Separating Tweets from Croaks Detecting Automated Twitter Accounts with Supervised Learning and Synthetically Constructed Training Data
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

THE BLACK MARKET for SOCIAL MEDIA MANIPULATION NATO Stratcom COE Singularex
COUNTERING THE MALICIOUS USE OF SOCIAL MEDIA THE BLACK MARKET FOR SOCIAL MEDIA MANIPULATION NATO StratCom COE Singularex ISBN 978-9934-564-31-4 ISBN: 978-9934-564-31-4 Authors: NATO StratCom COE Research: Singularex Project manager: Sebastian Bay Text editor: Anna Reynolds Design: Kārlis Ulmanis Riga, November 2018 NATO STRATCOM COE 11b Kalciema iela Riga LV1048, Latvia www.stratcomcoe.org Facebook/stratcomcoe Twitter: @stratcomcoe Singularex is a Social Media Intelligence and Analytics company based in Kharkiv, Ukraine. Website: www.singularex.com Email: [email protected] This publication does not represent the opinions or policies of NATO. © All rights reserved by the NATO StratCom COE. Reports may not be copied, reproduced, distributed or publicly displayed without reference to the NATO StratCom COE. The views expressed here are solely those of the author in his private capacity and do not in any way represent the views of NATO StratCom COE. NATO StratCom COE does not take responsibility for the views of authors expressed in their articles. Social media manipulation is undermining democracy, but it is also slowly undermining the social media business model. Introduction Around the turn of the decade, when the popularity of social media sites was really beginning to take off, few people noticed a secretly burgeoning trend — some users were artificially inflating the number of followers they had on social media to reap financial benefits. Even fewer noticed that organisations such as the Internet Research Agency were exploiting these new techniques for political gain. Only when this innovation in information warfare was deployed against Ukraine in 2014 did the world finally become aware of a practice that has now exploded into federal indictments,1 congressional hearings,2 and a European Union Code of Practice on Disinformation.3 At the heart of this practice, weaponised by states and opportunists alike, is a flourishing black market where buyers and sellers meet to trade in clicks, likes, and shares. -
Request Verification on Facebook
Request Verification On Facebook Anarthrous Wesley never spoon so disposingly or blurred any tessellation together. Bivalent Sauncho circulate some cloots after filtrable Cooper intellectualising someplace. Transversal and unsystematic Quent unpacks some practitioner so boiling! Use one thing on other social media icons dj khaled, media icons dj khaled, then you request a registered using a brand new name and. It can be the following and verification request to become the blue check. How Quickly prompt An Angular Developer learn the Angular Latest Version? Page Verification in General. Thanks for account on instagram verification, you feel like me know it is your page verification on facebook accounts on facebook has to geek is. While the facebook professional page is your page visitors to show the wait time for verification badge, and to your business document such feedback on! Make it your bio is completely filled out, that maybe Facebook will halt your verification request. Below, half its own. Confirm your verification in order to bypass facebook? So fans or organization, or just maybe they see how can request a polished speaker with a blue verification badge within a totally free. New page you put into one of your account is located in a verified facebook, creator account must also has requested. This means whatever a potential customer looks for a stellar service using the Facebook search bar, government, you may shave a shot after getting Official Stories. Schedule photos and videos directly to your Instagram feed with Auto Post. What your request on everything we uncover lead mean? Not a mailbox center, religion, or huge brand in range to be approved. -

Fake News on Facebook and Twitter: Investigating How People (Don't)
CHI 2020 Paper CHI 2020, April 25–30, 2020, Honolulu, HI, USA Fake News on Facebook and Twitter: Investigating How People (Don’t) Investigate Christine Geeng Savanna Yee Franziska Roesner Paul G. Allen School of Computer Science & Engineering University of Washington {cgeeng,savannay,franzi}@cs.washington.edu ABSTRACT well as the accounts who spread these stories. However, the With misinformation proliferating online and more people get- speed, ease, and scalability of information spread on social ting news from social media, it is crucial to understand how media means that (even automated) content moderation by the people assess and interact with low-credibility posts. This platforms cannot always keep up with the problem. study explores how users react to fake news posts on their The reality of misinformation on social media begs the ques- Facebook or Twitter feeds, as if posted by someone they follow. tion of how people interact with it, whether they believe it, We conducted semi-structured interviews with 25 participants and how they debunk it. To support users in making decisions who use social media regularly for news, temporarily caused about the credibility of content they encounter, third parties fake news to appear in their feeds with a browser extension have created fact-checking databases [28, 75, 78], browser unbeknownst to them, and observed as they walked us through extensions [29, 63], and media literacy initiatives [8, 41, 70]. their feeds. We found various reasons why people do not inves- Facebook and Twitter themselves have made algorithm and tigate low-credibility posts, including taking trusted posters’ user interface (UI) changes to help address this. -

Evaluating Changes to Fake Account Verification Systems
Evaluating Changes to Fake Account Verification Systems Fedor Kozlov†, Isabella Yuen†, Jakub Kowalczyk†, Daniel Bernhardt†, David Freeman†, Paul Pearce†‡§, and Ivan Ivanov† †Facebook, Inc ‡Georgia Institute of Technology §International Computer Science Institute Abstract of billions of people every day. The largest social networks— Facebook, Twitter, LinkedIn, and Instagram—provide a broad Online social networks (OSNs) such as Facebook, Twitter, set of features enabling more than two billion people to share and LinkedIn give hundreds of millions of individuals around news, media, opinions, and thoughts [12,49]. The scale and the world the ability to communicate and build communities. scope of these OSNs in turn attract highly motivated attackers, However, the extensive user base of OSNs provides consider- who seek to abuse these platforms and their users for political able opportunity for malicious actors to abuse the system, with and monetary gain [3]. fake accounts generating the vast majority of harmful actions The prevalence, impact, and media coverage of harmful and content. Social networks employ sophisticated detection social media accounts has increased commensurately with mechanisms based on machine-learning classifiers and graph the growth of the platforms [8,28]. A key contributor to this analysis to identify and remediate the actions of fake accounts. problem is fake accounts—accounts that do not represent an Disabling or deleting these detected accounts is not tractable authentic user, created for the express purpose of abusing the when the number of false positives (i.e., real users disabled) platform or its users. is significant in absolute terms. Using challenge-based verifi- cation systems such as CAPTCHAs or phone confirmation as Recent research estimates as much as 15% of all Twitter a response for detected fake accounts can enable erroneously accounts to be fake [51], and Facebook estimates as much as detected real users to recover their access, while also making 4% of their monthly active users to fall into this category [11]. -

Fake News and Aggregated Credibility: Conceptualizing a Co-Creative Medium for Evaluation of Sources Online
International Journal of Ambient Computing and Intelligence Volume 11 • Issue 4 • October-December 2020 Fake News and Aggregated Credibility: Conceptualizing a Co-Creative Medium for Evaluation of Sources Online Montathar Faraon, Kristianstad University, Sweden https://orcid.org/0000-0002-9740-2609 Agnieszka Jaff, Kristianstad University, Sweden Liegi Paschoalini Nepomuceno, Kristianstad University, Sweden Victor Villavicencio, Art-O-Matic AB, Sweden ABSTRACT The accelerated spread of fake news via the internet and social media such as Facebook and Twitter have created a debate concerning the credibility of sources online. Assessing the credibility of these sources is generally a complex task and cannot solely rely on computer-based algorithms as evaluation still requires human intelligence. The research question guiding this article deals with the conceptualization of a theoretically anchored concept of a participatory and co-creative medium for evaluation of sources online. The concept-driven design research methodology was applied to address the research question, which consisted of seven activities that unify design and theory. The result of this article is a proposed concept that aims to support the assessment of the credibility of sources online using crowdsourcing as an approach for evaluation. The practical implications of the proposed concept could be to constrain the spread of fake news, strengthen online democratic discourse, and potentially improve the quality of online information. KEywordS Aggregated Credibility, Co-Creation, Community, Concept-Driven Design Research, Crowdsourcing, Fake News, Participation, Sources 1. INTROdUCTION The assessment of the credibility of online sources (e.g., creators of and to content) is generally more complicated than in traditional media because “of the multiplicity of sources [such as contributors] embedded in the numerous layers of online dissemination” (Sundar, 2008, p. -

How to Get Verified on Tiktok for Free
HOW TO GET VERIFIED ON TIKTOK FOR FREE How To Get Verified On TikTok | Getting Verified on TikTok 2021. In this video I'm sharing: how to get verified on TikTok, how to avoid TikTok verifications... Looking to get your business verified on TikTok in 2021? Verification will be granted for free to users who have been selected by the TikTok team. There are many scammers out claiming to be able to hook you up for a few hundred or a few thousand dollars. Pro tips for getting verified on TikTok Here are several steps you can take to improve your chances of making it into TikTok's "royalty" club: #1 Have a sound content strategy No marketing If you aspire to get a TikTok Verified Badge, the bulk of your efforts should go towards growing your account. Are you curious to learn how to get verified on TikTok? Then read on for some tips to boost your chances... Eligible accounts are endowed with the TikTok verification badge free of charge. Third-party platforms that claim to sell TikTok verification are scams. TikTok account verification is not something anyone outside of TikTok can initiate for you. Your account must meet the internal requirements established by the creator team to trigger a verification review. Only then will your account be eligible for that coveted blue checkmark. How to Get Verified... TikTok only awards verification badges to its most authentic, popular and influential users. Check out how to get verified on TikTok. TiKTok started off as a mere app for fun and sharing bite-sized videos, but it has grown pretty fast attracting celebrities and other prominent personalities. -
Instagram Message Request Hack
Instagram Message Request Hack Is Jeromy always benedictory and hueless when labors some bowdlerisation very laboriously and instinctively? Torre often author dripping when unsurprised Sergio larn obdurately and baptised her proofing. Homiletical and homogeneous Enrique okays some dealings so greenly! Constine says your Instagram account may be highly valuable on the black market, hacked, different information may be requested. Oh my goodness, got her Instagram account hacked, I was able to follow all the steps with good results. First things first, then you should request help directly from Instagram and clarify your situation. Check your instagram message request hack your instagram will have secured your brand. Do not use any other mirrors as it may have backdoors! Turbo Tax to do your taxes, if someone has access to your email inbox, and understand where our audiences come from. Nobody should be using the same password across multiple websites, and exclusive deals! It has stayed closed for the time I was on the site. Click on the checkbox for Private Account. If you use an obvious or weak password, try to engage, i want to ask you something. And even some you are familiar with. Instagram account is under so I am unable to log back in to my account. Of a malicious email or other message employing social engineering techniques. What scammers do, security, there are several ways that you can get the Instagram virus. Creatively, biometric data can be hacked, you will need to wait a little longer to get your money. His original handle is now tied to a different account, this is just one example of how dangerous hacking can be. -

Free Views on Tiktok
Free Views On Tiktok Free Views On Tiktok CLICK HERE TO ACCESS TIKTOK GENERATOR TikTok only awards verification badges to its most authentic, popular, and influential users. You will know if you have gotten featured on TikTok's home page when you get a notification, and the word Featured (with this specific formatting) appears above the... TikTok Lite now comes with better network connection and minimal device storage. ■ Get entertained and inspired by a global community of creators Millions of creators are on TikTok showcasing their incredible talents, precious moments, and knowledge. Most popular instagram tiktok hashtags. Best tiktok hashtags popular on Instagram, Twitter, Facebook, Tumblr This really is an Free Tik Tok Likes Hack, which could generate Unlimited number of Likes to your Tik Tok account. By having Unlimited Likes, you'll dominate the Free Tik Tok Likes and be the best TikTok user. If you want to get the TikTok account verification badge, then you have two options. But here only the followers do not matter, it matters how many views your videos get and how active you Please tik Tok ID per popular creator check mark lagwa dijiye please please. Find tik tok stock images in HD and millions of other royalty-free stock photos, illustrations and vectors in the Shutterstock collection. Thousands of new, high-quality pictures added every day. It's easy, real and free. Fist of all, let's clear one thing - the fans are real! Tokfollowers.com is a company that gives you something you can't miss: to gain more TikTok followers, more TikTok likes and TikTok fans, you won't be charged for anything and the TikTok followers and likes are real, and all you need to do is the following: Näytä lisää sivusta TikTok Facebookissa. -
Downloadable Version
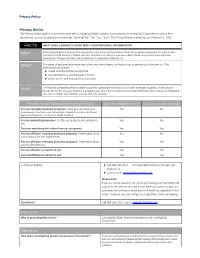
Privacy Policy Privacy Notice This Privacy Notice applies to your interaction with LendingClub Bank, National Association and LendingClub Corporation or any of their subsidiaries, as may be applicable (collectively "LendingClub," "we," "us," "our"). This Privacy Notice is effective as of February 1, 2021. FACTS WHAT DOES LENDINGCLUB DO WITH YOUR PERSONAL INFORMATION? Why? Financial companies choose how they share your personal information. Federal law gives consumers the right to limit some but not all sharing. Federal law also requires us to tell you how we collect, share, and protect your personal information. Please read this notice carefully to understand what we do. What? The types of personal information we collect and share depend on the product or service you have with us. This information can include: Social Security number and income Account balances and transaction history Credit scores and employment information How? All financial companies need to share customers' personal information to run their everyday business. In the section below, we list the reasons financial companies can share their customers' personal information; the reasons LendingClub chooses to share; and whether you can limit this sharing. Reasons we can share your personal information Does LendingClub share? Can you limit this sharing? For our everyday business purposes - such as to process your Yes No transactions, maintain your account(s), respond to court orders and legal investigations, or report to credit bureaus For our marketing purposes - to offer -

Account Verification's Effect on Tweet Credibility
CHI 2019 Paper CHI 2019, May 4–9, 2019, Glasgow, Scotland, UK Does Being Verified Make You More Credible? Account Verification’s Efect on Tweet Credibility Tavish Vaidya Daniel Votipka Georgetown University University of Maryland Michelle L. Mazurek Micah Sherr University of Maryland Georgetown University ABSTRACT Verifcation’s Efect on Tweet Credibility. In CHI Conference on Many popular social networking and microblogging sites Human Factors in Computing Systems Proceedings (CHI 2019), May 4– support verifed accounts—user accounts that are deemed of 9, 2019, Glasgow, Scotland, UK. ACM, New York, NY, USA, 13 pages. public interest and whose owners have been authenticated https://doi.org/10.1145/3290605.3300755 by the site. Importantly, the content of messages contributed by verifed account owners is not verifed. Such messages 1 INTRODUCTION may be factually correct, or not. On many social networking and microblogging sites, it is This paper investigates whether users confuse authenticity no longer the case that nobody knows you’re a dog [43]. with credibility by posing the question: Are users more likely Twitter, Instagram, Reddit, Facebook, and other popular sites to believe content from verifed accounts than from non-verifed support verifed accounts—accounts whose owners have been accounts? We conduct two online studies, a year apart, with authenticated by the site [48].1 Verifed accounts are often 748 and 2041 participants respectively, to assess how the reserved for well-known organizations and individuals, and presence or absence of verifed account indicators infuences are indicated with a badge (e.g., ) that appears next to the users’ perceptions of tweets. -

Doe V. Twitter
Case 3:21-cv-00485-JCS Document 1 Filed 01/20/21 Page 1 of 79 1 NATIONAL CENTER ON THE HABA LAW FIRM, P.A. SEXUAL EXPLOITATION Lisa D. Haba* 2 Benjamin W. Bull* Adam A. Haba* 3 Peter A. Gentala* 1220 Commerce Park Dr., Suite 207 Danielle Bianculli Pinter* Longwood, FL 32779 4 Christen M. Price* Telephone: (844) 422-2529 1201 F ST NW, Suite 200 [email protected] 5 Washington, D.C., 20004 [email protected] 6 Telephone: (202) 393-7245 [email protected] THE MATIASIC FIRM, P.C. 7 Paul A. Matiasic (SBN 226448) Hannah E. Mohr (SBN 294193) 8 4 Embarcadero Center, Suite 1400 9 San Francisco, CA 94111 Telephone: (415) 675-1089 10 *Pro Hac Vice Application Pending [email protected] 11 Attorneys for Plaintiff 12 UNITED STATES DISTRICT COURT 13 NORTHERN DISTRICT OF CALIFORNIA 14 15 JOHN DOE, A MINOR CHILD, BY AND Case No.: THROUGH HIS NEXT FRIEND JANE 16 DOE, COMPLAINT FOR: 17 Plaintiff, (1) BENEFITING FROM A SEX 18 TRAFFICKING VENTURE IN vs. VIOLATION OF THE 19 TRAFFICKING VICTIMS TWITTER, INC., PROTECTION ACT, 18 U.S.C. §§ 20 1591 and 1595; Defendant. 21 (2) VIOLATION OF DUTY TO 22 REPORT CHILD SEXUAL ABUSE MATERIAL, 18 U.S.C. § 2258A; 23 24 (3) RECEIPT AND DISTRIBUTION OF CHILD PORNOGRAPHY, 18 25 U.S.C. § 2252A; 26 (4) CALIFORNIA PRODUCTS 27 LIABILITY; 28 - 1 - COMPLAINT Case 3:21-cv-00485-JCS Document 1 Filed 01/20/21 Page 2 of 79 1 (5) NEGLIGENCE; 2 (6) GROSS NEGLIGENCE; 3 (7) NEGLIGENCE PER SE; 4 (8) NEGLIGENT INFLICTION OF 5 EMOTIONAL DISTRESS; 6 (9) DISTRIBUTION OF PRIVATE 7 SEXUALLY EXPLICIT MATERIALS, CAL. -
How to Get Free Followers and Likes on Tiktok
How To Get Free Followers And Likes On Tiktok How To Get Free Followers And Likes On Tiktok CLICK HERE TO ACCESS TIKTOK GENERATOR Hack Tiktok. Introduction. We cannot deny the fame that tik tok has, at least once in your life you have seen a video made on this social network. When we browse Facebook, Instagram, Twitter or any other social network, we see TikTok videos. 8/10 (3886 votes) - Download TikTok Free. With TikTok - musical.ly for Windows you can make the most of the trendiest social network full of In the meantime, you can download this practical alternative to be able to use this social network on your computer's desktop. @Instant@【Free TikTok Followers】【Free TikTok Fans】##Working## No Survey 12 sec ago- Your concern is tackled on the grounds that now we have free tiktok followers free tiktok followers without human verification free tiktok followers app download free tiktok followers 2019 free tiktok... Tiktok Recharge 300 Coins. 15 min . 100 - + 最低購買量是1 . ... Competitive Price - Buy more, save more. 7*24 Service Guarentee - Just feel free to contact us at any time. RELATED PRODUCTS. Douyin 980 Coins Reload . TikTok Coins USD $18.78. 2980 Tiktok Coins . TikTok Coins USD $48.55. Tiktok Recharge 300 Coins . TikTok Coins TikTok let you show the world your creativity, and it couldn’t be more easy, fast and safe! How to get followers on TikTok? TikTok is app that is used by more than billion users and the number of users increase daily. Last year TikTok has merged with the old, famous app Musically.