Smarx OS Compendium 2020 for the CRYPTO-BOX
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

A History of End-To-End Encryption and the Death of PGP
25/05/2020 A history of end-to-end encryption and the death of PGP Hey! I'm David, a security engineer at the Blockchain team of Facebook (https://facebook.com/), previously a security consultant for the Cryptography Services of NCC Group (https://www.nccgroup.com). I'm also the author of the Real World Cryptography book (https://www.manning.com/books/real-world- cryptography?a_aid=Realworldcrypto&a_bid=ad500e09). This is my blog about cryptography and security and other related topics that I Ûnd interesting. A history of end-to-end encryption and If you don't know where to start, you might want to check these popular the death of PGP articles: posted January 2020 - How did length extension attacks made it 1981 - RFC 788 - Simple Mail Transfer Protocol into SHA-2? (/article/417/how-did-length- extension-attacks-made-it-into-sha-2/) (https://tools.ietf.org/html/rfc788) (SMTP) is published, - Speed and Cryptography the standard for email is born. (/article/468/speed-and-cryptography/) - What is the BLS signature scheme? (/article/472/what-is-the-bls-signature- This is were everything starts, we now have an open peer-to-peer scheme/) protocol that everyone on the internet can use to communicate. - Zero'ing memory, compiler optimizations and memset_s (/article/419/zeroing-memory- compiler-optimizations-and-memset_s/) 1991 - The 9 Lives of Bleichenbacher's CAT: New Cache ATtacks on TLS Implementations The US government introduces the 1991 Senate Bill 266, (/article/461/the-9-lives-of-bleichenbachers- which attempts to allow "the Government to obtain the cat-new-cache-attacks-on-tls- plain text contents of voice, data, and other implementations/) - How to Backdoor Di¸e-Hellman: quick communications when appropriately authorized by law" explanation (/article/360/how-to-backdoor- from "providers of electronic communications services di¸e-hellman-quick-explanation/) and manufacturers of electronic communications - Tamarin Prover Introduction (/article/404/tamarin-prover-introduction/) service equipment". -

Security Target
Acronis SCS Acronis Cyber Backup 12.5 SCS Hardened Edition Server v12.5 Security Target Document Version: 0.14 Prepared for: Prepared by: Acronis SCS Corsec Security, Inc. 6370 E. Thomas Road, Suite 250 13921 Park Center Road, Suite 460 Scottsdale, AZ 85251 Herndon, VA 20171 United States of America United States of America Phone: +1 781 782 9000 Phone: +1 703 267 6050 www.acronisscs.com www.corsec.com Security Target, Version 0.14 August 19, 2020 Table of Contents 1. Introduction .......................................................................................................................................................4 1.1 Purpose .....................................................................................................................................................4 1.2 Security Target and TOE References .........................................................................................................4 1.3 Product Overview ......................................................................................................................................5 1.3.1 Product Components........................................................................................................................5 1.4 TOE Overview ............................................................................................................................................6 1.4.1 TOE Environment..............................................................................................................................7 1.5 -

Detecting and Preventing Active Attacks Against Autocrypt Release 0.10.0
Detecting and preventing active attacks against Autocrypt Release 0.10.0 NEXTLEAP researchers Jan 09, 2020 Contents 1 Introduction2 1.1 Attack model and terminology............................2 1.2 Problems of current key-verification techniques...................3 1.3 Integrating key verification with general workflows.................3 1.4 Supplementary key consistency through ClaimChains................4 1.5 Detecting inconsistencies through Gossip and DKIM................5 2 Securing communications against network adversaries6 2.1 Setup Contact protocol................................7 2.2 Verified Group protocol................................ 12 2.3 History-verification protocol............................. 17 2.4 Verifying keys through onion-queries......................... 20 3 Key consistency with ClaimChains 23 3.1 High level overview of the ClaimChain design.................... 23 3.2 Use and architecture................................. 24 3.3 Evaluating ClaimChains to guide verification.................... 26 4 Using Autocrypt key gossip to guide key verification 28 4.1 Attack Scenarios................................... 28 4.2 Probability of detecting an attack through out of band verification......... 29 5 Using DKIM signature checks to guide key verification 32 5.1 DKIM Signatures on Autocrypt Headers....................... 32 5.2 Device loss and MITM attacks............................ 33 5.3 Open Questions.................................... 34 1 1 Introduction This document considers how to secure Autocrypt1-capable mail apps against active network at- tackers. Autocrypt aims to achieve convenient end-to-end encryption of e-mail. The Level 1 Autocrypt specification offers users opt-in e-mail encryption, but only considers passive adver- saries. Active network adversaries, who could, for example, tamper with the Autocrypt header during e-mail message transport, are not considered in the Level 1 specification. Yet, such active attackers might undermine the security of Autocrypt. -

Microsoft Windows Common Criteria Evaluation Security Target
Microsoft Common Criteria Security Target Microsoft Windows Common Criteria Evaluation Microsoft Windows 10 version 1809 (October 2018 Update) Microsoft Windows Server 2019 (October 2018 Update) Security Target Document Information Version Number 0.05 Updated On June 18, 2019 Microsoft © 2019 Page 1 of 126 Microsoft Common Criteria Security Target Version History Version Date Summary of changes 0.01 June 27, 2018 Initial draft 0.02 December 21, 2018 Updates from security target evaluation 0.03 February 21, 2019 Updates from evaluation 0.04 May 6, 2019 Updates from GPOS PP v4.2.1 0.05 June 18, 2019 Public version Microsoft © 2019 Page 2 of 126 Microsoft Common Criteria Security Target This is a preliminary document and may be changed substantially prior to final commercial release of the software described herein. The information contained in this document represents the current view of Microsoft Corporation on the issues discussed as of the date of publication. Because Microsoft must respond to changing market conditions, it should not be interpreted to be a commitment on the part of Microsoft, and Microsoft cannot guarantee the accuracy of any information presented after the date of publication. This document is for informational purposes only. MICROSOFT MAKES NO WARRANTIES, EXPRESS OR IMPLIED, AS TO THE INFORMATION IN THIS DOCUMENT. Complying with all applicable copyright laws is the responsibility of the user. This work is licensed under the Creative Commons Attribution-NoDerivs- NonCommercial License (which allows redistribution of the work). To view a copy of this license, visit http://creativecommons.org/licenses/by-nd-nc/1.0/ or send a letter to Creative Commons, 559 Nathan Abbott Way, Stanford, California 94305, USA. -

Microsoft Windows Vista and Windows Server 2008 EAL1 Security Target
Microsoft Windows Vista and Windows Server 2008 EAL1 Security Target Version 1.0 August 14, 2008 Prepared For: Microsoft Corporation Corporate Headquarters One Microsoft Way Redmond, WA 98052-6399 Prepared By: Science Applications International Corporation Common Criteria Testing Laboratory 7125 Gateway Drive Columbia, MD 21046-2554 Version 1.0, 8/14/2008 This is a preliminary document and may be changed substantially prior to final commercial release of the software described herein. The information contained in this document represents the current view of Microsoft Corporation on the issues discussed as of the date of publication. Because Microsoft must respond to changing market conditions, it should not be interpreted to be a commitment on the part of Microsoft, and Microsoft cannot guarantee the accuracy of any information presented after the date of publication. This document is for informational purposes only. MICROSOFT MAKES NO WARRANTIES, EXPRESS OR IMPLIED, AS TO THE INFORMATION IN THIS DOCUMENT. Complying with all applicable copyright laws is the responsibility of the user. This work is licensed under the Creative Commons Attribution-NoDerivs-NonCommercial License (which allows redistribution of the work). To view a copy of this license, visit http://creativecommons.org/licenses/by-nd- nc/1.0/ or send a letter to Creative Commons, 559 Nathan Abbott Way, Stanford, California 94305, USA. Microsoft may have patents, patent applications, trademarks, copyrights, or other intellectual property rights covering subject matter in this document. Except as expressly provided in any written license agreement from Microsoft, the furnishing of this document does not give you any license to these patents, trademarks, copyrights, or other intellectual property. -
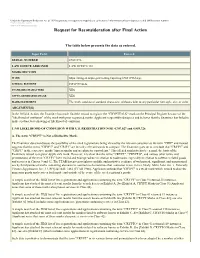
Request for Reconsideration After Final Action
Under the Paperwork Reduction Act of 1995 no persons are required to respond to a collection of information unless it displays a valid OMB control number. PTO Form 1960 (Rev 10/2011) OMB No. 0651-0050 (Exp 09/20/2020) Request for Reconsideration after Final Action The table below presents the data as entered. Input Field Entered SERIAL NUMBER 87031396 LAW OFFICE ASSIGNED LAW OFFICE 116 MARK SECTION MARK https://tmng-al.uspto.gov/resting2/api/img/87031396/large LITERAL ELEMENT CRYPTTALK STANDARD CHARACTERS YES USPTO-GENERATED IMAGE YES MARK STATEMENT The mark consists of standard characters, without claim to any particular font style, size or color. ARGUMENT(S) In the Official Action, the Examiner has made final the refusal to register the "CRYPTTALK" mark on the Principal Register because of the "likelihood of confusion" of the mark with prior registered marks. Applicant respectfully disagrees and believes that the Examiner has failed to make a prima facie showing of likelihood of confusion. I. NO LIKELIHOOD OF CONFUSION WITH U.S. REGISTRATION NOS. 4,707,027 and 4,859,726 A. The term "CRYPT" is Not a Distinctive Mark. The Examiner does not discuss the possibility of the cited registrations being viewed by the relevant consumer as the term "CRIP" and instead suggests that the terms "CRYPT" and "CRIPT" are the only relevant words to compare. The Examiner goes on to conclude that "CRYPT" and "CRIPT" in the respective marks "appear similar and are phonetic equivalents." This alleged similarity has been made the basis of the Examiners refusal to register Applicant's mark. -

Ways to a Better Password Management
St at e of IT Changes Survey Result s + Infographic Tips for a Bet t er Passw ord Securit y Policy Dat a Governance: The Key t o Com pliance Basic Rules How -t o: Ways t o a Bet t er Det ect ing Passw ord Changes in Act ive oPf aWsisnwdoowrds Server Direct ory SMecaunriatygem ent Contents Nine St eps t o a Bet t er Passw ord Managem ent 3 by Richard Muniz Why You Need t o Ensure Adm inist rat ors 5 Change Passw ords Regularly by Orin Thomas How t o St ore and Ret rieve Passw ords Securely 7 w it h Pow erShell by Adam Bertram 3 Ways t o Prot ect t he Keys t o Your Kingdom - 11 Dom ain Adm inist rat or Credent ials by Russell Smith June 2015 SysAdmin Magazine St at e of IT Changes Survey 2015: 13 Docum ent ing and Audit ing Dat a Governanm e: The Key t o Com pliance 16 by Deb Shinder Internet Usage Policy against Inappropriate 18 Content by Richard Muniz How to Detect Password Changes 20 in Active Directory June 2015 SysAdmin Magazine Nine Steps to a Better Passw ord Managem ent by Richard Muniz 20+ years in IT industry, a practicing systems administrator and a teacher Passwords remind me a bit of the Coyote. Not Monde and right on the background, taped to the one that chases the Road Runner, but the the wall, is a list of passwords (and you thought one that lives in my native South-West and howls you had it rough with people taping them under at the moon. -

Easy Encryption for Email, Photo, and Other Cloud Services John Seunghyun Koh
Easy Encryption for Email, Photo, and Other Cloud Services John Seunghyun Koh Submitted in partial fulfillment of the requirements for the degree of Doctor of Philosophy under the Executive Committee of the Graduate School of Arts and Sciences COLUMBIA UNIVERSITY 2021 © 2021 John Seunghyun Koh All Rights Reserved Abstract Easy Encryption for Email, Photo, and Other Cloud Services John Seunghyun Koh Modern users carry mobile devices with them at nearly all times, and this likely has contribut- ed to the rapid growth of private user data—such as emails, photos, and more—stored online in the cloud. Unfortunately, the security of many cloud services for user data is lacking, and the vast amount of user data stored in the cloud is an attractive target for adversaries. Even a single compro- mise of a user’s account yields all its data to attackers. A breach of an unencrypted email account gives the attacker full access to years, even decades, of emails. Ideally, users would encrypt their data to prevent this. However, encrypting data at rest has long been considered too difficult for users, even technical ones, mainly due to the confusing nature of managing cryptographic keys. My thesis is that strong security can be made easy to use through client-side encryption using self-generated per-device cryptographic keys, such that user data in cloud services is well pro- tected, encryption is transparent and largely unnoticeable to users even on multiple devices, and encryption can be used with existing services without any server-side modifications. This dis- sertation introduces a new paradigm for usable cryptographic key management, Per-Device Keys (PDK), and explores how self-generated keys unique to every device can enable new client-side encryption schemes that are compatible with existing online services yet are transparent to users. -

Encryption Enterprise Advanced Installation Guide V10.0 Notes, Cautions, and Warnings
Dell Encryption Enterprise Advanced Installation Guide v10.0 Notes, cautions, and warnings NOTE: A NOTE indicates important information that helps you make better use of your product. CAUTION: A CAUTION indicates either potential damage to hardware or loss of data and tells you how to avoid the problem. WARNING: A WARNING indicates a potential for property damage, personal injury, or death. © 2012-2018 Dell Inc. All rights reserved. Dell, EMC, and other trademarks are trademarks of Dell Inc. or its subsidiaries. Other trademarks may be trademarks of their respective owners.Registered trademarks and trademarks used in the Dell Encryption, Endpoint Security Suite Enterprise, and Data Guardian suite of documents: Dell™ and the Dell logo, Dell Precision™, OptiPlex™, ControlVault™, Latitude™, XPS®, and KACE™ are trademarks of Dell Inc. Cylance®, CylancePROTECT, and the Cylance logo are registered trademarks of Cylance, Inc. in the U.S. and other countries. McAfee® and the McAfee logo are trademarks or registered trademarks of McAfee, Inc. in the US and other countries. Intel®, Pentium®, Intel Core Inside Duo®, Itanium®, and Xeon® are registered trademarks of Intel Corporation in the U.S. and other countries. Adobe®, Acrobat®, and Flash® are registered trademarks of Adobe Systems Incorporated. Authen tec® and Eikon® are registered trademarks of Authen tec. AMD® is a registered trademark of Advanced Micro Devices, Inc. Microsoft®, Windows®, and Windows Server®, Internet Explorer®, Windows Vista®, Windows 7®, Windows 10®, Active Directory®, Access®, BitLocker®, BitLocker To Go®, Excel®, Hyper-V®, Outlook®, PowerPoint®, Word®, OneDrive®, SQL Server®, and Visual C++® are either trademarks or registered trademarks of Microsoft Corporation in the United States and/or other countries. -

Security Best Practices for Developing Windows Azure Applications
Security Best Practices For Developing Windows Azure Applications Authors Andrew Marshall (Senior Security Program Manager, Security Engineering) Michael Howard (Principal Security Program Manager, Security Engineering) Grant Bugher (Lead Security Program Manager, OSSC) Brian Harden (Security Architect, OSSC) Contributors Charlie Kaufman (Principal Architect) Martin Rues (Director, OSSC) Vittorio Bertocci (Senior Technical Evangelist, Developer and Platform Evangelism) June 2010 (REVISION 2) The information contained in this document represents the current view of Microsoft Corporation on the issues discussed as of the date of publication. Because Microsoft must respond to changing market conditions, it should not be interpreted to be a commitment on the part of Microsoft, and Microsoft cannot guarantee the accuracy of any information presented after the date of publication. This White Paper is for informational purposes only. MICROSOFT MAKES NO WARRANTIES, EXPRESS, IMPLIED OR STATUTORY, AS TO THE INFORMATION IN THIS DOCUMENT. Complying with all applicable copyright laws is the responsibility of the user. Without limiting the rights under copyright, no part of this document may be reproduced, stored in or introduced into a retrieval system, or transmitted in any form or by any means (electronic, mechanical, photocopying, recording, or otherwise), or for any purpose, without the express written permission of Microsoft Corporation. Microsoft may have patents, patent applications, trademarks, copyrights, or other intellectual property rights -

Invisimole: the Hidden Part of the Story Unearthing Invisimole’S Espionage Toolset and Strategic Cooperations
ESET Research white papers TLP: WHITE INVISIMOLE: THE HIDDEN PART OF THE STORY UNEARTHING INVISIMOLE’S ESPIONAGE TOOLSET AND STRATEGIC COOPERATIONS Authors: Zuzana Hromcová Anton Cherepanov TLP: WHITE 2 InvisiMole: The hidden part of the story CONTENTS 1 EXECUTIVE SUMMARY � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � 4 2 ATTACKS AND INVESTIGATION � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � 4 2.1 InvisiMole’s toolset ������������������������������������������������������������������������������������������������������������������������ 5 2.2 Cooperation between InvisiMole and Gamaredon . 5 3 BUILDING BLOCKS � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � 6 3.1 Structure ������������������������������������������������������������������������������������������������������������������������������������������6 3.1.1 InvisiMole blobs . 6 3.1.2 Execution guardrails with DPAPI ���������������������������������������������������������������������������������7 3.2 Payload ��������������������������������������������������������������������������������������������������������������������������������������������8 3.2.1 TCP downloader ��������������������������������������������������������������������������������������������������������������9 3.2.2 DNS downloader . 9 3.2.3 RC2CL backdoor �������������������������������������������������������������������������������������������������������������13 -

Dell Data Protection | Encryption Enterprise Edition Advanced Installation Guide V8.13 Notes, Cautions, and Warnings
Dell Data Protection | Encryption Enterprise Edition Advanced Installation Guide v8.13 Notes, cautions, and warnings NOTE: A NOTE indicates important information that helps you make better use of your product. CAUTION: A CAUTION indicates either potential damage to hardware or loss of data and tells you how to avoid the problem. WARNING: A WARNING indicates a potential for property damage, personal injury, or death. © 2017 Dell Inc. All rights reserved.Dell, EMC, and other trademarks are trademarks of Dell Inc. or its subsidiaries. Other trademarks may be trademarks of their respective owners. Registered trademarks and trademarks used in the Dell Data Protection Encryption, Endpoint Security Suite, Endpoint Security Suite Enterprise, and Dell Data Guardian suite of documents: DellTM and the Dell logo, Dell PrecisionTM, OptiPlexTM, ControlVaultTM, LatitudeTM, XPS®, and KACETM are trademarks of Dell Inc. Cylance®, CylancePROTECT, and the Cylance logo are registered trademarks of Cylance, Inc. in the U.S. and other countries. McAfee® and the McAfee logo are trademarks or registered trademarks of McAfee, Inc. in the US and other countries. Intel®, Pentium®, Intel Core Inside Duo®, Itanium®, and Xeon® are registered trademarks of Intel Corporation in the U.S. and other countries. Adobe®, Acrobat®, and Flash® are registered trademarks of Adobe Systems Incorporated. Authen Tec® and Eikon® are registered trademarks of Authen Tec. AMD® is a registered trademark of Advanced Micro Devices, Inc. Microsoft®, Windows®, and Windows Server®, Internet Explorer®, MS-DOS®, Windows Vista®, MSN®, ActiveX®, Active Directory®, Access®, ActiveSync®, BitLocker®, BitLocker To Go®, Excel®, Hyper-V®, Silverlight®, Outlook®, PowerPoint®, OneDrive®, SQL Server®, and Visual C++® are either trademarks or registered trademarks of Microsoft Corporation in the United States and/or other countries.