Security and Hardening Guide Security and Hardening Guide Opensuse Leap 15.3
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
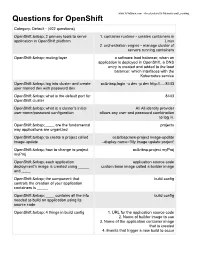
Questions for Openshift
www.YoYoBrain.com - Accelerators for Memory and Learning Questions for OpenShift Category: Default - (402 questions) OpenShift: 2 primary tools to serve 1. container runtime - creates containers in application in OpenShift platform Linux 2. orchestration engine - manage cluster of servers running containers OpenShift: routing layer a software load balancer, when an application is deployed in OpenShift, a DNS entry is created and added to the load balancer, which interfaces with the Kubernetes service OpenShift: log into cluster and create oc login -u dev -p dev http://....:8443 user named dev with password dev OpenShift: what is the default port for 8443 OpenShift cluster OpenShift: what is a cluster's initial All All identity provider user name/password configuration allows any user and password combination to log in. OpenShift: ____ are the fundamental projects way applications are organized OpenShift: to create a project called oc new-project image-update image-update --display-name='My image update project' OpenShift: how to change to project oc project myProj myProj OpenShift: each application application source code deployment's image is created using _____ custom base image called a builder image and ____ OpenShift: the component that build config controls the creation of your application containers is _____ OpenShift: ____ contains all the info build config needed to build an application using its source code OpenShift: 4 things in build config 1. URL for the application source code 2. Name of builder image to use 3. Name of the application container image that is created 4. -

An User & Developer Perspective on Immutable Oses
An User & Developer Perspective on Dario Faggioli Virtualization SW. Eng. @ SUSE Immutable OSes [email protected] dariof @DarioFaggioli https://dariofaggioli.wordpress.com/ https://about.me/dario.faggioli About Me What I do ● Virtualization Specialist Sw. Eng. @ SUSE since 2018, working on Xen, KVM, QEMU, mostly about performance related stuff ● Daily activities ⇒ how and what for I use my workstation ○ Read and send emails (Evolution, git-send-email, stg mail, ...) ○ Write, build & test code (Xen, KVM, Libvirt, QEMU) ○ Work with the Open Build Service (OBS) ○ Browse Web ○ Test OSes in VMs ○ Meetings / Video calls / Online conferences ○ Chat, work and personal ○ Some 3D Printing ○ Occasionally play games ○ Occasional video-editing ○ Maybe scan / print some document 2 ● Can all of the above be done with an immutable OS ? Immutable OS: What ? Either: ● An OS that you cannot modify Or, at least: ● An OS that you will have an hard time modifying What do you mean “modify” ? ● E.g., installing packages ● ⇒ An OS on which you cannot install packages ● ⇒ An OS on which you will have an hard time installing packages 3 Immutable OS: What ? Seriously? 4 Immutable OS: Why ? Because it will stay clean and hard to break ● Does this sound familiar? ○ Let’s install foo, and it’s dependency, libfoobar_1 ○ Let’s install bar (depends from libfoobar_1, we have it already) ○ Actually, let’s add an external repo. It has libfoobar_2 that makes foo work better! ○ Oh no... libfoobar_2 would break bar!! ● Yeah. It happens. Even in the best families distros -
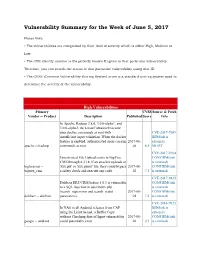
Vulnerability Summary for the Week of June 5, 2017
Vulnerability Summary for the Week of June 5, 2017 Please Note: • The vulnerabilities are categorized by their level of severity which is either High, Medium or Low. • The CVE identity number is the publicly known ID given to that particular vulnerability. Therefore, you can search the status of that particular vulnerability using that ID. • The CVSS (Common Vulnerability Scoring System) score is a standard scoring system used to determine the severity of the vulnerability. High Vulnerabilities Primary CVSS Source & Patch Vendor -- Product Description Published Score Info In Apache Hadoop 2.8.0, 3.0.0-alpha1, and 3.0.0-alpha2, the LinuxContainerExecutor runs docker commands as root with CVE-2017-7669 insufficient input validation. When the docker BID(link is feature is enabled, authenticated users can run 2017-06- external) apache -- hadoop commands as root. 04 8.5 MLIST CVE-2017-9364 Unrestricted File Upload exists in BigTree CONFIRM(link CMS through 4.2.18: if an attacker uploads an is external) bigtreecms -- 'xxx.pht' or 'xxx.phtml' file, they could bypass 2017-06- CONFIRM(link bigtree_cms a safety check and execute any code. 02 7.5 is external) CVE-2017-9435 Dolibarr ERP/CRM before 5.0.3 is vulnerable CONFIRM(link to a SQL injection in user/index.php is external) (search_supervisor and search_statut 2017-06- CONFIRM(link dolibarr -- dolibarr parameters). 05 7.5 is external) CVE-2014-9923 In NAS in all Android releases from CAF BID(link is using the Linux kernel, a Buffer Copy external) without Checking Size of Input vulnerability 2017-06- CONFIRM(link google -- android could potentially exist. -

The BIG Change for Opensuse Leap 15.3 About Me
The BIG Change for openSUSE Leap 15.3 About Me openSUSE Manager Hobbies ● Marketing/PR ● Fantasy Sports ● Event Organizer ● Mining ● Coordinate Event ● Series Binge Watcher Sponsorship Interesting Fact Education Christopher Reeve was ● MBA - Business to blame for me breaking my arm ● BA - Education Douglas DeMaio (Superman 1978) V International GNU Health Conference - Nov. 20 - 21, online event - #GHCon2020 The Way to openSUSE Leap 15.3 bout Me !losing the Leap Gap What is it & why does it matter. Jump 15.&.1 Leap 15.3 The efforts to change What to expect with in how a distribution is coming releases of this built openSUSE distribution What is openSUSE Leap Leap is trying to bridge “Community and Enterprise” the distribution is based on the latest version of SUSE Linux Enterprise available to the date, typically with a 12 months release cycle. Leap 15.2 Retrospective told us that users value most the installer, stability, seamless migrations, and YaST. These would be then our strengths according to users! The distribution is often profiled as the more stable one and easy to use as there should be no radical or disruptive changes in between minor updates. Some users say It’s the KDE distribution. Box says “The Linux Distribution for Beginners and Pros” !"osing the Leap Gap ● CtLG is a SUSE driven effort to bring Leap closer to SUSE Linux Enterprise than ever before. This brings quite some challenges but also open some new opportunities. ● Unification of openSUSE Leap and SUSE Linux Enterprise 15 code streams and feature set. ● Concept of building a community distribution by combining rpms from openSUSE Backports (community part) and SUSE signed SLE rpms (Enterprise part). -

Zypper Cheat Sheet Or Type M an Zypper on a Terminal
More Information: Page 1 Zypper Cheat Sheet https://en.opensuse.org/SDB:Zypper_usage or type m an zypper on a terminal For Zypper version 1.0.9 Package Management Source Packages and Build Dependencies Basic Help Selecting Packages zypper source-install or zypper si Examples: zypper #list the available global options and commands By capability name: zypper si zypper zypper help [command] #Print help for a specific command zypper in 'perl(Log::Log4perl)' Install only the source package zypper shell or zypper sh #Open a zypper shell session zypper in qt zypper in -D zypper By capability name and/or architecture and/or version Install only the build dependencies zypper in 'zypper<0.12.10' Repository Management zypper in -d zypper zypper in zypper.i586=0.12.11 Listing Defined Repositories By exact package name (--name) Updating Packages zypper in -n ftp zypper repos or zypper lr By exact package name and repository (implies --name) zypper update or zypper up Examples: zypper in factory:zypper Examples: zypper lr -u #include repo URI on the table By package name using wildcards zypper up #update all installed packages zypper lr -P #include repo priority and sort by it zypper in yast*ftp* with newer version as far as possible By specifying a .rpm file to install zypper up libzypp zypper #update libzypp Refreshing Repositories zypper in skype-2.0.0.72-suse.i586.rpm and zypper zypper refresh or zypper ref zypper in sqlite3 #update sqlite3 or install Installing Packages Examples: if not yet installed zypper ref packman main #specify repos to be -
Snort 2.9.9.X on Opensuse Leap 42.2
Snort Installation on openSUSE Leap 42.2 64 bits Boris A. Gómez Universidad Tecnológica de Panamá July 2017 About This Guide This guide has been tested on openSUSE Leap 42.2, 64 bits, using DAQ 2.0.6 and Snort 2.9.9.0. Software was installed in a virtual machine: Virtual Machine Manager: VirtualBox 5.1.22 or KVM 1.4.0 HOST operating system: Windows 7 or openSUSE Leap 42.2 GUEST operating system: openSUSE Leap 42.2 (Snort will be installed here) For clarity, the following color code was used: Orange – commands that the user types at the shell prompt. Blue – text inside of configuration files. Purple – text to focus your attention on. This guide is based on the document "Snort 2.9.8.x on OpenSuSE 13x" by William Parker. Network Card Configuration Run VirtualBox | KVM manager and configure the network section of the guest machine to bridge mode. KVM Manager: VirtualBox Manager: Guest Machine Start your guest machine and set its network interface card to a static IP, for example 192.168.99.10, then check settings: ifconfig eth0 Link encap:Ethernet HWaddr 08:00:27:50:CA:99 inet addr: 192.168.99.10 Bcast:192.168.99.255 Mask:255.255.255.0 Verify that you can access Internet by accessing a web page, for example: https://snort.org Before proceeding, it is advisable to update the system. Required Packages Use YAST to install the following packages: gcc version 4.8.x (including libraries: libgcc_s1 (5.3.1), libgcc_s1-32bit(5.3.1)) flex (2.5.37) bison (2.7) php5-zlib (5.5.14 including zlib-devel 1.2.8) libpcap1 (1.8.1 including libpcap-devel 1.8.1) (versions must match) libpcre1 (8.39 including pcre-devel 8.39 and libpcre1-32bit 8.39) (versions must match) libdnet1 (1.12 including libdnet-devel 1.12) (versions must match) tcpdump (4.5.1). -

(Un)Smashing the Stack
Hello, Interwebs Hi, and thanks for reading this. As I mentioned a number of times during the talk this was one long, hard slog of a topic for me. My intent was not to duplicate existing research (Johnson and Silberman @ BHUS05, others), but to try to make this topic comprehensible for the typical security professional, who (GASP! SHOCK! HORROR!) may not necessarily grasp all the hairy internals of exploit development, but still is tasked with protecting systems. For the other 90% of us out there, our job is not to be leet, but rather not to get owned, something I hope to get a little bit better at every day. Since exploit mitigation is something that might bring us all a little bit closer to that, I wanted to explore the topic. Thanks much to BH for giving me the opportunity to do so, and to all of you for listening. Thanks also to all the amazing people working on these technologies, especially the PaX team and Hiroaki Etoh of IBM. -- shawn P.S. It’s actually Thompson that had the Phil Collins hair, not Ritchie. Sorry, Dennis. 28 75 6e 29 53 6d 61 73 68 69 6e 67 20 74 68 65 20 53 74 61 63 6b 0d 0a (un)Smashing the Stack 4f 76 65 72 66 6c 6f 77 73 2c 20 43 6f 75 6e 74 65 72 6d 65 61 73 75 72 65 73 20 61 6e 64 20 74 68 65 20 52 65 61 6c 20 57 6f 72 6c 64 Overflows, Countermeasures and the Real World Shawn Moyer :: Chief Researcher ---- SpearTip Technologies ---> blackhat [at] cipherpunx [dot] org Hey, who is this guy? ShawnM: InfoSec consultant, (quasi-) developer, husband, father, and raging paranoid with obsessive tendencies Chief Researcher at SpearTip Technologies Security Consultancy in Saint Louis, MO Forensics, Assessment, MSSP, network analysis Weddings, Funerals, Bar Mitzvahs I like unsolvable problems, so I’m mostly interested in defense. -

Integrating New Major Components on Fast and Slow Moving Distributions
IntegratingIntegrating newnew majormajor componentscomponents onon fastfast andand slowslow movingmoving distributionsdistributions How latest GNOME desktop was integrated into latest SUSE / openSUSE releases Frédéric Crozat <[email protected]> SUSE Linux Enterprise Release Manager What we don’t do What we do DistributionDistribution deliverydelivery stylesstyles 4 Three distributions styles ● Rolling: – Bleeding edge – Release as soon as possible – Example: openSUSE Tumbleweed, ArchLinux, Gentoo ● Regular: – Release one to twice a year – Update their entire stack for each release – Example: Ubuntu, Fedora, Debian ● LTS / Enterprise: – Slow cadence (yearly or even less than that) – Very few things move between sub-releases – Example: openSUSE Leap, Ubuntu LTS, SLES/SLED, RHEL 5 openSUSE/SUSE terminology ● OBS = OpenBuildService ● SLE = SUSE Linux Enterprise (Server / Desktop) – Enterprise distribution, developed by SUSE ● openSUSE Tumbleweed: – openSUSE Rolling release, by openSUSE, using only Factory packages, tested by openQA ● openSUSE Factory: – Development repository for Tumbleweed ● openSUSE Leap: – openSUSE Stable release, based on SLE common code + Packages from Factory (or specific repository) 6 IntegrationIntegration processprocess 7 OBS and Devel project ● On OBS, every source package is handled in a project which can build several packages together ● openSUSE Tumbleweed uses devel project per “topic” (KDE, GNOME, X11, …) ● Changes (patch, version update) are done in Devel projects and then, pushed to “main” distribution for -

Guide to Open Source Solutions
White paper ___________________________ Guide to open source solutions “Guide to open source by Smile ” Page 2 PREAMBLE SMILE Smile is a company of engineers specialising in the implementing of open source solutions OM and the integrating of systems relying on open source. Smile is member of APRIL, the C . association for the promotion and defence of free software, Alliance Libre, PLOSS, and PLOSS RA, which are regional cluster associations of free software companies. OSS Smile has 600 throughout the World which makes it the largest company in Europe - specialising in open source. Since approximately 2000, Smile has been actively supervising developments in technology which enables it to discover the most promising open source products, to qualify and assess them so as to offer its clients the most accomplished, robust and sustainable products. SMILE . This approach has led to a range of white papers covering various fields of application: Content management (2004), portals (2005), business intelligence (2006), PHP frameworks (2007), virtualisation (2007), and electronic document management (2008), as well as PGIs/ERPs (2008). Among the works published in 2009, we would also cite “open source VPN’s”, “Firewall open source flow control”, and “Middleware”, within the framework of the WWW “System and Infrastructure” collection. Each of these works presents a selection of best open source solutions for the domain in question, their respective qualities as well as operational feedback. As open source solutions continue to acquire new domains, Smile will be there to help its clients benefit from these in a risk-free way. Smile is present in the European IT landscape as the integration architect of choice to support the largest companies in the adoption of the best open source solutions. -

Red Hat Directory Server 11 Installation Guide
Red Hat Directory Server 11 Installation Guide Instructions for installing Red Hat Directory Server Last Updated: 2021-04-23 Red Hat Directory Server 11 Installation Guide Instructions for installing Red Hat Directory Server Marc Muehlfeld Red Hat Customer Content Services [email protected] Legal Notice Copyright © 2021 Red Hat, Inc. The text of and illustrations in this document are licensed by Red Hat under a Creative Commons Attribution–Share Alike 3.0 Unported license ("CC-BY-SA"). An explanation of CC-BY-SA is available at http://creativecommons.org/licenses/by-sa/3.0/ . In accordance with CC-BY-SA, if you distribute this document or an adaptation of it, you must provide the URL for the original version. Red Hat, as the licensor of this document, waives the right to enforce, and agrees not to assert, Section 4d of CC-BY-SA to the fullest extent permitted by applicable law. Red Hat, Red Hat Enterprise Linux, the Shadowman logo, the Red Hat logo, JBoss, OpenShift, Fedora, the Infinity logo, and RHCE are trademarks of Red Hat, Inc., registered in the United States and other countries. Linux ® is the registered trademark of Linus Torvalds in the United States and other countries. Java ® is a registered trademark of Oracle and/or its affiliates. XFS ® is a trademark of Silicon Graphics International Corp. or its subsidiaries in the United States and/or other countries. MySQL ® is a registered trademark of MySQL AB in the United States, the European Union and other countries. Node.js ® is an official trademark of Joyent. Red Hat is not formally related to or endorsed by the official Joyent Node.js open source or commercial project. -

Red Hat Enterprise Linux 6 6.4 Release Notes
Red Hat Enterprise Linux 6 6.4 Release Notes Release Notes for Red Hat Enterprise Linux 6.4 Edition 4 Last Updated: 2017-10-20 Red Hat Enterprise Linux 6 6.4 Release Notes Release Notes for Red Hat Enterprise Linux 6.4 Edition 4 Red Hat Engineering Content Services Legal Notice Copyright © 2012 Red Hat, Inc. This document is licensed by Red Hat under the Creative Commons Attribution-ShareAlike 3.0 Unported License. If you distribute this document, or a modified version of it, you must provide attribution to Red Hat, Inc. and provide a link to the original. If the document is modified, all Red Hat trademarks must be removed. Red Hat, as the licensor of this document, waives the right to enforce, and agrees not to assert, Section 4d of CC-BY-SA to the fullest extent permitted by applicable law. Red Hat, Red Hat Enterprise Linux, the Shadowman logo, JBoss, OpenShift, Fedora, the Infinity logo, and RHCE are trademarks of Red Hat, Inc., registered in the United States and other countries. Linux ® is the registered trademark of Linus Torvalds in the United States and other countries. Java ® is a registered trademark of Oracle and/or its affiliates. XFS ® is a trademark of Silicon Graphics International Corp. or its subsidiaries in the United States and/or other countries. MySQL ® is a registered trademark of MySQL AB in the United States, the European Union and other countries. Node.js ® is an official trademark of Joyent. Red Hat Software Collections is not formally related to or endorsed by the official Joyent Node.js open source or commercial project. -

Debian \ Amber \ Arco-Debian \ Arc-Live \ Aslinux \ Beatrix
Debian \ Amber \ Arco-Debian \ Arc-Live \ ASLinux \ BeatriX \ BlackRhino \ BlankON \ Bluewall \ BOSS \ Canaima \ Clonezilla Live \ Conducit \ Corel \ Xandros \ DeadCD \ Olive \ DeMuDi \ \ 64Studio (64 Studio) \ DoudouLinux \ DRBL \ Elive \ Epidemic \ Estrella Roja \ Euronode \ GALPon MiniNo \ Gibraltar \ GNUGuitarINUX \ gnuLiNex \ \ Lihuen \ grml \ Guadalinex \ Impi \ Inquisitor \ Linux Mint Debian \ LliureX \ K-DEMar \ kademar \ Knoppix \ \ B2D \ \ Bioknoppix \ \ Damn Small Linux \ \ \ Hikarunix \ \ \ DSL-N \ \ \ Damn Vulnerable Linux \ \ Danix \ \ Feather \ \ INSERT \ \ Joatha \ \ Kaella \ \ Kanotix \ \ \ Auditor Security Linux \ \ \ Backtrack \ \ \ Parsix \ \ Kurumin \ \ \ Dizinha \ \ \ \ NeoDizinha \ \ \ \ Patinho Faminto \ \ \ Kalango \ \ \ Poseidon \ \ MAX \ \ Medialinux \ \ Mediainlinux \ \ ArtistX \ \ Morphix \ \ \ Aquamorph \ \ \ Dreamlinux \ \ \ Hiwix \ \ \ Hiweed \ \ \ \ Deepin \ \ \ ZoneCD \ \ Musix \ \ ParallelKnoppix \ \ Quantian \ \ Shabdix \ \ Symphony OS \ \ Whoppix \ \ WHAX \ LEAF \ Libranet \ Librassoc \ Lindows \ Linspire \ \ Freespire \ Liquid Lemur \ Matriux \ MEPIS \ SimplyMEPIS \ \ antiX \ \ \ Swift \ Metamorphose \ miniwoody \ Bonzai \ MoLinux \ \ Tirwal \ NepaLinux \ Nova \ Omoikane (Arma) \ OpenMediaVault \ OS2005 \ Maemo \ Meego Harmattan \ PelicanHPC \ Progeny \ Progress \ Proxmox \ PureOS \ Red Ribbon \ Resulinux \ Rxart \ SalineOS \ Semplice \ sidux \ aptosid \ \ siduction \ Skolelinux \ Snowlinux \ srvRX live \ Storm \ Tails \ ThinClientOS \ Trisquel \ Tuquito \ Ubuntu \ \ A/V \ \ AV \ \ Airinux \ \ Arabian