Theoretical Computer Science
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

FUNDAMENTALS of COMPUTING (2019-20) COURSE CODE: 5023 502800CH (Grade 7 for ½ High School Credit) 502900CH (Grade 8 for ½ High School Credit)
EXPLORING COMPUTER SCIENCE NEW NAME: FUNDAMENTALS OF COMPUTING (2019-20) COURSE CODE: 5023 502800CH (grade 7 for ½ high school credit) 502900CH (grade 8 for ½ high school credit) COURSE DESCRIPTION: Fundamentals of Computing is designed to introduce students to the field of computer science through an exploration of engaging and accessible topics. Through creativity and innovation, students will use critical thinking and problem solving skills to implement projects that are relevant to students’ lives. They will create a variety of computing artifacts while collaborating in teams. Students will gain a fundamental understanding of the history and operation of computers, programming, and web design. Students will also be introduced to computing careers and will examine societal and ethical issues of computing. OBJECTIVE: Given the necessary equipment, software, supplies, and facilities, the student will be able to successfully complete the following core standards for courses that grant one unit of credit. RECOMMENDED GRADE LEVELS: 9-12 (Preference 9-10) COURSE CREDIT: 1 unit (120 hours) COMPUTER REQUIREMENTS: One computer per student with Internet access RESOURCES: See attached Resource List A. SAFETY Effective professionals know the academic subject matter, including safety as required for proficiency within their area. They will use this knowledge as needed in their role. The following accountability criteria are considered essential for students in any program of study. 1. Review school safety policies and procedures. 2. Review classroom safety rules and procedures. 3. Review safety procedures for using equipment in the classroom. 4. Identify major causes of work-related accidents in office environments. 5. Demonstrate safety skills in an office/work environment. -

Software for Numerical Computation
Purdue University Purdue e-Pubs Department of Computer Science Technical Reports Department of Computer Science 1977 Software for Numerical Computation John R. Rice Purdue University, [email protected] Report Number: 77-214 Rice, John R., "Software for Numerical Computation" (1977). Department of Computer Science Technical Reports. Paper 154. https://docs.lib.purdue.edu/cstech/154 This document has been made available through Purdue e-Pubs, a service of the Purdue University Libraries. Please contact [email protected] for additional information. SOFTWARE FOR NUMERICAL COMPUTATION John R. Rice Department of Computer Sciences Purdue University West Lafayette, IN 47907 CSD TR #214 January 1977 SOFTWARE FOR NUMERICAL COMPUTATION John R. Rice Mathematical Sciences Purdue University CSD-TR 214 January 12, 1977 Article to appear in the book: Research Directions in Software Technology. SOFTWARE FOR NUMERICAL COMPUTATION John R. Rice Mathematical Sciences Purdue University INTRODUCTION AND MOTIVATING PROBLEMS. The purpose of this article is to examine the research developments in software for numerical computation. Research and development of numerical methods is not intended to be discussed for two reasons. First, a reasonable survey of the research in numerical methods would require a book. The COSERS report [Rice et al, 1977] on Numerical Computation does such a survey in about 100 printed pages and even so the discussion of many important fields (never mind topics) is limited to a few paragraphs. Second, the present book is focused on software and thus it is natural to attempt to separate software research from numerical computation research. This, of course, is not easy as the two are intimately intertwined. -

Quantum Hypercomputation—Hype Or Computation?
Quantum Hypercomputation—Hype or Computation? Amit Hagar,∗ Alex Korolev† February 19, 2007 Abstract A recent attempt to compute a (recursion–theoretic) non–computable func- tion using the quantum adiabatic algorithm is criticized and found wanting. Quantum algorithms may outperform classical algorithms in some cases, but so far they retain the classical (recursion–theoretic) notion of computability. A speculation is then offered as to where the putative power of quantum computers may come from. ∗HPS Department, Indiana University, Bloomington, IN, 47405. [email protected] †Philosophy Department, University of BC, Vancouver, BC. [email protected] 1 1 Introduction Combining physics, mathematics and computer science, quantum computing has developed in the past two decades from a visionary idea (Feynman 1982) to one of the most exciting areas of quantum mechanics (Nielsen and Chuang 2000). The recent excitement in this lively and fashionable domain of research was triggered by Peter Shor (1994) who showed how a quantum computer could exponentially speed–up classical computation and factor numbers much more rapidly (at least in terms of the number of computational steps involved) than any known classical algorithm. Shor’s algorithm was soon followed by several other algorithms that aimed to solve combinatorial and algebraic problems, and in the last few years the- oretical study of quantum systems serving as computational devices has achieved tremendous progress. According to one authority in the field (Aharonov 1998, Abstract), we now have strong theoretical evidence that quantum computers, if built, might be used as powerful computational tool, capable of per- forming tasks which seem intractable for classical computers. -

Mathematics and Computation
Mathematics and Computation Mathematics and Computation Ideas Revolutionizing Technology and Science Avi Wigderson Princeton University Press Princeton and Oxford Copyright c 2019 by Avi Wigderson Requests for permission to reproduce material from this work should be sent to [email protected] Published by Princeton University Press, 41 William Street, Princeton, New Jersey 08540 In the United Kingdom: Princeton University Press, 6 Oxford Street, Woodstock, Oxfordshire OX20 1TR press.princeton.edu All Rights Reserved Library of Congress Control Number: 2018965993 ISBN: 978-0-691-18913-0 British Library Cataloging-in-Publication Data is available Editorial: Vickie Kearn, Lauren Bucca, and Susannah Shoemaker Production Editorial: Nathan Carr Jacket/Cover Credit: THIS INFORMATION NEEDS TO BE ADDED WHEN IT IS AVAILABLE. WE DO NOT HAVE THIS INFORMATION NOW. Production: Jacquie Poirier Publicity: Alyssa Sanford and Kathryn Stevens Copyeditor: Cyd Westmoreland This book has been composed in LATEX The publisher would like to acknowledge the author of this volume for providing the camera-ready copy from which this book was printed. Printed on acid-free paper 1 Printed in the United States of America 10 9 8 7 6 5 4 3 2 1 Dedicated to the memory of my father, Pinchas Wigderson (1921{1988), who loved people, loved puzzles, and inspired me. Ashgabat, Turkmenistan, 1943 Contents Acknowledgments 1 1 Introduction 3 1.1 On the interactions of math and computation..........................3 1.2 Computational complexity theory.................................6 1.3 The nature, purpose, and style of this book............................7 1.4 Who is this book for?........................................7 1.5 Organization of the book......................................8 1.6 Notation and conventions..................................... -

Top 10 Reasons to Major in Computing
Top 10 Reasons to Major in Computing 1. Computing is part of everything we do! Computing and computer technology are part of just about everything that touches our lives from the cars we drive, to the movies we watch, to the ways businesses and governments deal with us. Understanding different dimensions of computing is part of the necessary skill set for an educated person in the 21st century. Whether you want to be a scientist, develop the latest killer application, or just know what it really means when someone says “the computer made a mistake”, studying computing will provide you with valuable knowledge. 2. Expertise in computing enables you to solve complex, challenging problems. Computing is a discipline that offers rewarding and challenging possibilities for a wide range of people regardless of their range of interests. Computing requires and develops capabilities in solving deep, multidimensional problems requiring imagination and sensitivity to a variety of concerns. 3. Computing enables you to make a positive difference in the world. Computing drives innovation in the sciences (human genome project, AIDS vaccine research, environmental monitoring and protection just to mention a few), and also in engineering, business, entertainment and education. If you want to make a positive difference in the world, study computing. 4. Computing offers many types of lucrative careers. Computing jobs are among the highest paid and have the highest job satisfaction. Computing is very often associated with innovation, and developments in computing tend to drive it. This, in turn, is the key to national competitiveness. The possibilities for future developments are expected to be even greater than they have been in the past. -

Open Dissertation Draft Revised Final.Pdf
The Pennsylvania State University The Graduate School ICT AND STEM EDUCATION AT THE COLONIAL BORDER: A POSTCOLONIAL COMPUTING PERSPECTIVE OF INDIGENOUS CULTURAL INTEGRATION INTO ICT AND STEM OUTREACH IN BRITISH COLUMBIA A Dissertation in Information Sciences and Technology by Richard Canevez © 2020 Richard Canevez Submitted in Partial Fulfillment of the Requirements for the Degree of Doctor of Philosophy December 2020 ii The dissertation of Richard Canevez was reviewed and approved by the following: Carleen Maitland Associate Professor of Information Sciences and Technology Dissertation Advisor Chair of Committee Daniel Susser Assistant Professor of Information Sciences and Technology and Philosophy Lynette (Kvasny) Yarger Associate Professor of Information Sciences and Technology Craig Campbell Assistant Teaching Professor of Education (Lifelong Learning and Adult Education) Mary Beth Rosson Professor of Information Sciences and Technology Director of Graduate Programs iii ABSTRACT Information and communication technologies (ICTs) have achieved a global reach, particularly in social groups within the ‘Global North,’ such as those within the province of British Columbia (BC), Canada. It has produced the need for a computing workforce, and increasingly, diversity is becoming an integral aspect of that workforce. Today, educational outreach programs with ICT components that are extending education to Indigenous communities in BC are charting a new direction in crossing the cultural barrier in education by tailoring their curricula to distinct Indigenous cultures, commonly within broader science, technology, engineering, and mathematics (STEM) initiatives. These efforts require examination, as they integrate Indigenous cultural material and guidance into what has been a largely Euro-Western-centric domain of education. Postcolonial computing theory provides a lens through which this integration can be investigated, connecting technological development and education disciplines within the parallel goals of cross-cultural, cross-colonial humanitarian development. -

From Ethnomathematics to Ethnocomputing
1 Bill Babbitt, Dan Lyles, and Ron Eglash. “From Ethnomathematics to Ethnocomputing: indigenous algorithms in traditional context and contemporary simulation.” 205-220 in Alternative forms of knowing in mathematics: Celebrations of Diversity of Mathematical Practices, ed Swapna Mukhopadhyay and Wolff- Michael Roth, Rotterdam: Sense Publishers 2012. From Ethnomathematics to Ethnocomputing: indigenous algorithms in traditional context and contemporary simulation 1. Introduction Ethnomathematics faces two challenges: first, it must investigate the mathematical ideas in cultural practices that are often assumed to be unrelated to math. Second, even if we are successful in finding this previously unrecognized mathematics, applying this to children’s education may be difficult. In this essay, we will describe the use of computational media to help address both of these challenges. We refer to this approach as “ethnocomputing.” As noted by Rosa and Orey (2010), modeling is an essential tool for ethnomathematics. But when we create a model for a cultural artifact or practice, it is hard to know if we are capturing the right aspects; whether the model is accurately reflecting the mathematical ideas or practices of the artisan who made it, or imposing mathematical content external to the indigenous cognitive repertoire. If I find a village in which there is a chain hanging from posts, I can model that chain as a catenary curve. But I cannot attribute the knowledge of the catenary equation to the people who live in the village, just on the basis of that chain. Computational models are useful not only because they can simulate patterns, but also because they can provide insight into this crucial question of epistemological status. -
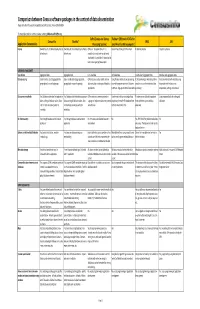
Comparison Between Census Software Packages in the Context of Data Dissemination Prepared by Devinfo Support Group (DSG) and UN Statistics Division (DESA/UNSD)
Comparison between Census software packages in the context of data dissemination Prepared by DevInfo Support Group (DSG) and UN Statistics Division (DESA/UNSD) For more information or comments please contact: [email protected] CsPro (Census and Survey Redatam (REtrieval of DATa for CensusInfo DevInfo* SPSS SAS Application Characteristics Processing System) small Areas by Microcomputer) License Owned by UN, distributed royalty-free to Owned by UN, distributed royalty-free to CSPro is in the public domain. It is Version free of charge for Download Properitery license Properitery license all end-users all end-users available at no cost and may be freely distributed. It is available for download at www.census.gov/ipc/www/cspro DATABASE MANAGEMENT Type of data Aggregated data. Aggregated data. Individual data. Individual data. Individual and aggregated data. Individual and aggregated data. Data processing Easily handles data disaggregated by Easily handles data disaggregated by CSPro lets you create, modify, and run Using Process module allows processing It allows entering primary data, define It lets you interact with your data using geographical area and subgroups. geographical area and subgroups. data entry, batch editing, and tabulation data with programs written in Redatam variables and perform statistical data integrated tools for data entry, applications command language or limited Assisstants processing computation, editing, and retrieval. Data consistency checks Yes, Database administration application Yes, Database administration -

Research; *Electronic Data Processing; Information Processing; Information Systems; *Manpower Utilization; *Personnel Data; Personnel Management; Questionnaires
DOCUMENT RESUME ED 084 382 CE 000 533 AUTHOR Bayhylle, J. E., Ed.; Hersleb, A., Ed. TITLE The Development of Electronic Data Processing in Manpower Areas; A Comparative Study of Personnel Information Systems and their Implications in Six European Countries. INSTITUTION Organisation for Economic Cooperation and Development, Paris (France) . PUB DATE 73 NOTE 366p. AVAILABLE FROMOECD Publications Center, Suite 1207, 1750 Pennsylvania Ave., N.W., Washington, DC 20006 ($8.50) EDRS PRICE MF-$0.65 HC- $13.16 DESCRIPTORS Case Studies; Data Bases; Data Processing; *Ecqnomic .Research; *Electronic Data Processing; Information Processing; Information Systems; *Manpower Utilization; *Personnel Data; Personnel Management; Questionnaires ABSTRACT Usable data about human resources in the ecqnqmy are fundamentally important, but present methods of obtaining, organizing, and using such information are increasingly unsatisfactory. The application of electronic data processing to manpower and social concerns should be improved and increased. This could stimulate closer exchange between government, institutions, and business enterprises in the collection and dissemination of manpower data. The first phase of the study was a broad-scope questionnaire of 38 companies in Austria, France, Germany, Great Britain, Sweden, and Switzerland which have developed, or are planning to develop, computer-based personnel information, systems. The second phase consisted of depth study of eight of the companies. Case study investigations were concerned with the content and function of the system and with the administrative and personnel consequences of the introduction of such systems. A set of key.points which emerged from the study is developed. A model demonstrates the need for coordination to increase communication vertically and horizontally. -

Cloud Computing and E-Commerce in Small and Medium Enterprises (SME’S): the Benefits, Challenges
International Journal of Science and Research (IJSR) ISSN (Online): 2319-7064 Cloud Computing and E-commerce in Small and Medium Enterprises (SME’s): the Benefits, Challenges Samer Jamal Abdulkader1, Abdallah Mohammad Abualkishik2 1, 2 Universiti Tenaga Nasional, College of Graduate Studies, Jalan IKRAM-UNITEN, 43000 Kajang, Selangor, Malaysia Abstract: Nowadays the term of cloud computing is become widespread. Cloud computing can solve many problems that faced by Small and medium enterprises (SME’s) in term of cost-effectiveness, security-effectiveness, availability and IT-resources (hardware, software and services). E-commerce in Small and medium enterprises (SME’s) is need to serve the customers a good services to satisfy their customers and give them good profits. These enterprises faced many issues and challenges in their business like lake of resources, security and high implementation cost and so on. This paper illustrate the literature review of the benefits can be serve by cloud computing and the issues and challenges that E-commerce Small and medium enterprises (SME’s) faced, and how cloud computing can solve these issues. This paper also presents the methodology that will be used to gather data to see how far the cloud computing has influenced the E-commerce small and medium enterprises in Jordan. Keywords: Cloud computing, E-commerce, SME’s. 1. Introduction applications, and services) that can be rapidly provisioned and released with minimal management effort or service Information technology (IT) is playing an important role in provider interaction.” [7]. From the definition of NIST there the business work way, like how to create the products, are four main services classified as cloud services which are; services to the enterprise customers [1]. -

Introduction to the Theory of Computation Computability, Complexity, and the Lambda Calculus Some Notes for CIS262
Introduction to the Theory of Computation Computability, Complexity, And the Lambda Calculus Some Notes for CIS262 Jean Gallier and Jocelyn Quaintance Department of Computer and Information Science University of Pennsylvania Philadelphia, PA 19104, USA e-mail: [email protected] c Jean Gallier Please, do not reproduce without permission of the author April 28, 2020 2 Contents Contents 3 1 RAM Programs, Turing Machines 7 1.1 Partial Functions and RAM Programs . 10 1.2 Definition of a Turing Machine . 15 1.3 Computations of Turing Machines . 17 1.4 Equivalence of RAM programs And Turing Machines . 20 1.5 Listable Languages and Computable Languages . 21 1.6 A Simple Function Not Known to be Computable . 22 1.7 The Primitive Recursive Functions . 25 1.8 Primitive Recursive Predicates . 33 1.9 The Partial Computable Functions . 35 2 Universal RAM Programs and the Halting Problem 41 2.1 Pairing Functions . 41 2.2 Equivalence of Alphabets . 48 2.3 Coding of RAM Programs; The Halting Problem . 50 2.4 Universal RAM Programs . 54 2.5 Indexing of RAM Programs . 59 2.6 Kleene's T -Predicate . 60 2.7 A Non-Computable Function; Busy Beavers . 62 3 Elementary Recursive Function Theory 67 3.1 Acceptable Indexings . 67 3.2 Undecidable Problems . 70 3.3 Reducibility and Rice's Theorem . 73 3.4 Listable (Recursively Enumerable) Sets . 76 3.5 Reducibility and Complete Sets . 82 4 The Lambda-Calculus 87 4.1 Syntax of the Lambda-Calculus . 89 4.2 β-Reduction and β-Conversion; the Church{Rosser Theorem . 94 4.3 Some Useful Combinators . -

What Is Computation? the Enduring Legacy of the Turing Machine by Lance Fortnow, Northwestern University
Ubiquity, an ACM publication December, 2010 Ubiquity Symposium What is Computation? The Enduring Legacy of the Turing Machine by Lance Fortnow, Northwestern University Editor’s Introduction In this eighth article in the ACM Ubiquity symposium discussing, What is Computation?, Lance Fortnow invokes the significance of the Turing machine in addressing the question. Editor http://ubiquity.acm.org 1 ©2010 Association for Computing Machinery Ubiquity, an ACM publication December, 2010 Ubiquity Symposium What is Computation? The Enduring Legacy of the Turing Machine by Lance Fortnow, Northwestern University Supported in part by NSF grants CCF‐0829754 and DMS‐0652521 This is one of a series of Ubiquity articles addressing the question “What is Computation?” Alan Turing1, in his seminal 1936 paper On computable numbers, with an application to the Entscheidungsproblem [4], directly answers this question by describing the now classic Turing machine model. The Church‐Turing thesis is simply stated. Everything computable is computable by a Turing machine. The Church‐Turing thesis has stood the test of time, capturing computation models Turing could not have conceived of, including digital computation, probabilistic, parallel and quantum computers and the Internet. The thesis has become accepted doctrine in computer science and the ACM has named its highest honor after Turing. Many now view computation as a fundamental part of nature, like atoms or the integers. So why are we having a series now asking a question that was settled in the 1930s? A few computer scientists nevertheless try to argue that the thesis fails to capture some aspects of computation. Some of these have been published in prestigious venues such as Science [2], the Communications of the ACM [5] and now as a whole series of papers in ACM Ubiquity.