A Mini Course on Percolation Theory
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Geodesic Distance Descriptors
Geodesic Distance Descriptors Gil Shamai and Ron Kimmel Technion - Israel Institute of Technologies [email protected] [email protected] Abstract efficiency of state of the art shape matching procedures. The Gromov-Hausdorff (GH) distance is traditionally used for measuring distances between metric spaces. It 1. Introduction was adapted for non-rigid shape comparison and match- One line of thought in shape analysis considers an ob- ing of isometric surfaces, and is defined as the minimal ject as a metric space, and object matching, classification, distortion of embedding one surface into the other, while and comparison as the operation of measuring the discrep- the optimal correspondence can be described as the map ancies and similarities between such metric spaces, see, for that minimizes this distortion. Solving such a minimiza- example, [13, 33, 27, 23, 8, 3, 24]. tion is a hard combinatorial problem that requires pre- Although theoretically appealing, the computation of computation and storing of all pairwise geodesic distances distances between metric spaces poses complexity chal- for the matched surfaces. A popular way for compact repre- lenges as far as direct computation and memory require- sentation of functions on surfaces is by projecting them into ments are involved. As a remedy, alternative representa- the leading eigenfunctions of the Laplace-Beltrami Opera- tion spaces were proposed [26, 22, 15, 10, 31, 30, 19, 20]. tor (LBO). When truncated, the basis of the LBO is known The question of which representation to use in order to best to be the optimal for representing functions with bounded represent the metric space that define each form we deal gradient in a min-max sense. -

Modern Discrete Probability I
Preliminaries Some fundamental models A few more useful facts about... Modern Discrete Probability I - Introduction Stochastic processes on graphs: models and questions Sebastien´ Roch UW–Madison Mathematics September 6, 2017 Sebastien´ Roch, UW–Madison Modern Discrete Probability – Models and Questions Preliminaries Review of graph theory Some fundamental models Review of Markov chain theory A few more useful facts about... 1 Preliminaries Review of graph theory Review of Markov chain theory 2 Some fundamental models Random walks on graphs Percolation Some random graph models Markov random fields Interacting particles on finite graphs 3 A few more useful facts about... ...graphs ...Markov chains ...other things Sebastien´ Roch, UW–Madison Modern Discrete Probability – Models and Questions Preliminaries Review of graph theory Some fundamental models Review of Markov chain theory A few more useful facts about... Graphs Definition (Undirected graph) An undirected graph (or graph for short) is a pair G = (V ; E) where V is the set of vertices (or nodes, sites) and E ⊆ ffu; vg : u; v 2 V g; is the set of edges (or bonds). The V is either finite or countably infinite. Edges of the form fug are called loops. We do not allow E to be a multiset. We occasionally write V (G) and E(G) for the vertices and edges of G. Sebastien´ Roch, UW–Madison Modern Discrete Probability – Models and Questions Preliminaries Review of graph theory Some fundamental models Review of Markov chain theory A few more useful facts about... An example: the Petersen graph Sebastien´ Roch, UW–Madison Modern Discrete Probability – Models and Questions Preliminaries Review of graph theory Some fundamental models Review of Markov chain theory A few more useful facts about.. -

Probabilistic and Geometric Methods in Last Passage Percolation
Probabilistic and geometric methods in last passage percolation by Milind Hegde A dissertation submitted in partial satisfaction of the requirements for the degree of Doctor of Philosophy in Mathematics in the Graduate Division of the University of California, Berkeley Committee in charge: Professor Alan Hammond, Co‐chair Professor Shirshendu Ganguly, Co‐chair Professor Fraydoun Rezakhanlou Professor Alistair Sinclair Spring 2021 Probabilistic and geometric methods in last passage percolation Copyright 2021 by Milind Hegde 1 Abstract Probabilistic and geometric methods in last passage percolation by Milind Hegde Doctor of Philosophy in Mathematics University of California, Berkeley Professor Alan Hammond, Co‐chair Professor Shirshendu Ganguly, Co‐chair Last passage percolation (LPP) refers to a broad class of models thought to lie within the Kardar‐ Parisi‐Zhang universality class of one‐dimensional stochastic growth models. In LPP models, there is a planar random noise environment through which directed paths travel; paths are as‐ signed a weight based on their journey through the environment, usually by, in some sense, integrating the noise over the path. For given points y and x, the weight from y to x is defined by maximizing the weight over all paths from y to x. A path which achieves the maximum weight is called a geodesic. A few last passage percolation models are exactly solvable, i.e., possess what is called integrable structure. This gives rise to valuable information, such as explicit probabilistic resampling prop‐ erties, distributional convergence information, or one point tail bounds of the weight profile as the starting point y is fixed and the ending point x varies. -
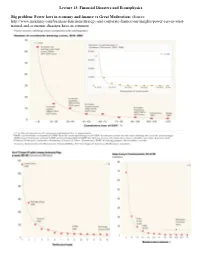
Lecture 13: Financial Disasters and Econophysics
Lecture 13: Financial Disasters and Econophysics Big problem: Power laws in economy and finance vs Great Moderation: (Source: http://www.mckinsey.com/business-functions/strategy-and-corporate-finance/our-insights/power-curves-what- natural-and-economic-disasters-have-in-common Analysis of big data, discontinuous change especially of financial sector, where efficient market theory missed the boat has drawn attention of specialists from physics and mathematics. Wall Street“quant”models may have helped the market implode; and collapse spawned econophysics work on finance instability. NATURE PHYSICS March 2013 Volume 9, No 3 pp119-197 : “The 2008 financial crisis has highlighted major limitations in the modelling of financial and economic systems. However, an emerging field of research at the frontiers of both physics and economics aims to provide a more fundamental understanding of economic networks, as well as practical insights for policymakers. In this Nature Physics Focus, physicists and economists consider the state-of-the-art in the application of network science to finance.” The financial crisis has made us aware that financial markets are very complex networks that, in many cases, we do not really understand and that can easily go out of control. This idea, which would have been shocking only 5 years ago, results from a number of precise reasons. What does physics bring to social science problems? 1- Heterogeneous agents – strange since physics draws strength from electron is electron is electron but STATISTICAL MECHANICS --- minority game, finance artificial agents, 2- Facility with huge data sets – data-mining for regularities in time series with open eyes. 3- Network analysis 4- Percolation/other models of “phase transition”, which directs attention at boundary conditions AN INTRODUCTION TO ECONOPHYSICS Correlations and Complexity in Finance ROSARIO N. -

Network Science
This is a preprint of Katy Börner, Soma Sanyal and Alessandro Vespignani (2007) Network Science. In Blaise Cronin (Ed) Annual Review of Information Science & Technology, Volume 41. Medford, NJ: Information Today, Inc./American Society for Information Science and Technology, chapter 12, pp. 537-607. Network Science Katy Börner School of Library and Information Science, Indiana University, Bloomington, IN 47405, USA [email protected] Soma Sanyal School of Library and Information Science, Indiana University, Bloomington, IN 47405, USA [email protected] Alessandro Vespignani School of Informatics, Indiana University, Bloomington, IN 47406, USA [email protected] 1. Introduction.............................................................................................................................................2 2. Notions and Notations.............................................................................................................................4 2.1 Graphs and Subgraphs .........................................................................................................................5 2.2 Graph Connectivity..............................................................................................................................7 3. Network Sampling ..................................................................................................................................9 4. Network Measurements........................................................................................................................11 -

Processes on Complex Networks. Percolation
Chapter 5 Processes on complex networks. Percolation 77 Up till now we discussed the structure of the complex networks. The actual reason to study this structure is to understand how this structure influences the behavior of random processes on networks. I will talk about two such processes. The first one is the percolation process. The second one is the spread of epidemics. There are a lot of open problems in this area, the main of which can be innocently formulated as: How the network topology influences the dynamics of random processes on this network. We are still quite far from a definite answer to this question. 5.1 Percolation 5.1.1 Introduction to percolation Percolation is one of the simplest processes that exhibit the critical phenomena or phase transition. This means that there is a parameter in the system, whose small change yields a large change in the system behavior. To define the percolation process, consider a graph, that has a large connected component. In the classical settings, percolation was actually studied on infinite graphs, whose vertices constitute the set Zd, and edges connect each vertex with nearest neighbors, but we consider general random graphs. We have parameter ϕ, which is the probability that any edge present in the underlying graph is open or closed (an event with probability 1 − ϕ) independently of the other edges. Actually, if we talk about edges being open or closed, this means that we discuss bond percolation. It is also possible to talk about the vertices being open or closed, and this is called site percolation. -

Latent Distance Estimation for Random Geometric Graphs ∗
Latent Distance Estimation for Random Geometric Graphs ∗ Ernesto Araya Valdivia Laboratoire de Math´ematiquesd'Orsay (LMO) Universit´eParis-Sud 91405 Orsay Cedex France Yohann De Castro Ecole des Ponts ParisTech-CERMICS 6 et 8 avenue Blaise Pascal, Cit´eDescartes Champs sur Marne, 77455 Marne la Vall´ee,Cedex 2 France Abstract: Random geometric graphs are a popular choice for a latent points generative model for networks. Their definition is based on a sample of n points X1;X2; ··· ;Xn on d−1 the Euclidean sphere S which represents the latent positions of nodes of the network. The connection probabilities between the nodes are determined by an unknown function (referred to as the \link" function) evaluated at the distance between the latent points. We introduce a spectral estimator of the pairwise distance between latent points and we prove that its rate of convergence is the same as the nonparametric estimation of a d−1 function on S , up to a logarithmic factor. In addition, we provide an efficient spectral algorithm to compute this estimator without any knowledge on the nonparametric link function. As a byproduct, our method can also consistently estimate the dimension d of the latent space. MSC 2010 subject classifications: Primary 68Q32; secondary 60F99, 68T01. Keywords and phrases: Graphon model, Random Geometric Graph, Latent distances estimation, Latent position graph, Spectral methods. 1. Introduction Random geometric graph (RGG) models have received attention lately as alternative to some simpler yet unrealistic models as the ubiquitous Erd¨os-R´enyi model [11]. They are generative latent point models for graphs, where it is assumed that each node has associated a latent d point in a metric space (usually the Euclidean unit sphere or the unit cube in R ) and the connection probability between two nodes depends on the position of their associated latent points. -

Average D-Distance Between Vertices of a Graph
italian journal of pure and applied mathematics { n. 33¡2014 (293¡298) 293 AVERAGE D-DISTANCE BETWEEN VERTICES OF A GRAPH D. Reddy Babu Department of Mathematics Koneru Lakshmaiah Education Foundation (K.L. University) Vaddeswaram Guntur 522 502 India e-mail: [email protected], [email protected] P.L.N. Varma Department of Science & Humanities V.F.S.T.R. University Vadlamudi Guntur 522 237 India e-mail: varma [email protected] Abstract. The D-distance between vertices of a graph G is obtained by considering the path lengths and as well as the degrees of vertices present on the path. The average D-distance between the vertices of a connected graph is the average of the D-distances between all pairs of vertices of the graph. In this article we study the average D-distance between the vertices of a graph. Keywords: D-distance, average D-distance, diameter. 2000 Mathematics Subject Classi¯cation: 05C12. 1. Introduction The concept of distance is one of the important concepts in study of graphs. It is used in isomorphism testing, graph operations, hamiltonicity problems, extremal problems on connectivity and diameter, convexity in graphs etc. Distance is the basis of many concepts of symmetry in graphs. In addition to the usual distance, d(u; v) between two vertices u; v 2 V (G) we have detour distance (introduced by Chartrand et al, see [2]), superior distance (introduced by Kathiresan and Marimuthu, see [6]), signal distance (introduced by Kathiresan and Sumathi, see [7]), degree distance etc. 294 d. reddy babu, p.l.n. varma In an earlier article [9], the authors introduced the concept of D-distance be- tween vertices of a graph G by considering not only path length between vertices, but also the degrees of all vertices present in a path while de¯ning the D-distance. -

Understanding Complex Systems: a Communication Networks Perspective
1 Understanding Complex Systems: A Communication Networks Perspective Pavlos Antoniou and Andreas Pitsillides Networks Research Laboratory, Computer Science Department, University of Cyprus 75 Kallipoleos Street, P.O. Box 20537, 1678 Nicosia, Cyprus Telephone: +357-22-892687, Fax: +357-22-892701 Email: [email protected], [email protected] Technical Report TR-07-01 Department of Computer Science University of Cyprus February 2007 Abstract Recent approaches on the study of networks have exploded over almost all the sciences across the academic spectrum. Over the last few years, the analysis and modeling of networks as well as networked dynamical systems have attracted considerable interdisciplinary interest. These efforts were driven by the fact that systems as diverse as genetic networks or the Internet can be best described as complex networks. On the contrary, although the unprecedented evolution of technology, basic issues and fundamental principles related to the structural and evolutionary properties of networks still remain unaddressed and need to be unraveled since they affect the function of a network. Therefore, the characterization of the wiring diagram and the understanding on how an enormous network of interacting dynamical elements is able to behave collectively, given their individual non linear dynamics are of prime importance. In this study we explore simple models of complex networks from real communication networks perspective, focusing on their structural and evolutionary properties. The limitations and vulnerabilities of real communication networks drive the necessity to develop new theoretical frameworks to help explain the complex and unpredictable behaviors of those networks based on the aforementioned principles, and design alternative network methods and techniques which may be provably effective, robust and resilient to accidental failures and coordinated attacks. -

Critical Percolation As a Framework to Analyze the Training of Deep Networks
Published as a conference paper at ICLR 2018 CRITICAL PERCOLATION AS A FRAMEWORK TO ANALYZE THE TRAINING OF DEEP NETWORKS Zohar Ringel Rodrigo de Bem∗ Racah Institute of Physics Department of Engineering Science The Hebrew University of Jerusalem University of Oxford [email protected]. [email protected] ABSTRACT In this paper we approach two relevant deep learning topics: i) tackling of graph structured input data and ii) a better understanding and analysis of deep networks and related learning algorithms. With this in mind we focus on the topological classification of reachability in a particular subset of planar graphs (Mazes). Doing so, we are able to model the topology of data while staying in Euclidean space, thus allowing its processing with standard CNN architectures. We suggest a suitable architecture for this problem and show that it can express a perfect solution to the classification task. The shape of the cost function around this solution is also derived and, remarkably, does not depend on the size of the maze in the large maze limit. Responsible for this behavior are rare events in the dataset which strongly regulate the shape of the cost function near this global minimum. We further identify an obstacle to learning in the form of poorly performing local minima in which the network chooses to ignore some of the inputs. We further support our claims with training experiments and numerical analysis of the cost function on networks with up to 128 layers. 1 INTRODUCTION Deep convolutional networks have achieved great success in the last years by presenting human and super-human performance on many machine learning problems such as image classification, speech recognition and natural language processing (LeCun et al. -

Markov Chain Monte Carlo Estimation of Exponential Random Graph Models
Markov Chain Monte Carlo Estimation of Exponential Random Graph Models Tom A.B. Snijders ICS, Department of Statistics and Measurement Theory University of Groningen ∗ April 19, 2002 ∗Author's address: Tom A.B. Snijders, Grote Kruisstraat 2/1, 9712 TS Groningen, The Netherlands, email <[email protected]>. I am grateful to Paul Snijders for programming the JAVA applet used in this article. In the revision of this article, I profited from discussions with Pip Pattison and Garry Robins, and from comments made by a referee. This paper is formatted in landscape to improve on-screen readability. It is read best by opening Acrobat Reader in a full screen window. Note that in Acrobat Reader, the entire screen can be used for viewing by pressing Ctrl-L; the usual screen is returned when pressing Esc; it is possible to zoom in or zoom out by pressing Ctrl-- or Ctrl-=, respectively. The sign in the upper right corners links to the page viewed previously. ( Tom A.B. Snijders 2 MCMC estimation for exponential random graphs ( Abstract bility to move from one region to another. In such situations, convergence to the target distribution is extremely slow. To This paper is about estimating the parameters of the exponential be useful, MCMC algorithms must be able to make transitions random graph model, also known as the p∗ model, using frequen- from a given graph to a very different graph. It is proposed to tist Markov chain Monte Carlo (MCMC) methods. The exponen- include transitions to the graph complement as updating steps tial random graph model is simulated using Gibbs or Metropolis- to improve the speed of convergence to the target distribution. -

Exploring Healing Strategies for Random Boolean Networks
Exploring Healing Strategies for Random Boolean Networks Christian Darabos 1, Alex Healing 2, Tim Johann 3, Amitabh Trehan 4, and Am´elieV´eron 5 1 Information Systems Department, University of Lausanne, Switzerland 2 Pervasive ICT Research Centre, British Telecommunications, UK 3 EML Research gGmbH, Heidelberg, Germany 4 Department of Computer Science, University of New Mexico, Albuquerque, USA 5 Division of Bioinformatics, Institute for Evolution and Biodiversity, The Westphalian Wilhelms University of Muenster, Germany. [email protected], [email protected], [email protected], [email protected], [email protected] Abstract. Real-world systems are often exposed to failures where those studied theoretically are not: neuron cells in the brain can die or fail, re- sources in a peer-to-peer network can break down or become corrupt, species can disappear from and environment, and so forth. In all cases, for the system to keep running as it did before the failure occurred, or to survive at all, some kind of healing strategy may need to be applied. As an example of such a system subjected to failure and subsequently heal, we study Random Boolean Networks. Deletion of a node in the network was considered a failure if it affected the functional output and we in- vestigated healing strategies that would allow the system to heal either fully or partially. More precisely, our main strategy involves allowing the nodes directly affected by the node deletion (failure) to iteratively rewire in order to achieve healing. We found that such a simple method was ef- fective when dealing with small networks and single-point failures.