A Study and Implementation of RSA Cryptosystem ∗
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

By Sieving, Primality Testing, Legendre's Formula and Meissel's
Computation of π(n) by Sieving, Primality Testing, Legendre’s Formula and Meissel’s Formula Jason Eisner, Spring 1993 This was one of several optional small computational projects assigned to undergraduate mathematics students at Cambridge University in 1993. I’m releasing my code and writeup in 2002 in case they are helpful to anyone—someone doing research in this area wrote to me asking for them. My linear-time version of the Sieve of Eratosthenes may be original; I have not seen that algorithm anywhere else. But the rest of this work is straightforward implementation and exposition of well-known methods. A good reference is H. Riesel, Prime Numbers and Computer Methods for Factorization. My Common Lisp implementation is in the file primes.lisp. The standard language reference (now available online for free) is Guy L. Steele, Jr., Common Lisp: The Language, 2nd ed., Digital Press, 1990. Note: In my discussion of running time, I have adopted the usual ideal- ization of a machine that can perform addition and multiplication operations in constant time. Real computers obviously fall short of this ideal; for exam- ple, when n and m are represented in base 2 by arbitrary length bitstrings, it takes time O(log n log m) to compute nm. Introduction: In this project we’ll look at several approaches for find- ing π(n), the numberof primes less than n. Each approach has its advan- tages. • Sieving produces a complete list of primes that can be further analyzed. For instance, after sieving, we may easily identify the 8169 pairs of twin primes below 106. -

Primes and Primality Testing
Primes and Primality Testing A Technological/Historical Perspective Jennifer Ellis Department of Mathematics and Computer Science What is a prime number? A number p greater than one is prime if and only if the only divisors of p are 1 and p. Examples: 2, 3, 5, and 7 A few larger examples: 71887 524287 65537 2127 1 Primality Testing: Origins Eratosthenes: Developed “sieve” method 276-194 B.C. Nicknamed Beta – “second place” in many different academic disciplines Also made contributions to www-history.mcs.st- geometry, approximation of andrews.ac.uk/PictDisplay/Eratosthenes.html the Earth’s circumference Sieve of Eratosthenes 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 96 97 98 99 100 Sieve of Eratosthenes We only need to “sieve” the multiples of numbers less than 10. Why? (10)(10)=100 (p)(q)<=100 Consider pq where p>10. Then for pq <=100, q must be less than 10. By sieving all the multiples of numbers less than 10 (here, multiples of q), we have removed all composite numbers less than 100. -

Primality Testing for Beginners
STUDENT MATHEMATICAL LIBRARY Volume 70 Primality Testing for Beginners Lasse Rempe-Gillen Rebecca Waldecker http://dx.doi.org/10.1090/stml/070 Primality Testing for Beginners STUDENT MATHEMATICAL LIBRARY Volume 70 Primality Testing for Beginners Lasse Rempe-Gillen Rebecca Waldecker American Mathematical Society Providence, Rhode Island Editorial Board Satyan L. Devadoss John Stillwell Gerald B. Folland (Chair) Serge Tabachnikov The cover illustration is a variant of the Sieve of Eratosthenes (Sec- tion 1.5), showing the integers from 1 to 2704 colored by the number of their prime factors, including repeats. The illustration was created us- ing MATLAB. The back cover shows a phase plot of the Riemann zeta function (see Appendix A), which appears courtesy of Elias Wegert (www.visual.wegert.com). 2010 Mathematics Subject Classification. Primary 11-01, 11-02, 11Axx, 11Y11, 11Y16. For additional information and updates on this book, visit www.ams.org/bookpages/stml-70 Library of Congress Cataloging-in-Publication Data Rempe-Gillen, Lasse, 1978– author. [Primzahltests f¨ur Einsteiger. English] Primality testing for beginners / Lasse Rempe-Gillen, Rebecca Waldecker. pages cm. — (Student mathematical library ; volume 70) Translation of: Primzahltests f¨ur Einsteiger : Zahlentheorie - Algorithmik - Kryptographie. Includes bibliographical references and index. ISBN 978-0-8218-9883-3 (alk. paper) 1. Number theory. I. Waldecker, Rebecca, 1979– author. II. Title. QA241.R45813 2014 512.72—dc23 2013032423 Copying and reprinting. Individual readers of this publication, and nonprofit libraries acting for them, are permitted to make fair use of the material, such as to copy a chapter for use in teaching or research. Permission is granted to quote brief passages from this publication in reviews, provided the customary acknowledgment of the source is given. -

The Pollard's Rho Method for Factoring Numbers
Foote 1 Corey Foote Dr. Thomas Kent Honors Number Theory Date: 11-30-11 The Pollard’s Rho Method for Factoring Numbers We are all familiar with the concepts of prime and composite numbers. We also know that a number is either prime or a product of primes. The Fundamental Theorem of Arithmetic states that every integer n ≥ 2 is either a prime or a product of primes, and the product is unique apart from the order in which the factors appear (Long, 55). The number 7, for example, is a prime number. It has only two factors, itself and 1. On the other hand 24 has a prime factorization of 2 3 × 3. Because its factors are not just 24 and 1, 24 is considered a composite number. The numbers 7 and 24 are easier to factor than larger numbers. We will look at the Sieve of Eratosthenes, an efficient factoring method for dealing with smaller numbers, followed by Pollard’s rho, a method that allows us how to factor large numbers into their primes. The Sieve of Eratosthenes allows us to find the prime numbers up to and including a particular number, n. First, we find the prime numbers that are less than or equal to √͢. Then we use these primes to see which of the numbers √͢ ≤ n - k, ..., n - 2, n - 1 ≤ n these primes properly divide. The remaining numbers are the prime numbers that are greater than √͢ and less than or equal to n. This method works because these prime numbers clearly cannot have any prime factor less than or equal to √͢, as the number would then be composite. -

The I/O Complexity of Computing Prime Tables 1 Introduction
The I/O Complexity of Computing Prime Tables Michael A. Bender1, Rezaul Chowdhury1, Alex Conway2, Mart´ın Farach-Colton2, Pramod Ganapathi1, Rob Johnson1, Samuel McCauley1, Bertrand Simon3, and Shikha Singh1 1 Stony Brook University, Stony Brook, NY 11794-2424, USA. fbender,rezaul,pganapathi,rob,smccauley,shiksinghg @cs.stonybrook.edu 2 Rutgers University, Piscataway, NJ 08854, USA. ffarach,[email protected] 3 LIP, ENS de Lyon, 46 allee´ d’Italie, Lyon, France. [email protected] Abstract. We revisit classical sieves for computing primes and analyze their performance in the external-memory model. Most prior sieves are analyzed in the RAM model, where the focus is on minimizing both the total number of operations and the size of the working set. The hope is that if the working set fits in RAM, then the sieve will have good I/O performance, though such an outcome is by no means guaranteed by a small working-set size. We analyze our algorithms directly in terms of I/Os and operations. In the external- memory model, permutation can be the most expensive aspect of sieving, in contrast to the RAM model, where permutations are trivial. We show how to implement classical sieves so that they have both good I/O performance and good RAM performance, even when the problem size N becomes huge—even superpolynomially larger than RAM. Towards this goal, we give two I/O-efficient priority queues that are optimized for the operations incurred by these sieves. Keywords: External-Memory Algorithms, Prime Tables, Sorting, Priority Queues 1 Introduction According to Fox News [21], “Prime numbers, which are divisible only by themselves and one, have little mathematical importance. -
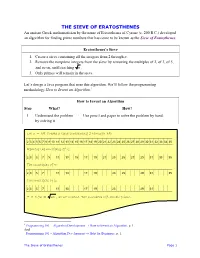
THE SIEVE of ERATOSTHENES an Ancient Greek Mathematician by the Name of Eratosthenes of Cyrene (C
THE SIEVE OF ERATOSTHENES An ancient Greek mathematician by the name of Eratosthenes of Cyrene (c. 200 B.C.) developed an algorithm for finding prime numbers that has come to be known as the Sieve of Eratosthenes. Eratosthenes’s Sieve 1. Create a sieve containing all the integers from 2 through n. 2. Remove the nonprime integers from the sieve by removing the multiples of 2, of 3, of 5, and so on, until reaching n . 3. Only primes will remain in the sieve. Let’s design a Java program that uses this algorithm. We’ll follow the programming methodology How to Invent an Algorithm.1 How to Invent an Algorithm Step What? How? 1 Understand the problem Use pencil and paper to solve the problem by hand. by solving it Let n = 35. Create a sieve containing 2 through 35: 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 Remove the multiples of 2: 2 3 5 7 9 11 13 15 17 19 21 23 25 27 29 31 33 35 The multiples of 3: 2 3 5 7 11 13 17 19 23 25 29 31 35 The multiples of 5: 2 3 5 7 11 13 17 19 23 29 31 7 > 5.92 = 35 , so we’re done. The numbers left are all prime. 1 Programming 101 ‒ Algorithm Development → How to Invent an Algorithm, p. 1. And Programming 101 ‒ Algorithm Development → Help for Beginners, p. -

Prime Number Sieves Utrecht University
Prime number sieves Utrecht University Guido Reitsma Supervisor: Lasse Grimmelt January 17th 2020 Acknowledgements First I want to thank Lasse for being a great supervisor, especially given that it was his first bachelor's thesis that he supervised and I'm definitely not the easiest person. Secondly I want to thank all my friends, family and other people, who supported me and listened to my thoughts for the last three months and before. 2 Contents 1 Introduction 4 1.1 Sieve of Eratosthenes Historically . .4 1.2 The way many people know the Sieve of Eratosthenes . .4 1.3 Estimating primes via Eratosthenes' Sieve . .5 1.4 RSA . .8 2 Combinatorial Sieve 10 2.1 Notation . 10 2.2 Sieve weights . 10 2.3 Buchstab's Identity . 11 2.4 Brun's sieve . 12 3 The General Number Field Sieve 14 3.1 Difference of Squares Factorization method . 14 3.2 Free parameters in GNFS . 14 3.3 Z[θ]........................................ 15 3.4 Finding two squares . 15 3.5 Smoothness over a factor base . 16 3.6 Verifying squares in Z and Z[θ]......................... 17 3.7 Combine everything . 18 4 Discussion and Conclusion 20 4.1 How to go further with sieves . 20 4.2 Number of calculations using GNFS . 21 4.3 Is RSA really safe? . 21 4.4 Conclusion . 21 3 Chapter 1 Introduction In this thesis there are two applications from the Sieve of Eratosthenes The two sieves that are mentioned in this thesis are the combinatorial sieve and the General Number field Sieve. We will then compare both of the methods which each other and look how these methods coincide or differ. -

MATH 453 Primality Testing We Have Seen a Few Primality Tests in Previous Chapters: Sieve of Eratosthenes (Trivial Divi- Sion), Wilson’S Test, and Fermat’S Test
MATH 453 Primality Testing We have seen a few primality tests in previous chapters: Sieve of Eratosthenes (Trivial divi- sion), Wilson's Test, and Fermat's Test. • Sieve of Eratosthenes (or Trivial division) Let n 2 N with n > 1. p If n is not divisible by any integer d p≤ n, then n is prime. If n is divisible by some integer d ≤ n, then n is composite. • Wilson Test Let n 2 N with n > 1. If (n − 1)! 6≡ −1 mod n, then n is composite. If (n − 1)! ≡ −1 mod n, then n is prime. • Fermat Test Let n 2 N and a 2 Z with n > 1 and (a; n) = 1: If an−1 6≡ 1 mod n; then n is composite. If an−1 ≡ 1 mod n; then the test is inconclusive. Remark 1. Using the same assumption as above, if n is composite and an−1 ≡ 1 mod n, then n is said to be a pseudoprime to base a. If n is a pseudoprime to base a for all a 2 Z such that (a; n) = 1, then n is called a Carmichael num- ber. It is known that there are infinitely Carmichael numbers (hence infinitely many pseudoprimes to any base a). However, pseudoprimes are generally very rare. For example, among the first 1010 positive integers, 14; 882 integers (≈ 0:00015%) are pseudoprimes (to base 2), compared with 455; 052; 511 primes (≈ 4:55%) In reality, thep primality tests listed above are computationally inefficient. For instance, it takes up to n divisions to determine whether n is prime using the Trivial Division method. -

Of 9 Math 3336 Section 4.3 Primes and Greatest Common Divisors
Math 3336 Section 4.3 Primes and Greatest Common Divisors • Prime Numbers and their Properties • Greatest Common Divisors and • Conjectures and Open Problems Least Common Multiples About Primes • The Euclidian Algorithm • gcds as Linear Combinations Definition: A positive integer greater than 1 is called prime if the only positive factors of are 1 and . A positive integer that is greater than 1 and is not prime is called composite. Example: The integer 11 is prime because its only positive factors are 1 and 11, but 12 is composite because it is divisible by 3, 4, and 6. The Fundamental Theorem of Arithmetic: Every positive integer greater than 1 can be written uniquely as a prime or as the product of two or more primes where the prime factors are written in order of nondecreasing size. Examples: a. 50 = 2 5 b. 121 = 11 2 c. 256 = 2⋅ 2 8 Theorem: If is a composite integer, then has a prime divisor less than or equal to . Proof: √ Page 1 of 9 Example: Show that 97 is prime. Example: Find the prime factorization of each of these integers a. 143 b. 81 Theorem: There are infinitely many primes. Proof: Page 2 of 9 Questions: 1. The proof of the previous theorem by A. Contrapositive C. Direct B. Contradiction 2. Is the proof constructive OR nonconstructive? 3. Have we shown that Q is prime? The Sieve of Eratosthenes can be used to find all primes not exceeding a specified positive integer. For example, begin with the list of integers between 1 and 100. -

Parallel Prime Sieve: Finding Prime Numbers
Parallel Prime Sieve: Finding Prime Numbers David J. Wirian Institute of Information & Mathematical Sciences Massey University at Albany, Auckland, New Zealand [email protected] ABSTRACT Before the 19 th of century, there was not much use of prime numbers. However in the 19 th of century, the people used prime numbers to secure the messages and data during times of war. This research paper is to study how we find a large prime number using some prime sieve techniques using parallel computation, and compare the techniques by finding the results and the implications. INTRODUCTION The use of prime numbers is becoming more important in the 19 th of century due to their role in data encryption/decryption by public keys with such as RSA algorithm. This is why finding a prime number becomes an important part in the computer world. In mathematics, there are loads of theories on prime, but the cost of computation of big prime numbers is huge. The size of prime numbers used dictate how secure the encryption will be. For example, 5 digits in length (40-bit encryption) yields about 1.1 trillion possible results; 7 digits in length (56-bit encryption) will result about 72 quadrillion possible results [11]. This results show that cracking the encryption with the traditional method will take very long time. It was found that using two prime numbers multiplied together makes a much better key than any old number because it has only four factors; one, itself, and the two prime that it is a product of. This makes the code much harder to crack. -
Primality Testing : a Review
Primality Testing : A Review Debdas Paul April 26, 2012 Abstract Primality testing was one of the greatest computational challenges for the the- oretical computer scientists and mathematicians until 2004 when Agrawal, Kayal and Saxena have proved that the problem belongs to complexity class P . This famous algorithm is named after the above three authors and now called The AKS Primality Testing having run time complexity O~(log10:5(n)). Further improvement has been done by Carl Pomerance and H. W. Lenstra Jr. by showing a variant of AKS primality test has running time O~(log7:5(n)). In this review, we discuss the gradual improvements in primality testing methods which lead to the breakthrough. We also discuss further improvements by Pomerance and Lenstra. 1 Introduction \The problem of distinguishing prime numbers from a composite numbers and of resolving the latter into their prime factors is known to be one of the most important and useful in arithmetic. It has engaged the industry and wisdom of ancient and modern geometers to such and extent that its would be superfluous to discuss the problem at length . Further, the dignity of the science itself seems to require that every possible means be explored for the solution of a problem so elegant and so celebrated." - Johann Carl Friedrich Gauss, 1781 A number is a mathematical object which is used to count and measure any quantifiable object. The numbers which are developed to quantify natural objects are called Nat- ural Numbers. For example, 1; 2; 3; 4;::: . Further, we can partition the set of natural 1 numbers into three disjoint sets : f1g, set of fprime numbersg and set of fcomposite numbersg. -

The Sieve of Eratosthenes
Chapter 3 The Sieve of Eratosthenes An algorithm for finding prime numbers Mathematicians who work in the field of number theory are interested in how numbers are related to one another. One of the key ideas in this area is how an integer can be expressed as the product of other integers. If an integer can only be written in product form as the product of 1 and the number itself it is called a prime number. Other numbers, known as composite numbers, are the product of two or more factors, for example, 15 = 3 5 and ⇥ 12 = 2 2 3. ⇥ ⇥ Ancient mathematicians devoted considerable attention to the subject. Over 2,000 years ago Euclid investigated several relationships among prime numbers, among other things proving there are an infinite number of primes. For most of their history, prime numbers were only of theoretical interest, but today they are at the heart of a variety of important computer applications. The security of messages transmitted using public key cryptography, the most widely used method for transferring sensitive information on the Internet, relies heavily on properties of prime numbers that were discovered thousands of years ago. One of the fascinating things about prime numbers is the fact that there is no regular pattern to help predict which numbers will be prime. The number 839 is prime, and the next higher prime is 853, a distance of 14 numbers. But the next prime right after that is 857, only 4 numbers away. In some cases they appear in pairs, such as 881 and 883, where the difference between successive primes is only 2.