Master Thesis
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Echolock: Towards Low Effort Mobile User Identification
EchoLock: Towards Low Effort Mobile User Identification Yilin Yang Chen Wang Yingying Chen Rutgers University Louisiana State University Rutgers University yy450@scarletmail. [email protected] ∗ yingche@scarletmail. rutgers.edu rutgers.edu Yan Wang Binghamton University [email protected] ABSTRACT User identification plays a pivotal role in how we interact with our mobile devices. Many existing authentication ap- proaches require active input from the user or specialized sensing hardware, and studies on mobile device usage show significant interest in less inconvenient procedures. In this paper, we propose EchoLock, a low effort identification scheme that validates the user by sensing hand geometry via com- modity microphones and speakers. These acoustic signals produce distinct structure-borne sound reflections when con- tacting the user’s hand, which can be used to differentiate Figure 1: Capture of hand biometric informa- between different people based on how they hold their mo- tion embedded in structure-borne sound using bile devices. We process these reflections to derive unique commodity microphones and speakers. acoustic features in both the time and frequency domain, convenient practices [37]. Techniques such as facial recog- which can effectively represent physiological and behavioral nition or fingerprinting provide fast validation without traits, such as hand contours, finger sizes, holding strength, requiring considerable effort from the user, but demand and gesture. Furthermore, learning-based algorithms are de- dedicated hardware components that may not be avail- veloped to robustly identify the user under various environ- able on all devices. This is of particular importance in ments and conditions. We conduct extensive experiments markets of developing countries, where devices such as with 20 participants using different hardware setups in key the Huawei IDEOS must forgo multiple utilities in or- use case scenarios and study various attack models to demon- der to maintain affordable price points (e.g. -

Test Coverage Guide
TEST COVERAGE GUIDE Test Coverage Guide A Blueprint for Strategic Mobile & Web Testing SUMMER 2021 1 www.perfecto.io TEST COVERAGE GUIDE ‘WHAT SHOULD I BE TESTING RIGHT NOW?’ Our customers often come to Perfecto testing experts with a few crucial questions: What combination of devices, browsers, and operating systems should we be testing against right now? What updates should we be planning for in the future? This guide provides data to help you answer those questions. Because no single data source tells the full story, we’ve combined exclusive Perfecto data and global mobile market usage data to provide a benchmark of devices, web browsers, and user conditions to test on — so you can make strategic decisions about test coverage across mobile and web applications. CONTENTS 3 Putting Coverage Data Into Practice MOBILE RECOMMENDATIONS 6 Market Share by Country 8 Device Index by Country 18 Mobile Release Calendar WEB & OS RECOMMENDATIONS 20 Market Share by Country 21 Browser Index by Desktop OS 22 Web Release Calendar 23 About Perfecto 2 www.perfecto.io TEST COVERAGE GUIDE DATA INTO PRACTICE How can the coverage data be applied to real-world executions? Here are five considerations when assessing size, capacity, and the right platform coverage in a mobile test lab. Optimize Your Lab Configuration Balance Data & Analysis With Risk Combine data in this guide with your own Bundle in test data parameters (like number of tests, analysis and risk assessment to decide whether test duration, and required execution time). These to start testing with the Essential, Enhanced, or parameters provide the actual time a full- cycle or Extended mobile coverage buckets. -

Factory Model Device Model
Factory Model Device Model Acer A1-713 acer_aprilia Acer A1-811 mango Acer A1-830 ducati Acer A3-A10 G1EA3 Acer A3-A10 mtk6589_e_lca Acer A3-A10 zara Acer A3-A20 acer_harley Acer A3-A20FHD acer_harleyfhd Acer Acer E320-orange C6 Acer Aspire A3 V7 Acer AT390 T2 Acer B1-723 oban Acer B1-730 EverFancy D40 Acer B1-730 vespatn Acer CloudMobile S500 a9 Acer DA220HQL lenovo72_we_jb3 Acer DA222HQL N451 Acer DA222HQLA A66 Acer DA222HQLA Flare S3 Power Acer DA226HQ tianyu72_w_hz_kk Acer E330 C7 Acer E330 GT-N7105T Acer E330 STUDIO XL Acer E350 C8n Acer E350 wiko Acer G100W maya Acer G1-715 A510s Acer G1-715 e1808_v75_hjy1_5640_maxwest Acer Icona One 7 vespa Acer Iconia One 7 AT1G* Acer Iconia One 7 G1-725 Acer Iconia One 7 m72_emmc_s6_pcb22_1024_8g1g_fuyin Acer Iconia One 7 vespa2 Acer Iconia One 8 vespa8 Acer Iconia Tab 7 acer_apriliahd Acer Iconia Tab 8 ducati2fhd Acer Iconia Tab 8 ducati2hd Acer Iconia Tab 8 ducati2hd3g Acer Iconia Tab 8 Modelo II - Professor Acer Iconia Tab A100 (VanGogh) vangogh Acer Iconia Tab A200 s7503 Acer Iconia Tab A200 SM-N9006 Acer Iconia Tab A501 ELUGA_Mark Acer Iconia Tab A501 picasso Acer Iconia Tab A510 myPhone Acer Iconia Tab A510 picasso_m Acer Iconia Tab A510 ZUUM_M50 Acer Iconia Tab A701 picasso_mf Acer Iconia Tab A701 Revo_HD2 Acer Iconia TalkTab 7 acer_a1_724 Acer Iconia TalkTab 7 AG CHROME ULTRA Acer Liquid a1 Acer Liquid C1 I1 Acer Liquid C1 l3365 Acer Liquid E1 C10 Acer Liquid E2 C11 Acer Liquid E3 acer_e3 Acer Liquid E3 acer_e3n Acer Liquid E3 LS900 Acer Liquid E3 Quasar Acer Liquid E600 e600 Acer Liquid -
Micromax Remotely Installing Unwanted Apps on Devices
11/16/2016 Micromax Remotely Installing Unwanted Apps on Devices search LOGIN REGISTER plus 0 53861 Your Entries Total Entries Days Win an Android Yoga Book from XDA! January 14, 2015 50 Comments Diamondback Micromax Remotely Installing Unwanted Apps on Devices 8 Ways to Enter Login with: In the recent past, we witnessed quite a few acts of OEMs messing with devices to achieve various goals, such as increasing benchmark results. We also heard about manufacturers and carriers adding Click For a Daily tracing software to their devices, in order to collect data about how the device performs, statistics Bonus Entry about voice and data connectivity between the device and radio towers, or even battery runtime data (CarrierIQ are you listening?). Today, however, reports are coming in that users of certain devices Follow by Indian phone manufacturer Micromax noticed apps being silently installed without their consent @xdadevelopers on or permission. Twitter It appears that even uninstalling these apps won’t help, as shortly after, they will simply re-appear Tweet on Twitter again. Obviously, this is wrong on so many levels, but I’d like to point out a few key problems here Subscribe to XDA TV! anyway: Visit our sponsor (Honor) at Best Buy http://www.xdadevelopers.com/micromaxremotelyinstallingunwantedappsondevices/ 1/14 11/16/2016 Micromax Remotely Installing Unwanted Apps on Devices (Honor) at Best Buy Having no control over which apps are installed on your device poses a huge security risk, as you don’t get to -

Why Can't I Use Bluetooth to Transfer Files to Another Device? Applicable Products: Problem: 1
Why can't I use Bluetooth to transfer files to another device? Applicable products: Problem: 1. The user is unable to send files using Bluetooth. 2. The user is unable to receive files using Bluetooth. Solution: 1. The distance between your phone and the other Bluetooth device may have exceeded the maximum operational range of Bluetooth devices (10 meters). In this case, move your phone closer to the Bluetooth device, and try again. 2. The other Bluetooth device may not have responded to your file transfer request in time. You can try sending the request again and then remind the other party to confirm the transfer more quickly. 3. Your phone is not paired with the Bluetooth device. In this case, first make sure that Bluetooth is enabled on both devices, and that both devices are visible to nearby Bluetooth devices (for laptops, check that the file receiving screen is displayed). Then send the file. 4. Pair the two devices first, and then send the file. 5. Check whether the other Bluetooth device supports the file format you are trying to send. 6. If the other Bluetooth device supports the given file format, try sending the file again. Note: 1. iPhones can be paired with Huawei phones using Bluetooth, but do not support file transfer. 2. The music app preinstalled in your Huawei phone does not support Bluetooth sharing. Therefore, you cannot share music downloaded within the app with other Bluetooth devices. Open the Files app, touch Local > Internal storage > Music, find the name of the song you want to share, and touch to share it with other Bluetooth devices. -

A Critical Review on Huawei's Trusted Execution Environment
Unearthing the TrustedCore: A Critical Review on Huawei’s Trusted Execution Environment Marcel Busch, Johannes Westphal, and Tilo Müller Friedrich-Alexander-University Erlangen-Nürnberg, Germany {marcel.busch, johannes.westphal, tilo.mueller}@fau.de Abstract to error. In theory, any bug in the feature-rich domain, includ- ing severe kernel-level bugs, cannot affect the integrity and Trusted Execution Environments (TEEs) are an essential confidentiality of a TEE, as TEEs are isolated from the rest building block in the security architecture of modern mo- of the system by means of hardware primitives. As ARM is bile devices. In this paper, we review a TEE implementa- the predominant architecture used for chipsets in mobile de- tion, called TrustedCore (TC), that has been used on Huawei vices, the ARM TrustZone (TZ)[6] provides the trust anchor phones for several years. We unveil multiple severe design for virtually all TEEs in mobile devices, including Huawei and implementation flaws in the software stack of this TEE, models. which affect devices including the popular Huawei P9 Lite, Although TEEs have been extensively used by millions released in 2016, and partially the more recent Huawei P20 of products for years, security analyses targeting these sys- Lite, released in 2018. First, we reverse-engineer TC’s com- tems are rarely discussed in public since all major vendors, ponents, their interconnections, and their integration with the including Huawei, Qualcomm, and Samsung, maintain strict Android system, focusing on security aspects. Second, we ex- secrecy about their individual proprietary implementations. amine the Trusted Application (TA) loader of the TC platform However, the correct implementation of a TEE is complex and reveal multiple design flaws. -

Accelerating Development Using the Web: Empowering Poor and Marginalized Populations George Sadowsky, Ed
Accelerating Development Using the Web: Empowering Poor and Marginalized Populations George Sadowsky, ed. George Sadowsky Najeeb Al-Shorbaji Richard Duncombe Torbjörn Fredriksson Alan Greenberg Nancy Hafkin Michael Jensen Shalini Kala Barbara J. Mack Nnenna Nwakanma Daniel Pimienta Tim Unwin Cynthia Waddell Raul Zambrano Cover image: Paul Butler http://paulbutler.org/archives/visualizing-facebook-friends/ Creative Commons License Attribution-ShareAlike 3.0 This work, with the exception of Chapter 7 (Health), is licensed under the Creative Commons Attribution 3.0 Unported License. To view a copy of this license, visit http://creativecommons.org/licenses/by/3.0/ or send a letter to Creative Commons, 171 Second Street, Suite 300, San Francisco, California, 94105, USA. Chapter 7 (Health) © World Health Organization [2012]. All rights reserved. The World Health Organization has granted the Publisher permission for the reproduction of this chapter. Accelerating Development Using the Web | Foreword from the Rockefeller Foundation i Foreword from the Rockefeller Foundation For almost 100 years, the Rockefeller Foundation has been at the forefront of new ideas and innovations related to emerging areas of technology. In its early years, the Foundation advanced new technologies to eradicate hookworm and develop a vaccine for yellow fever, creating a lasting legacy of strengthening the application of new technologies to improve the lives of the world’s poor and vulnerable. By the middle of the 20th century, this approach led the Foundation to the pre-cursor to the modern day comput- er. At the dawn of the digital era in 1956, the Foundation helped launch the field of artificial intelligence through its support for the work of John McCarthy, the computing visionary who coined the term. -

HR Kompatibilitätsübersicht
HR-imotion Kompatibilität/Compatibility 2018 / 11 Gerätetyp Telefon 22410001 23010201 22110001 23010001 23010101 22010401 22010501 22010301 22010201 22110101 22010701 22011101 22010101 22210101 22210001 23510101 23010501 23010601 23010701 23510320 22610001 23510420 Smartphone Acer Liquid Zest Plus Smartphone AEG Voxtel M250 Smartphone Alcatel 1X Smartphone Alcatel 3 Smartphone Alcatel 3C Smartphone Alcatel 3V Smartphone Alcatel 3X Smartphone Alcatel 5 Smartphone Alcatel 5v Smartphone Alcatel 7 Smartphone Alcatel A3 Smartphone Alcatel A3 XL Smartphone Alcatel A5 LED Smartphone Alcatel Idol 4S Smartphone Alcatel U5 Smartphone Allview P8 Pro Smartphone Allview Soul X5 Pro Smartphone Allview V3 Viper Smartphone Allview X3 Soul Smartphone Allview X5 Soul Smartphone Apple iPhone Smartphone Apple iPhone 3G / 3GS Smartphone Apple iPhone 4 / 4S Smartphone Apple iPhone 5 / 5S Smartphone Apple iPhone 5C Smartphone Apple iPhone 6 / 6S Smartphone Apple iPhone 6 Plus / 6S Plus Smartphone Apple iPhone 7 Smartphone Apple iPhone 7 Plus Smartphone Apple iPhone 8 Smartphone Apple iPhone 8 Plus Smartphone Apple iPhone SE Smartphone Apple iPhone X Smartphone Apple iPhone XR Smartphone Apple iPhone Xs Smartphone Apple iPhone Xs Max Smartphone Archos 50 Saphir Smartphone Archos Diamond 2 Plus Smartphone Archos Saphir 50x Smartphone Asus ROG Phone Smartphone Asus ZenFone 3 Smartphone Asus ZenFone 3 Deluxe Smartphone Asus ZenFone 3 Zoom Smartphone Asus Zenfone 5 Lite ZC600KL Smartphone Asus Zenfone 5 ZE620KL Smartphone Asus Zenfone 5z ZS620KL Smartphone Asus -

Android용 Cisco Jabber 12.8 릴리스 노트
Android용 Cisco Jabber 12.8 릴리스 노트 초판: 2020년 1월 22일 릴리스 12.8의 새로운 기능 Android 10 지원 Android 10에 대한 지원을 추가했습니다. Android 장치의 얼굴 인식 지원 이제 얼굴 인식 기능을 사용하여 적절한 Android 장치를 인증할 수 있습니다. 이전 릴리스에서는 사용자가 Android 장치에서 지문을 통해 인증할 수 있었습니다. LocalAuthenticationWithBiometrics 매개 변수를 사용하여 이 기능을 비활성화할 수 있습니다. 이 기능 에 대한 자세한 내용은 Cisco Jabber의 기능 구성에서 생체 인식 인증에 대한 섹션을 참조하십시오. 헌트 그룹 기능 향상 이제 모바일 클라이언트에서 헌트 그룹에 로그인하거나 로그아웃할 수 있습니다. 자세한 내용은 Cisco Jabber 기능 구성의 헌트 그룹 섹션을 참조하십시오. 음성 메일 기능 향상 데스크톱 클라이언트에서 모바일 클라이언트로 릴리스 12.7 음성 메일 기능 향상을 확장했습니다. 사용자는 통화를 하지 않고 음성 메일을 생성하여 하나 이상의 연락처에 음성 메일을 보낼 수 있습니 다. 음성 메일 서버 관리자는 사용자가 음성 메일을 전송할 수 있는 메일 그룹을 만들 수도 있습니다. 사용자는 음성 메일 서버의 카탈로그에서 수신자를 선택할 수 있습니다. 사용자는 음성 메일 또는 해당 메시지의 모든 수신자에게 직접 응답할 수 있습니다. 사용자는 음성 메일을 새 수신자에게 전달할 수도 있습니다. Android 장치에서 강제 업그레이드 관리자는 Google Play에서 ForceUpgradingOnMobile 매개 변수를 사용하여 최신 버전으로 업그레이드 를 시행할 수 있습니다. 팀 메시징 모드에 대한 사용자 정의 연락처 Jabber Team 메시징 모드 배포는 사용자 정의 연락처를 지원합니다. 이제 데스크톱 클라이언트에서 사용자 정의 연락처를 만들고 편집 및 삭제할 수 있습니다. 이 연락처는 모바일 클라이언트에서도 사 Android용 Cisco Jabber 12.8 릴리스 노트 1 요구 사항 용할 수 있습니다. 그러나 모바일 클라이언트에서 사용자 정의 연락처를 만들거나 편집 또는 삭제할 수는 없습니다. Webex 제어 허브를 통한 Jabber 분석 배포에 Webex 제어 허브가 구성되어 있는 경우 제어 허브를 통해 Jabber 분석에 액세스할 수 있습니 다. -
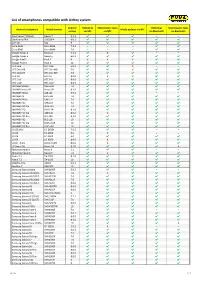
List of Smartphones Compatible with Airkey System
List of smartphones compatible with AirKey system Android Unlocking Maintenance tasks Unlocking Maintenance tasks Android smartphone Model number Media updates via NFC version via NFC via NFC via Bluetooth via Bluetooth Asus Nexus 7 (Tablet) Nexus 7 5.1.1 ✔ ✔ ✔ – – Blackberry PRIV STV100-4 6.0.1 ✔ ✔ ✔ ✔ ✔ CAT S61 S61 9 ✔ ✔ ✔ ✔ ✔ Doro 8035 Doro 8035 7.1.2 – – – ✔ ✔ Doro 8040 Doro 8040 7.0 – – – ✔ ✔ Google Nexus 4 Nexus 4 5.1.1 ✔ X ✔ – – Google Nexus 5 Nexus 5 6.0.1 ✔ ✔ ✔ ✔ ✔ Google Pixel 2 Pixel 2 9 X X X ✔ ✔ Google Pixel 4 Pixel 4 10 ✔ ✔ ✔ ✔ ✔ HTC One HTC One 5.0.2 ✔ ✔ X – – HTC One M8 HTC One M8 6.0 ✔ ✔ X ✔ ✔ HTC One M9 HTC One M9 7.0 ✔ ✔ ✔ ✔ ✔ HTC 10 HTC 10 8.0.0 ✔ X X ✔ ✔ HTC U11 HTC U11 8.0.0 ✔ ✔ ✔ ✔ ✔ HTC U12+ HTC U12+ 8.0.0 ✔ ✔ ✔ ✔ ✔ HUAWEI Mate 9 MHA-L09 7.0 ✔ ✔ ✔ ✔ ✔ HUAWEI Nexus 6P Nexus 6P 8.1.0 ✔ ✔ ✔ ✔ ✔ HUAWEI P8 lite ALE-L21 5.0.1 ✔ ✔ ✔ – – HUAWEI P9 EVA-L09 7.0 ✔ ✔ ✔ ✔ ✔ HUAWEI P9 lite VNS-L21 7.0 ✔ ✔ ✔ ✔ ✔ HUAWEI P10 VTR-L09 7.0 ✔ ✔ ✔ ✔ ✔ HUAWEI P10 lite WAS-LX1 7.0 ✔ ✔ ✔ ✔ ✔ HUAWEI P20 EML-L29 8.1.0 ✔ ✔ ✔ ✔ ✔ HUAWEI P20 lite ANE-LX1 8.0.0 ✔ X ✔ ✔ ✔ HUAWEI P20 Pro CLT-L29 8.1.0 ✔ ✔ ✔ ✔ ✔ HUAWEI P30 ELE-L29 10 ✔ ✔ ✔ ✔ ✔ HUAWEI P30 lite MAR-LX1A 10 ✔ ✔ ✔ ✔ ✔ HUAWEI P30 Pro VOG-L29 10 ✔ ✔ ✔ ✔ ✔ LG G2 Mini LG-D620r 5.0.2 ✔ ✔ ✔ – – LG G3 LG-D855 5.0 ✔ X ✔ – – LG G4 LG-H815 6.0 ✔ ✔ ✔ ✔ ✔ LG G6 LG-H870 8.0.0 ✔ X ✔ ✔ ✔ LG G7 ThinQ LM-G710EM 8.0.0 ✔ X ✔ ✔ ✔ LG Nexus 5X Nexus 5X 8.1.0 ✔ ✔ ✔ ✔ X Motorola Moto X Moto X 5.1 ✔ ✔ ✔ – – Motorola Nexus 6 Nexus 6 7.0 ✔ X ✔ ✔ ✔ Nokia 7.1 TA-1095 8.1.0 ✔ ✔ X ✔ ✔ Nokia 7.2 TA-1196 10 ✔ ✔ ✔ -

How to Prevent Android Os from Closing a Background App
MAKING LIFE WONDERFUL HOW TO PREVENT ANDROID OS FROM CLOSING A BACKGROUND APP Consult this guide to understand how to easily set your Android Smartphone to prevent it from closing background apps. © 2020 VYVO™ MAKING LIFE WONDERFUL INTRO Smartphones are getting more and more powerful, but the battery capacity is lagging behind. Vendors are always trying to squeeze some battery-saving features into the firmware with each new Android release. The smartphones are unable to do some tasks for you in the background unless you actively use your device at the time. This affects most of the apps, which are not just another browser window. Most affected are alarm clocks, health trackers, automation apps, or simply anything which needs to do some job for you at a particular moment when you don’t use your phone. Google has already taken care of limiting background services and optimizing battery usage with Doze mode. But many OEMs have again added multiple layers of meaningless restrictions in the name of squeezing extra battery life. These limitations are enabled by default for every app you download, making the setup more complicated to prevent Android OS from closing a background app. As you know, some services associated with our VYVO wearable devices require an active connection to the smartphone. For example, to be able to send alerts and SOS messages, your VYVO watch needs to be connected to your smartphone (via Bluetooth) and with the App active. For this reason, you need to avoid stopping the App from running through background operations. As well as when the phone is on standby, the App must be active in the background. -

Smartphone Camera Modules Comparison 2020 Vol 3: Focus on Huawei
REVERSE COSTING® – STRUCTURAL, PROCESS & COST REPORT P9 P10 P20 Pro Mate 20 Pro P30 Pro Mate 30 Pro P40 Pro Smartphone Camera Modules Comparison 2020 Vol. 3 Focus on Huawei SP20525 - IMAGING report by Audrey LAHRACH Physical Analysis by Véronique LE TROADEC & Guillaume CHEVALIER December 2020 – Sample 22 bd Benoni Goullin 44200 NANTES - FRANCE +33 2 40 18 09 16 [email protected] www.systemplus.fr ©2020 by System Plus Consulting | SP20525 – Smartphone Camera Module Comparison 2020 Vol 3: Focus on Huawei | Sample 1 Table of Contents Cost Comparison 96 Overview / Introduction 5 o CIS Die Cost Comparison o Executive Summary o Reverse Costing Methodology o Front Facing o Glossary o Rear Facing Company Profile & Supply Chain 9 o Total CIS Die Price o Huawei, Sony, Omnivision o CM Cost Comparison o Players & Market Forecast Physical Comparison 19 o Front Facing o Camera Module Overview o Rear Facing o Summary of the Physical Analysis o Total CM Price o Huawei P40 Pro Detailed Physical Analysis 122 o Huawei P30 Pro ➢ P Series o Huawei P20 Pro o P40 Pro ✓ Front & Rear Camera o Huawei P10 o P30 Pro o Huawei P9 ✓ Front & Rear Camera o Mate 30 Pro o P20 Pro o Mate 20 Pro ✓ Front & Rear Camera Physical Evolution 55 o P10 o Display Evolution ✓ Front & Rear Camera o Huawei Front Camera Evolution P Series o P9 o Huawei Rear Camera Evolution P Series ✓ Front & Rear Camera o Huawei Front Camera Evolution/Comparison Mate vs P Series ➢ Mate Series o Huawei Rear Camera Evolution/Comparison Mate vs P Series o Mate 30 Pro o Camera Module Description ✓ Front & Rear Camera o Bonding & Stacking evolution (Sony & Omnivision) o Mate 20 Pro ✓ Front & Rear Camera Feedbacks 240 SystemPlus Consulting services 242 ©2020 by System Plus Consulting | SP20525 – Smartphone Camera Module Comparison 2020 Vol 3: Focus on Huawei | Sample 2 Executive Summary Overview / Introduction o Executive Summary o Reverse Costing Huawei is among the top 3 smartphone OEMs today.