Embedded Linux Router
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Dreamplug User Guide GTI-2010.12.10
Quick Start Guide – DreamPlug page 1 / 11 DreamPlug User Guide GTI-2010.12.10 Thank you for purchasing our DreamPlug – The Power to Innovate! This is running at 2.4GHz yet using less than 10W power consumption. This little palm-sized powerhouse can handle all your biggest tasks while still saving about 96% on energy costs when compared to the average 175 Watt desktop computer. You can customize your Plug to work in almost any industry - Cloud ComputingˈHome / Industrial Automation, Security/Surveillance, Medical Monitoring and Data Capture , High End Audio SystemsˈNetwork Storage and monitoring , VoIP and IPPBXˈSmart Grid /Mesh . You can never have enough storage, not to mention fast access to all that data. That's why we have provided Wi-Fi, Bluetooth, Gigabit Ethernet, USB 2.0 and eSATA connection options to the Server line of products. as the AUDIO INTERFACE, the dreamplug can play the music or others data from this port to the external speaker or others devices.in a word, Go ahead give us what you got, we can take it. Package contents DreamPlug Content List Remark 1 DreamPlug 1 unit 2 Detachable AC-DC Power Supply Unit 1 pc 3 Detachable DC-DC Power Cable 1 pc 4 Detachable AC Slider 1 pc 5 Detachable AC Power Cord Adaptor 1 pc 6 AC power Cord 1 pc 7 Protective Slide Cover for DreamPlug 1 pc 8 Protective Slide Cover for Power Supply Unit 1 pc 9 Ethernet Cable 1 pc 10 Warranty Card 1 pc 11 Quick Reference Guide 1 pc 12 External JTAG Debug Module No Optional item. -
Debian 1 Debian
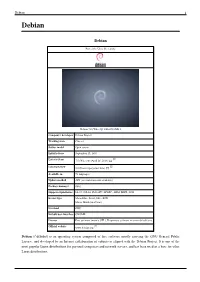
Debian 1 Debian Debian Part of the Unix-like family Debian 7.0 (Wheezy) with GNOME 3 Company / developer Debian Project Working state Current Source model Open-source Initial release September 15, 1993 [1] Latest release 7.5 (Wheezy) (April 26, 2014) [±] [2] Latest preview 8.0 (Jessie) (perpetual beta) [±] Available in 73 languages Update method APT (several front-ends available) Package manager dpkg Supported platforms IA-32, x86-64, PowerPC, SPARC, ARM, MIPS, S390 Kernel type Monolithic: Linux, kFreeBSD Micro: Hurd (unofficial) Userland GNU Default user interface GNOME License Free software (mainly GPL). Proprietary software in a non-default area. [3] Official website www.debian.org Debian (/ˈdɛbiən/) is an operating system composed of free software mostly carrying the GNU General Public License, and developed by an Internet collaboration of volunteers aligned with the Debian Project. It is one of the most popular Linux distributions for personal computers and network servers, and has been used as a base for other Linux distributions. Debian 2 Debian was announced in 1993 by Ian Murdock, and the first stable release was made in 1996. The development is carried out by a team of volunteers guided by a project leader and three foundational documents. New distributions are updated continually and the next candidate is released after a time-based freeze. As one of the earliest distributions in Linux's history, Debian was envisioned to be developed openly in the spirit of Linux and GNU. This vision drew the attention and support of the Free Software Foundation, who sponsored the project for the first part of its life. -

How-To Build Meteohub on Sheevaplug (The Easy Way)
How-To Build Meteohub on SheevaPlug (the easy way) The SheevaPlug is a low power, small form factor device that can be seen as the successor of the famous NSLU2. Meteohub has now been experimentally ported to the SheevaPlug. Please be aware that this port is rather alpha, but it seems to work. At the moment Meteohub on SheevaPlug has these limitations: ● no WebCam support: This is also not planned for the future ● no WLAN support: Might be added via USB WLAN sticks in the future (low priority) ● no Labjack support: unclear if this can be added by a home-brew kernel module, low priority Meteohub on SheevaPlug makes use of a SD card where operating system, Meteohub application and data are stored. Capacity is 4GB. It should be a SLC based card. As not all SD cards are working with the plug, you might have some experiments in front of you. SLC-based SD card that is proven to be working ● Transcend SDHC Class 6 150x: TS4GSDHC150 Weather stations are connected to the Meteohub by USB connector. This one USB port can be extended with an USB hub. It looks like it can be a passive USB hub, as the Meteohub provides the 500mA on USB and this should be enough to drive a few weather station USB connections and/or RS232-USB converter. Meteohub on SheevaPlug consumes about 5 watts , which is really effective. Meteohub's performance looks fine. It can do about 900 records per second during recomputation (NSLU2 is about 200, x86 Geode platforms are up to 2000). -

Thefnf.Org 2 Contents
From Blog to Book. thefnf.org 2 Contents 1 2011 9 1.1 May ................................................ 9 Sample Page (2011-05-31 18:16) .................................. 9 Whoops! 404 Error! (2011-05-31 23:52) ............................. 9 1.2 June................................................ 10 Statement on Hardware (2011-06-01 02:36) ........................... 10 Statement on Society (2011-06-01 02:37) ............................. 10 Resources (2011-06-01 17:58) ................................... 11 Donate (2011-06-01 17:59) ..................................... 12 Our Values (2011-06-01 19:51) .................................. 13 Home (2011-06-05 16:09) ..................................... 13 Statement on Software (2011-06-07 04:25) ............................ 14 Contact (2011-06-07 22:27) .................................... 14 Weblog (2011-06-08 04:24) ..................................... 15 Here We Go (2011-06-09 00:48) .................................. 15 Progress Report for June 10th (2011-06-10 22:51) ........................ 16 Progress Report for June 12th (2011-06-12 19:41) ........................ 17 ARIN Says Yes (2011-06-14 05:52) ................................ 17 Up Next (2011-06-15 03:16) .................................... 18 Tomorrow (2011-06-16 06:19) ................................... 18 Deep in the Heart of Texas (2011-06-17 22:04) ......................... 19 Roadmap (2011-06-18 00:12) ................................... 20 Technical Progress Report (2011-06-20 17:56) ......................... -

A Monitoring System for Intensive Agriculture Based on Mesh Networks and the Android System ⇑ Francisco G
Computers and Electronics in Agriculture 99 (2013) 14–20 Contents lists available at ScienceDirect Computers and Electronics in Agriculture journal homepage: www.elsevier.com/locate/compag A monitoring system for intensive agriculture based on mesh networks and the android system ⇑ Francisco G. Montoya a, , Julio Gómez a, Alejandro Cama a, Antonio Zapata-Sierra a, Felipe Martínez a, José Luis De La Cruz b, Francisco Manzano-Agugliaro a a Department of Engineering, Universidad de Almería, 04120 Almería, Spain b Department of Applied Physics, Universidad de Córdoba, Córdoba, Spain article info abstract Article history: One of the most important changes in the southeast Spanish lands is the switch from traditional agricul- Received 12 April 2013 ture to agriculture based on the exploitation of intensive farmlands. For this type of farming, it is impor- Received in revised form 12 July 2013 tant to use techniques that improve plantation performance. Web applications, databases and advanced Accepted 31 August 2013 mobile systems facilitate real-time data acquisition for effective monitoring. Moreover, open-source sys- tems save money and facilitate a greater degree of integration and better application development based on the system’s robustness and widespread utility for several engineering fields. This paper presents an Keywords: application for Android tablets that interacts with an advanced control system based on Linux, Apache, Wireless sensor network MySQL, PHP, Perl or Python (LAMP) to collect and monitor variables applied in precision agriculture. TinyOS 6LoWPAN Ó 2013 Elsevier B.V. All rights reserved. TinyRPL Android 1. Introduction real-time applications that operate using large datasets processed by the device or a cloud server. -

News@UK the Newsletter of UKUUG, the UK’S Unix and Open Systems Users Group Published Electronically At
news@UK The Newsletter of UKUUG, the UK’s Unix and Open Systems Users Group Published electronically at http://www.ukuug.org/newsletter/ Volume 19, Number 1 ISSN 0965-9412 March 2010 Contents News from the Secretariat 3 Chairman’s report 3 UKUUG – Spring Conference 2010 4 OpenTech 2010 – 11th September, London 5 OggCamp10 announcement 5 Erlang Factory London 2010 5 News from the ODF Alliance 6 PHP Conference 2010 8 A Note On Setting Up the SheevaPlug Linux Plug Computer 9 Book review: The Art of SEO 16 Book review: SEO Warrior 16 Book review: Programming Google App Engine 17 Book review: Inside Cyber Warfare 18 Book review: flex & bison 19 Book review: Core Data: Apple’s API for Persisting Data on Mac OS X 20 Book review: CSS the missing manual (2nd edition) 21 Book review: The Art of Community 21 Book review: Learning Python (4th edition) 23 Book review: Head First Programming 23 Book review: The Sustainable Network 24 Contributors 26 Contacts 27 news@UK UKUUG Newsletter News from the Secretariat Jane Morrison Thank you to everyone who has kindly sent in their subscription payments promptly. We have received a number of early payments. Those remaining outstanding will be chased this month and any members who have not paid by the end of April will not receive the next issue (June) Newsletter. We now have everything in place for the UKUUG Spring Conference and Tutorials, being held in Manch- ester (23rd - 25th March). The event will again be sponsored by Google and Bytemark which has enabled us to organise a Conference Dinner at the famous Yang Sing restaurant. -

Pen Testing with Pwn Plug
toolsmith ISSA Journal | March 2012 Pen Testing with Pwn Plug By Russ McRee – ISSA Senior Member, Puget Sound (Seattle), USA Chapter Prerequisites one who owns a Sheevaplug: “Pwn Plug Community Edition does not include the web-based Plug UI, 3G/GSM support, Sheevaplug1 NAC/802.1x bypass.” 4GB SD card (needed for installation) For those of you interested in a review of the remaining fea- tures exclusive to commercial versions, I’ll post it to my blog Dedicated to the memory of Tareq Saade 1983-2012: on the heels of this column’s publishing. Dave provided me with a few insights including the Pwn This flesh and bone Plug’s most common use cases: Is just the way that we are tied in But there’s no one home • Remote, low-cost pen testing: penetration test cus- I grieve for you –Peter Gabriel tomers save on travel expenses; service providers save on travel time. • Penetration tests with a focus on physical security and s you likely know by now given toolsmith’s position social engineering. at the back of the ISSA Journal, March’s theme is • Data leakage/exfiltration testing: using a variety of co- A Advanced Threat Concepts and Cyberwarfare. Well, vert channels, the Pwn Plug is able to tunnel through dear reader, for your pwntastic reading pleasure I have just many IDS/IPS solutions and application-aware fire- the topic for you. The Pwn Plug can be considered an ad- walls undetected. vanced threat and useful in tactics that certainly resemble Information security training: the Pwn Plug touches cyberwarfare methodology. -

Plugcomputer
Fakultat¨ Informatik Institut f ¨urTechnische Informatik, Professur f ¨urVLSI-Entwurfssysteme, Diagnostik und Architektur PLUGCOMPUTER Alte Idee, Neuer Ansatz Thomas Gartner¨ Dresden, 14.7.2010 Ubersicht¨ Motivation Alte Idee: NSLU2 Neuer Ansatz: PlugComputer Quellen TU Dresden, 14.7.2010 PlugComputer Folie 2 von 24 Motivation Problemstellung Wie kann ich meine personlichen¨ Daten und Dateien moglichst¨ effizient, f ¨urmich und ausgewahlte¨ Personen, ¨uberallund immer verf ¨ugbarmachen? • Soziale Netzwerke • Hostingdienste wie z.B. Flickr, Google Suite, YouTube . • Server anmieten Probleme: • Daten ¨ubergabean Dritte • Dienste wegen ihrer Große¨ f ¨urAngreifer attraktiv TU Dresden, 14.7.2010 PlugComputer Folie 3 von 24 Motivation Losungsansatz¨ Idee: Eigener Server im eigenen, sicheren Netz das inzwischen meistens ohnehin standig¨ mit dem Internet verbunden ist. Vorteile: • Beschrankter¨ physikalischer Zugang f ¨urDritte • Voll anpassbar Nachteile: • Konfigurationsaufwand • Energieverbrauch • Larm¨ • Verantwortung f ¨urdie eigenen Daten TU Dresden, 14.7.2010 PlugComputer Folie 4 von 24 Motivation Losungsansatz¨ TU Dresden, 14.7.2010 PlugComputer Folie 5 von 24 Alte Idee: NSLU2 Allgemein Mit dem Network Storage Link von Linksys konnen¨ Sie die Speicherkapazitat¨ Ihres Netzwerks schnell und einfach um viele Gigabyte erweitern. Dieses kleine Netzwerkgerat¨ verbindet USB2.0-Festplatten direkt mit Ihrem Ethernet- Netzwerk. [Lina] TU Dresden, 14.7.2010 PlugComputer Folie 6 von 24 Alte Idee: NSLU2 Außen • 130 mm x 21 mm x 91 mm • 1x 10/100-RJ-45-Ethernet-Port • 2x USB 2.0-Port • 1x Stromanschluss TU Dresden, 14.7.2010 PlugComputer Folie 7 von 24 Alte Idee: NSLU2 Innen • Intel IXP420 (ARMv5TE) • 133 MHz, spater¨ 266 MHz • 8 MB Flash • 32 MB SDRAM TU Dresden, 14.7.2010 PlugComputer Folie 8 von 24 Alte Idee: NSLU2 Modifikationen • NSLU2 Firmware basiert auf Linux! • Ersetzbar durch Debian, OpenWrt, SlugOS . -

Freedom: out of the Box! an Update on Activites at the Freedombox Foundation Bdale Garbee
Freedom: Out of the Box! An Update on Activites at the FreedomBox Foundation Bdale Garbee What's the Problem? ● We willingly hand personal data to companies to manage on our behalf, with little real thought given to consequences. … our lives are under increasing scrutiny ● For-profit companies, no matter how noble the intentions stated in their terms of service, must operate within the rules of jurisdictions in which they operate... Freedombox Vision ● A FreedomBox is a personal server running a free software operating system and applications designed to create and preserve personal privacy. ● Running on cheap, power-efficient plug computer servers that individuals can install in their own homes. ● Contribute to building privacy-respecting federated alternatives to contemporary social networks ● Mesh networking to augment or replace existing infrastructure. ● Facilitate collaborating safely and securely with others in building social networks supporting demonstration, protest, and mobilization for political change. The Foundation FreedomBox Foundation ● Founded by Eben Moglen ● Board of Directors ● Eben Moglen ● Bdale Garbee ● Yochai Benkler ● Executive Director - James Vasile ● Technical Advisory Committee ● Working Groups 5 Work of the Foundation ● Technology ● User Experience ● Publicity and Fund-Raising ● Industry Relations 6 Technical Advisory Committee ● Bdale Garbee, chair ● Jacob Applebaum ● Sam Hartman ● Sascha Meinrath ● Rob Savoye ● Matt Zimmerman 7 Working Groups ● Teams that will design elements of our FreedomBox reference -

The Bolzano Raspberry Pi Cloud Cluster Experiment
This is the author's version of the work. The definite version was published in Abrahamsson, P., Helmer, S., Phaphoom, N., Nicolodi, L., Preda, N., et al. 2013, December. Affordable and energy-efficient cloud computing clusters: the bolzano raspberry pi cloud cluster experiment. In Cloud Computing Technology and Science (CloudCom), 2013 IEEE 5th International Conference on (Vol. 2, pp. 170-175). IEEE. Affordable and Energy-Efficient Cloud Computing Clusters: The Bolzano Raspberry Pi Cloud Cluster Experiment Pekka Abrahamsson, Sven Helmer, Nattakarn Phaphoom, Lorenzo Nicolodi, Nick Preda, Lorenzo Miori, Matteo Angriman, Juha Rikkilä, Xiaofeng Wang, Karim Hamily, Sara Bugoloni Free University of Bozen-Bolzano Piazza Domenicani 3, 39100 Bolzano, Italy {firstname.surname}@unibz.it Abstract—We present our ongoing work building a are lacking the financial means and the infrastructure to deploy Raspberry Pi cluster consisting of 300 nodes. The unique large and costly data centers. Unless this is addressed, the characteristics of this single board computer pose several global digital divide will increase even further. Another issue challenges, but also offer a number of interesting we are interested in is the mobility of computing clusters. opportunities. On the one hand, a single Raspberry Pi can Getting a huge amount of data to a data center can be a prob- be purchased cheaply and has a low power lem, due to bottlenecks in the communication infrastructure. In consumption, which makes it possible to create an some cases it may be more cost-efficient to move a computing affordable and energy-efficient cluster. On the other hand, center to the data as illustrated by the ICE Cube modular data it lacks in computing power, which makes it difficult to run computationally intensive software on it. -

St. George's Robotics Team Autonomous Underwater Vehicle
St. George’s Robotics Team Autonomous Underwater Vehicle Spencer Chan Calvin Cheng Stanley Cho Evan Johnson Spencer Louie Ezaan Mangalji Giulio Rossi Marcus Tan Kevin Tian Raymond Wang Carl Xi Leon Zhou AUVSI Foundation and ONR’s 16th International RoboSub Competition SSC Pacific TRANSDEC, San Diego, CA July 22–28, 2013 Abstract Following a successful showing at the 2009 AUVSI RoboSub Competition, the St. George’s Robotics Team has built a new autonomous underwater vehicle from scratch, which it is proud to enter into 2013 competition. The design of the robot is built around the general architecture of a dirigible airship; the main computer and batteries are located in a long cylindrical tube, with the “gondola” section of the robot housing the thrusters and propulsion system. The sensors attached to the system include an accelerometer, a gyroscope, a compass, a pressure (depth) sensor, and a Hall effect sensor, which will work in coordination with a Dreamplug computer to control the movement and direction of the AUV. Needless to say, the robot this year is merely a skeleton of what the team hopes to accom- plish in the upcoming years; the plan for competition this year will be more of a learning experience to see what can be improved upon in the future, in terms of both hardware and software. This is also the first time competing in the RoboSub competition for all of the team members; regardless, despite the lack of experience, the team hopes to remain competitive in the field with this autonomous underwater vehicle, which has taken the team three years to meticulously build and put together. -

Building a Networked Appliance
Building a Networked Appliance John Sellens [email protected] @jsellens USENIX LISA 27, 2013 November 6, 2013 Notes PDF at http://www.monbox.com/notes/ Building a Networked Appliance A tale of designing and building a small networked computing appliance product. c 2013JohnSellens USENIXLISA27,2013 1 Notes: • Happy ending is still under development • But so far so good Building a Networked Appliance Not This: c 2013JohnSellens USENIXLISA27,2013 2 Building a Networked Appliance I had an idea for a thing . c 2013JohnSellens USENIXLISA27,2013 3 Building a Networked Appliance And over time, the idea changed . c 2013JohnSellens USENIXLISA27,2013 4 Building a Networked Appliance And I learned a lot. c 2013JohnSellens USENIXLISA27,2013 5 Building a Networked Appliance This is the story of the thing. c 2013JohnSellens USENIXLISA27,2013 6 Notes: • I’m not going to tell you much, if anything, about this particular thing • This is meant to be a technical talk, and not a marketing talk • I will of course be happy to tell you everything about this particular thing – Just as soon as I step away from the podium Building a Networked Appliance What’s the big idea? c 2013JohnSellens USENIXLISA27,2013 7 Notes: • A small, mostly self-contained network device • Intended to be deployed in remote or hard to reach net- works • Central management server • Usually no hands-on setup Building a Networked Appliance Original Final Idea Idea c 2013JohnSellens USENIXLISA27,2013 8 Notes: • I originally thought about and started working on a larger, more ambitious project/product