaching and research institutions in France or recherche français ou étrangers, des laboratoires abroad, or from public or private research centers. publics ou privés. GRENOBLE INP n◦ attribu´epar la biblioth`eque THESE` pour obtenir le grade de ❉♦❝❡✉ ❉✉ ●♦✉♣❡ ●❡♥♦❜❧❡ ■◆ Sp´ecialit´e: Informatique pr´epar´eeau Laboratoire d’Informatique de Grenoble dans le cadre de l’Ecole´ Doctorale Math´ematiques, Sciences et Technologies de l’Information, Informatique pr´esent´eeet soutenue publiquement par R´emi ❊♠♦♥❡ le 23 septembre 2009 ❉❡❝✐♣✐♦♥ ❙♠❛♥✐✉❡ ❞❡ ❙❡✈✐❝❡ ❡ ❞✬❯✐♥❡ à ❙❡✈✐❝❡ ♣♦✉ ❧✬■♥❡❧❧✐❣❡♥❝❡ ❆♠❜✐❛♥❡ ❙❡♠❛♥✐❝ ❉❡❝✐♣✐♦♥ ♦❢ ❙❡✈✐❝❡ ❛♥❞ ❙❡✈✐❝❡ ❋❛❝♦✐❡ ❢♦ ❆♠❜✐❡♥ ■♥❡❧❧✐❣❡♥❝❡ Directeur de th`ese : James L. ❈♦✇❧❡② Co-directeur de th`ese : Dominique ❱❛✉❢❡②❞❛③ JURY Pr. Marie-Christine Rousset Pr´esident Pr. James L. Crowley Directeur de th`ese Dr. Dominique Vaufreydaz Co-directeur de th`ese Pr. Gregory D. Abowd Rapporteur Pr. David Simplot-Ryl Rapporteur Pr. Michel Riveill Examinateur 2 R´esum´e Ce manuscrit ´etudie l’ad´equation des approches `aservices, ainsi que leur am´elioration, pour l’int´egration dynamique et la r´eutilisation logicielle dans le cadre de l’informatique ambiante. -

The Spring Framework: an Open Source Java Platform for Developing Robust Java Applications
International Journal of Innovative Technology and Exploring Engineering (IJITEE) ISSN: 2278-3075, Volume-3 Issue-2, July 2013 The Spring Framework: An Open Source Java Platform for Developing Robust Java Applications Dashrath Mane, Ketaki Chitnis, Namrata Ojha Abstract— The fundamental concepts of Spring Framework is Supported deployment platforms range from standalone presented in this paper.Spring framework is an open source Java applications to Tomcat and Java EE servers such as platform that provides comprehensive infrastructure support for WebSphere. Spring is also a first-class citizen on major developing robust Java applications very easily and very rapidly. cloud platforms with Java support, e.g. on Heroku, Google The Spring Framework is a lightweight solution and a potential App Engine, Amazon Elastic Beanstalk and VMware's one-stop-shop for building your enterprise-ready applications. Cloud Foundry.[1] IndexTerms— Aspect Oriented Programming, Dependency Injection, IoC Container, ORM. II. SPRING FRAMEWORK ARCHITECTURE Spring could potentially be a one-stop shop for all your I. INTRODUCTION enterprise applications; however, Spring is modular, Spring is the most popular application development allowing you to pick and choose which modules are framework for enterprise Java. Millions of developers applicable to you, without having to bring in the rest. around the world use Spring Framework to create high The Spring Framework provides about 20 modules which performing, easily testable, reusable code. Spring can be used based on an application requirement. framework is an open source Java platform and it was initially written by Rod Johnson and was first released under the Apache 2.0 license in June 2003. -

Sun Certified Enterprise Architect for Java EE Study Guide / Mark Cade, Humphrey Sheil
Many of the designations used by manufacturers and sellers to distinguish their products are claimed as trademarks. Where those designations appear in this book, and the publisher was aware of a trademark claim, the designations have been printed with initial capital letters or in all capitals. Sun Microsystems, Inc. has intellectual property rights relating to implementations of the technology described in this publication. In particular, and without limitation, these intellectual property rights may include one or more U.S. patents, foreign patents, or pending applications. Sun, Sun Microsystems, the Sun logo, J2ME, J2EE, Java Card, and all Sun and Java based trademarks and logos are trademarks or registered trademarks of Sun Microsystems, Inc., in the United States and other countries. UNIX is a registered trademark in the United States and other countries, exclusively licensed through X/Open Company, Ltd. This publication is provided “as is” without warranty of any kind, either express or implied, including, but not limited to, the implied warranties of merchantability, fitness for a particular purpose, or non-infringement. This publication could include technical inaccuracies or typographical errors. Changes are periodically added to the information herein; these changes will be incorporated in new editions of the publication. Sun Microsystems, Inc. may make improvements and/or changes in the product(s) and/or the program(s) described in this publication at any time. The authors and publisher have taken care in the preparation of this book, but make no expressed or implied warranty of any kind and assume no responsibility for errors or omissions. No liability is assumed for incidental or consequential damages in connection with or arising out of the use of the information or programs contained herein. -

An Introduction to Dependency Inversion Page 1 of 12
Peruse Muse Infuse: An Introduction to Dependency Inversion Page 1 of 12 An Introduction to Dependency Inversion Originaly posted by AdrianK, 1-Nov-2010 at: http://www.morphological.geek.nz/blogs/viewpost/Peruse Muse Infuse/An Introduction to Dependency Inversion.aspx Tagged under: Architecture, Web Development, Patterns An Introduction to Dependency Inversion This article is for anyone (mainly developers, and specifically .Net developers) who is unfamiliar with Dependency Inversion or design patterns in general. The basic rationale behind the Dependency Inversion Principle [1] (DIP, or simply DI) is very simple; and like most other simple design principles it is suitable in many different situations. Once you understand it you’ll wonder how you managed without it. The key benefit it brings is control over dependencies – by removing them (or perhaps more correctly – by “inverting” them), and this isn’t just limited to “code” – you’ll find this also opens up new opportunities regarding how you can structure and run the actual development process. Implementing DI and is fairly straight forward and will often involve other design patterns, such as the Factory pattern [2] and Lazy Load pattern [3] ; and embodies several other principles including the Stable Abstractions Principle and Interface Segregation Principle. I’ll be using acronyms where I can, here’s a quick glossary for them. • BL: Business Logic, sometimes referred to as the Business Logic Layer. • DA: Data Access, often referred to as the DAL or Data Access Layer. • DI: can refer to either Dependency Inversion or Dependency Injection – both of which (at least for this article) essentially mean the same thing.