Enabling Privacy-Awareness in Social Networks
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Intro to Google for the Hill
Introduction to A company built on search Our mission Google’s mission is to organize the world’s information and make it universally accessible and useful. As a first step to fulfilling this mission, Google’s founders Larry Page and Sergey Brin developed a new approach to online search that took root in a Stanford University dorm room and quickly spread to information seekers around the globe. The Google search engine is an easy-to-use, free service that consistently returns relevant results in a fraction of a second. What we do Google is more than a search engine. We also offer Gmail, maps, personal blogging, and web-based word processing products to name just a few. YouTube, the popular online video service, is part of Google as well. Most of Google’s services are free, so how do we make money? Much of Google’s revenue comes through our AdWords advertising program, which allows businesses to place small “sponsored links” alongside our search results. Prices for these ads are set by competitive auctions for every search term where advertisers want their ads to appear. We don’t sell placement in the search results themselves, or allow people to pay for a higher ranking there. In addition, website managers and publishers take advantage of our AdSense advertising program to deliver ads on their sites. This program generates billions of dollars in revenue each year for hundreds of thousands of websites, and is a major source of funding for the free content available across the web. Google also offers enterprise versions of our consumer products for businesses, organizations, and government entities. -

1592213370-Monetize.Pdf
Table of Contents 1. Online Monetization: How to Turn Your Following into Cash 1.1 What is monetization? 1.2 How to monetize your website, blog, or social media channel 1.3 Does a monetization formula exist? Chapter 1 Takeaways 2. How to Monetize Your Blog The Right Way 2.1 Why should you start monetizing with your blog? 2.2 How to earn money from blogging 2.3 How to transform your blog visitors into loyal fans 2.4 Blog monetization tools you should know about Chapter 2 Takeaways 3. Facebook Monetization: The What, Why, Where, and How 3.1 How Facebook monetization works 3.2 Facebook monetization strategies Chapter 3 Takeaways 4. How to monetize your Instagram following 4.1 Before you go chasing that Instagram money... 4.2 The four main ways you can earn money on Instagram 4.3 Instagram monetization tools 4.4 Ideas to make money on Instagram Chapter 4 Takeaways 5. Monetizing a YouTube Brand Without Ads 5.1 How to monetize Youtube videos without Adsense 5.2 Essential Youtube monetization tools 5.3 Factors that determine your channel’s long-term success Chapter 5 Takeaways 1. Online Monetization: How to Turn Your Following into Cash 5 Stop me if you’ve heard this one before. Jenn, a customer service agent at a car leasing company, is fed up with her job. Her pay’s lousy, she’s on edge with customers yelling at her over the phone all day (they actually treat her worse in person), and her boss ignores all her suggestions, even though she knows he could make her job a lot less stressful. -

Google Adsense Fuels Growth for Android- Focused Site
Google AdSense Case Study Google AdSense fuels growth for Android- focused site About elandroidelibre • elandoidelibre.com • Based in Madrid • Blog about the Android operating system “We regard AdSense as an essential tool that’s helping us to set up more blogs, take on more staff, and earn more revenue.” — Paolo Álvarez, administrator and editor. elandroidelibre.com (“the free Android”) is a leading Spanish-language blog about the Android operating system, featuring news, reviews, games and other apps for Android smartphone users. Launched in 2009, it now employs six people and attracts 6.5 million visits each month. Since the outset, Google AdSense has accounted for around 40 per cent of its income. Administrator and editor Paolo Álvarez says: “I was attracted to AdSense because it was simple and effective. I began using it right from the start, and even though I wasn’t an expert, I could see that it worked.” He’s highly satisfied with the quality and relevance of the ads appearing on his site, and says the 300 x 250 Medium Rectangle and the 728 x 90 Leaderboard formats work particularly well. Álvarez uses Google AdSense reports and Google Analytics to analyse the return on the site and gain a better understanding of the kind of visitors it attracts: for example 30 per cent of traffic and income comes from mobile devices. He has also begun using Google’s free ad serving solution, DoubleClick for Publishers, allowing him to manage his online advertising more effectively and segment traffic from different countries. He plans to continue improving the quality and quantity of content in the future. -

Rdfa in XHTML: Syntax and Processing Rdfa in XHTML: Syntax and Processing
RDFa in XHTML: Syntax and Processing RDFa in XHTML: Syntax and Processing RDFa in XHTML: Syntax and Processing A collection of attributes and processing rules for extending XHTML to support RDF W3C Recommendation 14 October 2008 This version: http://www.w3.org/TR/2008/REC-rdfa-syntax-20081014 Latest version: http://www.w3.org/TR/rdfa-syntax Previous version: http://www.w3.org/TR/2008/PR-rdfa-syntax-20080904 Diff from previous version: rdfa-syntax-diff.html Editors: Ben Adida, Creative Commons [email protected] Mark Birbeck, webBackplane [email protected] Shane McCarron, Applied Testing and Technology, Inc. [email protected] Steven Pemberton, CWI Please refer to the errata for this document, which may include some normative corrections. This document is also available in these non-normative formats: PostScript version, PDF version, ZIP archive, and Gzip’d TAR archive. The English version of this specification is the only normative version. Non-normative translations may also be available. Copyright © 2007-2008 W3C® (MIT, ERCIM, Keio), All Rights Reserved. W3C liability, trademark and document use rules apply. Abstract The current Web is primarily made up of an enormous number of documents that have been created using HTML. These documents contain significant amounts of structured data, which is largely unavailable to tools and applications. When publishers can express this data more completely, and when tools can read it, a new world of user functionality becomes available, letting users transfer structured data between applications and web sites, and allowing browsing applications to improve the user experience: an event on a web page can be directly imported - 1 - How to Read this Document RDFa in XHTML: Syntax and Processing into a user’s desktop calendar; a license on a document can be detected so that users can be informed of their rights automatically; a photo’s creator, camera setting information, resolution, location and topic can be published as easily as the original photo itself, enabling structured search and sharing. -

Broadband Video Advertising 101
BROADBAND VIDEO ADVERTISING 101 The web audience’s eyes are already on broadband THE ADVERTISING CHALLENGES OF video, making the player and the surrounding areas the ONLINE PUBLISHERS perfect real estate for advertising. This paper focuses on what publishers need to know about online advertising in Why put advertising on your broadband video? When order to meet their business goals and adapt as the online video plays on a site, the user’s attention is largely drawn advertising environment shifts. away from other content areas on the page and is focused on the video. The player, therefore, is a premium spot for advertising, and this inventory space commands a premium price. But adding advertising to your online video involves a lot of moving parts and many decisions. You need to consider the following: • What types and placements of ads do you want? • How do you count the ads that are viewed? • How do you ensure that the right ad gets shown to the right viewer? Luckily, there are many vendors that can help publishers fill up inventory, manage their campaigns, and get as much revenue from their real estate as possible. This paper focuses on the online advertising needs of the publisher and the services that can help them meet their advertising goals. THE VIDEO PLATFORM COMCASTTECHNOLOGYSOLUTIONS.COM | 800.844.1776 | © 2017 COMCAST TECHNOLOGY SOLUTIONS ONLINE VIDEO ADS: THE BASICS AD TYPES You have many choices in how you combine ads with your content. The best ads are whatever engages your consumers, keeps them on your site, and makes them click. -

Linked Data Overview and Usage in Social Networks
Linked Data Overview and Usage in Social Networks Gustavo G. Valdez Technische Universitat Berlin Email: project [email protected] Abstract—This paper intends to introduce the principles of Webpages, also possibly reference any Object or Concept (or Linked Data, show some possible uses in Social Networks, even relationships of concepts/objects). advantages and disadvantages of using it, aswell as presenting The second one combines the unique identification of the an example application of Linked Data to the field of social networks. first with a well known retrieval mechanism (HTTP), enabling this URIs to be looked up via the HTTP protocol. I. INTRODUCTION The third principle tackles the problem of using the same The web is a very good source of human-readable informa- document standards, in order to have scalability and interop- tion that has improved our daily life in several areas. By using erability. This is done by having a standard, the Resource De- rich text and hyperlinks, it made our access to information scription Framewok (RDF), which will be explained in section something more active rather than passive. But the web was III-A. This standards are very useful to provide resources that made for humans and not for machines, even though today are machine-readable and are identified by a URI. a lot of the acesses to the web are made by machines. This The fourth principle basically advocates that hyperlinks has lead to the search for adding structure, so that data is should be used not only to link webpages, but also to link more machine-readable. -

A Visual Notation for the Integrated Representation of OWL Ontologies
A Visual Notation for the Integrated Representation of OWL Ontologies Stefan Negru1 and Steffen Lohmann2 1Faculty of Computer Science, Alexandru Ioan Cuza University, General Berthelot 16, 700483 Iasi, Romania 2Institute for Visualization and Interactive Systems (VIS), Universit¨atsstraße 38, 70569 Stuttgart, Germany [email protected], [email protected] Keywords: Ontology Visualization, Visual Notation, OWL, Semantic Web, Knowledge Visualization, Ontologies. Abstract: The paper presents a visual notation for the Web Ontology Language (OWL) providing an integrated view on the classes and individuals of ontologies. The classes are displayed as circles, with the size of each circle representing its connectivity in the ontology. The individuals are represented as sections in the circles so that it is immediately clear from the visualization how many individuals the classes contain. The notation can be used to visualize the property relations of either the classes (conceptual layer) or of selected individuals (integrated layer), while certain elements are always shown for a better understanding. It requires only a small number of graphical elements and the resulting visualizations are comparatively compact. Yet, the notation is comprehensive, as it defines graphical representations for all OWL elements that can be reasonably visualized. The applicability of the notation is illustrated by the example of the Friend of a Friend (FOAF) ontology. 1 INTRODUCTION reasoning. Even though it provides great means to de- scribe and integrate information on the Web, its text- The Web of Data has attracted large interest for both based representation is difficult to understand for av- data publishers and consumers in the last years. -

Mapping Between Digital Identity Ontologies Through SISM
Mapping between Digital Identity Ontologies through SISM Matthew Rowe The OAK Group, Department of Computer Science, University of Sheffield, Regent Court, 211 Portobello Street, Sheffield S1 4DP, UK [email protected] Abstract. Various ontologies are available defining the semantics of dig- ital identity information. Due to the rise in use of lowercase semantics, such ontologies are now used to add metadata to digital identity informa- tion within web pages. However concepts exist in these ontologies which are related and must be mapped together in order to enhance machine- readability of identity information on the web. This paper presents the Social identity Schema Mapping (SISM) vocabulary which contains a set of mappings between related concepts in distinct digital identity ontolo- gies using OWL and SKOS mapping constructs. Key words: Semantic Web, Social Web, SKOS, OWL, FOAF, SIOC, PIMO, NCO, Microformats 1 Introduction The semantic web provides a web of machine-readable data. Ontologies form a vital component of the semantic web by providing conceptualisations of domains of knowledge which can then be used to provide a common understanding of some domain. A basic ontology contains a vocabulary of concepts and definitions of the relationships between those concepts. An agent reading a concept from an ontology can look up the concept and discover its properties and characteristics, therefore interpreting how it fits into that particular domain. Due to the great number of ontologies it is common for related concepts to be defined in separate ontologies, these concepts must be identified and mapped together. Web technologies such as Microformats, eRDF and RDFa have allowed web developers to encode lowercase semantics within XHTML pages. -
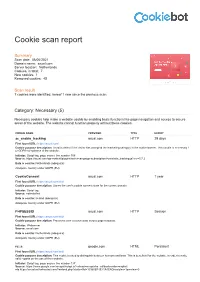
Cookie Scan Report
Cookie scan report Summary Scan date: 08/06/2021 Domain name: axual.com Server location: Netherlands Cookies, in total: 7 New cookies: 1 Removed cookies: 45 Scan result 7 cookies were identified, hereof 1 new since the previous scan. Category: Necessary (5) Necessary cookies help make a website usable by enabling basic functions like page navigation and access to secure areas of the website. The website cannot function properly without these cookies. COOKIE NAME PROVIDER TYPE EXPIRY ac_enable_tracking axual.com HTTP 29 days First found URL: https://axual.com/ Cookie purpose description: Used to detect if the visitor has accepted the marketing category in the cookie banner. This cookie is necessary f or GDPR-compliance of the website. Initiator: Script tag, page source line number 508 Source: https://axual.com/wp-content/plugins/activecampaign-subscription-forms/site_tracking.js?ver=5.7.2 Data is sent to: Netherlands (adequate) Adequate country under GDPR (EU) CookieConsent axual.com HTTP 1 year First found URL: https://axual.com/trial/ Cookie purpose description: Stores the user's cookie consent state for the current domain Initiator: Script tag Source: notinstalled Data is sent to: Ireland (adequate) Adequate country under GDPR (EU) PHPSESSID axual.com HTTP Session First found URL: https://axual.com/trial/ Cookie purpose description: Preserves user session state across page requests. Initiator: Webserver Source: axual.com Data is sent to: Netherlands (adequate) Adequate country under GDPR (EU) rc::a google.com HTML Persistent First found URL: https://axual.com/trial/ Cookie purpose description: This cookie is used to distinguish between humans and bots. -

Ei-Report-2013.Pdf
Economic Impact United States 2013 Stavroulla Kokkinis, Athina Kohilas, Stella Koukides, Andrea Ploutis, Co-owners The Lucky Knot Alexandria,1 Virginia The web is working for American businesses. And Google is helping. Google’s mission is to organize the world’s information and make it universally accessible and useful. Making it easy for businesses to find potential customers and for those customers to find what they’re looking for is an important part of that mission. Our tools help to connect business owners and customers, whether they’re around the corner or across the world from each other. Through our search and advertising programs, businesses find customers, publishers earn money from their online content and non-profits get donations and volunteers. These tools are how we make money, and they’re how millions of businesses do, too. This report details Google’s economic impact in the U.S., including state-by-state numbers of advertisers, publishers, and non-profits who use Google every day. It also includes stories of the real business owners behind those numbers. They are examples of businesses across the country that are using the web, and Google, to succeed online. Google was a small business when our mission was created. We are proud to share the tools that led to our success with other businesses that want to grow and thrive in this digital age. Sincerely, Jim Lecinski Vice President, Customer Solutions 2 Economic Impact | United States 2013 Nationwide Report Randy Gayner, Founder & Owner Glacier Guides West Glacier, Montana The web is working for American The Internet is where business is done businesses. -

Microformats the Next (Small) Thing on the Semantic Web?
Standards Editor: Jim Whitehead • [email protected] Microformats The Next (Small) Thing on the Semantic Web? Rohit Khare • CommerceNet “Designed for humans first and machines second, microformats are a set of simple, open data formats built upon existing and widely adopted standards.” — Microformats.org hen we speak of the “evolution of the is precisely encoding the great variety of person- Web,” it might actually be more appropri- al, professional, and genealogical relationships W ate to speak of “intelligent design” — we between people and organizations. By contrast, can actually point to a living, breathing, and an accidental challenge is that any blogger with actively involved Creator of the Web. We can even some knowledge of HTML can add microformat consult Tim Berners-Lee’s stated goals for the markup to a text-input form, but uploading an “promised land,” dubbed the Semantic Web. Few external file dedicated to machine-readable use presume we could reach those objectives by ran- remains forbiddingly complex with most blog- domly hacking existing Web standards and hop- ging tools. ing that “natural selection” by authors, software So, although any intelligent designer ought to developers, and readers would ensure powerful be able to rely on the long-established facility of enough abstractions for it. file transfer to publish the “right” model of a social Indeed, the elegant and painstakingly inter- network, the path of least resistance might favor locked edifice of technologies, including RDF, adding one of a handful of fixed tags to an exist- XML, and query languages is now growing pow- ing indirect form — the “blogroll” of hyperlinks to erful enough to attack massive information chal- other people’s sites. -

From FOAF to English: Linguistic Contribution to Web Semantics
From FOAF to English: Linguistic Contribution to Web Semantics Max Silberztein Université de Franche-Comté [email protected] Abstract which sentence to produce. This article presents the linguistic component of such a system. This paper presents a linguistic module capable of generating a set of English sentences that 2 The linguistic framework correspond to a Resource Description Framework (RDF) statement; I discuss how a Based on the principles of linguistic approaches to generator can control the linguistic module, as generation laid out by Danlos (1987), I have used well as the various limitations of a pure the NooJ1 platform to construct a set of linguistic linguistic framework. resources that parses a sequence of RDF statements and produces a corresponding set of English 1 Introduction sentences. NooJ allows linguists to construct structured sets of linguistic resources (“modules”) Automatic Natural Language Generation Software in the form of dictionaries and grammars2 to aims to express information stored in a knowledge formalize a large gamut of linguistic phenomena: database as a Natural Language text. The orthography and spelling, inflectional, derivational information at the source typically consists of a and agglutinative morphology, local and structural series of simple atomic statements, such as “John syntax, transformational syntax, lexical and owns a house”, “Mary lives in Manchester”, “Peter predicative semantics. All linguistic analyses are is Ann’s cousin”. These statements are usually performed sequentially by adding and/or removing stored in a knowledge database or ontology in a linguistic annotations to/from a Text Annotation formal notation such as Prolog (e.g. Structure (TAS); at each level of the analysis, each “Own(John,House)”) or XML.