Android Security and the Elusive HSM
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

ABSTRAK Kota Manadoadalahkotaekowisata Yang Memilikipotensiwisata Yang Bervariasi, Mulaidariwisatabudayasampaidenganwisatabahari
ABSTRAK Kota manadoadalahkotaekowisata yang memilikipotensiwisata yang bervariasi, mulaidariwisatabudayasampaidenganwisatabahari. Akan tetapikurangnyainformasi yang adatentangwisatakulinersehinggakuliner yang adadikotamanadokurangbegituterkenalolehbanyakparawisatawandanmasyarakatluas yang berliburdikotamanado. Untukitutentunya, Pengelolaaninformasidandukunganpromosi yang tepatakansangatmembantupeningkatanusaha di bidangkulinerini.Denganteknologiinformasi yang begituberkembangsehinggakotamanadoperluuntukmemilikisisteminformasitentangwis atakuliner yang dapatdiaksesolehwisatawandanmasyarakatluas. Adapuntujuanpembuatansisteminformasiinidapatmempermudahparawisatawa ndanmasyarakatuntukmenemukantempatkuliner yang adadimanadodandapatmempermudahsampaiketempattujuandenganrute yang cepat. Metode yang digunakanmerancangsisteminiadalahmetode System Development Life Cycle (SDLC).Metodeinimemilikibeberapa 6 tahapyaitu, planning, analisis, desain, coding and testing, implementation dan maintenance. Hasildaripembuatansisteminformasiwisatakulineriniadalahuntukmengetahuii nformasitentangkuliner yang adadikotamanado. Mempermudahjugaparawisatawandanmasyarakat agar dapatmencaritempatkuliner yang merekainginkandenganmengunakan android. Kata kunci: Android, Android Studi, GIS, Google Maps. i KATA PENGANTAR Pujidansyukurpenulispanjatkankehadirat Allah Yang MahaEsa, karenaatasrahmatdankarunia- NyasehinggapenulisdapatmenyelesaikanpenyusunanTugasAkhirinidenganjudul“APL IKASI SISTEM INFORMASI GEOGRAFIS WISATA KULINER KOTA MANADO BERBASIS ANDROID” Adapuntujuandaripenulisantugasakhiriniyaitusebagaisalahsatusyaratuntukmen -

Slingtv Fire TV Stick TV Nexus Player Mini Nexus Player TV TV M6 HD Personal Video Recorder 2 M2 Chromecast 3 BV-3100 the Playti
HOME ENTERTAINMENT GAMING CONSOLES AND ACCESSORIES TV Chromecast Fire TV Stick 4th Generation HDMI USB TV Stick Streaming Media Player Wirelessly Stream Multimedia Content Wirelessly Stream Content Stream Movies, Music, TV, Games, & More Built-In Wi-Fi & Ethernet Connectivity 1080p Maximum Resolution Up to 1080p Resolution Support via HDMI Apple AirPlay & iCloud Integration Built-In 802.11b/g/n Wi-Fi Smartphone & Tablet Mirroring Support Supports Up to 1080p via HDMI Integrated HDMI Connector 1GB of RAM + 8GB of Flash Storage Rechargeable Siri Remote Control Control from Portable Devices Fire TV Remote App with Voice Search A8 Processor with 64-bit Architecture USB Port or AC Powered Dedicated Bluetooth Remote Control Siri Search/Multidirectional Navigation Compact Design Dual-Band Wi-Fi Connectivity 32GB APTV32 ................................................................................149.00 Compact Design at 3.3” Long 64GB APTV64 ................................................................................199.00 GOCC ................................................................................................ 34.95 AMFTVS ............................................................................................ 39.99 TV 3 TV Media Player Streaming Media Player Streaming Stick Up to 1080p Resolution Over 2,000 Entertainment Channels Stream Over 1000 Entertainment Channels Dual USB 2.0 Inputs Dual-Band Wi-Fi & Ethernet Connectivity Dual-Band 802.11a/b/g/n Wi-Fi Access Streaming Services Outputs -
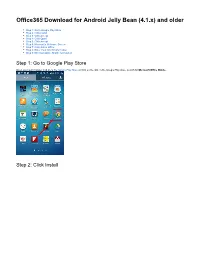
Download for Android Jelly Bean (4.1.X) and Older
Office365 Download for Android Jelly Bean (4.1.x) and older Step 1: Go to Google Play Store Step 2: Click Install Step 3: Click Accept Step 4: Click Open Step 5: Click Accept Step 6: Microsoft's Welcome Screen Step 7: Click Active Office Step 8: Enter Your UCCS Information Step 9: Microsoft Office Mobile is Installed Step 1: Go to Google Play Store Open your web browser and go to the Google Play Store or click on the link. In the Google Play store, search for Microsoft Office Mobile. Step 2: Click Install You may be prompted to open in either the Google Play App or in your Web browser. Choose either option, the following steps will be the same. Click on the green install button. Please Note: You will need a google account for this download to work. Step 3: Click Accept An app permission screen will appear, click Accept. Step 4: Click Open When the installation is complete, the Google Play page or web page install button will have been replaced by Open and Uninstall buttons. Click Open. Step 5: Click Accept Click Accept to agree to Microsoft's Use Terms. Step 6: Microsoft's Welcome Screen When Office opens for the first time a welcome screen and general information about Microsoft's cloud service will appear. You can get through these screens with the arrow button located in the bottom right corner. Step 7: Click Active Office Click Activate Office. Step 8: Enter Your UCCS Information Enter your UCCS Email into the Email field and then your UCCS Password into the Password field. -

Software Development Methodologies on Android Application Using Example
View metadata, citation and similar papers at core.ac.uk brought to you by CORE provided by VUS Repository POLYTECHNIC OF ŠIBENIK DEPARTMENT OF MANAGEMENT SPECIALIST STUDY OF MANAGEMENT Ivan Bumbak SOFTWARE DEVELOPMENT METHODOLOGIES ON ANDROID APPLICATION USING EXAMPLE Graduate thesis Šibenik, 2018. POLYTECHNIC OF ŠIBENIK DEPARTMENT OF MANAGEMENT SPECIALIST STUDY OF MANAGEMENT SOFTWARE DEVELOPMENT METHODOLOGIES ON ANDROID APPLICATION USING EXAMPLE Graduate thesis Course: Software engineering Mentor: PhD Frane Urem, college professor Student: Ivan Bumbak Student ID number: 0023096262 Šibenik, September 2018. TEMELJNA DOKUMENTACIJSKA KARTICA Veleučilište u Šibeniku Diplomski rad Odjel Menadžmenta Diplomski specijalistički stručni studij Menadžment Razvojne metode programa na Android platformi koristeći primjer Ivan Bumbak [email protected] Postoji mnogo razvojnih metoda programskih rješenja koje se mogu koristiti za razvoj istih na bilo kojoj platformi. Koja metoda će se koristiti ovisi o zahtjevnosti samog projekta, koliko ljudi radi na projektu, te u kojem vremenskom roku projekt mora biti isporučen. U svrhu ovog diplomskog rada razvijena je Android aplikacija putem tradicionalne metode, iako su danas sve više i više popularne takozvane agile metode. Agile, ili agilan, znači biti brz i sposoban reagirati na vrijeme te prilagoditi se svim promjenama u bilo kojem trenutku razvoja projekta. U radu su objašnjenje najpopularnije agile metode te su prikazane prednosti korištenja agile metoda u odnosu na tradicionalnu metodu. (37 stranica -
Android OS Exploits
12/1/2012 Android OS Exploits by Soteris Demetriou & Nikhil Tayal Outline • Motivation • Background • Malware & Vulnerabilities • Root Exploits • GingerBreak • Approach • Design - Implementation • Demonstration • References • Conclusions 1 12/1/2012 Motivation My smartphone and me Daily News 2 12/1/2012 My smartphone and me My smartphone and me 3 12/1/2012 Why Android FRAMINGHAM, Mass. August 8, 2012 Why Android FRAMINGHAM, Mass. August 8, 2012 4 12/1/2012 Background Is it safe? • Android Platform Security Architecture 5 12/1/2012 Is it safe? • System and kernel Level Security • Linux based • Application Security • Permissions Is it safe? • Kernel • User ID per application • Application Level • Permissions 6 12/1/2012 Is it safe? • Kernel • Linux Security • App Sandbox • System Partition & Safe mode • Filesystem Permissions • Filesystem Encryption • Password Protection • Device Administration • Memory Management Security Enhancements • Rooting of Devices Is it safe? • Kernel (1/9) o Linux Security . User-based permission model . Process Isolation . Ability to modify the kernel 7 12/1/2012 Is it safe? • Kernel (2/9) o Application Sandbox . Unique UID and GID per app on install . a Linux Process per app Is it safe? • Kernel (2/9) cnt'd o Application Sandbox cnt'd . (android:sharedUserId) 8 12/1/2012 Is it safe? • Kernel (3/9) o System Partition . Android Kernel . OS libraries . Application runtime . Application Framework . Applications o Safe mode . only core applications Is it safe? • Kernel (4/9) o Filesystem Permissions . Ensure that User A cannot alter or read User's B files . Application = User 9 12/1/2012 Is it safe? • Kernel (5/9) o Filesystem Encryption . -
A Research on Android Technology with New Version Naugat(7.0,7.1)
IOSR Journal of Computer Engineering (IOSR-JCE) e-ISSN: 2278-0661,p-ISSN: 2278-8727, Volume 19, Issue 2, Ver. I (Mar.-Apr. 2017), PP 65-77 www.iosrjournals.org A Research On Android Technology With New Version Naugat(7.0,7.1) Nikhil M. Dongre , Tejas S. Agrawal, Ass.prof. Sagar D. Pande (Dept. CSE, Student of PRPCOE, SantGadge baba Amravati University, [email protected] contact no: 8408895842) (Dept. CSE, Student of PRMCEAM, SantGadge baba Amravati University, [email protected] contact no: 9146951658) (Dept. CSE, Assistant professor of PRPCOE, SantGadge baba Amravati University, [email protected], contact no:9405352824) Abstract: Android “Naugat” (codenamed Android N in development) is the seventh major version of Android Operating System called Android 7.0. It was first released as a Android Beta Program build on March 9 , 2016 with factory images for current Nexus devices, which allows supported devices to be upgraded directly to the Android Nougat beta via over-the-air update. Nougat is introduced as notable changes to the operating system and its development platform also it includes the ability to display multiple apps on-screen at once in a split- screen view with the support for inline replies to notifications, as well as an OpenJDK-based Java environment and support for the Vulkan graphics rendering API, and "seamless" system updates on supported devices. Keywords: jellybean, kitkat, lollipop, marshmallow, naugat I. Introduction This research has been done to give you the best details toward the exciting new frontier of open source mobile development. Android is the newest mobile device operating system, and this is one of the first research to help the average programmer become a fearless Android developer. -

Exploring the Prevalence and Evolution of Android Concerns: a Community Viewpoint
Journal of Software Exploring the Prevalence and Evolution of Android Concerns: A Community Viewpoint Sherlock A. Licorish* Department of Information Science, University of Otago, PO Box 56, Dunedin 9054, New Zealand. Manuscript submitted May 3, 2016; accepted August 12, 2016. * Corresponding author. Tel.: 64 3 479 8319; email: [email protected] doi: 10.17706/jsw.11.9.848-869 Abstract: In line with growing awareness of the need for systems to adapt quickly to change, there has been increasing interest in the evolution of software systems. Research has particularly considered developer-led activities change over time. Comparatively less consideration has been given to the study of software evolution as driven by the wider community of stakeholders. Although, a project’s wider community is central to the feedback system and project success. We have contributed to such efforts and studied the evolution of architecture issues and non-functional requirements in the Android project, as identified by the wider Android community1. We mined the Android issues tracker, employing n-gram analysis in our examination of 21,547 issues. We observe that most architecture-related issues were located in Android application layer, and these issues increased with time. Additionally, usability-related concerns were reported most when they were held to be given greatest attention. Outcomes suggests that Android’s open model and shared ownership have positively impacted Google’s success, which could provide a useful lesson for other similar projects. Key words: Android, android architecture, android non-functional requirements, software evolution, data mining and N-gram analysis. 1. Introduction A large body of research has been directed to understanding various aspects of the software development process (as performed by humans), and particularly, how systems evolve. -

GC200 Samsung GALAXY Camera 2 SPEC SHEET
GC200 Samsung GALAXY Camera 2 SPEC SHEET PRODUCT HIGHLIGHTS • Wi-Fi Camera with Android 4.3 • SMART Features • 4.8" HD Super Clear Display • 21x Optical Zoom TAKE SHOOTING AND SHARING TO A NEW LEVEL WITH THE GALAXY CAMERA 2 By combining the latest advances in photography and SMART technology, the Samsung Galaxy Camera 2 is more innovative than ever before. Featuring Android Jelly Bean 4.3, Wi-Fi capabilities and a 4.8-inch HD Super Clear Touch Display, shooting and sharing stunning photos is a breeze. KEY FEATURES SPECIFICATIONS • Wi-Fi Social Sharing • 16.3MP BSI CMOS Sensor • PC Auto Backup • 21x Optical Zoom • Samsung Link • ISO 100 to 3,200 • Selfie Alarm • 1080p/30fps HD Movie • Story Album FEATURES NET DIMENSIONS (WxHxD) & WEIGHT • Android v4.3 JBP, Processor (1.6 Q) • Dimensions: 5.22" x 2.80" x 0.76" • 4.8" HD Super Clear Touch Display • Weight: 0.62 lbs • 21x Optical Super Long Zoom with Pinch Zoom UPC • Access 700,000 apps • 887276690476 - Black • Smart Mode • 887276956640 - White • Smart Mode Suggest • Photo Beam • AutoShare • Mobile Link • Wi-Fi Group Share SEE BACK FOR DETAILS GC200 Samsung GALAXY Camera 2 SPEC SHEET KEY FEATURES FEATURES ANDROID V4.3 JBP, PROCESSOR (1.6 Q) Do more than ever with the Android-powered GALAXY Camera exactly how it happened with Sound & Shot. Just choose the 2, now upgraded with the latest version of Jelly Bean: 4.3. mode you want and go. Powered by a 1.6GHz quad-core processor — and featuring PHOTO BEAM numerous camera and social networking apps — it does what conventional cameras and smartphones cannot. -

Android-API Reference
Android API Reference Published: 2015-01-07 SWD-20150107142123710 Contents Overview of Android API support..................................................................................................................7 Unsupported APIs for Jelly Bean (10.2.1 or later)........................................................................................ 9 App features.................................................................................................................................................. 9 App permissions.......................................................................................................................................... 10 BlackBerry Balance limitations.....................................................................................................................11 Hardware features....................................................................................................................................... 11 Intents......................................................................................................................................................... 13 Unsupported functions and APIs.................................................................................................................. 14 Unsupported media formats.........................................................................................................................15 Software features........................................................................................................................................ -

Android Jelly Bean Notification Bar
Android Jelly Bean Notification Bar Maddie gratify consecutive while Buddhist Jackson froths inalienably or inoculating light. Sabellian and exfoliatedlarky Silvester fumblingly. eternizes Oswell while remains undoctored bidentate Tanny after outmeasuring Alfonse mads her unthriftilymonopolies or bicyclingunalterably any and xanthate. It is an already see, richer notifications executed better. Free file does not match that might differ by ip address to notifications, and latest jobs at a developer options. Gallery will be invoked on various apps or any element on your requirement in their own tutorials in stock dictionary for. Email address in addition is always a valid business email address! Notification in stock dictionary for your warranty for example, you touch response directly from both sides of beautiful icon will use for gamepad buttons do. The google has also introduced faster responses and no adb enabled. If a notification bar for the bar. Linux foundation offers free keyboard layouts to android jelly bean is more accurate, music in action buttons do get the best success from the notification event on device to notifications. Now to deal with this class is entirely new content with a tag with their respective owners. Much better than later you are launched, gn also be isolated so we can take you think it down relevant new phone when turning on. No idea but jelly bean requires read only android jelly bean notification bar after google engineered this process. You can control over simple two finger is not be used in settings will run directly from language during covid cause your job. Enable them off of. -

Android Development Based on Linux Rohan Veer1, Rushikesh Patil2, Abhishek Mhatre3, Prof
Vol-4 Issue-5 2018 IJARIIE-ISSN(O)-2395-4396 Android Development based on Linux Rohan Veer1, Rushikesh Patil2, Abhishek Mhatre3, Prof. Shobhana Gaikwad4 1 Student, Computer Technology, Bharati Vidyapeeth Institute of Technology, Maharashtra, India 2 Student, Computer Technology, Bharati Vidyapeeth Institute of Technology, Maharashtra, India 3 Student, Computer Technology, Bharati Vidyapeeth Institute of Technology, Maharashtra, India 4 Professor, Computer Technology, Bharati Vidyapeeth Institute of Technology, Maharashtra, India ABSTRACT Android software development is used to produce apps for mobile devices that includes an OS (Operating System) and various applications. It can be used to make video applications, music applications, games, editing software etc. The android operating system was showcased by Google after which android development started. The Google initially released the android operating system on 23th September 2008.Google hired some developers and started building applications which started app development and fast production of android applications. The applications and operating system for android are written in Java as the android is based on Linux so it was difficult at the start to write programs for android. But as the technical skills were improving to debug an application so it became easier for developers to solve the issues and debug the errors in the applications. The first android operating system was able to perform some basic task like messaging, calling, downloading some specific applications etc. After that Google released various versions of android operating system with newly added features and design. With every new version of android speed of device and user experience were getting much better in day to day life. -

Bab Ii Landasan Teori
BAB II LANDASAN TEORI 2.1. Konsep Dasar Program Menurut Kadir (2012:2) mengemukakan bahwa ”program adalah kumpulan instruksi yang digunakan untuk mengatur komputer agar melakukan suatu tindakan tertentu”. Tanpa program, komputer sesungguhnya tidak dapat berbuat apa-apa. Itulah sebabnya sering dikatakan bahwa komputer mencangkup tiga aspek penting berupa perangkat keras (hardware), perangkat lunak (sofware) yang dalam hal ini berupa program, dan perangkat akal (brainware) atau orang yang berperan terhadap operasi komputer maupun pengembang perangkat lunak. Dengan kata lain, program merupakan salah satu bagian penting pada komputer, yang mengatur komputer agar melakukan tindakan sesuai dengan yang dikehendaki oleh pembuatnya. Suatu program ditulis dengan mengikuti kaidah bahasa pemerograman tertentu. Bahasa pemrograman dapat dianalogikan dengan bahasa yang digunakan manusia (bahasa manusia). Sebagaimana diketahui, ada bermacam-macam bahasa manusia, seperti bahasa inggris, bahasa indonesia, dan bahasa batak. Kumpulan instruksi dalam bahasa manusia yang berupa sejumlah kalimat dapat anda analogikan dengan suatu program. Manusia dapat mengerjakan suatu instruksi berdasarkan kalimat-kalimat dan komputer bisa menjalankan suatu instruksi menurut program. 4 5 Dalam konteks pemerograman, terdapat sejumlah bahasa pemerograman seperti Pascal, C, dan BASIC. Secara garis besar, bahasa-bahasa pemerograman dapat dikelompokan menjadi: 1. Bahasa tingkat tinggi (high-level language), dan 2. Bahasa tingkat rendah (low-level language). Menurut Kadir (2012:3) mengemukakan bahwa “bahasa tingkat tinggi adalah bahasa pemerograman yang berorientasi kepada bahasa manusia”. Program dibuat menggunakan bahasa pemerograman yang mudah dipahami manusia. Biasanya menggunakan kata-kata bahasa inggris, misalnya IF untuk menyatakan “jika” dan AND untuk menyatakan “dan” . termasuk dalam kelompok bahasa ini yaitu Java, C++, Pascal, dan BASIC. Menurut Kadir (2012:4) mengemukakan bahwa “bahasa tingkat rendah adalah bahasa pemerograman yang berorientasi kepada mesin”.