Practical Keystroke Timing Attacks in Sandboxed Javascript (Updated)
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
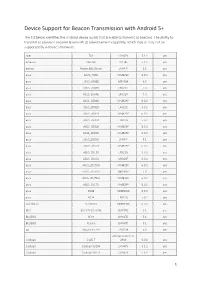
Device Support for Beacon Transmission with Android 5+
Device Support for Beacon Transmission with Android 5+ The list below identifies the Android device builds that are able to transmit as beacons. The ability to transmit as a beacon requires Bluetooth LE advertisement capability, which may or may not be supported by a device’s firmware. Acer T01 LMY47V 5.1.1 yes Amazon KFFOWI LVY48F 5.1.1 yes archos Archos 80d Xenon LMY47I 5.1 yes asus ASUS_T00N MMB29P 6.0.1 yes asus ASUS_X008D MRA58K 6.0 yes asus ASUS_Z008D LRX21V 5.0 yes asus ASUS_Z00AD LRX21V 5.0 yes asus ASUS_Z00AD MMB29P 6.0.1 yes asus ASUS_Z00ED LRX22G 5.0.2 yes asus ASUS_Z00ED MMB29P 6.0.1 yes asus ASUS_Z00LD LRX22G 5.0.2 yes asus ASUS_Z00LD MMB29P 6.0.1 yes asus ASUS_Z00UD MMB29P 6.0.1 yes asus ASUS_Z00VD LMY47I 5.1 yes asus ASUS_Z010D MMB29P 6.0.1 yes asus ASUS_Z011D LRX22G 5.0.2 yes asus ASUS_Z016D MXB48T 6.0.1 yes asus ASUS_Z017DA MMB29P 6.0.1 yes asus ASUS_Z017DA NRD90M 7.0 yes asus ASUS_Z017DB MMB29P 6.0.1 yes asus ASUS_Z017D MMB29P 6.0.1 yes asus P008 MMB29M 6.0.1 yes asus P024 LRX22G 5.0.2 yes blackberry STV100-3 MMB29M 6.0.1 yes BLU BLU STUDIO ONE LMY47D 5.1 yes BLUBOO XFire LMY47D 5.1 yes BLUBOO Xtouch LMY47D 5.1 yes bq Aquaris E5 HD LRX21M 5.0 yes ZBXCNCU5801712 Coolpad C106-7 291S 6.0.1 yes Coolpad Coolpad 3320A LMY47V 5.1.1 yes Coolpad Coolpad 3622A LMY47V 5.1.1 yes 1 CQ CQ-BOX 2.1.0-d158f31 5.1.1 yes CQ CQ-BOX 2.1.0-f9c6a47 5.1.1 yes DANY TECHNOLOGIES HK LTD Genius Talk T460 LMY47I 5.1 yes DOOGEE F5 LMY47D 5.1 yes DOOGEE X5 LMY47I 5.1 yes DOOGEE X5max MRA58K 6.0 yes elephone Elephone P7000 LRX21M 5.0 yes Elephone P8000 -

Copy of Google VR Compatible Phones
Google VR Compatible Phones Apple Huawei LG Nokia Sony iPhone 6s Ascend D2 G Flex 2 7 Xperia X iPhone 6s Plus Ascend P6 G2 7 Plus** Xperia X Performance iPhone 7 Honor 10 ** G3 8 Xperia XZ Premium iPhone 7 Plus Honor 3 G3 LTE-A 8 Sirocco Xperia XZ1 iPhone 8 Honor 3X G750 G4 Lumia 930 Xperia XZ2 Compact iPhone 8 Plus Honor 6 G5 3 Xperia XZ2 Premium iPhone X** Honor 6 Plus GX F310L 5 Xperia XZs Honor 7 Nexus 4 Xperia Z Honor 8 Nexus 5 Xperia Z1 Asus Honor 9 Nexus 5X OnePlus Xperia Z1 S Padfone 2 Honor View 10 ** Optimus G N3 Xperia Z2 Padfone Infinity Mate 10 Porsche Design Optimus G E970 OnePlus Xperia Z2a Padfone Infinity 2 Mate 10 Pro ** Optimus GJ E975W X Xperia Z3 Zenfone 2 Mate 10 ** Optimus LTE2 2 Xperia Z3 + Zenfone 2 Deluxe Mate 10 ** Q6 3 Zperia Z3 + Dual Zenfone 2 Laser Mate 9 Pro V30** 3T Xperia Z3 Dual Zenfone 3 Mate RS Porsche Desing ** V30S ThinQ** 5 Xperia Z5 Zenfone 3 Max Mate S VU 3 F300L 5T** Zperia Z5 Dual Zenfone 3 Zoom Nova 2 X Venture Xperia Z5 Premium Zenfone 4 Max Nova 2 Plus Xperia ZL Zenfone 4 Max Pro Nova 2s ** Samsung Zenfone 5** P10 Microsoft Galaxy A3 P10 Lite Lumia 950 Galaxy A5 Xiaomi P10 Plus Galaxy A8 Black Shark Blackberry P20 ** Galaxy A8+ Mi 3 Motion P20 Lite ** Motorola Galaxy Alpha Mi 4 Priv P20 Pro ** DROID Maxx Galaxy C5 Pro Mi 4 LTE Z30 P8 DROID Turbo Galaxy C7 Mi 4c P9 DROID Turbo 2 Galaxy J5 Mi 4i Y7 DROID Ultra Galaxy J7 Mi 5 Google Y9 (2018) ** Mot X Force Galaxy J7 Pro Mi 5c PIxel Moto G4 Galaxy J7 V Mi 5s Pixel 2 Moto G4 Plus Galaxy K Zoom Mi 6 Pixel 2 XL ** Lenovo Moto G5 Galaxy Note 3 Neo -

Brand Old Device
# New Device Old Device - Brand Old Device - Model Name 1 Galaxy A6+ Asus Asus Zenfone 2 Laser ZE500KL 2 Galaxy A6+ Asus Asus Zenfone 2 Laser ZE601KL 3 Galaxy A6+ Asus Asus ZenFone 2 ZE550ML 4 Galaxy A6+ Asus Asus Zenfone 2 ZE551ML 5 Galaxy A6+ Asus Asus Zenfone 3 Laser 6 Galaxy A6+ Asus Asus Zenfone 3 Max ZC520TL 7 Galaxy A6+ Asus Asus Zenfone 3 Max ZC553KL 8 Galaxy A6+ Asus Asus Zenfone 3 ZE520KL 9 Galaxy A6+ Asus Asus Zenfone 3 ZE552KL 10 Galaxy A6+ Asus Asus Zenfone 3s Max 11 Galaxy A6+ Asus Asus Zenfone Max 12 Galaxy A6+ Asus Asus Zenfone Selfie 13 Galaxy A6+ Asus Asus ZenFone Zoom ZX550 14 Galaxy A6+ Gionee Gionee A1 15 Galaxy A6+ Gionee Gionee A1 Lite 16 Galaxy A6+ Gionee Gionee A1 Plus 17 Galaxy A6+ Gionee Gionee Elife E8 18 Galaxy A6+ Gionee Gionee Elife S Plus 19 Galaxy A6+ Gionee Gionee Elife S7 20 Galaxy A6+ Gionee Gionee F103 21 Galaxy A6+ Gionee Gionee F103 Pro 22 Galaxy A6+ Gionee Gionee Marathon M4 23 Galaxy A6+ Gionee Gionee Marathon M5 24 Galaxy A6+ Gionee Gionee marathon M5 Lite 25 Galaxy A6+ Gionee Gionee Marathon M5 Plus 26 Galaxy A6+ Gionee Gionee P5L 27 Galaxy A6+ Gionee Gionee P7 Max 28 Galaxy A6+ Gionee Gionee S6 29 Galaxy A6+ Gionee Gionee S6 Pro 30 Galaxy A6+ Gionee Gionee S6s 31 Galaxy A6+ Gionee Gionee X1s 32 Galaxy A6+ Google Google Pixel 33 Galaxy A6+ Google Google Pixel XL LTE 34 Galaxy A6+ Google Nexus 5X 35 Galaxy A6+ Google Nexus 6 36 Galaxy A6+ Google Nexus 6P 37 Galaxy A6+ HTC Htc 10 38 Galaxy A6+ HTC Htc Desire 10 Pro 39 Galaxy A6+ HTC Htc Desire 628 40 Galaxy A6+ HTC HTC Desire 630 41 Galaxy A6+ -

Xiaomi Redmi Note 3 PRO HASZNÁLATI ÚTMUTATÓ
Xiaomi Redmi Note 3 PRO HASZNÁLATI ÚTMUTATÓ Ez a használati útmutató a Xiaomi Global 7.2.3.0 MIUI7 Stable International szoftver verziójához készült. A frissítések után egyes funkciók változhatnak! Xiaomi Redmi Note 3 PRO Manual HU v1.0 - 1. oldal Bevezetés Köszönjük, hogy Xiaomi terméket választott! Kérjük, használatba vétel előtt olvassa el figyelmesen ezt a használati utasítást, hogy a készüléket könnyen és egyszerűen tudja használni. A jobb szolgáltatás elérése érdekében a használati utasítás tartalma megváltozhat! A készülék funkciói és tulajdonságai előzetes figyelmeztetés nélkül megváltozhatnak! Amennyiben eltérést tapasztal, keresse fel weboldalunkat a legfrissebb információkért! Kezdeti lépések Biztonsági figyelmeztetések Mindig tartsa be az alábbi előírásokat a készülék használata során. Ezzel csökkentheti tűz, áramütés és balesetveszély kockázatát. Figyelem: Áramütés elkerülése érdekében ne használja a terméket esőben vagy víz közelében. Karbantartás előtt húzza ki a készülékből a hálózati adaptert. Tartsa távol magas hőforrástól és kerülje a közvetlen napfénnyel történő érintkezést. Védje az adapter kábelét. Vezesse úgy a kábelt, hogy ne lehessen rálépni, illetve ne sértse meg rá vagy mellé helyezett más eszköz. Különösen figyeljen a kábelre a készülék csatlakozójánál. Csak a készülékhez mellékelt hálózati adaptert használja. Más adapter használata érvényteleníti a garanciát. Húzza ki az adaptert a fali aljzatból, amikor nem használja azt a készülék töltéséhez. - Tartsa a telefont és tartozékait gyermekek által nem elérhető helyen. - Tartsa távol a telefont a nedvességtől, mert az károsíthatja a készüléket. Ne használjon kémiai / vegyi anyagokat a készülék tisztításához - A készüléket csak arra felhatalmazott személy (márkaszerviz) szerelheti szét. - Beázás esetén azonnal kapcsolja ki a készüléket. Ne vegye le a hátlapot és a szárításhoz ne használjon melegítő / szárító eszközt, pl. -

Xiaomi Redmi Note 3
Xiaomi Redmi Note 3 Special Edition HASZNÁLATI ÚTMUTATÓ Ez a használati útmutató a MIUI 8 Global 6.9.8 International szoftver verziójához készült. A frissítések után egyes funkciók változhatnak! Xiaomi Redmi Note 3 Special Edition Manual HU v1.0 - 1. oldal Bevezetés Köszönjük, hogy Xiaomi terméket választott! Kérjük, használatba vétel előtt olvassa el figyelmesen ezt a használati utasítást, hogy a készüléket könnyen és egyszerűen tudja használni. A jobb szolgáltatás elérése érdekében a használati utasítás tartalma megváltozhat! A készülék funkciói és tulajdonságai előzetes figyelmeztetés nélkül megváltozhatnak! Amennyiben eltérést tapasztal, keresse fel weboldalunkat a legfrissebb információkért! Kezdeti lépések Biztonsági figyelmeztetések Mindig tartsa be az alábbi előírásokat a készülék használata során. Ezzel csökkentheti tűz, áramütés és balesetveszély kockázatát. Figyelem: Áramütés elkerülése érdekében ne használja a terméket esőben vagy víz közelében. Karbantartás előtt húzza ki a készülékből a hálózati adaptert. Tartsa távol magas hőforrástól és kerülje a közvetlen napfénnyel történő érintkezést. Védje az adapter kábelét. Vezesse úgy a kábelt, hogy ne lehessen rálépni, illetve ne sértse meg rá vagy mellé helyezett más eszköz. Különösen figyeljen a kábelre a készülék csatlakozójánál. Csak a készülékhez mellékelt hálózati adaptert használja. Más adapter használata érvényteleníti a garanciát. Húzza ki az adaptert a fali aljzatból, amikor nem használja azt a készülék töltéséhez. - Tartsa a telefont és tartozékait gyermekek által nem elérhető helyen. - Tartsa távol a telefont a nedvességtől, mert az károsíthatja a készüléket. Ne használjon kémiai / vegyi anyagokat a készülék tisztításához - A készüléket csak arra felhatalmazott személy (márkaszerviz) szerelheti szét. - Beázás esetén azonnal kapcsolja ki a készüléket. Ne vegye le a hátlapot és a szárításhoz ne használjon melegítő / szárító eszközt, pl. -
App Invisible Miui 8 Download App Invisible Miui 8 Download
app invisible miui 8 download App invisible miui 8 download. Completing the CAPTCHA proves you are a human and gives you temporary access to the web property. What can I do to prevent this in the future? If you are on a personal connection, like at home, you can run an anti-virus scan on your device to make sure it is not infected with malware. If you are at an office or shared network, you can ask the network administrator to run a scan across the network looking for misconfigured or infected devices. Another way to prevent getting this page in the future is to use Privacy Pass. You may need to download version 2.0 now from the Chrome Web Store. Cloudflare Ray ID: 67e071023c2b84ec • Your IP : 188.246.226.140 • Performance & security by Cloudflare. App invisible miui 8 download. The new Xiaomi Redmi 5A is barely any different compared to the Redmi 4A, but that isn't stopping the company from hyping its launch. We review. 10 Sep 2018 At first glance, MIUI launcher seems to have taken inspiration from iOS launcher and it still lacks an App Drawer. Also, MIUI launcher doesn't. The official Pixel Launcher has a lot of exclusive features like the Google Now panel and G Search Pill that only work while it is running as a. In MIUI 10, you'll probably spend zero seconds waiting for the app to load in most cases and go directly to the start page after tapping the icon without having to 1 Jul 2017 3 best ways to hide apps in miui 8 without root access in your xiaomi phone. -

Box Price Oppo A37 16Gb 650,000 550,000 350,000
Harga Sesuai Grade Box Brand Model Memory Price A B C D Oppo A37 16gb 650,000 550,000 350,000 200,000 50,000 Oppo A39 32gb 700,000 600,000 400,000 250,000 50,000 Oppo F1 PLUS 64gb 900,000 800,000 500,000 300,000 50,000 Oppo F1S 32gb 850,000 750,000 500,000 300,000 50,000 Oppo F1S 64gb 850,000 750,000 500,000 300,000 50,000 Oppo F3 64gb 1,050,000 850,000 550,000 350,000 100,000 Oppo F5 32gb 1,100,000 1,000,000 600,000 350,000 100,000 Oppo F5 64gb 1,100,000 1,000,000 600,000 350,000 100,000 Oppo F7 64gb 1,500,000 1,250,000 850,000 500,000 100,000 Oppo F7 128gb 1,500,000 1,250,000 850,000 500,000 100,000 Oppo F9 64gb 1,750,000 1,500,000 1,300,000 700,000 100,000 Galaxy A3 (2016) Single Samsung 16gb SIM 650,000 550,000 350,000 200,000 50,000 Samsung Galaxy A3 (2016) 16gb 650,000 550,000 350,000 200,000 50,000 Galaxy A5 (2016) Single Samsung 16gb SIM 800,000 700,000 500,000 300,000 50,000 Samsung Galaxy A5 (2016) 16gb 800,000 700,000 500,000 300,000 50,000 Samsung Galaxy A5 (2017) 32gb 1,100,000 1,000,000 600,000 400,000 100,000 Galaxy A5 (2017) Single Samsung 32gb SIM 1,100,000 1,000,000 600,000 400,000 100,000 Samsung Galaxy A6 (2018) 32gb 1,100,000 1,000,000 600,000 400,000 100,000 Samsung Galaxy A6 plus (2018) 32gb 1,500,000 1,400,000 900,000 600,000 100,000 Galaxy A7 (2016) Single Samsung 16gb Sim 950,000 850,000 550,000 300,000 50,000 Samsung Galaxy A7 (2016) 16gb 950,000 850,000 550,000 300,000 50,000 Samsung Galaxy A7 (2017) 32gb 1,200,000 1,100,000 650,000 400,000 100,000 Galaxy A7 (2017) Single Samsung 32gb SIM 1,200,000 1,100,000 -

Alcatel One Touch Go Play 7048 Alcatel One Touch
Acer Liquid Jade S Alcatel Idol 3 4,7" Alcatel Idol 3 5,5" Alcatel One Touch Go Play 7048 Alcatel One Touch Pop C3/C2 Alcatel One Touch POP C7 Alcatel Pixi 4 4” Alcatel Pixi 4 5” (5045x) Alcatel Pixi First Alcatel Pop 3 5” (5065x) Alcatel Pop 4 Lte Alcatel Pop 4 plus Alcatel Pop 4S Alcatel Pop C5 Alcatel Pop C9 Allview C6 Quad Apple Iphone 4 / 4s Apple Iphone 5 / 5s / SE Apple Iphone 5c Apple Iphone 6/6s 4,7" Apple Iphone 6 plus / 6s plus Apple Iphone 7 Apple Iphone 7 plus Apple Iphone 8 Apple Iphone 8 plus Apple Iphone X HTC 8S HTC Desire 320 HTC Desire 620 HTC Desire 626 HTC Desire 650 HTC Desire 820 HTC Desire 825 HTC 10 One M10 HTC One A9 HTC One M7 HTC One M8 HTC One M8s HTC One M9 HTC U11 Huawei Ascend G620s Huawei Ascend G730 Huawei Ascend Mate 7 Huawei Ascend P7 Huawei Ascend Y530 Huawei Ascend Y540 Huawei Ascend Y600 Huawei G8 Huawei Honor 5x Huawei Honor 7 Huawei Honor 8 Huawei Honor 9 Huawei Mate S Huawei Nexus 6p Huawei P10 Lite Huawei P8 Huawei P8 Lite Huawei P9 Huawei P9 Lite Huawei P9 Lite Mini Huawei ShotX Huawei Y3 / Y360 Huawei Y3 II Huawei Y5 / Y541 Huawei Y5 / Y560 Huawei Y5 2017 Huawei Y5 II Huawei Y550 Huawei Y6 Huawei Y6 2017 Huawei Y6 II / 5A Huawei Y6 II Compact Huawei Y6 pro Huawei Y635 Huawei Y7 2017 Lenovo Moto G4 Plus Lenovo Moto Z Lenovo Moto Z Play Lenovo Vibe C2 Lenovo Vibe K5 LG F70 LG G Pro Lite LG G2 LG G2 mini D620 LG G3 LG G3 s LG G4 LG G4c H525 / G4 mini LG G5 / H830 LG K10 / K10 Lte LG K10 2017 / K10 dual 2017 LG K3 LG K4 LG K4 2017 LG K7 LG K8 LG K8 2017 / K8 dual 2017 LG L Fino LG L5 II LG L7 LG -
Barometer of Mobile Internet Connections in Poland
Barometer of Mobile Internet Connections in Poland Publication of July 21, 2020 First half 2020 nPerf is a trademark owned by nPerf SAS, 87 rue de Sèze 69006 LYON – France. Contents 1 Summary of results ...................................................................................................................... 2 1.1 nPerf score, all technologies combined ............................................................................... 2 1.2 Our analysis ........................................................................................................................... 3 2 Overall results 2G/3G/4G ............................................................................................................. 3 2.1 Data amount and distribution ............................................................................................... 3 2.2 Success rate 2G/3G/4G ........................................................................................................ 4 2.3 Download speed 2G/3G/4G .................................................................................................. 4 2.4 Upload speed 2G/3G/4G ....................................................................................................... 5 2.5 Latency 2G/3G/4G ................................................................................................................ 5 2.6 Browsing test 2G/3G/4G....................................................................................................... 6 2.7 Streaming test 2G/3G/4G .................................................................................................... -
Redmi 3S Fastboot Driver Download DRIVER REDMI 3S FASTBOOT WINDOWS 8.1 DOWNLOAD
redmi 3s fastboot driver download DRIVER REDMI 3S FASTBOOT WINDOWS 8.1 DOWNLOAD. The moto g is an android smartphone developed and manufactured by motorola mobility, at the time a subsidiary of d on 13 november 2013, the phone was initially aimed at emerging markets, although it was also available in developed markets as a low-price option. Yeah but they kinda lost my trust there. SYNAPTICS. A few weeks ago i bought a xiaomi phone redmi note 4 running miui 8.1.6.0. The process is very easy and you can follow this step by step guide to learn how to boot the xiaomi redmi 4 into fastboot mode. This feature is not available right now. How to uninstall twrp custom rom file on 20 february. Manage your data and devices anytime, anywhere. Compare xiaomi redmi 3s prices before buying online. Having miui version 4 miui 8. By putting your phone into download mode, you can then flash either stock rom or custom rom on it. How to unbrick or fix bootloop in redmi note 3 please visit mi india. Redmi 3s battery has 4000mah rated and 4100mah typical capacity. Redmi note 3 fastboot flashing guide hindi by admin octo 38 comments. It s been several weeks since the redmi note 5 and note 5 pro were made official. You can use internet but not make calls. If u are okay with having miui but still have the craze to have a custom rom, u can go to mi community app n. Hereby states that this website is dedicated, but not related to xiaomi inc. -

Barometer of Mobile Internet Connections in Russia
Barometer of mobile Internet connections in Russia Publication of July 9th, 2021 H2 2020 & H1 2021 nPerf is a trademark owned by nPerf SAS, 87 rue de Sèze 69006 LYON – France. ussi Contents 1 Summary ...................................................................................................................................... 2 1.1 2G/3G/4G nPerf Score .......................................................................................................... 2 1.2 Our analysis ........................................................................................................................... 3 2 Overall results ............................................................................................................................... 4 2.1 Data amount and distribution ............................................................................................... 4 2.2 2G/3G/4G Success rate ........................................................................................................ 4 2.3 2G/3G/4G download speed .................................................................................................. 5 2.4 2G/3G/4G Upload speed ....................................................................................................... 6 2.5 2G/3G/4G Latency ................................................................................................................ 7 2.6 2G/3G/4G Browsing test....................................................................................................... 7 2.7 2G/3G/4G -
Xiaomi Redmi Note 3
review smartphone XIAOMI REDMI NOTE 3 A budget smartphone with best-in-class features for this category — Raj Kumar Maurya iaomi with the Make in India initiative adds another budget smartphone in their Redmi series. Redmi is the widely popular Xsmartphone series known for its affordable pricing and good specs. Redmi Note 3 is different in design from its predecessors and looks more appealing with its solid metallic body. Look and feel: The back panel of the phone is completely built with metal, sandwiched between two plastic pieces. The top plastic piece is replete with a 3.5mm headphone jack, noise cancellation and infrared (IR) emitter whereas bottom has the standard Micro- USB connector for charging and mic. The body has a smooth matte Price: `9,999 finish that doesn’t attract fingerprints. You can easily clean dust and grime off from the body with a simple wipe. The front has a 5.5-inch Full HD IPS display with narrow bezels and a glossy rim running along the edges. The IPS panel of the phone has very good color reproduction and is easily visible under direct sunlight. The top of the screen has the standard ear speaker, sensor, 5 Megapixel camera along with a notification LED for alerts. The capacitive buttons at the bottom of the screen are backlit which is different from the previous Redmi models. The volume rocker and power button are placed on the right, while the left side houses the hybrid SCORE Dual-SIM tray. The phone feels quite comfortable in hands; however, Price: 8/10 it might be a little bit tricky for small hands to use it one handed.