An Edge IDS Based on Biological Immune Principles for Dynamic Threat Detection
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

A Complete Collection of Chinese Institutes and Universities For
Study in China——All China Universities All China Universities 2019.12 Please download WeChat app and follow our official account (scan QR code below or add WeChat ID: A15810086985), to start your application journey. Study in China——All China Universities Anhui 安徽 【www.studyinanhui.com】 1. Anhui University 安徽大学 http://ahu.admissions.cn 2. University of Science and Technology of China 中国科学技术大学 http://ustc.admissions.cn 3. Hefei University of Technology 合肥工业大学 http://hfut.admissions.cn 4. Anhui University of Technology 安徽工业大学 http://ahut.admissions.cn 5. Anhui University of Science and Technology 安徽理工大学 http://aust.admissions.cn 6. Anhui Engineering University 安徽工程大学 http://ahpu.admissions.cn 7. Anhui Agricultural University 安徽农业大学 http://ahau.admissions.cn 8. Anhui Medical University 安徽医科大学 http://ahmu.admissions.cn 9. Bengbu Medical College 蚌埠医学院 http://bbmc.admissions.cn 10. Wannan Medical College 皖南医学院 http://wnmc.admissions.cn 11. Anhui University of Chinese Medicine 安徽中医药大学 http://ahtcm.admissions.cn 12. Anhui Normal University 安徽师范大学 http://ahnu.admissions.cn 13. Fuyang Normal University 阜阳师范大学 http://fynu.admissions.cn 14. Anqing Teachers College 安庆师范大学 http://aqtc.admissions.cn 15. Huaibei Normal University 淮北师范大学 http://chnu.admissions.cn Please download WeChat app and follow our official account (scan QR code below or add WeChat ID: A15810086985), to start your application journey. Study in China——All China Universities 16. Huangshan University 黄山学院 http://hsu.admissions.cn 17. Western Anhui University 皖西学院 http://wxc.admissions.cn 18. Chuzhou University 滁州学院 http://chzu.admissions.cn 19. Anhui University of Finance & Economics 安徽财经大学 http://aufe.admissions.cn 20. Suzhou University 宿州学院 http://ahszu.admissions.cn 21. -

Partner Universities and Institutions List 1/ 19
Partner Universities and Institutions List (May 19, 2017) Total : 63 Countries, 506iversities & Institutions Signature Country University / Institution Agreement Level Date Afghanistan Kabul University Department Level 2014.01. Australia Curtin University University Level 2012.06. Australia Macquarie University University Level 2011.04. Australia Murdoch University University Level 2008.05. Australia Swinburne University of Technology College Level 2012.09. Australia The University of Adelaide University Level 2012.07. Australia University of New England University Level 2008.06. Australia University of the Sunshine Coast University Level 2008.01. Austria International Institute for Applied Systems Analysis (IIASA) Research Center Level 2014.07. Austria University of Applied Sciences Technikum Wien (FH Technikum Wien) University Level 2008.05. Azerbaijan Azerbaijan University of Architecture and Construction University Level 2012.01. University Level (Glocal Azerbaijan Baku State University 2007.02. Campus) Belarus Belarusian State University of Culture and Arts University Level 2007.05. Belgium Ghent University, Global Campus University Level 2016.03. Belgium Vesalius College University Level 2009.11. Brazil Mackenzie Presbyterian University University Level 2012.11. Brazil Universidade de Ribeirão Preto (UNAERP) University Level 2014.02. Brazil Universidade Estadual Paulista (UNESP) University Level 2013.05. Brazil Universidade Federal Fluminese University Level 2013.04. University Level (Glocal Cambodia Build Bright University 2012.07. Campus) University Level (Glocal Cambodia Pannasastra University 2012.03. Campus) Cambodia Royal University of Phnom Penh University Level 2011.01. Canada Centennial College University Level 2015.02. Canada Douglas College University Level 2008.03. Canada Lethbridge College University Level 2012.03. Canada McGill University Department Level 2013.12. 1/ 19 Partner Universities and Institutions List Signature Country University / Institution Agreement Level Date Graduate School Level 2007.02. -

University of Leeds Chinese Accepted Institution List 2021
University of Leeds Chinese accepted Institution List 2021 This list applies to courses in: All Engineering and Computing courses School of Mathematics School of Education School of Politics and International Studies School of Sociology and Social Policy GPA Requirements 2:1 = 75-85% 2:2 = 70-80% Please visit https://courses.leeds.ac.uk to find out which courses require a 2:1 and a 2:2. Please note: This document is to be used as a guide only. Final decisions will be made by the University of Leeds admissions teams. -

Chen Meng 512-203-4429
Chen Meng 512-203-4429 |[email protected]|https://www.linkedin.com/in/chen-meng-education-technologies/|Austin, TX SUMMARY I have 8 years of teaching English to high school students, junior college students, and undergraduates. I am now working on my Ph.D. career on the learning technologies program and doing research on Edtech-related projects in UT Austin. I know how to teach, to communicate, to deal with problems, to research, and to create in the educational technology field. I am particularly interested in making innovations in interdisciplinary fields of study and making positive changes to learning and education in my own ways. EDUCATION Phd in Learning Technologies The University of Texas at Austin Expected Graduation: 2024 MA in English Language and Literature Shandong University Graduation: 2017 BA of English Weifang University Graduation: 2006 Associate Degree of Foreign Affair Secretary University of Jinan Graduation: 2004 TEACHING/MANAGEMENT EXPERIENCE English Teacher and Educational Administrator 08/2017- 07/2019 Jinan Vocational College of Nursing, Jinan, Shandong, China Teach and coach students practical skills of college English Create, design and update course content, schedule and make collective lesson preparation Make classroom management and conduct daily teaching affairs English Teacher, IELTS speaking coach, and Educational Administrator 01/2010- 07/2017 Qilu Institute of Technology, Jinan, Shandong, China Teach and coach students practical skills of college English, bilingual translation, business English and hospitality English Design and update IELTS speaking test training program and coach students to handle speaking test skills Deal with daily educational administration including course schedule and grade management, file translation and reception of foreign universities visits. -

Dr. Ma's Curriculum Vitae
Dr. Ma's Curriculum Vitae 1. Personal Particulars Name: Professor Wen-Xiu Ma (Ph.D.) Address: Department of Mathematics and Statistics University of South Florida 4202 E Fowler Avenue, CMC 342 Tampa, FL 33620-5700, USA Phone & Fax: +1-813-974-9563 & +1-813-974-2700 Email: [email protected], [email protected], [email protected] Web page: http://www.math.usf.edu/∼mawx 2. Education Background 1978-1982: B.S., Department of Mathematics University of Science and Technology of China, Hefei, P.R. China Major: Computational Mathematics 1982-1985: M.S., Graduate School of Academia Sinica, Beijing, P.R. China Major: Applied Mathematics 1987-1990: Ph.D., Computing Center of Academia Sinica, Beijing, P.R. China Major: Mathematical Physics 3. Professional Experience 1985-1987: Assistant Professor Department of Applied Mathematics Shanghai Jiao Tong University, Shanghai, P.R. China 1990-1992: National Postdoctoral Fellow Department of Mathematics, Fudan University, Shanghai, P.R. China Research area: Integrable Systems and Soliton Theory 1992-1997: Associate Professor Institute of Mathematics, Fudan University, Shanghai, P.R. China 1992-1995: Shanghai Qi Ming Xing (Outstanding Young Research Fellow) Shanghai Government, Shanghai, P.R. China 1993-1994: Visiting Scholar Chinese University of Hong Kong, Hong Kong, P.R. China 1 1994-1996: Humboldt Research Fellow Department of Mathematics and Computer Sciences University of Paderborn, Paderborn, Germany Research area: Soliton Theory and Computer Algebra Methods 1996.6-7: Visiting Scholar Institute of Theoretic Physics, University of Montpellier II, Montpellier, France 1996-1997: Research Fellow Department of Mathematics, UMIST, Manchester, UK Research area: Classical and Quantum Integrable Systems 1997-2002: Assistant Professor Department of Mathematics, City University of Hong Kong Hong Kong, P.R. -

Monitor the Processes of Ice Film Disappearance Under a Stimulant Convection Condition and Absorption Ethanol Vapor to Ice by a Quartz Crystal Microbalance
Int. J. Electrochem. Sci., 11 (2016) 2595 - 2611 International Journal of ELECTROCHEMICAL SCIENCE www.electrochemsci.org Monitor the Processes of Ice Film Disappearance under a Stimulant Convection Condition and Absorption Ethanol Vapor to Ice by a Quartz Crystal Microbalance Lei Yu1, Xiaolong Ma2, Ting Wu2,Yangyang Ma2, Dazhong Shen, Qi Kang2,* 1Department of Chemical Engineering and Environment, Weifang University of Science and Technology, Weifang 262700, P. R. China. 2College of Chemistry, Chemical Engineering and Materials Science, Collaborative Innovation Center of Functionalized Probes for Chemical Imaging in Universities of Shandong, Key Laboratory of Molecular and Nano Probes, Ministry of Education, Shandong Provincial Key Laboratory of Clean Production of Fine Chemicals, Shandong Normal University, Jinan 250014, P. R. China. *E-mail: [email protected] doi: 10.20964/110402595 Received: 24 January 2016 / Accepted: 19 February 2016 / Published: 1 March 2016 In this work, the processes of ice film disappearance under a stimulant convection conditions and absorption to ethanol vapor to ice film were monitored by a quartz crystal microbalance (QCM) technique. The influence of the thickness of ice film on the response of the QCM was investigated by an impedance analysis method. It is shown that part of freshly prepared amorphous ice film on QCM is disappeared gradually during a stimulant convection process at -18 C. We report a mulriple resonance phenomenon in QCM with unsymmetrical mass loading. The shape of the conductance- frequency spectrum of QCM depends on the thickness and distribution of the ice film deposited. After adsorption of ethanol vapor, the rigidity of the ice film is decreased gradually. -
1 Please Read These Instructions Carefully
PLEASE READ THESE INSTRUCTIONS CAREFULLY. MISTAKES IN YOUR CSC APPLICATION COULD LEAD TO YOUR APPLICATION BEING REJECTED. Visit http://studyinchina.csc.edu.cn/#/login to CREATE AN ACCOUNT. • The online application works best with Firefox or Internet Explorer (11.0). Menu selection functions may not work with other browsers. • The online application is only available in Chinese and English. 1 • Please read this page carefully before clicking on the “Application online” tab to start your application. 2 • The Program Category is Type B. • The Agency No. matches the university you will be attending. See Appendix A for a list of the Chinese university agency numbers. • Use the + by each section to expand on that section of the form. 3 • Fill out your personal information accurately. o Make sure to have a valid passport at the time of your application. o Use the name and date of birth that are on your passport. Use the name on your passport for all correspondences with the CLIC office or Chinese institutions. o List Canadian as your Nationality, even if you have dual citizenship. Only Canadian citizens are eligible for CLIC support. o Enter the mailing address for where you want your admission documents to be sent under Permanent Address. Leave Current Address blank. Contact your home or host university coordinator to find out when you will receive your admission documents. Contact information for you home university CLIC liaison can be found here: http://clicstudyinchina.com/contact-us/ 4 • Fill out your Education and Employment History accurately. o For Highest Education enter your current degree studies. -
Detecting Spamming Stores by Analyzing Their Suspicious Behaviors
1 Detecting Spamming Stores by Analyzing Their Suspicious Behaviors Ji Chengzhang*, Dae-Ki Kang** *Weifang University of Science & Technology, Weifang 262700, China **Dongseo University, 47 Churye Ro, Sasang-Gu, Busan 617-716, Republic of Korea [email protected], [email protected] Abstract— The purpose of this paper is to detect the stores with spamming behaviors. We identify suspicious behaviors of these stores to detect spamming stores. These suspicious behaviors are from the two following observations. First, spamming stores may target quantity of sale and product reviews to influence consumers' decisions. Second, they tend to deviate from the other stores in quantity of the sale and reviews. From those observations, we propose a novel scoring methods to find spamming stores, and they are applied on AliExpress dataset. Our experiment results show that our proposed methods are effective in finding spamming stores. Keywords— Spamming behavior, spamming store, detection method Ji Chengzhang He received the B.S. degree in computer science and technology from Linyi University, Linyi, Shandong Province, China in 2005, and received the M.S. degree in computer application technology from Ocean University of China, Qingdao, Shandong Province, China in 2010. He had been working as an Assistant or Lecturer in Weifang University of Science & Technology, China from 2005 to 2015. Currently he is a doctoral candidate in machine learning at Dongseo University, Korea. His research interests include machine learning, data mining, spam review detection. Dae-Ki Kang is an Associate Professor at Dongseo University in Korea. He was a Senior Member of the Engineering Staff at the Associated Institute of Electronics & Telecommunications Research in South Korea. -

International Partner Institutions Spreadsheet (PDF)
CSU International Partnerships and Exchanges (updated May 2018) # of Yrs Start End or for Auto University or College Country Date Renewal Date Renewal Type of Relationship(s) Student Program Student Tuition, Bridge Provider Direct Student Tuition, Fees, Program Cont. Educ. for CSU Enroll Tuition & Fees & Room & Faculty Int'l to Immersion Faculty- Study Fees Room Board Exchange ACCE Student Masters at Excursion at Led Study Graduate Abroad Exchange Exchange Exchange (FE) Program Cohort CSU CSU Abroad General Studies Arab Academy of Sciemnce, Technology N/A and Maritime Transport X X X 1 (AASTMT) Egypt 2018 2023 Wales 2013 2018 N/A 2 Bangor University X Beijing Institute of China 2011 2017 5 X X X X X 3 Petrochemical Technology South Busan Global Village 2016 2021 N/A 4 Korea X Center for Bilingual Multicultural Studies, Mexico 2005 None N/A 5 Cuernavaca X X UK 2014 2019 6 Cherwell School, Oxford X South Chonnam National 2014 2019 5 7 University Korea X X X X X UK 2004 None 8 Edge Hill University X Florence University of the Italy 2015 2019 N/A 9 Arts X South Hankuk University of 2014 2021 N/A 10 Foreign Studies, Seoul Korea X X X X Germany 2012 2017 5 11 Heilbronn University X X X Kansai Gaidai University, Japan 2003 None N/A 12 Osaka X X CSU International Partnerships and Exchanges (updated May 2018) # of Yrs Start End or for Auto University or College Country Date Renewal Date Renewal Type of Relationship(s) Student Program Student Tuition, Bridge Provider Direct Student Tuition, Fees, Program Cont. -

Research on Innovation and Entrepreneurship Education System Under the New Business Background
Advances in Social Science, Education and Humanities Research, volume 336 5th International Conference on Social Science and Higher Education (ICSSHE 19) Research on Innovation and Entrepreneurship Education System under the New Business Background Zhi-xia ZHOU* Zhi-hong ZHOU Economy and Management College Accounting Faculty Weifang University Shandong Economics & Trade Vocational College Weifang, China Weifang, China Zi-yan PEI Ya-zhou LI Class 3 Grade 71 Student of Economy and Management College Student of Weifang First Middle School Weifang University Weifang, China Weifang, China Shu-mao Guo Student of Economy and Management College Weifang University Weifang, China Abstract—The thesis takes innovation and entrepreneurship reform, promote the reform and innovation of practical education system in the new business background as research teaching and personnel training mode, and also an important object, aims to cultivate college students' entrepreneurial spirit indicator to test the quality of applied talents in schools [1]. How and improve their entrepreneurial skills. It adopts the method to cultivate college students' entrepreneurial spirit and improve combining practical research and theoretical analysis, proposes their entrepreneurial skills in the "double creation" the construct strategies: implementing the goal of Ministry of environment has become a hot issue in colleges and Education's industry-university cooperation and education, universities. carrying out in-depth cooperation with enterprises to optimize the design and -
The Empirical Assessment Study on the Quality of Undergraduate Education in Shandong Province
2020 International Symposium on Education and Social Sciences (ESS 2020) The Empirical Assessment Study on the Quality of Undergraduate Education in Shandong Province Jiaming Wang a,*, Yunfei Zhang b, Yong Zhang c School of Chinese Law and Economics Management, Shengli College China University of Petroleum, Dongying Shandong, China a,*[email protected], [email protected], [email protected] Abstract. Higher education assessment has always been the focus of research by experts and scholars. Based on this, combined with the previous evaluation index system of undergraduate education quality constructed by using the index loop method, a data envelopment analysis model was constructed to conduct empirical evaluations of ordinary undergraduate colleges, private colleges, and independent colleges in Shandong Province, and visualize the results and discussion. Keywords: Data Envelopment Analysis, Undergraduate Education, Quality Assessment. 1. Introduction As for the evaluation of the quality of higher education, the most evaluations focus on output, but there is a large gap between the input of various types of universities. Insufficient investment in higher education institutions is likely to be lower. This article uses this as a starting point, combined with the indicator system that was previously constructed using the indicator loop method, from the perspective of input and output, to construct and improve the indicator system for the evaluation of educational quality in colleges and universities. References and supplements, contribute to the evaluation of the quality of higher education and improve the level. 2. Data Envelopment Analysis Data envelope analysis was proposed by A. Charnes and W. W. Copper on a linear programming model based on input and output. -
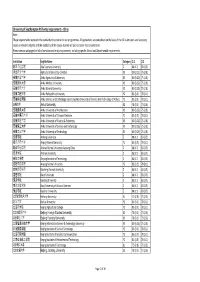
University of Southampton PGT Entry Requirements ‐ China Note: These Requirements Represent the Standard Entry Criteria for Our Programmes
University of Southampton PGT entry requirements ‐ China Note: These requirements represent the standard entry criteria for our programmes. All applications are considered on the basis of the full submission, and so strong scores in relevant subjects and the suitability of the course studied will also be taken into consideration. Please see our webpages for full information and entry requirements, including specific School and Departmental requirements. Institution English Name Category 2:1 2:2 阿坝师范学院 Aba Teachers University Z 88 (3.7) 83 (3.5) 河北农业大学 Agricultural University of Hebei X3 80 (3.25) 75 (2.8) 安徽农业大学 Anhui Agricultural University X3 80 (3.25) 75 (2.8) 安徽医科大学 Anhui Medical University X3 80 (3.25) 75 (2.8) 安徽师范大学 Anhui Normal University X3 80 (3.25) 75 (2.8) 安徽工程大学 Anhui Polytechnic University Y2 83 (3.5) 78 (3.1) 安徽科技学院 Anhui Science and Technology University (AKA University of Science And Technology of Anhui) Y2 83 (3.5) 78 (3.1) 安徽大学 Anhui University X2 78 (3.1) 73 (2.6) 安徽建筑大学 Anhui University of Architecture X3 80 (3.25) 75 (2.8) 安徽中医药大学 Anhui University of Chinese Medicine Y2 83 (3.5) 78 (3.1) 安徽财经大学 Anhui University of Finance & Economics X3 80 (3.25) 75 (2.8) 安徽理工大学 Anhui University of Science and Technology X3 80 (3.25) 75 (2.8) 安徽工业大学 Anhui University of Technology X3 80 (3.25) 75 (2.8) 安康学院 Ankang University Z 88 (3.7) 83 (3.5) 安庆师范大学 Anqing Normal University Y2 83 (3.5) 78 (3.1) 鞍山师范学院 Anshan Normal University Liaoning China Z 88 (3.7) 83 (3.5) 安顺学院 Anshun University Z 88 (3.7) 83 (3.5) 安阳工学院 Anyang Institute of Technology