UC Berkeley UC Berkeley Electronic Theses and Dissertations
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
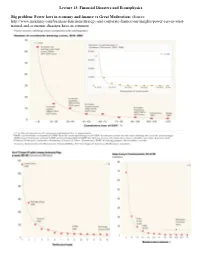
Lecture 13: Financial Disasters and Econophysics
Lecture 13: Financial Disasters and Econophysics Big problem: Power laws in economy and finance vs Great Moderation: (Source: http://www.mckinsey.com/business-functions/strategy-and-corporate-finance/our-insights/power-curves-what- natural-and-economic-disasters-have-in-common Analysis of big data, discontinuous change especially of financial sector, where efficient market theory missed the boat has drawn attention of specialists from physics and mathematics. Wall Street“quant”models may have helped the market implode; and collapse spawned econophysics work on finance instability. NATURE PHYSICS March 2013 Volume 9, No 3 pp119-197 : “The 2008 financial crisis has highlighted major limitations in the modelling of financial and economic systems. However, an emerging field of research at the frontiers of both physics and economics aims to provide a more fundamental understanding of economic networks, as well as practical insights for policymakers. In this Nature Physics Focus, physicists and economists consider the state-of-the-art in the application of network science to finance.” The financial crisis has made us aware that financial markets are very complex networks that, in many cases, we do not really understand and that can easily go out of control. This idea, which would have been shocking only 5 years ago, results from a number of precise reasons. What does physics bring to social science problems? 1- Heterogeneous agents – strange since physics draws strength from electron is electron is electron but STATISTICAL MECHANICS --- minority game, finance artificial agents, 2- Facility with huge data sets – data-mining for regularities in time series with open eyes. 3- Network analysis 4- Percolation/other models of “phase transition”, which directs attention at boundary conditions AN INTRODUCTION TO ECONOPHYSICS Correlations and Complexity in Finance ROSARIO N. -

Processes on Complex Networks. Percolation
Chapter 5 Processes on complex networks. Percolation 77 Up till now we discussed the structure of the complex networks. The actual reason to study this structure is to understand how this structure influences the behavior of random processes on networks. I will talk about two such processes. The first one is the percolation process. The second one is the spread of epidemics. There are a lot of open problems in this area, the main of which can be innocently formulated as: How the network topology influences the dynamics of random processes on this network. We are still quite far from a definite answer to this question. 5.1 Percolation 5.1.1 Introduction to percolation Percolation is one of the simplest processes that exhibit the critical phenomena or phase transition. This means that there is a parameter in the system, whose small change yields a large change in the system behavior. To define the percolation process, consider a graph, that has a large connected component. In the classical settings, percolation was actually studied on infinite graphs, whose vertices constitute the set Zd, and edges connect each vertex with nearest neighbors, but we consider general random graphs. We have parameter ϕ, which is the probability that any edge present in the underlying graph is open or closed (an event with probability 1 − ϕ) independently of the other edges. Actually, if we talk about edges being open or closed, this means that we discuss bond percolation. It is also possible to talk about the vertices being open or closed, and this is called site percolation. -

Understanding Complex Systems: a Communication Networks Perspective
1 Understanding Complex Systems: A Communication Networks Perspective Pavlos Antoniou and Andreas Pitsillides Networks Research Laboratory, Computer Science Department, University of Cyprus 75 Kallipoleos Street, P.O. Box 20537, 1678 Nicosia, Cyprus Telephone: +357-22-892687, Fax: +357-22-892701 Email: [email protected], [email protected] Technical Report TR-07-01 Department of Computer Science University of Cyprus February 2007 Abstract Recent approaches on the study of networks have exploded over almost all the sciences across the academic spectrum. Over the last few years, the analysis and modeling of networks as well as networked dynamical systems have attracted considerable interdisciplinary interest. These efforts were driven by the fact that systems as diverse as genetic networks or the Internet can be best described as complex networks. On the contrary, although the unprecedented evolution of technology, basic issues and fundamental principles related to the structural and evolutionary properties of networks still remain unaddressed and need to be unraveled since they affect the function of a network. Therefore, the characterization of the wiring diagram and the understanding on how an enormous network of interacting dynamical elements is able to behave collectively, given their individual non linear dynamics are of prime importance. In this study we explore simple models of complex networks from real communication networks perspective, focusing on their structural and evolutionary properties. The limitations and vulnerabilities of real communication networks drive the necessity to develop new theoretical frameworks to help explain the complex and unpredictable behaviors of those networks based on the aforementioned principles, and design alternative network methods and techniques which may be provably effective, robust and resilient to accidental failures and coordinated attacks. -

Critical Percolation As a Framework to Analyze the Training of Deep Networks
Published as a conference paper at ICLR 2018 CRITICAL PERCOLATION AS A FRAMEWORK TO ANALYZE THE TRAINING OF DEEP NETWORKS Zohar Ringel Rodrigo de Bem∗ Racah Institute of Physics Department of Engineering Science The Hebrew University of Jerusalem University of Oxford [email protected]. [email protected] ABSTRACT In this paper we approach two relevant deep learning topics: i) tackling of graph structured input data and ii) a better understanding and analysis of deep networks and related learning algorithms. With this in mind we focus on the topological classification of reachability in a particular subset of planar graphs (Mazes). Doing so, we are able to model the topology of data while staying in Euclidean space, thus allowing its processing with standard CNN architectures. We suggest a suitable architecture for this problem and show that it can express a perfect solution to the classification task. The shape of the cost function around this solution is also derived and, remarkably, does not depend on the size of the maze in the large maze limit. Responsible for this behavior are rare events in the dataset which strongly regulate the shape of the cost function near this global minimum. We further identify an obstacle to learning in the form of poorly performing local minima in which the network chooses to ignore some of the inputs. We further support our claims with training experiments and numerical analysis of the cost function on networks with up to 128 layers. 1 INTRODUCTION Deep convolutional networks have achieved great success in the last years by presenting human and super-human performance on many machine learning problems such as image classification, speech recognition and natural language processing (LeCun et al. -
![Arxiv:1504.02898V2 [Cond-Mat.Stat-Mech] 7 Jun 2015 Keywords: Percolation, Explosive Percolation, SLE, Ising Model, Earth Topography](https://docslib.b-cdn.net/cover/1084/arxiv-1504-02898v2-cond-mat-stat-mech-7-jun-2015-keywords-percolation-explosive-percolation-sle-ising-model-earth-topography-841084.webp)
Arxiv:1504.02898V2 [Cond-Mat.Stat-Mech] 7 Jun 2015 Keywords: Percolation, Explosive Percolation, SLE, Ising Model, Earth Topography
Recent advances in percolation theory and its applications Abbas Ali Saberi aDepartment of Physics, University of Tehran, P.O. Box 14395-547,Tehran, Iran bSchool of Particles and Accelerators, Institute for Research in Fundamental Sciences (IPM) P.O. Box 19395-5531, Tehran, Iran Abstract Percolation is the simplest fundamental model in statistical mechanics that exhibits phase transitions signaled by the emergence of a giant connected component. Despite its very simple rules, percolation theory has successfully been applied to describe a large variety of natural, technological and social systems. Percolation models serve as important universality classes in critical phenomena characterized by a set of critical exponents which correspond to a rich fractal and scaling structure of their geometric features. We will first outline the basic features of the ordinary model. Over the years a variety of percolation models has been introduced some of which with completely different scaling and universal properties from the original model with either continuous or discontinuous transitions depending on the control parameter, di- mensionality and the type of the underlying rules and networks. We will try to take a glimpse at a number of selective variations including Achlioptas process, half-restricted process and spanning cluster-avoiding process as examples of the so-called explosive per- colation. We will also introduce non-self-averaging percolation and discuss correlated percolation and bootstrap percolation with special emphasis on their recent progress. Directed percolation process will be also discussed as a prototype of systems displaying a nonequilibrium phase transition into an absorbing state. In the past decade, after the invention of stochastic L¨ownerevolution (SLE) by Oded Schramm, two-dimensional (2D) percolation has become a central problem in probability theory leading to the two recent Fields medals. -

Predicting Porosity, Permeability, and Tortuosity of Porous Media from Images by Deep Learning Krzysztof M
www.nature.com/scientificreports OPEN Predicting porosity, permeability, and tortuosity of porous media from images by deep learning Krzysztof M. Graczyk* & Maciej Matyka Convolutional neural networks (CNN) are utilized to encode the relation between initial confgurations of obstacles and three fundamental quantities in porous media: porosity ( ϕ ), permeability (k), and tortuosity (T). The two-dimensional systems with obstacles are considered. The fuid fow through a porous medium is simulated with the lattice Boltzmann method. The analysis has been performed for the systems with ϕ ∈ (0.37, 0.99) which covers fve orders of magnitude a span for permeability k ∈ (0.78, 2.1 × 105) and tortuosity T ∈ (1.03, 2.74) . It is shown that the CNNs can be used to predict the porosity, permeability, and tortuosity with good accuracy. With the usage of the CNN models, the relation between T and ϕ has been obtained and compared with the empirical estimate. Transport in porous media is ubiquitous: from the neuro-active molecules moving in the brain extracellular space1,2, water percolating through granular soils3 to the mass transport in the porous electrodes of the Lithium- ion batteries4 used in hand-held electronics. Te research in porous media concentrates on understanding the connections between two opposite scales: micro-world, which consists of voids and solids, and the macro-scale of porous objects. Te macroscopic transport properties of these objects are of the key interest for various indus- tries, including healthcare 5 and mining6. Macroscopic properties of the porous medium rely on the microscopic structure of interconnected pore space. Te shape and complexity of pores depend on the type of medium. -

Percolation Theory Are Well-Suited To
Models of Disordered Media and Predictions of Associated Hydraulic Conductivity A thesis submitted in partial fulfillment of the requirements for the degree of Master of Science By L AARON BLANK B.S., Wright State University, 2004 2006 Wright State University WRIGHT STATE UNIVERSITY SCHOOL OF GRADUATE STUDIES Novermber 6, 2006 I HEREBY RECOMMEND THAT THE THESIS PREPARED UNDER MY SUPERVISION BY L Blank ENTITLED Models of Disordered Media and Predictions of Associated Hydraulic Conductivity BE ACCEPTED IN PARTIAL FULFILLMENT OF THE REQUIREMENTS FOR THE DEGREE OF Master of Science. _______________________ Allen Hunt, Ph.D. Thesis Advisor _______________________ Lok Lew Yan Voon, Ph.D. Department Chair _______________________ Joseph F. Thomas, Jr., Ph.D. Dean of the School of Graduate Studies Committee on Final Examination ____________________ Allen Hunt, Ph.D. ____________________ Brent D. Foy, Ph.D. ____________________ Gust Bambakidis, Ph.D. ____________________ Thomas Skinner, Ph.D. Abstract In the late 20th century there was a spill of Technetium in eastern Washington State at the US Department of Energy Hanford site. Resulting contamination of water supplies would raise serious health issues for local residents. Therefore, the ability to predict how these contaminants move through the soil is of great interest. The main contribution to contaminant transport arises from being carried along by flowing water. An important control on the movement of the water through the medium is the hydraulic conductivity, K, which defines the ease of water flow for a given pressure difference (analogous to the electrical conductivity). The overall goal of research in this area is to develop a technique which accurately predicts the hydraulic conductivity as well as its distribution, both in the horizontal and the vertical directions, for media representative of the Hanford subsurface. -

A Deep Percolation Model for Estimating Ground-Water Recharge: Documentation of Modules for the Modular Modeling System of the U.S
Prepared in cooperation with the Bureau of Reclamation, Yakama Nation, and the Washington State Department of Ecology A Deep Percolation Model for Estimating Ground-Water Recharge: Documentation of Modules for the Modular Modeling System of the U.S. Geological Survey Scientific Investigations Report 2006–5318 U.S. Department of the Interior U.S. Geological Survey Cover: Photograph of Clark WEll No. 1, located on the north side of the Moxee Valley in North Yakima, Washington. The well is located in township 12 north, range 20 east, section 6. The well was drilled to a depth of 940 feet into an artesian zone of the Ellensburg Formation, and completed in 1897 at a cost of $2,000. The original flow from the well was estimated at about 600 gallons per minute, and was used to irrigate 250 acres in 1900 and supplied water to 8 small ranches with an additional 47 acres of irrigation. (Photograph was taken by E.E. James in 1897, and was printed in 1901 in the U.S. Geological Survey Water-Supply and Irrigation Paper 55.) A Deep Percolation Model for Estimating Ground-Water Recharge: Documentation of Modules for the Modular Modeling System of the U.S. Geological Survey By J.J. Vaccaro Prepared in cooperation with the Bureau of Reclamation, Yakama Nation, and Washington State Department of Ecology Scientific Investigations Report 2006–5318 U.S. Department of the Interior U.S. Geological Survey U.S. Department of the Interior DIRK KEMPTHORNE, Secretary U.S. Geological Survey Mark D. Myers, Director U.S. Geological Survey, Reston, Virginia: 2007 For product and ordering information: World Wide Web: http://www.usgs.gov/pubprod Telephone: 1-888-ASK-USGS For more information on the USGS--the Federal source for science about the Earth, its natural and living resources, natural hazards, and the environment: World Wide Web: http://www.usgs.gov Telephone: 1-888-ASK-USGS Any use of trade, product, or firm names is for descriptive purposes only and does not imply endorsement by the U.S. -

Percolation Pond with Recharge Shaft As a Method of Managed Aquifer Recharge for Improving the Groundwater Quality in the Saline Coastal Aquifer
J. Earth Syst. Sci. (2020) 129 63 Ó Indian Academy of Sciences https://doi.org/10.1007/s12040-019-1333-0 (0123456789().,-volV)(0123456789().,-volV) Percolation pond with recharge shaft as a method of managed aquifer recharge for improving the groundwater quality in the saline coastal aquifer MCRAICY and L ELANGO* Department of Geology, Anna University, Chennai 600 025, India. *Corresponding author. e-mail: [email protected] MS received 4 February 2019; revised 1 August 2019; accepted 7 November 2019 The deterioration of groundwater quality has become a serious problem for the safe drinking water supply in many parts of the world. Along coastal aquifers, the saline water moves landward due to several reasons even though significant rainfall is available. The objective of the present study is to investigate the impact of a combined recharge structure including a percolation pond and a recharge shaft in improving the groundwater quality of the surrounding area. The area chosen for this study is Andarmadam, Thiruvallur district of Tamil Nadu. As a part of the study, a suitable site was selected for the construction of a percolation pond based on preliminary Beld investigations in 2012. Three piezometers were also con- structed near the percolation pond to investigate the impact of the structure on groundwater recharge. Further, a recharge shaft was added to this structure in 2013 to overcome the clogging issues at the pond bottom and to enhance the recharge. The impact of the percolation pond on groundwater was assessed by comparing the periodical groundwater level Cuctuations with rainfall in the area. The Cuctuations in groundwater level near the percolation pond show variations before and after the construction of recharge shaft. -
![Arxiv:1804.02709V2 [Cond-Mat.Stat-Mech] 8 Jun 2019 L,Tesrnl Orltdfrisseswr Studied Were Exam- Systems for Fermi Correlated of Strongly [11]](https://docslib.b-cdn.net/cover/7751/arxiv-1804-02709v2-cond-mat-stat-mech-8-jun-2019-l-tesrnl-orltdfrisseswr-studied-were-exam-systems-for-fermi-correlated-of-strongly-11-2037751.webp)
Arxiv:1804.02709V2 [Cond-Mat.Stat-Mech] 8 Jun 2019 L,Tesrnl Orltdfrisseswr Studied Were Exam- Systems for Fermi Correlated of Strongly [11]
Machine learning of phase transitions in the percolation and XY models Wanzhou Zhang,1, 2 Jiayu Liu,1 and Tzu-Chieh Wei2 1College of Physics and Optoelectronics, Taiyuan University of Technology Shanxi 030024, China 2C.N. Yang Institute for Theoretical Physics and Department of Physics and Astronomy, State University of New York at Stony Brook, Stony Brook, NY 11794-3840, USA (Dated: June 11, 2019) In this paper, we apply machine learning methods to study phase transitions in certain statistical mechanical models on the two dimensional lattices, whose transitions involve non-local or topological properties, including site and bond percolations, the XY model and the generalized XY model. We find that using just one hidden layer in a fully-connected neural network, the percolation transition can be learned and the data collapse by using the average output layer gives correct estimate of the critical exponent ν. We also study the Berezinskii-Kosterlitz-Thouless transition, which involves binding and unbinding of topological defects—vortices and anti-vortices, in the classical XY model. The generalized XY model contains richer phases, such as the nematic phase, the paramagnetic and the quasi-long-range ferromagnetic phases, and we also apply machine learning method to it. We obtain a consistent phase diagram from the network trained with only data along the temperature axis at two particular parameter ∆ values, where ∆ is the relative weight of pure XY coupling. Besides using the spin configurations (either angles or spin components) as the input information in a convolutional neural network, we devise a feature engineering approach using the histograms of the spin orientations in order to train the network to learn the three phases in the generalized XY model and demonstrate that it indeed works. -

Percolation, Pretopology and Complex Systems Modeling
Percolation, Pretopology and Complex Systems Modeling Soufian Ben Amor, Ivan Lavallee´ and Marc Bui Complex Systems Modeling and Cognition Eurocontrol and EPHE Joint Research Lab 41 rue G. Lussac, F75005 Paris Email :{sofiane.benamor, marc.bui, ivan.lavallee}@ephe.sorbonne.fr Abstract A complex system is generally regarded as being a network of elements in mutual interactions, which total behavior cannot be deduced from that of its parts and their properties. Thus, the study of a complex phenomenon requires a holistic approach considering the system in its totality. The aim of our approach is the design of a unifying theoretical framework to define complex systems according to their common properties and to tackle their modeling by generalizing percolation processes using pretopology theory. keywords: Complex systems ; percolation ; pretopology; modeling; stochastic optimization. 1 Introduction There is no unified definition of complexity, but recent efforts aim more and more at giving a generalization of this concept1. The problem arising from the notion of complexity is to know if it is of ontological or epistemological nature. We can note that complexity exists generally according to a specific model or a scientific field. Recently, a methodology of complex phenomena modeling, founded on a concept known as hierarchical graphs was de- veloped in [12]. This promising modeling approach based on agents, makes it possible to take into account the various hierarchical levels in a system as well as the heterogeneous nature of the interactions. Nevertheless, the formal aspect in the study of complex systems remains fragmented. Our objective is to provide a work basis in order to specify some interesting research orientations and the adapted theoretical tools allowing the design of a general theory of complex systems. -

Coupling Agent Based Simulation with Dynamic Networks Analysis to Study
Coupling agent based simulation with dynamic networks analysis to study the emergence of mutual knowledge as a percolation phenomenon Julie Dugdale, Narjes Bellamine, Ben Saoud, Fedia Zouai, Bernard Pavard To cite this version: Julie Dugdale, Narjes Bellamine, Ben Saoud, Fedia Zouai, Bernard Pavard. Coupling agent based simulation with dynamic networks analysis to study the emergence of mutual knowledge as a perco- lation phenomenon. Journal of Systems Science and Complexity, Springer Verlag (Germany), 2016. hal-02091636 HAL Id: hal-02091636 https://hal.archives-ouvertes.fr/hal-02091636 Submitted on 5 Apr 2019 HAL is a multi-disciplinary open access L’archive ouverte pluridisciplinaire HAL, est archive for the deposit and dissemination of sci- destinée au dépôt et à la diffusion de documents entific research documents, whether they are pub- scientifiques de niveau recherche, publiés ou non, lished or not. The documents may come from émanant des établissements d’enseignement et de teaching and research institutions in France or recherche français ou étrangers, des laboratoires abroad, or from public or private research centers. publics ou privés. Coupling agent based simulation with dynamic networks analysis to study the emergence of mutual knowledge as a percolation phenomenon Julie Dugdale(1,2), Narjès Bellamine Ben Saoud(3,4), Fedia Zouai3, Bernard Pavard5 (1) Université Grenoble Alpes; LIG, Grenoble, France (2) University of Agder, Norway (3) Laboratoire RIADI – ENSI Université de La Manouba, Tunisia (4) Institut Supérieur d’Informatique, Université Tunis el Manar, Tunisia (5) Université P. Sabatier, CNRS, IRIT, Toulouse, France Abstract The emergence of mutual knowledge is a major cognitive mechanism for the robustness of complex socio technical systems.