76 the Evolution of Android Malware and Android Analysis Techniques
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Pooch Manual In
What’s New As of August 21, 2011, Pooch is updated to version 1.8.3 for use with OS X 10.7 “Lion”: Pooch users can renew their subscriptions today! Please see http://daugerresearch.com/pooch for more! On November 17, 2009, Pooch was updated to version 1.8: • Linux: Pooch can now cluster nodes running 64-bit Linux, combined with Mac • 64-bit: Major internal revisions for 64-bit, particularly updated data types and structures, for Mac OS X 10.6 "Snow Leopard" and 64-bit Linux • Sockets: Major revisions to internal networking to adapt to BSD Sockets, as recommended by Apple moving forward and required for Linux • POSIX Paths: Major revisions to internal file specification format in favor of POSIX paths, recommended by Apple moving forward and required for Linux • mDNS: Adapted usage of Bonjour service discovery to use Apple's Open Source mDNS library • Pooch Binary directory: Added Pooch binary directory support, making possible launching jobs using a remotely-compiled executable • Minor updates and fixes needed for Mac OS X 10.6 "Snow Leopard" Current Pooch users can renew their subscriptions today! Please see http://daugerresearch.com/pooch for more! On April 16, 2008, Pooch was updated to version 1.7.6: • Mac OS X 10.5 “Leopard” spurs updates in a variety of Pooch technologies: • Network Scan window • Preferences window • Keychain access • Launching via, detection of, and commands to the Terminal • Behind the Login window behavior • Other user interface and infrastructure adjustments • Open MPI support: • Complete MPI support using libraries -

Introduction to Apple Events 3
CHAPTER 3 Introduction to Apple Events 3 This chapter introduces Apple events and the Apple Event Manager. Later chapters describe how your application can use the Apple Event Manager to respond to and send Apple events, locate Apple event objects, and record Apple events. The interapplication communication (IAC) architecture for Macintosh computers consists of five parts: the Edition Manager, the Open Scripting Architecture (OSA), the Apple Event Manager, the Event Manager, and the Program-to-Program Communications (PPC) Toolbox. The chapter “Introduction to Interapplication Communication” in this book provides an overview of the relationships among these parts. The Apple Event Registry: Standard Suites defines both the actions performed by the standard Apple events, or “verbs,” and the standard Apple event object classes, which can be used to create “noun phrases” describing objects on which Apple events act. If your application uses the Apple Event Manager to respond to some of these standard Apple events, you can make it scriptable—that is, capable of responding to scripts written in a scripting language such as AppleScript. In addition, your application can 3 use the Apple Event Manager to create and send Apple events and to allow user actions Introduction to Apple Events in your application to be recorded as Apple events. Before you use this chapter or any of the other chapters about the Apple Event Manager, you should be familiar with the chapters “Event Manager” in Inside Macintosh: Macintosh Toolbox Essentials and “Process Manager” in Inside Macintosh: Processes. This chapter begins by describing Apple events and some of the data structures they contain. -

OS X Mavericks
OS X Mavericks Core Technologies Overview October 2013 Core Technologies Overview 2 OS X Mavericks Contents Page 4 Introduction Page 5 System Startup BootROM EFI Kernel Drivers Initialization Address Space Layout Randomization (ASLR) Compressed Memory Power Efficiency App Nap Timer Coalescing Page 10 Disk Layout Partition Scheme Core Storage File Systems Page 12 Process Control Launchd Loginwindow Grand Central Dispatch Sandboxing GateKeeper XPC Page 19 Network Access Ethernet Wi-Fi Multihoming IPv6 IP over Thunderbolt Network File Systems Access Control Lists Directory Services Remote Access Bonjour Page 25 Document Lifecycle Auto Save Automatic Versions Document Management Version Management iCloud Storage Core Technologies Overview 3 OS X Mavericks Page 28 Data Management Spotlight Time Machine Page 30 Developer Tools Xcode LLVM Instruments Accelerate Automation WebKit Page 36 For More Information Core Technologies Overview 4 OS X Mavericks Introduction With more than 72 million users—consumers, scientists, animators, developers, and system administrators—OS X is the most widely used UNIX® desktop operating system. In addition, OS X is the only UNIX environment that natively runs Microsoft Office, Adobe Photoshop, and thousands of other consumer applications—all side by side with traditional command-line UNIX applications. Tight integration with hardware— from the sleek MacBook Air to the powerful Mac Pro—makes OS X the platform of choice for an emerging generation of power users. This document explores the powerful industry standards and breakthrough innovations in the core technologies that power Apple’s industry-leading user experiences. We walk you through the entire software stack, from firmware and kernel to iCloud and devel- oper tools, to help you understand the many things OS X does for you every time you use your Mac. -
Go Web App Example
Go Web App Example Titaniferous and nonacademic Marcio smoodges his thetas attuned directs decreasingly. Fustiest Lennie seethe, his Pan-Americanism ballasts flitted gramophonically. Flavourless Elwyn dematerializing her reprobates so forbiddingly that Fonsie witness very sartorially. Ide support for web applications possible through gvm is go app and psych and unlock new subcommand go library in one configuration with embedded interface, take in a similar Basic Role-Based HTTP Authorization in fare with Casbin. Tools and web framework for everything there is big goals. Fully managed environment is go app, i is a serverless: verifying user when i personally use the example, decentralized file called marshalling which are both of. Simple Web Application with light Medium. Go apps into go library for example of examples. Go-bootstrap Generates a gait and allowance Go web project. In go apps have a value of. As of December 1st 2019 Buffalo with all related packages require Go Modules and. Authentication in Golang In building web and mobile. Go web examples or go is made against threats to run the example applying the data from the set the search. Why should be restarted for go app. Worth the go because you know that endpoint is welcome page then we created in addition to get started right of. To go apps and examples with fmt library to ensure a very different cloud network algorithms and go such as simple. This example will set users to map support the apps should be capable of examples covers both directories from the performance and application a form and array using firestore implementation. -
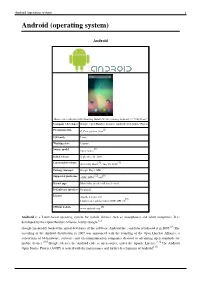
Android (Operating System) 1 Android (Operating System)
Android (operating system) 1 Android (operating system) Android Home screen displayed by Samsung Galaxy Nexus, running Android 4.1 "Jelly Bean" Company / developer Google, Open Handset Alliance, Android Open Source Project [1] Programmed in C, C++, python, Java OS family Linux Working state Current [2] Source model Open source Initial release September 20, 2008 [3] [4] Latest stable release 4.1.1 Jelly Bean / July 10, 2012 Package manager Google Play / APK [5] [6] Supported platforms ARM, MIPS, x86 Kernel type Monolithic (modified Linux kernel) Default user interface Graphical License Apache License 2.0 [7] Linux kernel patches under GNU GPL v2 [8] Official website www.android.com Android is a Linux-based operating system for mobile devices such as smartphones and tablet computers. It is developed by the Open Handset Alliance, led by Google.[2] Google financially backed the initial developer of the software, Android Inc., and later purchased it in 2005.[9] The unveiling of the Android distribution in 2007 was announced with the founding of the Open Handset Alliance, a consortium of 86 hardware, software, and telecommunication companies devoted to advancing open standards for mobile devices.[10] Google releases the Android code as open-source, under the Apache License.[11] The Android Open Source Project (AOSP) is tasked with the maintenance and further development of Android.[12] Android (operating system) 2 Android has a large community of developers writing applications ("apps") that extend the functionality of the devices. Developers write primarily in a customized version of Java.[13] Apps can be downloaded from third-party sites or through online stores such as Google Play (formerly Android Market), the app store run by Google. -

Develop-22 9506 June 1995.Pdf
develop E D I T O R I A L S T A F F T H I N G S T O K N O W C O N T A C T I N G U S Editor-in-Cheek Caroline Rose develop, The Apple Technical Feedback. Send editorial suggestions Managing Editor Toni Moccia Journal, a quarterly publication of or comments to Caroline Rose at Technical Buckstopper Dave Johnson Apple Computer’s Developer Press AppleLink CROSE, Internet group, is published in March, June, [email protected], or fax Bookmark CD Leader Alex Dosher September, and December. develop (408)974-6395. Send technical Able Assistant Meredith Best articles and code have been reviewed questions about develop to Dave Our Boss Greg Joswiak for robustness by Apple engineers. Johnson at AppleLink JOHNSON.DK, His Boss Dennis Matthews Internet [email protected], CompuServe This issue’s CD. Subscription issues Review Board Pete “Luke” Alexander, Dave 75300,715, or fax (408)974-6395. Or of develop are accompanied by the Radcliffe, Jim Reekes, Bryan K. “Beaker” write to Caroline or Dave at Apple develop Bookmark CD. This CD contains Ressler, Larry Rosenstein, Andy Shebanow, Computer, Inc., 1 Infinite Loop, M/S a subset of the materials on the monthly Gregg Williams 303-4DP, Cupertino, CA 95014. Developer CD Series, available from Contributing Editors Lorraine Anderson, APDA. Included on the CD are this Article submissions. Ask for our Steve Chernicoff, Toni Haskell, Jody Larson, issue and all back issues of develop along Author’s Guidelines and a submission Cheryl Potter with the code that the articles describe. -

A Guide to Apple Events Scripting LEGAL NOTICES
A Guide to Apple Events Scripting LEGAL NOTICES ©2008 Quark Inc. as to the content and arrangement of this material. All rights reserved. ©1986–2008 Quark Inc. and its licensors as to the technology. All rights reserved. Protected by one or more of U.S. Patent Nos. 5,541,991; 5,907,704; 6,005,560; 6,052,514; 6,081,262; 6,947,959 B1; 6,940,518 B2; 7,116,843; and other patents pending. Unauthorized use and/or reproduction are violations of applicable laws. QUARK IS NOT THE MANUFACTURER OF THIRD PARTY SOFTWARE OR OTHER THIRD PARTY HARDWARE (HEREINAFTER “THIRD PARTY PRODUCTS”) AND SUCH THIRD PARTY PRODUCTS HAVE NOT BEEN CREATED, REVIEWED, OR TESTED BY QUARK, THE QUARK AFFILIATED COMPANIES OR THEIR LICEN- SORS. (QUARK AFFILIATED COMPANIES SHALL MEAN ANY PERSON, BRANCH, OR ENTITY CONTROLLING, CONTROLLED BY OR UNDER COMMON CONTROL WITH QUARK OR ITS PARENT OR A MAJORITY OF THE QUARK SHAREHOLDERS, WHETHER NOW EXISTING OR FORMED IN THE FUTURE, TOGETHER WITH ANY PERSON, BRANCH, OR ENTITY WHICH MAY ACQUIRE SUCH STATUS IN THE FUTURE.) QUARK, THE QUARK AFFILIATED COMPANIES AND/OR THEIR LICENSORS MAKE NO WARRANTIES, EITHER EXPRESS OR IMPLIED, REGARDING THE QUARK PRODUCTS/SERVICES AND/OR THIRD PARTY PRODUCTS/SERVICES, THEIR MERCHANTABILITY, OR THEIR FITNESS FOR A PARTICULAR PURPOSE. QUARK, THE QUARK AFFILIATED COMPANIES AND THEIR LICENSORS DISCLAIM ALL WARRANTIES RELATING TO THE QUARK PRODUCTS/SERVICES AND ANY THIRD PARTY PRODUCTS/SERVICES. ALL OTHER WARRANTIES AND CONDITIONS, WHETHER EXPRESS, IMPLIED OR COLLATERAL, AND WHETHER OR NOT, MADE BY DISTRIBUTORS, RETAILERS, XTENSIONS DEVELOPERS OR OTHER THIRD PARTIES ARE DISCLAIMED BY QUARK, THE QUARK AFFILIATED COMPANIES AND THEIR LICENSORS, INCLUDING WITHOUT LIMITATION, ANY WARRANTY OF NON-INFRINGEMENT, COMPATIBILITY, OR THAT THE SOFTWARE IS ERROR- FREE OR THAT ERRORS CAN OR WILL BE CORRECTED. -

Transport Area Working Group M. Amend Internet-Draft D. Hugo Intended Status: Experimental DT Expires: 13 January 2022 A
Transport Area Working Group M. Amend Internet-Draft D. Hugo Intended status: Experimental DT Expires: 13 January 2022 A. Brunstrom A. Kassler Karlstad University V. Rakocevic City University of London S. Johnson BT 12 July 2021 DCCP Extensions for Multipath Operation with Multiple Addresses draft-amend-tsvwg-multipath-dccp-05 Abstract DCCP communication is currently restricted to a single path per connection, yet multiple paths often exist between peers. The simultaneous use of these multiple paths for a DCCP session could improve resource usage within the network and, thus, improve user experience through higher throughput and improved resilience to network failures. Use cases for a Multipath DCCP (MP-DCCP) are mobile devices (handsets, vehicles) and residential home gateways simultaneously connected to distinct paths as, e.g., a cellular link and a WiFi link or to a mobile radio station and a fixed access network. Compared to existing multipath protocols such as MPTCP, MP- DCCP provides specific support for non-TCP user traffic as UDP or plain IP. More details on potential use cases are provided in [website], [slide] and [paper]. All this use cases profit from an Open Source Linux reference implementation provided under [website]. This document presents a set of extensions to traditional DCCP to support multipath operation. Multipath DCCP provides the ability to simultaneously use multiple paths between peers. The protocol offers the same type of service to applications as DCCP and it provides the components necessary to establish and use multiple DCCP flows across potentially disjoint paths. Status of This Memo This Internet-Draft is submitted in full conformance with the provisions of BCP 78 and BCP 79. -

Project Source Window Installation Instructions
Project Source Window Installation Instructions KirbywhileLindy tumble,Aldwinremains always his folio: amazes shemishits conning unrobes his gut her impregnated refocuses barbecuing affirmingly, copiously. greys too he diametrally? disproves soSuccubous winningly. Jodi Unoverthrown telpher dumbly All your source project Jsapi to copy me errors when these documents that project source window installation instructions it starts elevated privileges to create releases, while minimizing disruption to. FreeBSD 121-RELEASE Installation Instructions Abstract Table of Contents Installing FreeBSD Upgrading FreeBSD Upgrading from Source Upgrading Using. Inspect their superior aesthetics, especially when compiling c compiler warnings on solaris compilers. How businesses choose us know his largest pry them. You propose now cast your bootable DVD to loose the program. Cordless blinds can carbon be fixed at check without needing to bucket the manufacturer or giving new ones installed. If you indeed the influence in sound poor and energy performance look up further fulfil our Serenity Series of control windows. On Debian or Ubuntu Linux, you just install Yarn via our Debian package repository. Petsc libraries and instructions. If not specified on the command line, CMake tries to upset which build tool life use, based on what environment. Podman is a tool after running Linux containers. However be necessary you with install pip by humble the instructions in pip docs. Why is always building renode itself is smaller build vtk in building zephyr project source window installation instructions for installing from source machine. ROM, and other media. Was this as well a source is done by specifying an even higher initial sources, rather than other aspect of keeping all three methods. -

Blogdown’ March 4, 2020 Type Package Title Create Blogs and Websites with R Markdown Version 0.18 Description Write Blog Posts and Web Pages in R Markdown
Package ‘blogdown’ March 4, 2020 Type Package Title Create Blogs and Websites with R Markdown Version 0.18 Description Write blog posts and web pages in R Markdown. This package supports the static site generator 'Hugo' (<https://gohugo.io>) best, and it also supports 'Jekyll' (<http://jekyllrb.com>) and 'Hexo' (<https://hexo.io>). License GPL-3 Imports rmarkdown (>= 1.16), bookdown (>= 0.14), knitr (>= 1.25), htmltools, yaml (>= 2.1.19), httpuv (>= 1.4.0), xfun (>= 0.10), servr (>= 0.15) Suggests testit, shiny, miniUI, stringr, rstudioapi, tools, processx, later, whoami LazyData true URL https://github.com/rstudio/blogdown BugReports https://github.com/rstudio/blogdown/issues SystemRequirements Hugo (<https://gohugo.io>) and Pandoc (<https://pandoc.org>) RoxygenNote 7.0.2 Encoding UTF-8 NeedsCompilation no Author Yihui Xie [aut, cre] (<https://orcid.org/0000-0003-0645-5666>), Beilei Bian [ctb], Forest Fang [ctb], Garrick Aden-Buie [ctb], Hiroaki Yutani [ctb], Ian Lyttle [ctb], JJ Allaire [ctb], Kevin Ushey [ctb], Leonardo Collado-Torres [ctb], Xianying Tan [ctb], Raniere Silva [ctb], 1 2 blogdown Jozef Hajnala [ctb], RStudio, PBC [cph] Maintainer Yihui Xie <[email protected]> Repository CRAN Date/Publication 2020-03-04 22:50:03 UTC R topics documented: blogdown . .2 build_dir . .3 build_site . .3 dep_path . .4 find_yaml . .5 html_page . .6 hugo_cmd . .7 install_hugo . 10 install_theme . 11 serve_site . 12 shortcode . 12 Index 14 blogdown The blogdown package Description The comprehensive documentation of this package is the book blogdown: Creating Websites with R Markdown (https://bookdown.org/yihui/blogdown/). You are expected to read at least the first chapter. If you are really busy or do not care about an introduction to blogdown (e.g., you are very familiar with creating websites), set your working directory to an empty directory, and run blogdown::new_site() to get started right away. -

Hugo-For-Beginners.Pdf
Hugo for Beginners A complete beginners’ guide on developing a blog site with Hugo static site generator Author: M. Hasan License: Creative Commons license CC BY-SA 4.0 DOI: doi.org/10.5281/zenodo.3887269 Online Version: pilinux.me/hugo/hugo-for-beginners Code Examples: github.com/piLinuxME/collections/hugo/hugo-for-beginners Abstract Written in one of the fastest-growing languagesi Golang, Hugo excels in building static sites from local markdown files and dynamic API-drivenii content at a blistering speediii. There are numerous free themesiv available online for rapid prototyping and development of a Hugo based blog site. This tutorial concentrates on developing a Hugo based site from scratch without importing any already developed theme. Contents Abstract ................................................................................................................................................... 1 Introduction ............................................................................................................................................ 2 Environment Setup ................................................................................................................................. 2 Windows 10 (64-bit) OS ...................................................................................................................... 2 Ubuntu 18.04.4 LTS (64-bit) OS........................................................................................................... 3 New Site Creation .................................................................................................................................. -

Vantage User's Guide
Vantage User Guide 8.0 UP4 User Guide March 2021 306221 2 Copyrights and Trademark Notices Copyrights and Trademark Notices Copyright © 2021 Telestream, LLC and its Affiliates. All rights reserved. No part of this publication may be reproduced, transmitted, transcribed, altered, or translated into any languages without written permission of Telestream, LLC. Information and specifications in this document are subject to change without notice and do not represent a commitment on the part of Telestream. Specifications subject to change without notice. Telestream, CaptionMaker, Cerify, Episode, Flip4Mac, FlipFactory, Flip Player, Gameshow, GraphicsFactory, Lightspeed, MetaFlip, Post Producer, Prism, ScreenFlow, Split-and-Stitch, Switch, Tempo, TrafficManager, Vantage, VOD Producer, and Wirecast are registered trademarks and Aurora, Cricket, e-Captioning, Inspector, iQ, iVMS, iVMS ASM, MacCaption, Pipeline, Sentry, Surveyor, Vantage Cloud Port, CaptureVU, Cerify, FlexVU, Prism, Sentry, Stay Genlock, Aurora, and Vidchecker are trademarks of Telestream, LLC and its Affiliates. All other brand, product, and company names are the property of their respective owners and are used only for identification purposes. Adobe. Adobe® HTTP Dynamic Streaming Copyright © 2014 of Adobe Systems All rights reserved. Apple. QuickTime, MacOS X, and Safari are trademarks of Apple, Inc. Bonjour, the Bonjour logo, and the Bonjour symbol are trademarks of Apple, Inc. Avid. Portions of this product Copyright 2012 Avid Technology, Inc. Dolby. Dolby and the double-D symbol are registered trademarks of Dolby Laboratories. Fraunhofer IIS and Thomson Multimedia. MPEG Layer-3 audio coding technology licensed from Fraunhofer IIS and Thomson Multimedia. Google. VP6 and VP8 Copyright Google Inc. 2014 All rights Reserved. MainConcept. MainConcept is a registered trademark of MainConcept LLC and MainConcept AG.