Automated Refactoring of Super-Class Method Invocations to the Template Method Design Pattern
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

OOP with Java 16
OOP with Java 16. Inheritance and Overriding Thomas Weise · 汤卫思 [email protected] · http://iao.hfuu.edu.cn Hefei University, South Campus 2 合肥学院 南艳湖校区/南2区 Faculty of Computer Science and Technology 计算机科学与技术系 Institute of Applied Optimization 应用优化研究所 230601 Shushan District, Hefei, Anhui, China 中国 安徽省 合肥市 蜀山区 230601 Econ. & Tech. Devel. Zone, Jinxiu Dadao 99 经济技术开发区 锦绣大道99号 Outline 1 Introduction 2 Extending Classes and Class Hierarchy 3 Multi-Level Inheritance 4 The Class Object 5 static vs. instance methods 6 Summary website OOPwithJava ThomasWeise 2/23 Introduction • So far, we have basically treated as objects as data structures and used methods to work on them OOPwithJava ThomasWeise 3/23 Introduction • So far, we have basically treated as objects as data structures and used methods to work on them • But Object-Oriented Programming is much more OOPwithJava ThomasWeise 3/23 Introduction • So far, we have basically treated as objects as data structures and used methods to work on them • But Object-Oriented Programming is much more • The true power of OOP arises from class inheritance and extension (often called specialization) OOPwithJava ThomasWeise 3/23 Extending Classes • A class Student can extend another class Person OOPwithJava ThomasWeise 4/23 Extending Classes • A class Student can extend another class Person • Student inherits all the fields and functionality of the original class Person OOPwithJava ThomasWeise 4/23 Extending Classes • A class Student can extend another class Person • Student inherits all the fields and functionality -

Programming in JAVA Topic: • a Closer Look at Methods And
B. Sc. (H) Computer Science Semester II BHCS03 – Programming in JAVA Topic: A Closer Look at Methods and Classes Inheritance Command Line Arguments The java command-line argument is an argument i.e. passed at the time of running the java program. The arguments passed from the console can be received in the java program and it can be used as an input. So, it provides a convenient way to check the behavior of the program for the different values. You can pass N (1,2,3 and so on) numbers of arguments from the command prompt. Simple example of command-line argument In this example, we are receiving only one argument and printing it. To run this java program, you must pass at least one argument from the command prompt. class CommandLineExample{ public static void main(String args[]){ System.out.println("Your first argument is: "+args[0]); } } compile by > javac CommandLineExample.java run by > java CommandLineExample sonoo Output: Your first argument is: sonoo Varargs: Variable length arguments A method with variable length arguments(Varargs) in Java can have zero or multiple arguments. Variable length arguments are most useful when the number of arguments to be passed to the method is not known beforehand. They also reduce the code as overloaded methods are not required. Example public class Demo { public static void Varargs(String... str) { System.out.println("\nNumber of arguments are: " + str.length); System.out.println("The argument values are: "); for (String s : str) System.out.println(s); } public static void main(String args[]) { Varargs("Apple", "Mango", "Pear"); Varargs(); Varargs("Magic"); } } Output Number of arguments are: 3 The argument values are: Apple Mango Pear Number of arguments are: 0 The argument values are: Number of arguments are: 1 The argument values are: Magic Overloading Varargs Methods Overloading allows different methods to have same name, but different signatures where signature can differ by number of input parameters or type of input parameters or both. -

Module 3 Inheritance in Java
Module 3 Inheritance in Java Inheritance in java is a mechanism in which one object acquires all the properties and behaviors of parent object. The idea behind inheritance in java is that you can create new classes that are built upon existing classes. When you inherit from an existing class, you can reuse methods and fields of parent class, and you can add new methods and fields also. Inheritance represents the IS-A relationship, also known as parent-child relationship. For Method Overriding (so runtime polymorphism can be achieved). For Code Reusability. Syntax of Java Inheritance class Subclass-name extends Superclass-name { KTUNOTES.IN //methods and fields } The extends keyword indicates that you are making a new class that derives from an existing class. In the terminology of Java, a class that is inherited is called a super class. The new class is called a subclass. As displayed in the above figure, Programmer is the subclass and Employee is the superclass. Relationship between two classes is Programmer IS-A Employee.It means that Programmer is a type of Employee. class Employee{ float salary=40000; } class Programmer extends Employee{ int bonus=10000; public static void main(String args[]){ Programmer p=new Programmer(); System.out.println("Programmer salary is:"+p.salary); System.out.println("Bonus of Programmer is:"+p.bonus); } } Programmer salary is:40000.0 Bonus of programmer is:10000 In the above example, Programmer object can access the field of own class as well as of Employee class i.e. code reusability. Downloaded from Ktunotes.in Types of inheritance in java On the basis of class, there can be three types of inheritance in java: single, multilevel hierarchical. -

Conformity Behavior of Dissimilar Methods for Object Oriented
K. LOUZAOUUI Conformity behavior of dissimilar methods for object oriented constraint programming 212 Conformity Behavior of Dissimilar Methods for Object Oriented Constraint Programming Khadija Louzaoui Khalid Benlhachmi Department of Mathematics Department of Computer Sciences Faculty of Sciences, Ibn Tofail University Faculty of Sciences, Ibn Tofail University Kenitra, Morocco Kenitra, Morocco Abstract—This paper presents an approach for testing the number of test cases is infinite, therefore, testing is very conformity of overridden and overriding methods using expensive. So, how to select the most proper set of test cases? inheritance principle. The first objective of this work is the In practice, various techniques are used for that, some of them reduction of the test sequences by using only one generation of are based on the specification of the program under test using test data. The second result is the conformity testing of methods precondition, postcondition and invariant constraints. In this even if they are not similar: Our approach shows how the similarity partitioning can be used for testing not the similarity way the specifications by constraints in an object oriented behavior between methods but the conformity behavior of paradigm can be specified by formal languages as OCL [3] and subclasses for an object oriented model. JML [4], and are used for generating test data from formal specifications [5]. This software verification by constraints can In this work we use a mathematical modeling such as domain help for creating a mathematical modeling and building the partitioning and states graph for testing the conformity of parts of different classes of errors (equivalence partitioning). -
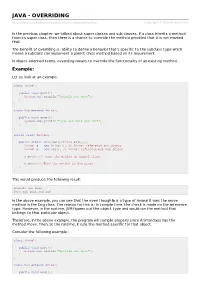
JAVA - OVERRIDING Copyright © Tutorialspoint.Com
JAVA - OVERRIDING http://www.tutorialspoint.com/java/java_overriding.htm Copyright © tutorialspoint.com In the previous chapter, we talked about super classes and sub classes. If a class inherits a method from its super class, then there is a chance to override the method provided that it is not marked final. The benefit of overriding is: ability to define a behavior that's specific to the subclass type which means a subclass can implement a parent class method based on its requirement. In object-oriented terms, overriding means to override the functionality of an existing method. Example: Let us look at an example. class Animal{ public void move(){ System.out.println("Animals can move"); } } class Dog extends Animal{ public void move(){ System.out.println("Dogs can walk and run"); } } public class TestDog{ public static void main(String args[]){ Animal a = new Animal(); // Animal reference and object Animal b = new Dog(); // Animal reference but Dog object a.move();// runs the method in Animal class b.move();//Runs the method in Dog class } } This would produce the following result: Animals can move Dogs can walk and run In the above example, you can see that the even though b is a type of Animal it runs the move method in the Dog class. The reason for this is: In compile time, the check is made on the reference type. However, in the runtime, JVM figures out the object type and would run the method that belongs to that particular object. Therefore, in the above example, the program will compile properly since Animal class has the method move. -

Method Overriding
Method Overriding OOC 4th Sem, ‘B’ Div 2016-17 Prof. Mouna M. Naravani ➢ In a class hierarchy, when a method in a subclass has the same name and type signature as a method in its superclass, then the method in the subclass is said to override the method in the superclass. ➢ When an overridden method is called from within a subclass, it will always refer to the version of that method defined by the subclass. ➢ The version of the method defined by the superclass will be hidden. class A { class B extends A { int i, j; int k; A(int a, int b) { B(int a, int b, int c) { i = a; super(a, b); j = b; k = c; } } // display i and j // display k -- this overrides show() in A void show() { void show() { System.out.println("i and j: " + i + " " + j); System.out.println("k: " + k); } } } } class Override { Output: public static void main(String args[]) k : 3 { B subOb = new B(1, 2, 3); subOb.show(); // this calls show() in B } } ➢ When show( ) is invoked on an object of type B, the version of show( ) defined within B is used. ➢ That is, the version of show( ) inside B overrides the version declared in A. ➢ If you wish to access the superclass version of an overridden method, you can do so by using super. class B extends A { int k; B(int a, int b, int c) { super(a, b); Output: k = c; i and j : 1 2 } k : 3 void show() { super.show(); // this calls A's show() System.out.println("k: " + k); } } ➢ Method overriding occurs only when the names and the type signatures of the two methods are identical. -

A Runtime Assertion Checker for the Java Modeling Language Yoonsik Cheon Iowa State University
Iowa State University Capstones, Theses and Retrospective Theses and Dissertations Dissertations 2003 A runtime assertion checker for the Java Modeling Language Yoonsik Cheon Iowa State University Follow this and additional works at: https://lib.dr.iastate.edu/rtd Part of the Computer Sciences Commons Recommended Citation Cheon, Yoonsik, "A runtime assertion checker for the Java Modeling Language " (2003). Retrospective Theses and Dissertations. 570. https://lib.dr.iastate.edu/rtd/570 This Dissertation is brought to you for free and open access by the Iowa State University Capstones, Theses and Dissertations at Iowa State University Digital Repository. It has been accepted for inclusion in Retrospective Theses and Dissertations by an authorized administrator of Iowa State University Digital Repository. For more information, please contact [email protected]. A runtime assertion checker for the Java Modeling Language by Yoonsik Cheon A dissertation submitted to the graduate faculty in partial fulfillment of the requirements for the degree of DOCTOR OF PHILOSOPHY Major: Computer Science Program of Study Committee: Gary T. Leavens, Major Professor Les Miller Robyn R. Lutz Don L. Pigozzi Clifford Bergman Iowa State University Ames, Iowa 2003 Copyright © Yoonsik Cheon, 2003. All rights reserved. UMI Number: 3085895 Copyright 2003 by Cheon, Yoonsik All rights reserved. UMI UMI Microform 3085895 Copyright 2003 by ProQuest Information and Learning Company. All rights reserved. This microform edition is protected against unauthorized copying under Title 17, United States Code. ProQuest Information and Learning Company 300 North Zeeb Road P.O. Box 1346 Ann Arbor, Ml 48106-1346 ii Graduate College Iowa State University This is to certify that the doctoral dissertation of Yoonsik Cheon has met the dissertation requirements of Iowa State University Signature was redacted for privacy. -

Unit 2 – Part 4. Polymorphism(OOP)
Unit 2 – part 4. Polymorphism(OOP) BCIS 222. Object Oriented Programming Instructor: Dr. Carlo A. Mora LMS: http://l earn.nmsu.ed u OOP Principles y Piece of Cake!! A (Abstraction) E P (Encapsulation) (Polymorphism) I (Inheritance) protected Members y Intermediate level of protection between public and private y prottdtected members accessible to y superclass members y subclass members y Clbhlass members in the same namespace y Subclass access superclass member y Keyword base and a dot (.) y E.g. base.toString() y Method overloading vs. Method overriding y Overloading Having several methods with same name but different parameters y Overriding redefining a method in a subclass y How to access and overridden method? super keyword UiUsing protec tdted iitnstance variiblables y Advantages y subclasses can modify values directly y Slight increase in performance y Avoid set/get function call overhead y Disadvantages y No validityyg checking y subclass can assign illegal value y Implementation dependent y subcl ass method s more likliklely depend ent on superclass iilmplemen ta tion y superclass implementation changes may result in subclass modifications y Fragile (brittle) software Wrapping up the Case Study y What advantages do we have by having a class Hierarchy? y No need to declare common members in subclasses (e.g. name) y Simplified version of methods (e.g. toString) y Wha t is the purpose of y GetGraduationDate method? y Rethink the TestClass y What if I need to create an array to hold different types of students? Polymorphism y Dictionary -

Inheritance in Java
Inheritance in Java • Inheritance in java is a mechanism in which one object acquires all the properties and behaviors of parent object. • The idea behind inheritance in java is that you can create new classes that are built upon existing classes. When you inherit from an existing class, you can reuse methods and fields of parent class, and you can add new methods and fields also. • Inheritance represents the IS-A relationship, also known as parent-child relationship. Use of inheritance in java • For Method Overriding (so runtime polymorphism can be achieved). • For Code Reusability. Syntax of Java Inheritance class Subclass-name extends Superclass-name { //methods and fields } • The extends keyword indicates that you are making a new class that derives from an existing class. The meaning of "extends" is to increase the functionality. • In the terminology of Java, a class which is inherited is called parent or super class and the new class is called child or subclass. Java Inheritance Example • As displayed in the above figure, Programmer is the subclass and Employee is the superclass. • Relationship between two classes is Programmer IS-A Employee. • It means that Programmer is a type of Employee. Java Inheritance Example class Employee{ float salary=40000; } class Programmer extends Employee{ int bonus=10000; public static void main(String args[]){ Programmer p=new Programmer(); System.out.println("Programmer salary is:"+p.salary); System.out.println("Bonus of Programmer is:"+p.bonus); } } Output : Programmer salary is:40000.0 Bonus of programmer is:10000 Types of inheritance in java • On the basis of class, there can be three types of inheritance in java: single, multilevel and hierarchical. -

Modern C++ Object-Oriented Programming
CPP Modern C++ Object-Oriented Programming ''Combine old and newer features to get the best out of the language'' Margit ANTAL 2020 C++ - Object-Oriented Programming Course content − Introduction to C++ − Object-oriented programming − Generic programming and the STL − Object-oriented design C++ - Object-Oriented Programming References − Bjarne Stroustrup, Herb Sutter, C++ Core Guidelines, 2017. rd − M. Gregoire, Professional C++, 3 edition, John Wiley & Sons, 2014. th − S. Lippman, J. Lajoie, B. E. Moo, C++ Primer, 5 edition, Addison Wesley, , 2013. th − S. Prata, C++ Primer Plus, 6 edition, Addison Wesley, 2012. − N. Josuttis, The C++ standard library. a tutorial and reference. Pearson Education. 2012. − A. Williams, C++ Concurrency in Action:Practical Multithreading. Greenwich, CT: Manning. 2012. Module 1 Introduction to C++ Introduction to C++ Content − History and evolution − Overview of the key features ● New built-in types ● Scope and namespaces ● Enumerations ● Dynamic memory: new and delete ● Smart pointers: unique_ptr, shared_ptr, weak_ptr ● Error handling with exceptions ● References ● The const modifier Introduction to C++ History and evolution − Creator: Bjarne Stroustrup 1983 − Standards: ● The first C++ standard − 1998 (C++98, major) − 2003 (C++03, minor) ● The second C++ standard − 2011 (C++11, major) – significant improvements in language and library − 2014 (C++14, minor) − 2017 (C++17, major) Introduction to C+ History and evolution − source: https://isocpp.org/std/status Introduction to C+ History and evolution − source: -

Chapter 10 ! the More Concrete "Subclass" Extends the More Abstract "Superclass" and Inherits the Functionality of the Superclass
Inheritance ! Two things which are different at one level are similar or equivalent at a more abstract level. ! Upper classes are more abstract; lower classes are more concrete. Chapter 10 ! The more concrete "subclass" extends the more abstract "superclass" and inherits the functionality of the superclass. ! The abstract class generalizes or abstracts the concrete class. 2 Inheritance … Inheritance … ! Recall that abstraction can be realized with an interface. ! An interface generalizes a class or less abstract interface. ! We can also define the abstraction relation between classes. ! The more concrete interface extends the more abstract interface. ! One class can generalize (or abstract) another class. ! Weapon extends Movable ! The more concrete class extends the more abstract class. ! The more concrete class implements the more abstract interface. ! extends ! InteractivePlayer implements Player ClosedFigure Figure ! 3 Circle extends ClosedFigure 4 Inheritance … Inheritance … ! The more concrete class extends the more abstract class. ! The more abstract class generalizes the more concrete class. ! Circle extends ClosedFigure ! ClosedFigure generalizes Circle ! Circle is-a ClosedFigure ! ClosedFigure is an abstraction of Circle ! Circle is a subtype of ClosedFigure ! ClosedFigure is a supertype of Circle ! ! Circle is a descendant of ClosedFigure 5 ClosedFigure is an ancestor of Circle 6 Inheritance … Inheritance … ! Class extension defines a subtype. ! As with interfaces, class extension creates a subtype relation between the types defined by the two classes. ! Expression can be cast up or down the class hierarchy. ! Given the following variable declarations: Figure top; Circle bottom; ! The following are legal (though not necessarily safe) expressions: ! Class extension is a transitive relation. (ClosedFigure) top // downward cast ! Circle extends Figure, etc. -

ICS 111 Overriding, Polymorphism
ICS 111 Overriding, Polymorphism ● overloading methods ● overriding methods ● object polymorphism ● abstract methods, abstract classes ● final methods, final classes ● example from textbook: bank accounts 1 Method Overloading ● We have already seen cases where methods with the same name are called on different parameters: – System.out.println() and System.out.println(String s) – constructors with different parameter types ● In each case, these are different methods that just happen to have the same name ● This is called overloading – for example, System.out.println is an overloaded method – constructors can be overloaded ● Overloading is fine under two conditions: – it doesn’t cause confusion to callers of the methods ● i.e. the methods should do “the same thing”, even though on different parameters – it is done on purpose, rather than accidentally ● accidental overloading can happen when overriding methods – discussed on the next slide 2 Method Overriding ● when a subclass extends a superclass, it inherits its public+protected methods ● sometimes in the subclass we want to modify what one of the superclass methods does: – suppose I create a MyAL class which extends ArrayList – I want to modify the single-parameter add method to add at the beginning of the array list, rather than at the end ● I can do this by re-declaring the same method in the subclass, with the same parameters, and re-implementing it ● the method in the subclass may use super to call the method in the superclass – example for MyAL: public void add(Value v) { super.add(0,