Framework De Aplicaciones Para Red Social Colaborativa Distribuida
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Thirty-Six More Short Essays, Plus Another, on the Probing Mind of Thomas Jefferson
THIRTY-SIX MORE SHORT ESSAYS, PLUS ANOTHER, ON THE PROBING MIND OF THOMAS JEFFERSON Author: M. Andrew Holowchak Number of Pages: 163 pages Published Date: 01 Mar 2020 Publisher: Cambridge Scholars Publishing Publication Country: Newcastle upon Tyne, United Kingdom Language: English ISBN: 9781527544840 DOWNLOAD: THIRTY-SIX MORE SHORT ESSAYS, PLUS ANOTHER, ON THE PROBING MIND OF THOMAS JEFFERSON Thirty-Six More Short Essays, Plus Another, on the Probing Mind of Thomas Jefferson PDF Book 65 PietroLucaAgostiniandRaffaellaNaggi NetworkOutcomeasTriggerfortheEvolutionofaDesign Network:CoordinationProcessesBetweenActors andObjects. Since contact with animals is commonplace all health care professionals should have an understanding of the importance, diagnosis and treatment of zoonotic infections. More than that, the technologies we adopt affect the very type of humans we become. With the chicken chapter alone, Becky demonstrates this breadth and depth of flavors with Yu Hsiang Chicken and Eggplant, Indochinese Chile Chicken, Roast Chicken with Za'atar and Yogurt Sauce, Chiles Rellenos with Pepita-Avocado Crema, and Chicken Meatballs with Garlic-Kale Marinara. com Technological Aspects of Virtual OrganizationsThis textbook was inspired by an undergraduate elective course given on virtual organizations and technology. Hydrocyclones continue to widen their appeal to engineers; besides their traditional role in mineral processing they now attract a lot of attention in chemical engineering, the oil and gas industry, power generation, the food industry, textiles, metal working, waste water treatment, pharmaceuticals, biotechnology and other industries. The authors, who are eminent in the special needs field, use up-to-date material to develop a new model for special- education in schools. The summary on the final spread allows children to compare and contrast different types of birds. -

What Is Dart?
1 Dart in Action By Chris Buckett As a language on its own, Dart might be just another language, but when you take into account the whole Dart ecosystem, Dart represents an exciting prospect in the world of web development. In this green paper based on Dart in Action, author Chris Buckett explains how Dart, with its ability to either run natively or be converted to JavaScript and coupled with HTML5 is an ideal solution for building web applications that do not need external plugins to provide all the features. You may also be interested in… What is Dart? The quick answer to the question of what Dart is that it is an open-source structured programming language for creating complex browser based web applications. You can run applications created in Dart by either using a browser that directly supports Dart code, or by converting your Dart code to JavaScript (which happens seamlessly). It is class based, optionally typed, and single threaded (but supports multiple threads through a mechanism called isolates) and has a familiar syntax. In addition to running in browsers, you can also run Dart code on the server, hosted in the Dart virtual machine. The language itself is very similar to Java, C#, and JavaScript. One of the primary goals of the Dart developers is that the language seems familiar. This is a tiny dart script: main() { #A var d = “Dart”; #B String w = “World”; #C print(“Hello ${d} ${w}”); #D } #A Single entry point function main() executes when the script is fully loaded #B Optional typing (no type specified) #C Static typing (String type specified) #D Outputs “Hello Dart World” to the browser console or stdout This script can be embedded within <script type=“application/dart”> tags and run in the Dartium experimental browser, converted to JavaScript using the Frog tool and run in all modern browsers, or saved to a .dart file and run directly on the server using the dart virtual machine executable. -

TIBCO Activematrix® BPM Web Client Developer's Guide Software Release 4.3 April 2019 2
TIBCO ActiveMatrix® BPM Web Client Developer's Guide Software Release 4.3 April 2019 2 Important Information SOME TIBCO SOFTWARE EMBEDS OR BUNDLES OTHER TIBCO SOFTWARE. USE OF SUCH EMBEDDED OR BUNDLED TIBCO SOFTWARE IS SOLELY TO ENABLE THE FUNCTIONALITY (OR PROVIDE LIMITED ADD-ON FUNCTIONALITY) OF THE LICENSED TIBCO SOFTWARE. THE EMBEDDED OR BUNDLED SOFTWARE IS NOT LICENSED TO BE USED OR ACCESSED BY ANY OTHER TIBCO SOFTWARE OR FOR ANY OTHER PURPOSE. USE OF TIBCO SOFTWARE AND THIS DOCUMENT IS SUBJECT TO THE TERMS AND CONDITIONS OF A LICENSE AGREEMENT FOUND IN EITHER A SEPARATELY EXECUTED SOFTWARE LICENSE AGREEMENT, OR, IF THERE IS NO SUCH SEPARATE AGREEMENT, THE CLICKWRAP END USER LICENSE AGREEMENT WHICH IS DISPLAYED DURING DOWNLOAD OR INSTALLATION OF THE SOFTWARE (AND WHICH IS DUPLICATED IN THE LICENSE FILE) OR IF THERE IS NO SUCH SOFTWARE LICENSE AGREEMENT OR CLICKWRAP END USER LICENSE AGREEMENT, THE LICENSE(S) LOCATED IN THE “LICENSE” FILE(S) OF THE SOFTWARE. USE OF THIS DOCUMENT IS SUBJECT TO THOSE TERMS AND CONDITIONS, AND YOUR USE HEREOF SHALL CONSTITUTE ACCEPTANCE OF AND AN AGREEMENT TO BE BOUND BY THE SAME. ANY SOFTWARE ITEM IDENTIFIED AS THIRD PARTY LIBRARY IS AVAILABLE UNDER SEPARATE SOFTWARE LICENSE TERMS AND IS NOT PART OF A TIBCO PRODUCT. AS SUCH, THESE SOFTWARE ITEMS ARE NOT COVERED BY THE TERMS OF YOUR AGREEMENT WITH TIBCO, INCLUDING ANY TERMS CONCERNING SUPPORT, MAINTENANCE, WARRANTIES, AND INDEMNITIES. DOWNLOAD AND USE OF THESE ITEMS IS SOLELY AT YOUR OWN DISCRETION AND SUBJECT TO THE LICENSE TERMS APPLICABLE TO THEM. BY PROCEEDING TO DOWNLOAD, INSTALL OR USE ANY OF THESE ITEMS, YOU ACKNOWLEDGE THE FOREGOING DISTINCTIONS BETWEEN THESE ITEMS AND TIBCO PRODUCTS. -

Attacking AJAX Web Applications Vulns 2.0 for Web 2.0
Attacking AJAX Web Applications Vulns 2.0 for Web 2.0 Alex Stamos Zane Lackey [email protected] [email protected] Blackhat Japan October 5, 2006 Information Security Partners, LLC iSECPartners.com Information Security Partners, LLC www.isecpartners.com Agenda • Introduction – Who are we? – Why care about AJAX? • How does AJAX change Web Attacks? • AJAX Background and Technologies • Attacks Against AJAX – Discovery and Method Manipulation – XSS – Cross-Site Request Forgery • Security of Popular Frameworks – Microsoft ATLAS – Google GWT –Java DWR • Q&A 2 Information Security Partners, LLC www.isecpartners.com Introduction • Who are we? – Consultants for iSEC Partners – Application security consultants and researchers – Based in San Francisco • Why listen to this talk? – New technologies are making web app security much more complicated • This is obvious to anybody who reads the paper – MySpace – Yahoo – Worming of XSS – Our Goals for what you should walk away with: • Basic understanding of AJAX and different AJAX technologies • Knowledge of how AJAX changes web attacks • In-depth knowledge on XSS and XSRF in AJAX • An opinion on whether you can trust your AJAX framework to “take care of security” 3 Information Security Partners, LLC www.isecpartners.com Shameless Plug Slide • Special Thanks to: – Scott Stender, Jesse Burns, and Brad Hill of iSEC Partners – Amit Klein and Jeremiah Grossman for doing great work in this area – Rich Cannings at Google • Books by iSECer Himanshu Dwivedi – Securing Storage – Hackers’ Challenge 3 • We are -

Google Wave Failure: Lesson Learned for Diffusion of an Online Collaboration Tool
GOOGLE WAVE FAILURE: LESSON LEARNED FOR DIFFUSION OF AN ONLINE COLLABORATION TOOL Laddawan Kaewkitipong Peter Ractham Department of Management Information Systems Thammasat Business School, Thammasat University Thailand INTRODUCTION Background and Motivation Collaboration has become increasingly important to the success of today’s enterprises. Modern organizations have been attempting to capitalize on their ability to collaborate between business units and manufacturing facilities to develop better products and services [17]. To achieve their goals, they no longer rely only on internal collaboration within their organization, but also on working closely and exchanging ideas with external partners. In other words, collaboration is viewed as a critical success factor in achieving a sustainable competitive advantage [2]. The need to collaborate is also seen in everyday’s life. A family, which has one or more family members who live abroad, might need to find a way to plan their holiday together. A group of friends who want to organize a party may need a tool to help them obtain common decisions more efficiently. As a result, many collaboration tools have been implemented to facilitate this kind of information sharing as well as decision-making tasks. Nevertheless, little has been reported on adoption success of such tools. In fact, diffusion of collaboration tools still remains as one of the most challenging problems in the area of IS research [31, 43]. Challenged by the problems and considering collaboration important activities, Google has launched many online tools to promote collaboration. Some of their popular tools are Gmail, Google Docs, and Google Calendar. An infamous tool, Google Wave, was one of the most ambitious products which many features that can help to facilitate online collaboration. -

Apachecon US 2008 with Apache Shindig
ApacheCon US 2008 Empowering the social web with Apache Shindig Henning Schmiedehausen Sr. Software Engineer – Ning, Inc. November 3 - 7 • New Orleans Leading the Wave of Open Source The Official User Conference of The Apache Software Foundation Freitag, 7. November 2008 1 • How the web became social • Get out of the Silo – Google Gadgets • OpenSocial – A social API • Apache Shindig • Customizing Shindig • Summary November 3 - 7 • New Orleans ApacheCon US 2008 Leading the Wave of Open Source The Official User Conference of The Apache Software Foundation Freitag, 7. November 2008 2 ApacheCon US 2008 In the beginning... Freitag, 7. November 2008 3 ApacheCon US 2008 ...let there be web 2.0 Freitag, 7. November 2008 4 • Web x.0 is about participation • Users have personalized logins Relations between users are graphs • "small world phenomenon", "six degrees of separation", Erdös number, Bacon number November 3 - 7 • New Orleans ApacheCon US 2008 Leading the Wave of Open Source The Official User Conference of The Apache Software Foundation Freitag, 7. November 2008 5 ApacheCon US 2008 The Silo problem Freitag, 7. November 2008 6 • How the web became social • Get out of the Silo – Google Gadgets • OpenSocial – A social API • Apache Shindig • Customizing Shindig • Summary November 3 - 7 • New Orleans ApacheCon US 2008 Leading the Wave of Open Source The Official User Conference of The Apache Software Foundation Freitag, 7. November 2008 7 ApacheCon US 2008 iGoogle Freitag, 7. November 2008 8 • Users adds Gadgets to their homepages Gadgets share screen space • Google experiments with Canvas view Javascript, HTML, CSS • A gadget runs on the Browser! Predefined Gadgets API • Core APIs for IO, JSON, Prefs; optional APIs (e.g. -

Dissecting the Evolution of the New OSN in Its First Year
Google+ or Google-? Dissecting the Evolution of the New OSN in its First Year Roberto Gonzalez, Ruben Cuevas Reza Motamedi, Reza Rejaie Universidad Carlos III de Madrid University of Oregon Leganes, Madrid, Spain Eugene, OR, US {rgonza1,rcuevas}@it.uc3m.es {motamedi,reza}@cs.uoregon.edu Angel Cuevas Telecom Sud Paris Evry, Île-de-France, France [email protected] ABSTRACT has been several official reports about the rapid growth of In the era when Facebook and Twitter dominate the market G+’s user population (400M users in Sep 2012) [1] while for social media, Google has introduced Google+ (G+) and some observers and users dismissed these claims and called reported a significant growth in its size while others called it G+ a “ghost town” [2]. This raises the following important a ghost town. This begs the question that ”whether G+ can question: “Can a new OSN such as G+ really attract a sig- really attract a significant number of connected and active nificant number of engaged users and be a relevant player users despite the dominance of Facebook and Twitter?”. in the social media market?”. A major Internet company This paper tackles the above question by presenting a de- such as Google, with many popular services, is perfectly po- tailed characterization of G+ based on large scale measure- sitioned to implicitly or explicitly require (or motivate) its ments. We identify the main components of G+ structure, current users to join its OSN. Then, it is interesting to assess characterize the key features of their users and their evolu- to what extent and how Google might have leveraged its po- tion over time. -

Creating a Simple Website
TUTORIAL Creating a Simple Website Why having a website? Table of Contents Table of Contents .................................................................................................................................... 2 Step 1: create a Google account (Gmail) ................................................................................................. 3 Step 2: create a Google website .............................................................................................................. 4 Step 3: edit a page ................................................................................................................................... 6 Add an hyperlink ................................................................................................................................. 7 Create a new page: .............................................................................................................................. 8 Add an image....................................................................................................................................... 9 Step 4: website page setting .................................................................................................................. 10 The header ......................................................................................................................................... 10 The side bar ...................................................................................................................................... -

Cliente Twitter Con Compresión De Datos
PROYECTO FIN DE GRADO GRADO EN INGENIERÍA INFROMÁTICA CLIENTE TWITTER CON COMPRESIÓN DE DATOS Autor: Plácido Fernández Declara Tutores: Luis Miguel Sánchez García Rafael Sotomayor Fernández Colmenarejo, Febrero de 2013 RESUMEN La popular red social Twitter es usada hoy en día en diversos lugares y momentos, gracias también a las redes móviles que nos proporcionan conexión a internet en casi cualquier lugar. Twitter permite publicar y mandar mensajes cortos de texto plano con un máximo de 140 caracteres, así como la lectura de estos mensajes cortos de otros usuarios a los que podemos seguir para tal propósito. Hacer uso de este servicio en zonas con buena cobertura, o cuando usamos Wi-fi no supone generalmente ningún problema. Es cuando nos encontramos en zonas de poca cobertura cuando vemos problemas para hacer uso de este servicio, ya que las velocidades de descarga pueden disminuir hasta el punto de necesitar decenas de segundos para disponer de los mensajes cortos, los “Tweets”. A esto hay que añadir que los planes de datos actuales están limitados de alguna forma (al alcanzar un número de Mb), por lo que la cantidad de Mb usada es hoy también un factor importante. Para ello esta aplicación ofrece la experiencia de un cliente Twitter sencillo en el que consultar los “Tweets” de a quien seguimos, así como publicar “Tweets”, haciendo uso de un Proxy que comprime estos datos considerablemente de forma que se reducen los tiempos de descarga para las zonas de poca cobertura y además se reduce el número de Mb consumidos por el dispositivo móvil. Índice de contenido RESUMEN ................................................................................................................................. -

Juror Misconduct in the Digital Age
GOOGLE, GADGETS, AND GUILT: JUROR MISCONDUCT IN THE DIGITAL AGE THADDEUS HOFFMEISTER* This Article begins by examining the traditional reasons for juror research. The Article then discusses how the Digital Age has created new rationales for juror research while simultaneously affording jurors greater opportunities to conduct such research. Next, the Article examines how technology has also altered juror-to-juror communications and juror-to-non-juror communications. Part I concludes by analyzing the reasons jurors violate court rules about discussing the case. In Part II, the Article explores possible steps to limit the negative impact of the Digital Age on juror research and communications. While no single solution or panacea exists for these problems, this Article focuses on several reform measures that could address and possibly reduce the detrimental effects of the Digital Age on jurors. The four remedies discussed in this Article are (1) penalizing jurors, (2) investigating jurors, (3) allowing jurors to ask questions, and (4) improving juror instructions. During the discussion on jury instructions, this Article analyzes two sets of jury instructions to see how well they adhere to the suggested changes proposed by this Article. This is followed by a draft model jury instruction. * Associate Professor of Law, University of Dayton School of Law. In addition to researching and writing on issues impacting jurors, the author edits a blog titled Juries. Prior to teaching, he served in the military, clerked for a federal judge, and worked on Capitol Hill. He earned his BA (French) from Morgan State University, JD from Northeastern University School of Law, and LLM from Georgetown University Law Center. -

Towards Secure and Reusable Web Applications
Mashups and Modularity: Towards Secure and Reusable Web Applications Antero Taivalsaari Tommi Mikkonen Sun Microsystems Laboratories [email protected] http://research.sun.com/projects/lively 2 Evolution of the Web 1) Simple pages with text and static images only (e.g., http://www.google.com) 2) Animated pages with plug-ins (e.g., http://www.cadillac.com) 3) Rich Internet Applications (e.g., docs.google.com) What's Next? 3 Web Applications – Implications • Web-based software will dramatically change the way people develop, deploy and use software. • No more installations! > Applications will simply run off the Web. • No more upgrades! > Always run the latest application version. • Instant worldwide deployment! > No middlemen or distributors needed. • No CPU dependencies, OS dependencies, ... > The Web is the Platform. 4 Unfortunately... • The web browser was not designed for running real applications. > It was designed in the early 1990s for viewing documents, forms and other page-structured artifacts – not applications. > Programming capabilities on the web were an afterthought, not something inherent in the design of the browser. • Various Rich Internet Application (RIA) technologies have been introduced recently to retrofit application execution capabilities into the web browser. 5 Web Development vs. Conventional Software The Impedance Mismatch Web Development Conventional SW Development - Documents - Applications - Page / form oriented interaction - Direct manipulation - Managed graphics, static layout - Directly drawn, dynamic -
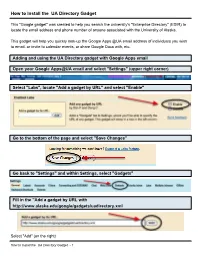
How to Install the UA Directory Gadget
How to Install the UA Directory Gadget This "Google gadget" was created to help you search the university's "Enterprise Directory" (EDIR) to locate the email address and phone number of anyone associated with the University of Alaska. This gadget will help you quickly look-up the Google Apps @UA email address of individuals you wish to email, or invite to calendar events, or share Google Docs with, etc. Adding and using the UA Directory gadget with Google Apps email Open your Google Apps@UA email and select "Settings" (upper right corner) Select "Labs", locate "Add a gadget by URL" and select "Enable" Go to the bottom of the page and select "Save Changes" Go back to "Settings" and within Settings, select "Gadgets" Fill in the "Add a gadget by URL with http://www.alaska.edu/google/gadgets/uadirectory.xml Select "Add" (on the right) How to Install the UA Directory Gadget - 1 In your Gadgets section you should see the following If you go back into your email on the left side you should now see the UA Directory Click on the "+" sign to expand the search box At this point, you have the option to authorize the gadget to access your contacts. If you decide to allow access, you will the option of adding the result from the search into your contacts - you will see "Add to Contact". This does not allow access to your account's contacts by anyone else or by any other application. If you choose to not authorize the gadget, the "Add to Contact" link will not be available in the search results.