Moving Forward: Forward Secrecy in Openpgp
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

A History of End-To-End Encryption and the Death of PGP
25/05/2020 A history of end-to-end encryption and the death of PGP Hey! I'm David, a security engineer at the Blockchain team of Facebook (https://facebook.com/), previously a security consultant for the Cryptography Services of NCC Group (https://www.nccgroup.com). I'm also the author of the Real World Cryptography book (https://www.manning.com/books/real-world- cryptography?a_aid=Realworldcrypto&a_bid=ad500e09). This is my blog about cryptography and security and other related topics that I Ûnd interesting. A history of end-to-end encryption and If you don't know where to start, you might want to check these popular the death of PGP articles: posted January 2020 - How did length extension attacks made it 1981 - RFC 788 - Simple Mail Transfer Protocol into SHA-2? (/article/417/how-did-length- extension-attacks-made-it-into-sha-2/) (https://tools.ietf.org/html/rfc788) (SMTP) is published, - Speed and Cryptography the standard for email is born. (/article/468/speed-and-cryptography/) - What is the BLS signature scheme? (/article/472/what-is-the-bls-signature- This is were everything starts, we now have an open peer-to-peer scheme/) protocol that everyone on the internet can use to communicate. - Zero'ing memory, compiler optimizations and memset_s (/article/419/zeroing-memory- compiler-optimizations-and-memset_s/) 1991 - The 9 Lives of Bleichenbacher's CAT: New Cache ATtacks on TLS Implementations The US government introduces the 1991 Senate Bill 266, (/article/461/the-9-lives-of-bleichenbachers- which attempts to allow "the Government to obtain the cat-new-cache-attacks-on-tls- plain text contents of voice, data, and other implementations/) - How to Backdoor Di¸e-Hellman: quick communications when appropriately authorized by law" explanation (/article/360/how-to-backdoor- from "providers of electronic communications services di¸e-hellman-quick-explanation/) and manufacturers of electronic communications - Tamarin Prover Introduction (/article/404/tamarin-prover-introduction/) service equipment". -

CS 255: Intro to Cryptography 1 Introduction 2 End-To-End
Programming Assignment 2 Winter 2021 CS 255: Intro to Cryptography Prof. Dan Boneh Due Monday, March 1st, 11:59pm 1 Introduction In this assignment, you are tasked with implementing a secure and efficient end-to-end encrypted chat client using the Double Ratchet Algorithm, a popular session setup protocol that powers real- world chat systems such as Signal and WhatsApp. As an additional challenge, assume you live in a country with government surveillance. Thereby, all messages sent are required to include the session key encrypted with a fixed public key issued by the government. In your implementation, you will make use of various cryptographic primitives we have discussed in class—notably, key exchange, public key encryption, digital signatures, and authenticated encryption. Because it is ill-advised to implement your own primitives in cryptography, you should use an established library: in this case, the Stanford Javascript Crypto Library (SJCL). We will provide starter code that contains a basic template, which you will be able to fill in to satisfy the functionality and security properties described below. 2 End-to-end Encrypted Chat Client 2.1 Implementation Details Your chat client will use the Double Ratchet Algorithm to provide end-to-end encrypted commu- nications with other clients. To evaluate your messaging client, we will check that two or more instances of your implementation it can communicate with each other properly. We feel that it is best to understand the Double Ratchet Algorithm straight from the source, so we ask that you read Sections 1, 2, and 3 of Signal’s published specification here: https://signal. -

The Double Ratchet Algorithm
The Double Ratchet Algorithm Trevor Perrin (editor) Moxie Marlinspike Revision 1, 2016-11-20 Contents 1. Introduction 3 2. Overview 3 2.1. KDF chains . 3 2.2. Symmetric-key ratchet . 5 2.3. Diffie-Hellman ratchet . 6 2.4. Double Ratchet . 13 2.6. Out-of-order messages . 17 3. Double Ratchet 18 3.1. External functions . 18 3.2. State variables . 19 3.3. Initialization . 19 3.4. Encrypting messages . 20 3.5. Decrypting messages . 20 4. Double Ratchet with header encryption 22 4.1. Overview . 22 4.2. External functions . 26 4.3. State variables . 26 4.4. Initialization . 26 4.5. Encrypting messages . 27 4.6. Decrypting messages . 28 5. Implementation considerations 29 5.1. Integration with X3DH . 29 5.2. Recommended cryptographic algorithms . 30 6. Security considerations 31 6.1. Secure deletion . 31 6.2. Recovery from compromise . 31 6.3. Cryptanalysis and ratchet public keys . 31 1 6.4. Deletion of skipped message keys . 32 6.5. Deferring new ratchet key generation . 32 6.6. Truncating authentication tags . 32 6.7. Implementation fingerprinting . 32 7. IPR 33 8. Acknowledgements 33 9. References 33 2 1. Introduction The Double Ratchet algorithm is used by two parties to exchange encrypted messages based on a shared secret key. Typically the parties will use some key agreement protocol (such as X3DH [1]) to agree on the shared secret key. Following this, the parties will use the Double Ratchet to send and receive encrypted messages. The parties derive new keys for every Double Ratchet message so that earlier keys cannot be calculated from later ones. -

Security Analysis of the Signal Protocol Student: Bc
ASSIGNMENT OF MASTER’S THESIS Title: Security Analysis of the Signal Protocol Student: Bc. Jan Rubín Supervisor: Ing. Josef Kokeš Study Programme: Informatics Study Branch: Computer Security Department: Department of Computer Systems Validity: Until the end of summer semester 2018/19 Instructions 1) Research the current instant messaging protocols, describe their properties, with a particular focus on security. 2) Describe the Signal protocol in detail, its usage, structure, and functionality. 3) Select parts of the protocol with a potential for security vulnerabilities. 4) Analyze these parts, particularly the adherence of their code to their documentation. 5) Discuss your findings. Formulate recommendations for the users. References Will be provided by the supervisor. prof. Ing. Róbert Lórencz, CSc. doc. RNDr. Ing. Marcel Jiřina, Ph.D. Head of Department Dean Prague January 27, 2018 Czech Technical University in Prague Faculty of Information Technology Department of Computer Systems Master’s thesis Security Analysis of the Signal Protocol Bc. Jan Rub´ın Supervisor: Ing. Josef Kokeˇs 1st May 2018 Acknowledgements First and foremost, I would like to express my sincere gratitude to my thesis supervisor, Ing. Josef Kokeˇs,for his guidance, engagement, extensive know- ledge, and willingness to meet at our countless consultations. I would also like to thank my brother, Tom´aˇsRub´ın,for proofreading my thesis. I cannot express enough gratitude towards my parents, Lenka and Jaroslav Rub´ınovi, who supported me both morally and financially through my whole studies. Last but not least, this thesis would not be possible without Anna who re- lentlessly supported me when I needed it most. Declaration I hereby declare that the presented thesis is my own work and that I have cited all sources of information in accordance with the Guideline for adhering to ethical principles when elaborating an academic final thesis. -

Analysis and Implementation of the Messaging Layer Security Protocol
View metadata, citation and similar papers at core.ac.uk brought to you by CORE provided by AMS Tesi di Laurea Alma Mater Studiorum · Universita` di Bologna CAMPUS DI CESENA Dipartimento di Informatica - Scienza e Ingegneria Corso di Laurea Magistrale in Ingegneria e Scienze Informatiche Analysis and Implementation of the Messaging Layer Security Protocol Tesi in Sicurezza delle Reti Relatore: Presentata da: Gabriele D'Angelo Nicola Giancecchi Anno Accademico 2018/2019 Parole chiave Network Security Messaging MLS Protocol Ratchet Trees \Oh me, oh vita! Domande come queste mi perseguitano. Infiniti cortei d'infedeli, citt`agremite di stolti, che v'`edi nuovo in tutto questo, oh me, oh vita! Risposta: Che tu sei qui, che la vita esiste e l’identit`a. Che il potente spettacolo continua, e che tu puoi contribuire con un verso." - Walt Whitman Alla mia famiglia. Introduzione L'utilizzo di servizi di messaggistica su smartphone `eincrementato in maniera considerevole negli ultimi anni, complice la sempre maggiore disponi- bilit`adi dispositivi mobile e l'evoluzione delle tecnologie di comunicazione via Internet, fattori che hanno di fatto soppiantato l'uso dei classici SMS. Tale incremento ha riguardato anche l'utilizzo in ambito business, un contesto dove `epi`ufrequente lo scambio di informazioni confidenziali e quindi la necessit`adi proteggere la comunicazione tra due o pi`upersone. Ci`onon solo per un punto di vista di sicurezza, ma anche di privacy personale. I maggiori player mondiali hanno risposto implementando misure di sicurezza all'interno dei propri servizi, quali ad esempio la crittografia end-to-end e regole sempre pi`ustringenti sul trattamento dei dati personali. -

Detecting and Preventing Active Attacks Against Autocrypt Release 0.10.0
Detecting and preventing active attacks against Autocrypt Release 0.10.0 NEXTLEAP researchers Jan 09, 2020 Contents 1 Introduction2 1.1 Attack model and terminology............................2 1.2 Problems of current key-verification techniques...................3 1.3 Integrating key verification with general workflows.................3 1.4 Supplementary key consistency through ClaimChains................4 1.5 Detecting inconsistencies through Gossip and DKIM................5 2 Securing communications against network adversaries6 2.1 Setup Contact protocol................................7 2.2 Verified Group protocol................................ 12 2.3 History-verification protocol............................. 17 2.4 Verifying keys through onion-queries......................... 20 3 Key consistency with ClaimChains 23 3.1 High level overview of the ClaimChain design.................... 23 3.2 Use and architecture................................. 24 3.3 Evaluating ClaimChains to guide verification.................... 26 4 Using Autocrypt key gossip to guide key verification 28 4.1 Attack Scenarios................................... 28 4.2 Probability of detecting an attack through out of band verification......... 29 5 Using DKIM signature checks to guide key verification 32 5.1 DKIM Signatures on Autocrypt Headers....................... 32 5.2 Device loss and MITM attacks............................ 33 5.3 Open Questions.................................... 34 1 1 Introduction This document considers how to secure Autocrypt1-capable mail apps against active network at- tackers. Autocrypt aims to achieve convenient end-to-end encryption of e-mail. The Level 1 Autocrypt specification offers users opt-in e-mail encryption, but only considers passive adver- saries. Active network adversaries, who could, for example, tamper with the Autocrypt header during e-mail message transport, are not considered in the Level 1 specification. Yet, such active attackers might undermine the security of Autocrypt. -

Is Bob Sending Mixed Signals?
Is Bob Sending Mixed Signals? Michael Schliep Ian Kariniemi Nicholas Hopper University of Minnesota University of Minnesota University of Minnesota [email protected] [email protected] [email protected] ABSTRACT Demand for end-to-end secure messaging has been growing rapidly and companies have responded by releasing applications that imple- ment end-to-end secure messaging protocols. Signal and protocols based on Signal dominate the secure messaging applications. In this work we analyze conversational security properties provided by the Signal Android application against a variety of real world ad- versaries. We identify vulnerabilities that allow the Signal server to learn the contents of attachments, undetectably re-order and drop messages, and add and drop participants from group conversations. We then perform proof-of-concept attacks against the application to demonstrate the practicality of these vulnerabilities, and suggest mitigations that can detect our attacks. The main conclusion of our work is that we need to consider more than confidentiality and integrity of messages when designing future protocols. We also stress that protocols must protect against compromised servers and at a minimum implement a trust but verify model. 1 INTRODUCTION (a) Alice’s view of the conversa-(b) Bob’s view of the conversa- Recently many software developers and companies have been inte- tion. tion. grating end-to-end encrypted messaging protocols into their chat applications. Some applications implement a proprietary protocol, Figure 1: Speaker inconsistency in a conversation. such as Apple iMessage [1]; others, such as Cryptocat [7], imple- ment XMPP OMEMO [17]; but most implement the Signal protocol or a protocol based on Signal, including Open Whisper Systems’ caching. -

Security & Privacy for Mobile Phones
Security & Privacy FOR Mobile Phones Carybé, Lucas Helfstein July 4, 2017 Instituto DE Matemática E Estatística - USP What IS security? • That GRANTS THE INFORMATION YOU PROVIDE THE ASSURANCES above; • That ENSURES THAT EVERY INDIVIDUAL IN THIS SYSTEM KNOWS EACH other; • That TRIES TO KEEP THE ABOVE PROMISES forever. Security IS ... A System! • That ASSURES YOU THE INTEGRITY AND AUTHENTICITY OF AN INFORMATION AS WELL AS ITS authors; 1 • That ENSURES THAT EVERY INDIVIDUAL IN THIS SYSTEM KNOWS EACH other; • That TRIES TO KEEP THE ABOVE PROMISES forever. Security IS ... A System! • That ASSURES YOU THE INTEGRITY AND AUTHENTICITY OF AN INFORMATION AS WELL AS ITS authors; • That GRANTS THE INFORMATION YOU PROVIDE THE ASSURANCES above; 1 • That TRIES TO KEEP THE ABOVE PROMISES forever. Security IS ... A System! • That ASSURES YOU THE INTEGRITY AND AUTHENTICITY OF AN INFORMATION AS WELL AS ITS authors; • That GRANTS THE INFORMATION YOU PROVIDE THE ASSURANCES above; • That ENSURES THAT EVERY INDIVIDUAL IN THIS SYSTEM KNOWS EACH other; 1 Security IS ... A System! • That ASSURES YOU THE INTEGRITY AND AUTHENTICITY OF AN INFORMATION AS WELL AS ITS authors; • That GRANTS THE INFORMATION YOU PROVIDE THE ASSURANCES above; • That ENSURES THAT EVERY INDIVIDUAL IN THIS SYSTEM KNOWS EACH other; • That TRIES TO KEEP THE ABOVE PROMISES forever. 1 Security IS ... A System! Eve | | | Alice "Hi" <---------------> "Hi" Bob 2 Security IS ... Cryptography! Eve | | | Alice "Hi" <----"*****"------> "Hi" Bob 3 Security IS ... Impossible! The ONLY TRULY SECURE SYSTEM IS ONE THAT IS POWERED off, CAST IN A BLOCK OF CONCRETE AND SEALED IN A lead-lined ROOM WITH ARMED GUARDS - AND EVEN THEN I HAVE MY doubts. -

Signal E2E-Crypto Why Can’T I Hold All These Ratchets
Signal E2E-Crypto Why Can’t I Hold All These Ratchets oxzi 23.03.2021 In the next 30 minutes there will be I a rough introduction in end-to-end encrypted instant messaging, I an overview of how Signal handles those E2E encryption, I and finally a demo based on a WeeChat plugin. Historical Background I Signal has not reinvented the wheel - and this is a good thing! I Goes back to Off-the-Record Communication (OTR)1. OTR Features I Perfect forward secrecy I Deniable authentication 1Borisov, Goldberg, and Brewer. “Off-the-record communication, or, why not to use PGP”, 2004 Influence and Evolution I OTR influenced the Signal Protocol, Double Ratchet. I Double Ratchet influence OMEMO; supports many-to-many communication. I Also influenced Olm, E2E encryption of the Matrix protocol. I OTR itself was influenced by this, version four was introduced in 2018. Double Ratchet The Double Ratchet algorithm is used by two parties to exchange encrypted messages based on a shared secret key. The Double Ratchet algorithm2 is essential in Signal’s E2E crypto. But first, some basics. 2Perrin, and Marlinspike. “The Double Ratchet Algorithm”, 2016 Cryptographic Ratchet A ratchet is a cryptographic function that only moves forward. In other words, one cannot easily reverse its output. Triple Ratchet, I guess.3 3By Salvatore Capalbi, https://www.flickr.com/photos/sheldonpax/411551322/, CC BY-SA 2.5 Symmetric-Key Ratchet Symmetric-Key Ratchet In everyday life, Keyed-Hash Message Authentication Code (HMAC) or HMAC-based KDFs (HKDF) are used. func ratchet(ckIn[]byte)(ckOut, mk[]byte){ kdf := hmac.New(sha256.New, ckIn) kdf.Write(c) // publicly known constant c out := kdf.Sum(nil) return out[:32], out[32:] } ck0 :=[]byte{0x23, 0x42, ...} // some initial shared secret ck1, mk1 := ratchet(ck0) ck2, mk2 := ratchet(ck1) Diffie-Hellman Key Exchange Diffie-Hellman Key Exchange Diffie-Hellman Key Exchange Originally, DH uses primitive residue classes modulo n. -
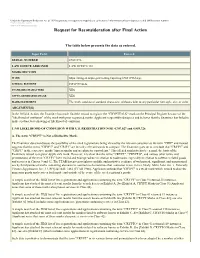
Request for Reconsideration After Final Action
Under the Paperwork Reduction Act of 1995 no persons are required to respond to a collection of information unless it displays a valid OMB control number. PTO Form 1960 (Rev 10/2011) OMB No. 0651-0050 (Exp 09/20/2020) Request for Reconsideration after Final Action The table below presents the data as entered. Input Field Entered SERIAL NUMBER 87031396 LAW OFFICE ASSIGNED LAW OFFICE 116 MARK SECTION MARK https://tmng-al.uspto.gov/resting2/api/img/87031396/large LITERAL ELEMENT CRYPTTALK STANDARD CHARACTERS YES USPTO-GENERATED IMAGE YES MARK STATEMENT The mark consists of standard characters, without claim to any particular font style, size or color. ARGUMENT(S) In the Official Action, the Examiner has made final the refusal to register the "CRYPTTALK" mark on the Principal Register because of the "likelihood of confusion" of the mark with prior registered marks. Applicant respectfully disagrees and believes that the Examiner has failed to make a prima facie showing of likelihood of confusion. I. NO LIKELIHOOD OF CONFUSION WITH U.S. REGISTRATION NOS. 4,707,027 and 4,859,726 A. The term "CRYPT" is Not a Distinctive Mark. The Examiner does not discuss the possibility of the cited registrations being viewed by the relevant consumer as the term "CRIP" and instead suggests that the terms "CRYPT" and "CRIPT" are the only relevant words to compare. The Examiner goes on to conclude that "CRYPT" and "CRIPT" in the respective marks "appear similar and are phonetic equivalents." This alleged similarity has been made the basis of the Examiners refusal to register Applicant's mark. -

Modern End-To-End Encrypted Messaging for the Desktop
Die approbierte Originalversion dieser Diplom-/ Masterarbeit ist in der Hauptbibliothek der Tech- nischen Universität Wien aufgestellt und zugänglich. http://www.ub.tuwien.ac.at The approved original version of this diploma or master thesis is available at the main library of the Vienna University of Technology. http://www.ub.tuwien.ac.at/eng Modern End-to-End Encrypted Messaging for the Desktop DIPLOMARBEIT zur Erlangung des akademischen Grades Diplom-Ingenieur im Rahmen des Studiums Software Engineering and Internet Computing eingereicht von Richard Bayerle Matrikelnummer 1025259 an der Fakultät für Informatik der Technischen Universität Wien Betreuung: Privatdozent Dipl.Ing. Mag. Dr. Edgar Weippl Mitwirkung: Dr. Martin Schmiedecker Wien, 2. Oktober 2017 Richard Bayerle Edgar Weippl Technische Universität Wien A-1040 Wien Karlsplatz 13 Tel. +43-1-58801-0 www.tuwien.ac.at Modern End-to-End Encrypted Messaging for the Desktop DIPLOMA THESIS submitted in partial fulfillment of the requirements for the degree of Diplom-Ingenieur in Software Engineering and Internet Computing by Richard Bayerle Registration Number 1025259 to the Faculty of Informatics at the TU Wien Advisor: Privatdozent Dipl.Ing. Mag. Dr. Edgar Weippl Assistance: Dr. Martin Schmiedecker Vienna, 2nd October, 2017 Richard Bayerle Edgar Weippl Technische Universität Wien A-1040 Wien Karlsplatz 13 Tel. +43-1-58801-0 www.tuwien.ac.at Erklärung zur Verfassung der Arbeit Richard Bayerle Seestraße 67 78315 Radolfzell am Bodensee Deutschland Hiermit erkläre ich, dass ich diese Arbeit selbständig verfasst habe, dass ich die verwen- deten Quellen und Hilfsmittel vollständig angegeben habe und dass ich die Stellen der Arbeit – einschließlich Tabellen, Karten und Abbildungen –, die anderen Werken oder dem Internet im Wortlaut oder dem Sinn nach entnommen sind, auf jeden Fall unter Angabe der Quelle als Entlehnung kenntlich gemacht habe. -

Easy Encryption for Email, Photo, and Other Cloud Services John Seunghyun Koh
Easy Encryption for Email, Photo, and Other Cloud Services John Seunghyun Koh Submitted in partial fulfillment of the requirements for the degree of Doctor of Philosophy under the Executive Committee of the Graduate School of Arts and Sciences COLUMBIA UNIVERSITY 2021 © 2021 John Seunghyun Koh All Rights Reserved Abstract Easy Encryption for Email, Photo, and Other Cloud Services John Seunghyun Koh Modern users carry mobile devices with them at nearly all times, and this likely has contribut- ed to the rapid growth of private user data—such as emails, photos, and more—stored online in the cloud. Unfortunately, the security of many cloud services for user data is lacking, and the vast amount of user data stored in the cloud is an attractive target for adversaries. Even a single compro- mise of a user’s account yields all its data to attackers. A breach of an unencrypted email account gives the attacker full access to years, even decades, of emails. Ideally, users would encrypt their data to prevent this. However, encrypting data at rest has long been considered too difficult for users, even technical ones, mainly due to the confusing nature of managing cryptographic keys. My thesis is that strong security can be made easy to use through client-side encryption using self-generated per-device cryptographic keys, such that user data in cloud services is well pro- tected, encryption is transparent and largely unnoticeable to users even on multiple devices, and encryption can be used with existing services without any server-side modifications. This dis- sertation introduces a new paradigm for usable cryptographic key management, Per-Device Keys (PDK), and explores how self-generated keys unique to every device can enable new client-side encryption schemes that are compatible with existing online services yet are transparent to users.