I-Sources 13 Septembre 2010 13
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Trend Analysis the Israeli Unit 8200 an OSINT-Based Study CSS
CSS CYBER DEFENSE PROJECT Trend Analysis The Israeli Unit 8200 An OSINT-based study Zürich, December 2019 Risk and Resilience Team Center for Security Studies (CSS), ETH Zürich Trend analysis: The Israeli Unit 8200 – An OSINT-based study Author: Sean Cordey © 2019 Center for Security Studies (CSS), ETH Zurich Contact: Center for Security Studies Haldeneggsteig 4 ETH Zurich CH-8092 Zurich Switzerland Tel.: +41-44-632 40 25 [email protected] www.css.ethz.ch Analysis prepared by: Center for Security Studies (CSS), ETH Zurich ETH-CSS project management: Tim Prior, Head of the Risk and Resilience Research Group, Myriam Dunn Cavelty, Deputy Head for Research and Teaching; Andreas Wenger, Director of the CSS Disclaimer: The opinions presented in this study exclusively reflect the authors’ views. Please cite as: Cordey, S. (2019). Trend Analysis: The Israeli Unit 8200 – An OSINT-based study. Center for Security Studies (CSS), ETH Zürich. 1 Trend analysis: The Israeli Unit 8200 – An OSINT-based study . Table of Contents 1 Introduction 4 2 Historical Background 5 2.1 Pre-independence intelligence units 5 2.2 Post-independence unit: former capabilities, missions, mandate and techniques 5 2.3 The Yom Kippur War and its consequences 6 3 Operational Background 8 3.1 Unit mandate, activities and capabilities 8 3.2 Attributed and alleged operations 8 3.3 International efforts and cooperation 9 4 Organizational and Cultural Background 10 4.1 Organizational structure 10 Structure and sub-units 10 Infrastructure 11 4.2 Selection and training process 12 Attractiveness and motivation 12 Screening process 12 Selection process 13 Training process 13 Service, reserve and alumni 14 4.3 Internal culture 14 5 Discussion and Analysis 16 5.1 Strengths 16 5.2 Weaknesses 17 6 Conclusion and Recommendations 18 7 Glossary 20 8 Abbreviations 20 9 Bibliography 21 2 Trend analysis: The Israeli Unit 8200 – An OSINT-based study selection tests comprise a psychometric test, rigorous Executive Summary interviews, and an education/skills test. -

Secrecy and Human Capital Management in US NSA and Israel Unit 8200
LOOSE LIPS BUILD SHIPS? Secrecy and Human Capital Management in US NSA and Israel Unit 8200 A THESIS SUBMITTED TO THE INTERSCHOOL HONORS PROGRAM IN INTERNATIONAL SECURITY STUDIES CENTER FOR INTERNATIONAL SECURITY AND COOPERATION FREEMAN SPOGLI INSTITUTE FOR INTERNATIONAL STUDIES STANFORD UNIVERSITY By: Lisa Catherine Wallace June 2014 Advisors: Mariano-Florentino Cuéllar Colonel Joseph Felter Abstract ! How do intelligence organizations attract and make use of top talent? This paper approaches this question through a comparative case study of the labor ecosystems surrounding both the US’ National Security Agency and IDF’s signals intelligence branch, Unit 8200. As the cyber realm continues to assume a growing role in modern national security threat environments, intelligence organizations must grow and adapt to accommodate these new objectives. This inevitably involves the question of how to attract and make use of top talent in order to solve difficult and highly technical national security problems. Israel and the United States share similar national security interests, and both possess burgeoning and impressive high-technology clusters. This paper claims that a growing, public network of Unit 8200 and other Intelligence Corps alumni is extant in Israel’s high-technology sector. Furthermore, affiliation with Unit 8200 has a positive signaling and social capital value. By contrast, this paper argues that alumni from the NSA do not possess as strong of a signaling or social capital value in the US. This paper argues that the NSA is hindered by the ontology, secrecy, and culture of the organization itself, as well as US public understanding of national security organizations and cyber threats. -

Location, Event&Q
# from what/ where which how why who for MOBILE versi on click here when who who where when index source "location, event" "phys, pol, med, doc" detail physical detail political name "9/11 Truth Interactive Spreadsheet Click on dow n arrow to sort / filter, click again to undo." Top 100 / compilations entity entity detail country / state date Item .. right-click on li nk to open in new tab 1 "Francis, Stephen NFU" WTC physical Controlled demolition Explosive experts "Overwhelming evidence indicates that a combination of n uclear, thermitic and conventional explosives were used in a controlled demoliti on of the WTC on 9/11. Nanothermite contributed but does not have sufficient det onation velocity to pulverize the WTC into dust. Architects & Engineers for 9/11 Truth is leading gatekeeper trying to deflect Israel's role. See Cozen O'Connor 9/11 lawsuit." pic "9/11 Truth, anti-Zionists" Engineers / Scie ntists "U.S., Israel, SA, Britain" 2 "Francis, Stephen NFU" "WTC, Pentagon, PA" political False flag Cabal "The cabal: U.S., Britain, Saudi Arabia and Israel execu ted the 9/11 false flag attack in order to usher in a new 'war on terror' along with the Iraq and Afghanistan wars and fullfil the PNAC's 'Full Spectrum Dominan ce' of the Middle East and its resources ... all have roots that go back to Zion ist / Nazi Germany, the Cold War ... 9/11 was a planned step." lnk Intel ag encies "Cabal: US, UK, Israel & SA" Mossad / Sayeret Matkal "U.S., Israel, S A, Britain" 3 "Fox, Donald" WTC 1-2 physical "Mini Neutron, Fissionless Fusio n" Controlled demolition "VeteransToday: Fox, Kuehn, Prager, Vike n,Ward, Cimono & Fetzer on mini neutron bombs discuss all major WTC theories micr o nuke (neutron) most promising comparatively low blast effects, a quick blast o f radiation that doesn't linger, a series of shape charged mini-neutron bombs we re detonated from top to bottom to simulate a free fall collapse. -

National Security Agency
Coordinates: 39°6′32″N 76°46′17″W National Security Agency The National Security Agency (NSA) is a national-level intelligence agency of the United National Security Agency States Department of Defense, under the authority of the Director of National Intelligence. The NSA is responsible for global monitoring, collection, and processing of information and data for foreign and domestic intelligence and counterintelligence purposes, specializing in a discipline known as signals intelligence (SIGINT). The NSA is also tasked with the protection of U.S. communications networks and information systems.[8][9] The NSA relies on a variety of measures to accomplish its Seal of the National Security Agency mission, the majority of which are clandestine.[10] Originating as a unit to decipher coded communications in World War II, it was officially formed as the NSA by President Harry S. Truman in 1952. Since then, it has become the largest of the U.S. intelligence organizations in terms of Flag of the National Security Agency personnel and budget.[6][11] The NSA currently conducts worldwide mass data collection and has been known to physically bug electronic systems as one method to this end.[12] The NSA is also alleged to have been behind such attack software as Stuxnet, which severely damaged Iran's nuclear program.[13][14] The NSA, alongside the Central Intelligence Agency (CIA), maintains a physical presence in many countries across the globe; the CIA/NSA joint Special Collection Service (a NSA Headquarters, Fort Meade, Maryland highly classified intelligence team) inserts eavesdropping devices in high value targets (such Agency overview as presidential palaces or embassies). -
Requests Report
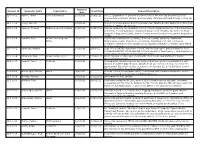
Received Request ID Requester Name Organization Closed Date Request Description Date 12-F-0001 Vahter, Tarmo Eesti Ajalehed AS 10/3/2011 3/19/2012 All U.S. Department of Defense documents about the meeting between Estonian president Arnold Ruutel (Ruutel) and Secretary of Defense Richard Cheney on July 19, 1991. 12-F-0002 Jeung, Michelle - 10/3/2011 - Copies of correspondence from Congresswoman Shelley Berkley and/or her office from January 1, 1999 to the present. 12-F-0003 Lemmer, Thomas McKenna Long & Aldridge 10/3/2011 11/22/2011 Records relating to the regulatory history of the following provisions of the Department of Defense Federal Acquisition Regulation Supplement (DFARS), the former Defense Acquisition Regulation (DAR), and the former Armed Services Procurement Regulation (ASPR). 12-F-0004 Tambini, Peter Weitz Luxenberg Law 10/3/2011 12/12/2011 Documents relating to the purchase, delivery, testing, sampling, installation, Office maintenance, repair, abatement, conversion, demolition, removal of asbestos containing materials and/or equipment incorporating asbestos-containing parts within its in the Pentagon. 12-F-0005 Ravnitzky, Michael - 10/3/2011 2/9/2012 Copy of the contract statement of work, and the final report and presentation from Contract MDA9720110005 awarded to the University of New Mexico. I would prefer to receive these documents electronically if possible. 12-F-0006 Claybrook, Rick Crowell & Moring LLP 10/3/2011 12/29/2011 All interagency or other agreements with effect to use USA Staffing for human resources management. 12-F-0007 Leopold, Jason Truthout 10/4/2011 - All documents revolving around the decision that was made to administer the anti- malarial drug MEFLOQUINE (aka LARIAM) to all war on terror detainees held at the Guantanamo Bay prison facility as stated in the January 23, 2002, Infection Control Standard Operating Procedure (SOP). -

S Black Agents Bang-And-Burner 14 “Bang and Burn” Jobs Involve Sabotage, Usually Through Demolitions Or Arson
night’'s black agents Bang-and-Burner 14 “Bang and burn” jobs involve sabotage, usually through demolitions or arson. This skill set translates with unnerving ease to EOD (explosive ordnance disposal) and arson investigation. Bang- and-burners set and disarm everything from booby traps to car bombs to ship- scuttling charges. Specific Examples: IRA or ETA bomb- builder, Albanian mafia arsonist, Polish Army combat engineer, Special Branch bomb disposal expert. INVESTIGATIVE ABILITIES: Architecture 2, Chemistry 2, Criminology 1, Intimidation 1 GENERAL ABILITIES: Conceal 4, Explosive Devices 8, Infiltration 2, Mechanics 4 Black Bagger A “black bag job” is FBI slang for a breaking-and-entry intrusion, usually intended to copy (or steal) documents or plant bugs or wiretaps. British spies often call break-in artists “box men,” a term originating in Victorian criminal slang. By any name, it’s burglary. Specific Examples: Cat burglar in Naples, Bulgarian NIS officer INVESTIGATIVE ABILITIES: on the Riviera, Bundespolizei handling “renditions” for the CIA. Bureaucracy 1, Forgery 4, museum security specialist, INVESTIGATIVE ABILITIES: Bureaucracy Photography 1 DGSE or Mossad covert entry 2, Cop Talk 1, Criminology Alternates: Cryptography specialist, NSA contractor. 2, Urban Survival 1 GENERAL ABILITIES: Cover 6, INVESTIGATIVE ABILITIES: Data Alternates: Chemistry, Data Digital Intrusion 4, Disguise 2, Recovery 1, Electronic Surveillance 2, Recovery, Electronic Surveillance, Infiltration 4, Mechanics 2 Photography 2, Streetwise 1 Notice, Streetwise Alternates: Architecture, Notice GENERAL ABILITIES: Conceal 6, Cuckoo GENERAL ABILITIES: Conceal 2, Digital Disguise 2, Driving 4, Explosive The cuckoo lays its eggs in another bird’s Intrusion 2, Filch 6, Infiltration 8 Devices 2, Infiltration 2, Stability 2 nest, convincing the stranger to raise its Alternates: Preparedness Alternates: Digital Intrusion chicks. -

Military and Strategic Affairs
Military and Strategic Affairs Military and Strategic Military and Strategic Affairs Volume 6 | No. 3 | December 2014 From Plowshares to Swords? UN Forces on Israel’s Borders in the Second Decade of the Twenty-First Century Chen Kertcher Hasn’t the Time Come for the Political Training of Senior IDF Ocers? Yoram Peri The RMA Theory and Small States Francis Domingo A Multidisciplinary Analysis of Cyber Information Sharing Aviram Zrahia Yemen: A Mirror to the Future of the Arab Spring Sami Kronenfeld and Yoel Guzansky Managing Intellectual Property in the Defense Establishment: Opportunities and Risks Shmuel Even and Yesha Sivan And What If We Did Not Deter Hizbollah? Yagil Henkin המכון למחקרי ביטחון לאומי THE INSTITUTE FOR NATIONAL SECURITYc STUDIES INCORPORATING THE JAFFEE bd CENTER FOR STRATEGIC STUDIES ISSN 2307-193X (print) • E-ISSN 2307-8634 (online) Military and Strategic Affairs Volume 6 | No. 3 | December 2014 CONTENTS From Plowshares to Swords? UN Forces on Israel’s Borders in the Second Decade of the Twenty-First Century | 3 Chen Kertcher Hasn’t the Time Come for the Political Training of Senior IDF Officers? | 17 Yoram Peri The RMA Theory and Small States | 43 Francis Domingo A Multidisciplinary Analysis of Cyber Information Sharing | 59 Aviram Zrahia Yemen: A Mirror to the Future of the Arab Spring | 79 Sami Kronenfeld and Yoel Guzansky Managing Intellectual Property in the Defense Establishment: Opportunities and Risks | 101 Shmuel Even and Yesha Sivan And What If We Did Not Deter Hizbollah? | 123 Yagil Henkin The purpose of Military and Strategic Affairs is to stimulate Military and and enrich the public debate on military issues relating to Strategic Affairs Israel’s national security. -

United States District Court for the District of Columbia
Case 1:10-cv-02119-RMC Document 44 Filed 11/02/12 Page 1 of 8 UNITED STATES DISTRICT COURT FOR THE DISTRICT OF COLUMBIA ) ANTHONY SHAFFER, ) ) ) Plaintiff, ) ) v. ) Civil Action No. 10-2119 (RMC) ) DEFENSE INTELLIGENCE AGENCY, ) et al., ) ) Defendants. ) ) MEMORANDUM OPINION Plaintiff Anthony Shaffer is an intelligence officer who was employed with the Defense Intelligence Agency, an operational component of the Department of Defense, from 1995-2006. After this, he joined the U.S. Army Reserve and retired as Lieutenant Colonel in 2011. Mr. Shaffer served two tours of duty in Afghanistan. Together with a ghost writer, Mr. Shaffer authored a book entitled Operation Dark Heart: Spycraft and Special Ops on the Frontlines of Afghanistan and the Path to Victory, which he describes as an eyewitness account of the 2003 “tipping point” of the war in Afghanistan. He is required by several secrecy agreements to submit all of his writings for prepublication review to ensure they do not contain classified information. Mr. Shaffer complains that several executive agencies improperly designated certain information in his book as classified and imposed a restraint on his First Amendment right to publish his book. The agencies assert that Mr. Shaffer lacks standing to bring his claim because he sold control of his book to his publisher in the United States; they move to dismiss the Amended Complaint. The motion will be denied. Mr. Shaffer has standing Case 1:10-cv-02119-RMC Document 44 Filed 11/02/12 Page 2 of 8 because he maintains rights to publish an unredacted version of his book and, if the redactions are overbroad, to otherwise “publish” the non-classified information in his book. -

Kean-Hamilton Statement on ABLE DANGER
August 12, 2005 Kean-Hamilton Statement on ABLE DANGER Thomas H. Kean and Lee H. Hamilton, former Chair and Vice Chair of the National Commission on Terrorist Attacks Upon the United States (9/11 Commission),in response to media inquiries about the Commission’s investigation of the ABLE DANGER program, today released the following statement: On October 21, 2003, Philip Zelikow, the executive director of the 9/11 Commission, two senior Commission staff members, and a representative of the executive branch, met at Bagram Base, Afghanistan, with three individuals doing intelligence work for the Department of Defense. One of the men, in recounting information about al Qaeda’s activities in Afghanistan before 9/11, referred to a DOD program known as ABLE DANGER. He said this program was now closed, but urged Commission staff to get the files on this program and review them, as he thought the Commission would find information about al Qaeda and Bin Ladin that had been developed before the 9/11 attack. He also complained that Congress, particularly the House Permanent Select Committee on Intelligence (HPSCI), had effectively ended a human intelligence network he considered valuable. As with their other meetings, Commission staff promptly prepared a memorandum for the record. That memorandum, prepared at the time, does not record any mention of Mohamed Atta or any of the other future hijackers, or any suggestion that their identities were known to anyone at DOD before 9/11. Nor do any of the three Commission staffers who participated in the interview, or the executive branch lawyer, recall hearing any such allegation. -

Prepublication Review in the Intelligence Community
TILL DEATH DO US PART: PREPUBLICATION REVIEW IN THE INTELLIGENCE COMMUNITY Kevin Casey* As a condition of access to classified information, most employees of the U.S. intelligence community are required to sign nondisclosure agreements that mandate lifetime prepublication review. In essence, these agreements require employees to submit any works that discuss their experiences working in the intelligence community---whether writ- ten or oral, fiction or nonfiction---to their respective agencies and receive approval before seeking publication. Though these agreements constitute an exercise of prior restraint, the Supreme Court has held them constitu- tional. This Note does not argue fororagainsttheconstitutionality of prepublication review; instead, it explores how prepublication review is actually practiced by agencies and concludes that thecurrentsystem, which lacks executive-branch-wide guidance, grants too much discretion to individual agencies. It compares the policies of individual agencies with the experiences of actual authors who have clashed with prepublication-review boards to argue that agencies conduct review in a manner that is inconsistent at best, and downright biased and discriminatory at worst. The level of secrecy shrouding intelligence agencies and the concomitant dearth of publicly available information about their activi- ties make it difcult to evaluate their performance and, by extension, the performance of our electedofcials in overseeing such activities. In such circumstances, memoirs and other forms of expression -

The Rise of Radical Islam and Effectiveness of Counter-Terrorism in a Global Age Written by Zaki Mehta
The Rise of Radical Islam and Effectiveness of Counter-Terrorism in a Global Age Written by Zaki Mehta This PDF is auto-generated for reference only. As such, it may contain some conversion errors and/or missing information. For all formal use please refer to the official version on the website, as linked below. The Rise of Radical Islam and Effectiveness of Counter- Terrorism in a Global Age https://www.e-ir.info/2011/09/20/the-rise-of-radical-islam-and-effectiveness-of-counter-terrorism-in-a-global-age/ ZAKI MEHTA, SEP 20 2011 Terrorism, one may argue, has existed for as long as man himself. Regardless of its aims, terrorism has throughout time continually changed in form due to ever changing factors such as; the perpetrators, means, motivation and the victims. Subsequently so have the methods with which to counter terrorism. Since the beginning of the twenty-first century there has been a stark shift in the global perception of terrorism and its cause. As a consequence of such a shift it is fair to say that there has been a direct change in the measures taken in order to halt terrorism. This dissertation seeks to discuss the origins and rise of radical Islam as the new so called ‘terror’ and the subsequent development and transition of counter-terrorism in the post September 11th 2001 period. Specifically, this essay seeks to discuss the development of counter-terrorism in relation to the pivotal concept of radical Islam. Rightly or wrongly radical Islam is perceived as the modern day global ‘terror’ and it will be used in this dissertation in order to assess the evolution of counter-terrorism in the twenty first century. -

ENDNOTES Endnotes
CHAPTER 1 ENDNOTES Endnotes 1 Guantánamo Remarks Cost Policy Chief His Job, CNN (Feb. 2, 2007), available at http://www.cnn. com/2007/US/02/02/gitmo.resignation (“When corporate CEOs see that those firms are representing the very terrorists who hit their bottom line back in 2001, those CEOs are going to make those law firms choose between representing terrorists or representing reputable firms.”). 2 Task Force staff interview with Moazzam Begg, Omar Deghayes, Bisher al-Rawi (Apr. 17, 2012) [hereinafter Begg, Deghayes, al-Rawi Interview]. 3 Neil A. Lewis, U.S. Military Eroding Trust of Detainees, Lawyers Say, N.Y. TIMES (Mar. 9, 2005), available at http://www.nytimes.com/2005/03/08/world/americas/08iht-gitmo.html (“Another lawyer, Marc Falkoff of New York, whose firm represents several Yemenis at the naval base in Cuba, said some of his clients had told him that a person who said he was a lawyer and had civilian clothes had conferred several times with some detainees. That person, Falkoff said his clients had told him, later appeared at the detention center in uniform, leading the inmates to distrust anyone claiming to be a lawyer and acting in their interest.”). See also Neil A. Lewis, Detainee’s Lawyer Says Captors Foment Mistrust, N.Y. TIMES (Dec. 7, 2005), available at http://www.nytimes.com/2005/12/07/international/07hamdan.html (“The Guantánamo authorities violated a court order by moving a prisoner from the general population there and placing him in close contact with a hard-core operative for Al Qaeda known for urging detainees to refuse to cooperate with their lawyers, according to papers filed with the United States District Court here by Lt.