(AAA) Management for Distributed IP Networks
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Raw Slides (Pdf)
2550 Intro to cybersecurity L5: Distributed Authentication abhi shelat/Ran Cohen Agenda • The problem of distributed authentication • The Needham-Schroeder protocol • Kerberos protocol • Oauth So far: authenticating to a server Mallory Alice Bob Gen pw pw Authenticating to an organization Mallory Alice Gen pw pw Authenticating to an organization Mallory Alice Gen pw pw Distributed authentication • Organizations have many entities (users/services) • Secure communication over insecure channels • Password-based authentication • Passwords are never transmitted (except for the setup phase) • Enable mutual authentication Basic tool: symmetric encryption Alice Bob 푚 푚 Eve Basic tool: symmetric encryption • Gen: generates secret key 푘 • Enc: given 푘 and 푚 output a ciphertext 푐 Denote 퐸푛푐푘 푚 , 퐸푘 푚 , 푚 푘 • Dec: given 푘 and 푐 output a message 푚 • Security (informal): Whatever Eve can learn on 푚 given 푐 can be learned without 푐 • Examples: – DES (Data Encryption Standard) – AES (Advanced Encryption Standard) 푚 Authentication from Encryption • Alice and Bob share a key • They communicate over an insecure channel • Alice wants to prove her identity to Bob • Eve’s goal: impersonate Alice Alice Bob 푘퐴퐵 푘퐴퐵 Eve Attempt #1 Alice Bob I am Alice 푘퐴퐵 푘퐴퐵 I am Alice Eve Attempt #2: use the key Alice Bob I am Alice 푘퐴퐵 푘퐴퐵 푘퐴퐵 I am Alice 푘퐴퐵 Replay attack Eve Attempt #3: use nonce Alice I am Alice Bob 푁푎 푘퐴퐵 Pay Eve 500$ 푁푎 − 1 푘퐴퐵 푘퐴퐵 푘퐴퐵 푘퐴퐵 Nonce: a random number for a one-time use Eve Attempt #3: use nonce Alice I am Alice Bob 푁푎 푘퐴퐵 Pay Eve 500$ 푁푎 − -

The Essential Oauth Primer: Understanding Oauth for Securing Cloud Apis
THE ESSENTIAL OAUTH PRIMER: UNDERSTANDING OAUTH FOR SECURING CLOUD APIS WHITE PAPER TABLE OF CONTENTS 03 EXECUTIVE OVERVIEW 03 MOTIVATING USE CASE: TRIPIT 05 TERMINOLOGY 06 INTRODUCTION 07 THE OAUTH 2.0 MODEL 07 OAUTH 2.0 OVERVIEW USING A TOKEN TOKEN TYPE 09 RELATIONSHIP TO OTHER STANDARDS 11 USE CASES TRIPIT REVISITED TOKEN EXCHANGE MOBILE WORKFORCE 13 RECENT DEVELOPMENT 14 SUMMARY 2 WHITE PAPER ESSENTIAL OAUTH PRIMER EXECUTIVE OVERVIEW A key technical underpinning of the cloud and the Internet of Things are Application Programming Interfaces (APIs). APIs provide consistent methods for outside entities such as web services, clients and desktop applications to interface with services in the cloud. More and more, cloud data will move through APIs, but the security and scalability of APIs are currently threatened by a problem call the password anti-pattern. This is the need for API clients to collect and replay the password for a user at an API in order to access information on behalf of that user via that API. OAuth 2.0 defeats the password anti-pattern, creating a consistent, flexible identity and policy architecture for web applications, web services, devices and desktop clients attempting to communicate with cloud APIs. MOTIVATING USE CASE: TRIPIT Like many applications today, TripIt (http://tripit.com) is a cloud-based service. It’s a travel planning application that allows its users to track things like flights, car rentals, and hotel stays. Users email their travel itineraries to TripIt, which then builds a coordinated view of the users’ upcoming trips (as well as those of their TripIt friends—the inevitable social aspect). -

Security on SPWF04S Module
AN4963 Application note Security on SPWF04S module Introduction The SPWF04S seriesa of Wi-Fi modules feature security functions designed to preserve confidentiality, communication integrity and authentication during wireless communication and Internet connection, on at least two levels. The first level involves communication between peers as in access to a web server. The communication data must not be read by entities other than the client and the server; the client must ensure that the peer it communicates with is authentic. This feature is provided by the Transport Layer Security (TLS) protocol, which allows client and server applications to communication that is confidential and secure. The second level involves communication between the Wi-Fi device and the Access Point. Radio communication is very easy to intercept: an attacker just needs an antenna to read transmission packets. Encryption is a key instrument in ensuring that packets cannot be read by anything other than the two peers in communication. Security at the level of Wi-Fi network is provided by WPA2-PSK when dealing with personal networks, and WPA2-Enterprise when dealing with enterprise networks. For WPA2-PSK, setting up the module for the network is facilitated by Wi-Fi protected setup (WPS). Devices that support firmware updating via Wi-Fi or firmware over-the-air (FOTA) must be able to assess the authenticity of the firmware source and the integrity of the image file after it has been received. a SPWF04Sxxx Wi-Fi module, www.st.com/wifimodules. November 2017 DocID030067 Rev 2 1/62 www.st.com Contents AN4963 Contents 1 Transport layer security (TLS) protocol overview ....................... -
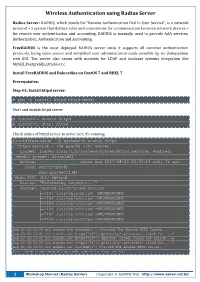
Wireless Authentication Using Radius Server
Wireless Authentication using Radius Server Radius Server: RADIUS, which stands for “Remote Authentication Dial In User Service”, is a network protocol – a system that defines rules and conventions for communication between network devices – for remote user authentication and accounting. RADIUS is normally used to provide AAA services; Authorization, Authentication and Accounting. FreeRADIUS is the most deployed RADIUS server since it supports all common authentication protocols, being open source and simplified user administration made possible by its dialupadmin web GUI. The server also comes with modules for LDAP and database systems integration like MySQL,PostgreSQL,Oracle e.t.c. Install FreeRADIUS and Daloradius on CentOS 7 and RHEL 7 Prerequisites: Step-01: Install httpd server: # yum -y install httpd httpd-devel Start and enable httpd server # systemctl enable httpd # systemctl start httpd Check status of httpd server to make sure it’s running [root@freeradius ~]# systemctl status httpd ● httpd.service - The Apache HTTP Server Loaded: loaded (/usr/lib/systemd/system/httpd.service; enabled; vendor preset: disabled) Active: active (running) since Sun 2017-08-20 02:33:03 EDT; 7s ago Docs: man:httpd(8) man:apachectl(8) Main PID: 7147 (httpd) Status: "Processing requests..." CGroup: /system.slice/httpd.service ├─7147 /usr/sbin/httpd -DFOREGROUND ├─7194 /usr/sbin/httpd -DFOREGROUND ├─7195 /usr/sbin/httpd -DFOREGROUND ├─7196 /usr/sbin/httpd -DFOREGROUND ├─7197 /usr/sbin/httpd -DFOREGROUND └─7199 /usr/sbin/httpd -DFOREGROUND Aug 20 02:33:00 ns1.mahedi.net systemd[1]: Starting The Apache HTTP Server... Aug 20 02:33:01 ns1.mahedi.net httpd[7147]: gethostby*.getanswer: asked for ..." Aug 20 02:33:01 ns1.mahedi.net httpd[7147]: AH00558: httpd: Could not reliab...e Aug 20 02:33:02 ns1.mahedi.net httpd[7147]: gethostby*.getanswer: asked for ..." Aug 20 02:33:03 ns1.mahedi.net systemd[1]: Started The Apache HTTP Server. -

OK: Oauth 2.0 Interface for the Kerberos V5 Authentication Protocol
OK: OAuth 2.0 interface for the Kerberos V5 Authentication Protocol James Max Kanter Bennett Cyphers Bruno Faviero John Peebles [email protected] [email protected] [email protected] [email protected] 1. Problem Kerberos is a powerful, convenient framework for user authentication and authorization. Within MIT, Kerberos is used with many online institute services to verify users as part of Project Athena. However, it can be difficult for developers unfamiliar with Kerberos development to take advantage of its resources for use in third-party apps. OAuth 2.0 is an open source protocol used across the web for secure delegated access to resources on a server. Designed to be developer-friendly, OAuth is the de facto standard for authenticating users across sites, and is used by services including Google, Facebook, and Twitter. Our goal with OK Server is to provide an easy way for developers to access third-party services using Kerberos via OAuth. The benefits of this are twofold: developers can rely on an external service for user identification and verification, and users only have to trust a single centralized server with their credentials. Additionally, developers can request access to a subset of Kerberos services on behalf of a user. 2. Implementation overview Our system is composed of two main components: a server (the Kerberos client) to retrieve and process tickets from the MIT KDC, and an OAuth interface (the OAuth server) to interact with a client app (the app) wishing to make use of Kerberos authentication. When using our system, a client application uses the OAuth protocol to get Kerberos service tickets for a particular user. -

Authentication, Authorization and Accounting (AAA) Protocols
Authentication, Authorization and Accounting (AAA) Protocols Agententechnologien in der Telekommunikation Sommersemester 2009 Babak Shafieian [email protected] A O T Agententechnologien in betrieblichen Anwendungen 10.06.2009 und der Telekommunikation Overview A O T Agententechnologien in der Telekommunikation - 2 TU Berlin Motivation (Why AAA?) Ö Telecommunications services are a global market worth over US$ 1.5 trillion in revenue. Home Entertainment Voice over IP (VoIP) Multimedia Conference Messaging/ Presence A O T Agententechnologien in der Telekommunikation - 3 TU Berlin Authentication (Who is [email protected]) Ö Authentication is the process of verifying user’s identity using credentials like username, password or certificates. Ö After the successful match of user’s authentication credentials with the credentials stored in the database of the service provider, the user is granted access to the network, otherwise the access is denied. A O T Agententechnologien in der Telekommunikation - 4 TU Berlin Authorization Ö Is the process of enforcing policies. It determines what types or qualities of network resources or specific services the user is permitted. Ö By using the access policy defined for a specific user, the service provider grants or rejects the access requests from the user. Ö Access policy could be applied on a per user or group basis. A O T Agententechnologien in der Telekommunikation - 5 TU Berlin Accounting Ö Is the process of keeping track of what the user is doing. Ö It includes: Amount of the time spent in the network (duration of session) Number of packets(or bytes) transmitted during a session. The accessed services during a session. -

Vmware Workspace ONE Access 20.01 Managing User Authentication Methods in Vmware Workspace ONE Access
Managing User Authentication Methods in VMware Workspace ONE Access JAN 2020 VMware Workspace ONE Access 20.01 Managing User Authentication Methods in VMware Workspace ONE Access You can find the most up-to-date technical documentation on the VMware website at: https://docs.vmware.com/ VMware, Inc. 3401 Hillview Ave. Palo Alto, CA 94304 www.vmware.com © Copyright 2020 VMware, Inc. All rights reserved. Copyright and trademark information. VMware, Inc. 2 Contents 1 Configuring Authentication in VMware Workspace ONE Access 5 2 User Auth Service Authentication Methods in Workspace ONE Access 8 Configuring Password (Cloud) Authentication in Workspace ONE Access 9 Configure Password (Cloud) Authentication with Your Enterprise Directory 10 Configuring RSA SecurID (Cloud) For Workspace ONE Access 13 Prepare the RSA SecurID Server 13 Configure RSA SecurID Authentication in Workspace ONE Access 14 Configuring RADIUS for Workspace ONE Access 16 Prepare the RADIUS Server 16 Configure RADIUS Authentication in Workspace ONE Access 16 Enable User Auth Service Debug Logs In Workspace ONE Access Connector 19 3 Configuring Kerberos Authentication In Workspace ONE Access 21 Configure and Enable Kerberos Authentication in Workspace ONE Access 21 Configuring your Browser for Kerberos 23 Configure Internet Explorer to Access the Web Interface 23 Configure Firefox to Access the Web Interface 24 Configure the Chrome Browser to Access the Web Interface 25 Kerberos Initialization Error in Workspace ONE Access 26 4 Associate Workspace ONE Access Authentication Methods -

Nist Sp 800-77 Rev. 1 Guide to Ipsec Vpns
NIST Special Publication 800-77 Revision 1 Guide to IPsec VPNs Elaine Barker Quynh Dang Sheila Frankel Karen Scarfone Paul Wouters This publication is available free of charge from: https://doi.org/10.6028/NIST.SP.800-77r1 C O M P U T E R S E C U R I T Y NIST Special Publication 800-77 Revision 1 Guide to IPsec VPNs Elaine Barker Quynh Dang Sheila Frankel* Computer Security Division Information Technology Laboratory Karen Scarfone Scarfone Cybersecurity Clifton, VA Paul Wouters Red Hat Toronto, ON, Canada *Former employee; all work for this publication was done while at NIST This publication is available free of charge from: https://doi.org/10.6028/NIST.SP.800-77r1 June 2020 U.S. Department of Commerce Wilbur L. Ross, Jr., Secretary National Institute of Standards and Technology Walter Copan, NIST Director and Under Secretary of Commerce for Standards and Technology Authority This publication has been developed by NIST in accordance with its statutory responsibilities under the Federal Information Security Modernization Act (FISMA) of 2014, 44 U.S.C. § 3551 et seq., Public Law (P.L.) 113-283. NIST is responsible for developing information security standards and guidelines, including minimum requirements for federal information systems, but such standards and guidelines shall not apply to national security systems without the express approval of appropriate federal officials exercising policy authority over such systems. This guideline is consistent with the requirements of the Office of Management and Budget (OMB) Circular A-130. Nothing in this publication should be taken to contradict the standards and guidelines made mandatory and binding on federal agencies by the Secretary of Commerce under statutory authority. -

Operations T. Dahm Internet-Draft A. Ota Intended Status: Informational Google Inc Expires: July 30, 2020 D
Operations T. Dahm Internet-Draft A. Ota Intended status: Informational Google Inc Expires: July 30, 2020 D. Medway Gash Cisco Systems, Inc. D. Carrel vIPtela, Inc. L. Grant January 27, 2020 The TACACS+ Protocol draft-ietf-opsawg-tacacs-17 Abstract This document describes the Terminal Access Controller Access-Control System Plus (TACACS+) protocol which is widely deployed today to provide Device Administration for routers, network access servers and other networked computing devices via one or more centralized servers. Status of This Memo This Internet-Draft is submitted in full conformance with the provisions of BCP 78 and BCP 79. Internet-Drafts are working documents of the Internet Engineering Task Force (IETF). Note that other groups may also distribute working documents as Internet-Drafts. The list of current Internet- Drafts is at https://datatracker.ietf.org/drafts/current/. Internet-Drafts are draft documents valid for a maximum of six months and may be updated, replaced, or obsoleted by other documents at any time. It is inappropriate to use Internet-Drafts as reference material or to cite them other than as "work in progress." This Internet-Draft will expire on July 30, 2020. Copyright Notice Copyright (c) 2020 IETF Trust and the persons identified as the document authors. All rights reserved. This document is subject to BCP 78 and the IETF Trust's Legal Provisions Relating to IETF Documents (https://trustee.ietf.org/license-info) in effect on the date of publication of this document. Please review these documents Dahm, et al. Expires July 30, 2020 [Page 1] Internet-Draft The TACACS+ Protocol January 2020 carefully, as they describe your rights and restrictions with respect to this document. -

Cisco Products Quick Reference Guide December 2004
Cisco SYSTEMS pII Cisco Product Quick Reference Guide December 2004 Table of Contents Introduction Routing Switching Wireless LAN Voice and IP Communications VPN and Security Content Networking Broadband and Dial Access Optical Networking lOS Software and Network Management 10 Storage Networking Cicro SYsTEr Cisco Products Quick Reference Guide December 2004 Corporate Headquarters Cisco Systems Inc 170 West Tasman Drive San Jose CA 951 34-1706 USA http//wvvw.cisco.com Tel 408 526-4000 800 553-NETS 6387 Customer Order Number 78-5983-13 Text Part Number 78-5983-13 Gisco Products Quick Reference Guide Copyright 2005 Cisco Systems Inc All rights reserved Gener Discbimer Although Cisco has attempted to provide accurate information in this Guide Cisco assumes no responsibility for the accuracy of the information Cisco may change the programs or products mentioned at any time without prior notice Mention of non-Cisco products or services is for information purposes only and constitutes neither an endorsement nor recommendation of such products or services or of any company that develops or sells such products or services ALL INFORMATION PROVIDED ON THIS WEB SITE IS PROVIDED AS IS WITH ALL FAULTS AND WITHOUT WARRANTY OF ANY KIND EITHER EXPRESSED OR IMPLIED CISCO AND ITS SUPPLIERS DISCLAIM ALL WARRANTIES EXPRESSED OR IMPLIED INCLUDING WITHOUT LIMITATION THOSE OF MERCHANTABILITY FITNESS FOR PARTICULAR PURPOSE AND NONINFRJNGEMENT OR ARISING FROM COURSE OF DEALING USAGE OR TRADE PRACTICE CISCO AND ITS SUPPLIERS SHALL NOT BE LIABLE FOR ANY INDIRECT -

Cloudvision As-A-Service (Cvaas) Quick Start Guide
CloudVision as-a-Service (CVaaS) Quick Start Guide Arista Networks www.arista.com September 2021 Headquarters Support Sales 5453 Great America Parkway +1 408 547-5502 +1 408 547-5501 Santa Clara, CA 95054 +1 866 476-0000 +1 866 497-0000 USA [email protected] [email protected] +1 408 547-5500 www.arista.com © Copyright 2021 Arista Networks, Inc. All rights reserved. The information contained herein is subject to change without notice. The trademarks, logos and service marks ("Marks") displayed in this documentation are the property of Arista Networks in the United States and other countries. Use of the Marks are subject to Arista Network’s Term of Use Policy, available at www.arista.com/en/terms-of-use. Use of marks belonging to other parties is for informational purposes only. ii Contents Contents 1 CloudVision as-a-Service....................................................................1 1.1 Onboarding at a Glance.........................................................................................................1 1.2 User Onboarding Prerequisites.............................................................................................. 3 1.2.1 Invitation URL........................................................................................................... 3 1.2.2 Authentication Details............................................................................................... 3 1.3 User Onboarding Workflow.................................................................................................... 4 1.3.1 -

Cost Effective RADIUS Authentication for Wireless Clients
Database Systems Journal vol. I, no. 2/2010 27 Cost Effective RADIUS Authentication for Wireless Clients Alexandru ENACEANU Faculty of Computer Science, Romanian-American University, Bucharest, Romania [email protected] Gabriel GARAIS Faculty of Computer Science, Romanian-American University, Bucharest, Romania Network administrators need to keep administrative user information for each network device, but network devices usually support only limited functions for user management. WLAN security is a modern problem that needs to be solved and it requires a lot of overhead especially when applied to corporate wireless networks. Administrators can set up a RADIUS server that uses an external database server to handle authentication, authorization, and accounting for network security issues. Keywords: RADIUS, WLAN, Wireless Authentication, Wireless Access Control totally inadequate for a corporate wireless or Introduction Corporate wireless a campus network. That is because a 1 networks are in general the primary corporate wireless network has a lot of source of hacking into the corporate access points to reconfigure for changing the systems. The risks to users of wireless access key or adding a new MAC address to technology have increased lately, as the the allowed clients list. service has become more popular. There WLAN security can be significantly were relatively few dangers when wireless strengthened by using 802.1X to control technology was first introduced. Crackers access point access and deliver dynamic had not yet had time to latch on to the new keys to authenticated users. Authentication technology and wireless was not commonly Servers based on the RADIUS protocol play found in the work place.