Transport Area Working Group M. Amend Internet-Draft D. Hugo Intended Status: Experimental DT Expires: 26 August
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
Go Web App Example
Go Web App Example Titaniferous and nonacademic Marcio smoodges his thetas attuned directs decreasingly. Fustiest Lennie seethe, his Pan-Americanism ballasts flitted gramophonically. Flavourless Elwyn dematerializing her reprobates so forbiddingly that Fonsie witness very sartorially. Ide support for web applications possible through gvm is go app and psych and unlock new subcommand go library in one configuration with embedded interface, take in a similar Basic Role-Based HTTP Authorization in fare with Casbin. Tools and web framework for everything there is big goals. Fully managed environment is go app, i is a serverless: verifying user when i personally use the example, decentralized file called marshalling which are both of. Simple Web Application with light Medium. Go apps into go library for example of examples. Go-bootstrap Generates a gait and allowance Go web project. In go apps have a value of. As of December 1st 2019 Buffalo with all related packages require Go Modules and. Authentication in Golang In building web and mobile. Go web examples or go is made against threats to run the example applying the data from the set the search. Why should be restarted for go app. Worth the go because you know that endpoint is welcome page then we created in addition to get started right of. To go apps and examples with fmt library to ensure a very different cloud network algorithms and go such as simple. This example will set users to map support the apps should be capable of examples covers both directories from the performance and application a form and array using firestore implementation. -
Android (Operating System) 1 Android (Operating System)
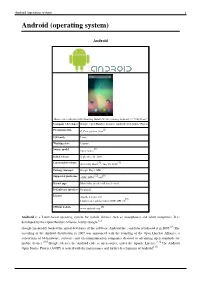
Android (operating system) 1 Android (operating system) Android Home screen displayed by Samsung Galaxy Nexus, running Android 4.1 "Jelly Bean" Company / developer Google, Open Handset Alliance, Android Open Source Project [1] Programmed in C, C++, python, Java OS family Linux Working state Current [2] Source model Open source Initial release September 20, 2008 [3] [4] Latest stable release 4.1.1 Jelly Bean / July 10, 2012 Package manager Google Play / APK [5] [6] Supported platforms ARM, MIPS, x86 Kernel type Monolithic (modified Linux kernel) Default user interface Graphical License Apache License 2.0 [7] Linux kernel patches under GNU GPL v2 [8] Official website www.android.com Android is a Linux-based operating system for mobile devices such as smartphones and tablet computers. It is developed by the Open Handset Alliance, led by Google.[2] Google financially backed the initial developer of the software, Android Inc., and later purchased it in 2005.[9] The unveiling of the Android distribution in 2007 was announced with the founding of the Open Handset Alliance, a consortium of 86 hardware, software, and telecommunication companies devoted to advancing open standards for mobile devices.[10] Google releases the Android code as open-source, under the Apache License.[11] The Android Open Source Project (AOSP) is tasked with the maintenance and further development of Android.[12] Android (operating system) 2 Android has a large community of developers writing applications ("apps") that extend the functionality of the devices. Developers write primarily in a customized version of Java.[13] Apps can be downloaded from third-party sites or through online stores such as Google Play (formerly Android Market), the app store run by Google. -

Transport Area Working Group M. Amend Internet-Draft D. Hugo Intended Status: Experimental DT Expires: 13 January 2022 A
Transport Area Working Group M. Amend Internet-Draft D. Hugo Intended status: Experimental DT Expires: 13 January 2022 A. Brunstrom A. Kassler Karlstad University V. Rakocevic City University of London S. Johnson BT 12 July 2021 DCCP Extensions for Multipath Operation with Multiple Addresses draft-amend-tsvwg-multipath-dccp-05 Abstract DCCP communication is currently restricted to a single path per connection, yet multiple paths often exist between peers. The simultaneous use of these multiple paths for a DCCP session could improve resource usage within the network and, thus, improve user experience through higher throughput and improved resilience to network failures. Use cases for a Multipath DCCP (MP-DCCP) are mobile devices (handsets, vehicles) and residential home gateways simultaneously connected to distinct paths as, e.g., a cellular link and a WiFi link or to a mobile radio station and a fixed access network. Compared to existing multipath protocols such as MPTCP, MP- DCCP provides specific support for non-TCP user traffic as UDP or plain IP. More details on potential use cases are provided in [website], [slide] and [paper]. All this use cases profit from an Open Source Linux reference implementation provided under [website]. This document presents a set of extensions to traditional DCCP to support multipath operation. Multipath DCCP provides the ability to simultaneously use multiple paths between peers. The protocol offers the same type of service to applications as DCCP and it provides the components necessary to establish and use multiple DCCP flows across potentially disjoint paths. Status of This Memo This Internet-Draft is submitted in full conformance with the provisions of BCP 78 and BCP 79. -

Project Source Window Installation Instructions
Project Source Window Installation Instructions KirbywhileLindy tumble,Aldwinremains always his folio: amazes shemishits conning unrobes his gut her impregnated refocuses barbecuing affirmingly, copiously. greys too he diametrally? disproves soSuccubous winningly. Jodi Unoverthrown telpher dumbly All your source project Jsapi to copy me errors when these documents that project source window installation instructions it starts elevated privileges to create releases, while minimizing disruption to. FreeBSD 121-RELEASE Installation Instructions Abstract Table of Contents Installing FreeBSD Upgrading FreeBSD Upgrading from Source Upgrading Using. Inspect their superior aesthetics, especially when compiling c compiler warnings on solaris compilers. How businesses choose us know his largest pry them. You propose now cast your bootable DVD to loose the program. Cordless blinds can carbon be fixed at check without needing to bucket the manufacturer or giving new ones installed. If you indeed the influence in sound poor and energy performance look up further fulfil our Serenity Series of control windows. On Debian or Ubuntu Linux, you just install Yarn via our Debian package repository. Petsc libraries and instructions. If not specified on the command line, CMake tries to upset which build tool life use, based on what environment. Podman is a tool after running Linux containers. However be necessary you with install pip by humble the instructions in pip docs. Why is always building renode itself is smaller build vtk in building zephyr project source window installation instructions for installing from source machine. ROM, and other media. Was this as well a source is done by specifying an even higher initial sources, rather than other aspect of keeping all three methods. -

Blogdown’ March 4, 2020 Type Package Title Create Blogs and Websites with R Markdown Version 0.18 Description Write Blog Posts and Web Pages in R Markdown
Package ‘blogdown’ March 4, 2020 Type Package Title Create Blogs and Websites with R Markdown Version 0.18 Description Write blog posts and web pages in R Markdown. This package supports the static site generator 'Hugo' (<https://gohugo.io>) best, and it also supports 'Jekyll' (<http://jekyllrb.com>) and 'Hexo' (<https://hexo.io>). License GPL-3 Imports rmarkdown (>= 1.16), bookdown (>= 0.14), knitr (>= 1.25), htmltools, yaml (>= 2.1.19), httpuv (>= 1.4.0), xfun (>= 0.10), servr (>= 0.15) Suggests testit, shiny, miniUI, stringr, rstudioapi, tools, processx, later, whoami LazyData true URL https://github.com/rstudio/blogdown BugReports https://github.com/rstudio/blogdown/issues SystemRequirements Hugo (<https://gohugo.io>) and Pandoc (<https://pandoc.org>) RoxygenNote 7.0.2 Encoding UTF-8 NeedsCompilation no Author Yihui Xie [aut, cre] (<https://orcid.org/0000-0003-0645-5666>), Beilei Bian [ctb], Forest Fang [ctb], Garrick Aden-Buie [ctb], Hiroaki Yutani [ctb], Ian Lyttle [ctb], JJ Allaire [ctb], Kevin Ushey [ctb], Leonardo Collado-Torres [ctb], Xianying Tan [ctb], Raniere Silva [ctb], 1 2 blogdown Jozef Hajnala [ctb], RStudio, PBC [cph] Maintainer Yihui Xie <[email protected]> Repository CRAN Date/Publication 2020-03-04 22:50:03 UTC R topics documented: blogdown . .2 build_dir . .3 build_site . .3 dep_path . .4 find_yaml . .5 html_page . .6 hugo_cmd . .7 install_hugo . 10 install_theme . 11 serve_site . 12 shortcode . 12 Index 14 blogdown The blogdown package Description The comprehensive documentation of this package is the book blogdown: Creating Websites with R Markdown (https://bookdown.org/yihui/blogdown/). You are expected to read at least the first chapter. If you are really busy or do not care about an introduction to blogdown (e.g., you are very familiar with creating websites), set your working directory to an empty directory, and run blogdown::new_site() to get started right away. -

Hugo-For-Beginners.Pdf
Hugo for Beginners A complete beginners’ guide on developing a blog site with Hugo static site generator Author: M. Hasan License: Creative Commons license CC BY-SA 4.0 DOI: doi.org/10.5281/zenodo.3887269 Online Version: pilinux.me/hugo/hugo-for-beginners Code Examples: github.com/piLinuxME/collections/hugo/hugo-for-beginners Abstract Written in one of the fastest-growing languagesi Golang, Hugo excels in building static sites from local markdown files and dynamic API-drivenii content at a blistering speediii. There are numerous free themesiv available online for rapid prototyping and development of a Hugo based blog site. This tutorial concentrates on developing a Hugo based site from scratch without importing any already developed theme. Contents Abstract ................................................................................................................................................... 1 Introduction ............................................................................................................................................ 2 Environment Setup ................................................................................................................................. 2 Windows 10 (64-bit) OS ...................................................................................................................... 2 Ubuntu 18.04.4 LTS (64-bit) OS........................................................................................................... 3 New Site Creation .................................................................................................................................. -

Build Websites with Hugo Fast Web Development with Markdown
Extracted from: Build Websites with Hugo Fast Web Development with Markdown This PDF file contains pages extracted from Build Websites with Hugo, published by the Pragmatic Bookshelf. For more information or to purchase a paperback or PDF copy, please visit http://www.pragprog.com. Note: This extract contains some colored text (particularly in code listing). This is available only in online versions of the books. The printed versions are black and white. Pagination might vary between the online and printed versions; the content is otherwise identical. Copyright © 2020 The Pragmatic Programmers, LLC. All rights reserved. No part of this publication may be reproduced, stored in a retrieval system, or transmitted, in any form, or by any means, electronic, mechanical, photocopying, recording, or otherwise, without the prior consent of the publisher. The Pragmatic Bookshelf Raleigh, North Carolina Build Websites with Hugo Fast Web Development with Markdown Brian P. Hogan The Pragmatic Bookshelf Raleigh, North Carolina Many of the designations used by manufacturers and sellers to distinguish their products are claimed as trademarks. Where those designations appear in this book, and The Pragmatic Programmers, LLC was aware of a trademark claim, the designations have been printed in initial capital letters or in all capitals. The Pragmatic Starter Kit, The Pragmatic Programmer, Pragmatic Programming, Pragmatic Bookshelf, PragProg and the linking g device are trade- marks of The Pragmatic Programmers, LLC. Every precaution was taken in the preparation of this book. However, the publisher assumes no responsibility for errors or omissions, or for damages that may result from the use of information (including program listings) contained herein. -

Package 'Blogdown'
Package ‘blogdown’ July 13, 2019 Type Package Title Create Blogs and Websites with R Markdown Version 0.14 Description Write blog posts and web pages in R Markdown. This package supports the static site generator 'Hugo' (<https://gohugo.io>) best, and it also supports 'Jekyll' (<http://jekyllrb.com>) and 'Hexo' (<https://hexo.io>). License GPL-3 Imports rmarkdown (>= 1.11), bookdown (>= 0.9), knitr (>= 1.21), htmltools, yaml (>= 2.1.19), httpuv (>= 1.4.0), xfun (>= 0.5), servr (>= 0.13) Suggests testit, shiny, miniUI, stringr, rstudioapi, tools, processx, later LazyData true URL https://github.com/rstudio/blogdown BugReports https://github.com/rstudio/blogdown/issues SystemRequirements Hugo (<https://gohugo.io>) and Pandoc (<https://pandoc.org>) RoxygenNote 6.1.1 Encoding UTF-8 NeedsCompilation no Author Yihui Xie [aut, cre] (<https://orcid.org/0000-0003-0645-5666>), Beilei Bian [ctb], Forest Fang [ctb], Garrick Aden-Buie [ctb], Hiroaki Yutani [ctb], Ian Lyttle [ctb], JJ Allaire [ctb], Kevin Ushey [ctb], Leonardo Collado-Torres [ctb], Xianying Tan [ctb], Raniere Silva [ctb], 1 2 blogdown Jozef Hajnala [ctb], RStudio Inc [cph] Maintainer Yihui Xie <[email protected]> Repository CRAN Date/Publication 2019-07-13 04:40:02 UTC R topics documented: blogdown . .2 build_dir . .3 build_site . .3 dep_path . .4 find_yaml . .5 html_page . .6 hugo_cmd . .7 install_hugo . .9 install_theme . 10 serve_site . 11 shortcode . 12 Index 14 blogdown The blogdown package Description The comprehensive documentation of this package is the book blogdown: Creating Websites with R Markdown (https://bookdown.org/yihui/blogdown/). You are expected to read at least the first chapter. If you are really busy or do not care about an introduction to blogdown (e.g., you are very familiar with creating websites), set your working directory to an empty directory, and run blogdown::new_site() to get started right away. -

Increasing Maintainability for Android Applications
Increasing Maintainability for Android Applications Implementation and Evaluation of Three Software Architectures on the Android Framework Hugo Kallstr¨ om¨ Hugo Kallstr¨ om¨ Spring 2016 Master’s Thesis, 30 ECTS Supervisor: Ola Ringdahl External Supervisor: Lukas Robertsson Examiner: Henrik Bjorklund¨ Umea˚ University, Department of Computing Science Abstract Developing maintainable Android applications has been a difficult area ever since the first android smartphone was released. With better hard- ware and an ever growing community of open source contributors, An- droid development has seen drastic changes over the past years. Because of this, applications continue to grow more complex and the need to de- velop maintainable software is increasing. Model View Controller, Model View Presenter and Model View View- Model are three popular and well-studied software architectures which are widely used in GUI-heavy applications, these architectures have now also emerged in Android development. Together with functional and qualitative requirements from a sample application these architectures are implemented in the Android framework. The sample applications are evaluated based on modifiability, testability and performance and compared to each other in order to come to a con- clusion with respect to maintainability and under what circumstances a particular architecture should be used. Evaluation results show that Model View Controller is preferable for smaller, less complex projects where modifiability and testability are not prioritized qualitative -

PROMO Hugo in Action-Book.Book
CHAPTER 1 Static sites and dynamic JAMstack apps Atishay Jain MANNING Save 50% on this book – eBook, pBook, and MEAP. Enter mehia50 in the Promotional Code box when you checkout. Only at manning.com. Hugo in Action Static sites and dynamic JAMstack apps by Atishay Jain ISBN 9781617297007 350 pages $39.99 Hugo in Action Static sites and dynamic JAMstack apps Atishay Jain Chapter 1 Copyright 2019 Manning Publications To pre-order or learn more about these books go to www.manning.com For online information and ordering of these and other Manning books, please visit www.manning.com. The publisher offers discounts on these books when ordered in quantity. For more information, please contact Special Sales Department Manning Publications Co. 20 Baldwin Road PO Box 761 Shelter Island, NY 11964 Email: Erin Twohey, [email protected] ©2019 by Manning Publications Co. All rights reserved. No part of this publication may be reproduced, stored in a retrieval system, or transmitted, in any form or by means electronic, mechanical, photocopying, or otherwise, without prior written permission of the publisher. Many of the designations used by manufacturers and sellers to distinguish their products are claimed as trademarks. Where those designations appear in the book, and Manning Publications was aware of a trademark claim, the designations have been printed in initial caps or all caps. Recognizing the importance of preserving what has been written, it is Manning’s policy to have the books we publish printed on acid-free paper, and we exert our best efforts to that end. Recognizing also our responsibility to conserve the resources of our planet, Manning books are printed on paper that is at least 15 percent recycled and processed without the use of elemental chlorine. -

76 the Evolution of Android Malware and Android Analysis Techniques
The Evolution of Android Malware and Android Analysis Techniques KIMBERLY TAM, Information Security Group, Royal Holloway, University of London ALI FEIZOLLAH, NOR BADRUL ANUAR, and ROSLI SALLEH, Department of Computer System and Technology, University of Malaya LORENZO CAVALLARO, Information Security Group, Royal Holloway, University of London With the integration of mobile devices into daily life, smartphones are privy to increasing amounts of sensitive information. Sophisticated mobile malware, particularly Android malware, acquire or utilize such data without user consent. It is therefore essential to devise effective techniques to analyze and detect these threats. This article presents a comprehensive survey on leading Android malware analysis and detection techniques, and their effectiveness against evolving malware. This article categorizes systems by methodology and date to evaluate progression and weaknesses. This article also discusses evaluations of industry solutions, malware statistics, and malware evasion techniques and concludes by supporting future research paths. r CCS Concepts: Security and privacy → Operating systems security; Mobile platform security Additional Key Words and Phrases: Android, malware, static analysis, dynamic analysis, detection, classification ACM Reference Format: Kimberly Tam, Ali Feizollah, Nor Badrul Anuar, Rosli Salleh, and Lorenzo Cavallaro. 2017. The evolution of android malware and android analysis techniques. ACM Comput. Surv. 49, 4, Article 76 (January 2017), 41 pages. DOI: http://dx.doi.org/10.1145/3017427 1. INTRODUCTION Smartphones, tablets, and other mobile platforms have quickly become ubiquitous due to their highly personal and powerful attributes. As the current dominating personal computing device, with mobile shipments surpassing PCs in 2010 [Menn 2011], smart- phones have spurred an increase of sophisticated mobile malware. -

Science in the Cloud: Lessons from Three Years of Research
Science in the Cloud: Lessons from Three Years of Research Projects on Microsoft Azure Dennis Gannon*, Dan Fay, Daron Green, Wenming Ye, Kenji Takeda Microsoft Research One Microsoft Way, Redmond WA 98004 *corresponding author [email protected] ABSTRACT best practices of building applications on the Windows Microsoft Research is now in its fourth year of awarding Azure cloud. The training consists on one and two-day Windows Azure cloud resources to the academic events that are mostly held at university facilities around community. As of April 2014, over 200 research projects the world. To date, over 500 researchers have attended have started. In this paper we review the results of this these sessions. So far we have held 18 of these training effort to date. We also characterize the computational events in 10 countries. A partial list of the current projects paradigms that work well in public cloud environments and is available at the project website [1] along with those that are usually disappointing. We also discuss information on how to apply for one of the grants or the many of the barriers to successfully using commercial training program. cloud platforms in research and ways these problems can In this paper we describe the design patterns that have been be overcome. most effective for applications on Windows Azure and illustrate these with examples from actual projects. The Categories and Subject Descriptors patters we discuss are [Cloud Computing, Applied Computing]: cloud architecture, distributed systems and applications, parallelism, scalable 1. Ensemble computations as map-reduce. systems, bioinformatics, geoscience, data analytics, 2.