Nolink Leftbehind
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
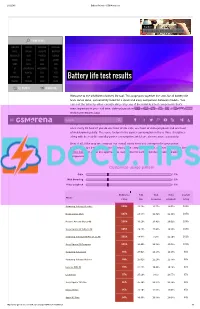
Battery Life Test Results HUAWEI TOSHIBA INTEX PLUM
2/12/2015 Battery life tests GSMArena.com Starborn SAMSUNG GALAXY S6 EDGE+ REVIEW PHONE FINDER SAMSUNG LENOVO VODAFONE VERYKOOL APPLE XIAOMI GIGABYTE MAXWEST MICROSOFT ACER PANTECH CELKON NOKIA ASUS XOLO GIONEE SONY OPPO LAVA VIVO LG BLACKBERRY MICROMAX NIU HTC ALCATEL BLU YEZZ MOTOROLA ZTE SPICE PARLA Battery life test results HUAWEI TOSHIBA INTEX PLUM ALL BRANDS RUMOR MILL Welcome to the GSMArena battery life tool. This page puts together the stats for all battery life tests we've done, conveniently listed for a quick and easy comparison between models. You can sort the table by either overall rating or by any of the individual test components that's most important to you call time, video playback or web browsing.TIP US 828K 100K You can find all about our84K 137K RSS LOG IN SIGN UP testing procedures here. SearchOur overall rating gives you an idea of how much battery backup you can get on a single charge. An overall rating of 40h means that you'll need to fully charge the device in question once every 40 hours if you do one hour of 3G calls, one hour of video playback and one hour of web browsing daily. The score factors in the power consumption in these three disciplines along with the reallife standby power consumption, which we also measure separately. Best of all, if the way we compute our overall rating does not correspond to your usage pattern, you are free to adjust the different usage components to get a closer match. Use the sliders below to adjust the approximate usage time for each of the three battery draining components. -

Response Data 910 14
Count of Type Desc. Total [40 (DUMMY) DISPLAY PHONES] 1 [BLACKBERRY] 2 [CHARGER] 1 [COVERS] 1 [FLIPTOP PHONE] 1 [HC1] 1 [HDCI M8 MOBILE PHONE] 1 [HUAWEI] 1 [I PHONE 4] 2 [I PHONE 5] 2 [I PHONE 5C] 1 [I PHONE 5S] 1 [I PHONE] 1 [IPHONE 5 WHITE IN COLOUR] 1 [IPHONE 5S] 1 [IPHONE 6] 1 [IPHONE CHARGER] 2 [IPHONE CHARGERS] 1 [IPHONE PHONE CHARGER] 1 [IPHONE] 2 [MOBILE PHONE AND CHARGED] 1 [MOBILE PHONE BATTERY] 1 [MOBILE PHONE CASE] 1 [MOBILE PHONE FOR SENIOR] 1 [MOBILE PHONE] 16 [MOBILE TELEPHONE - UNKNOWN DETAILS] 1 [MOBILE TELEPHONE] 4 [MOTOROLA] 1 [NOKIA LUMINA 530 MOBILE PHONE] 1 [NOKIA MOBILE] 1 [PHONE CHARGER] 1 [PHONE SIM CARD] 1 [SAMSUNG GALAXY S3 MINI] 1 [SAMSUNG] 1 [SIM CARD] 2 [SMART PHONE] 1 [SONY XPERIA Z1] 1 [SONY XPERIA Z2] 1 [TABLET] 1 [TELEPHONE CABLE] 1 [TESCO MOBILE PHONE] 1 [TESCO] 1 [UNKNOWN MAKE OF MOBILE PHONE] 1 [WORKS AND PERSONAL] 1 1PHONE 4S 1 3 [3 SIM CARD] 1 3G 1 4 [I PHONE] 1 4S 1 ACCESSORIES [CHARGER AND PHONE COVER] 1 ACER 2 ACER LIQUID 1 ACER LIQUID 3 1 ACER LIQUID 4Z [MOBILE TELEPHONE] 1 ACER LIQUID E 1 ACER LIQUID E2 1 ACER LIQUID E3 1 ACTEL [MOBILE PHONE] 1 ALCATEL 6 ALCATEL [MOBILE PHONE] 3 ALCATEL ITOUCH [ALCATEL ITOUCH] 1 ALCATEL ONE 232 1 ALCATEL ONE TOUCH 6 ALCATEL ONE TOUCH [TRIBE 30GB] 1 ALCATEL ONE TOUCH TRIBE 3040 1 ALCATELL 1 ANDROID [TABLET] 1 APHONE 5 1 APLE IPHONE 5C 1 APLLE I PHONE 5S 2 APLLE IPHONE 4 1 APPL I PHONE 4 1 APPLE 11 APPLE [I PHONE] 1 APPLE [IPHONE] 1 APPLE [MOBILE PHONE CHARGER] 1 APPLE 1 PHONE 4 1 APPLE 1 PHONE 5 1 APPLE 1 PHONE 5 [I PHONE] 1 APPLE 3GS [3GS] 1 APPLE 4 3 APPLE 4 -
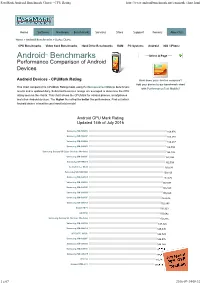
Passmark Android Benchmark Charts - CPU Rating
PassMark Android Benchmark Charts - CPU Rating http://www.androidbenchmark.net/cpumark_chart.html Home Software Hardware Benchmarks Services Store Support Forums About Us Home » Android Benchmarks » Device Charts CPU Benchmarks Video Card Benchmarks Hard Drive Benchmarks RAM PC Systems Android iOS / iPhone Android TM Benchmarks ----Select A Page ---- Performance Comparison of Android Devices Android Devices - CPUMark Rating How does your device compare? Add your device to our benchmark chart This chart compares the CPUMark Rating made using PerformanceTest Mobile benchmark with PerformanceTest Mobile ! results and is updated daily. Submitted baselines ratings are averaged to determine the CPU rating seen on the charts. This chart shows the CPUMark for various phones, smartphones and other Android devices. The higher the rating the better the performance. Find out which Android device is best for your hand held needs! Android CPU Mark Rating Updated 14th of July 2016 Samsung SM-N920V 166,976 Samsung SM-N920P 166,588 Samsung SM-G890A 166,237 Samsung SM-G928V 164,894 Samsung Galaxy S6 Edge (Various Models) 164,146 Samsung SM-G930F 162,994 Samsung SM-N920T 162,504 Lemobile Le X620 159,530 Samsung SM-N920W8 159,160 Samsung SM-G930T 157,472 Samsung SM-G930V 157,097 Samsung SM-G935P 156,823 Samsung SM-G930A 155,820 Samsung SM-G935F 153,636 Samsung SM-G935T 152,845 Xiaomi MI 5 150,923 LG H850 150,642 Samsung Galaxy S6 (Various Models) 150,316 Samsung SM-G935A 147,826 Samsung SM-G891A 145,095 HTC HTC_M10h 144,729 Samsung SM-G928F 144,576 Samsung -

Electronic 3D Models Catalogue (On July 26, 2019)
Electronic 3D models Catalogue (on July 26, 2019) Acer 001 Acer Iconia Tab A510 002 Acer Liquid Z5 003 Acer Liquid S2 Red 004 Acer Liquid S2 Black 005 Acer Iconia Tab A3 White 006 Acer Iconia Tab A1-810 White 007 Acer Iconia W4 008 Acer Liquid E3 Black 009 Acer Liquid E3 Silver 010 Acer Iconia B1-720 Iron Gray 011 Acer Iconia B1-720 Red 012 Acer Iconia B1-720 White 013 Acer Liquid Z3 Rock Black 014 Acer Liquid Z3 Classic White 015 Acer Iconia One 7 B1-730 Black 016 Acer Iconia One 7 B1-730 Red 017 Acer Iconia One 7 B1-730 Yellow 018 Acer Iconia One 7 B1-730 Green 019 Acer Iconia One 7 B1-730 Pink 020 Acer Iconia One 7 B1-730 Orange 021 Acer Iconia One 7 B1-730 Purple 022 Acer Iconia One 7 B1-730 White 023 Acer Iconia One 7 B1-730 Blue 024 Acer Iconia One 7 B1-730 Cyan 025 Acer Aspire Switch 10 026 Acer Iconia Tab A1-810 Red 027 Acer Iconia Tab A1-810 Black 028 Acer Iconia A1-830 White 029 Acer Liquid Z4 White 030 Acer Liquid Z4 Black 031 Acer Liquid Z200 Essential White 032 Acer Liquid Z200 Titanium Black 033 Acer Liquid Z200 Fragrant Pink 034 Acer Liquid Z200 Sky Blue 035 Acer Liquid Z200 Sunshine Yellow 036 Acer Liquid Jade Black 037 Acer Liquid Jade Green 038 Acer Liquid Jade White 039 Acer Liquid Z500 Sandy Silver 040 Acer Liquid Z500 Aquamarine Green 041 Acer Liquid Z500 Titanium Black 042 Acer Iconia Tab 7 (A1-713) 043 Acer Iconia Tab 7 (A1-713HD) 044 Acer Liquid E700 Burgundy Red 045 Acer Liquid E700 Titan Black 046 Acer Iconia Tab 8 047 Acer Liquid X1 Graphite Black 048 Acer Liquid X1 Wine Red 049 Acer Iconia Tab 8 W 050 Acer -

Phone Compatibility
Phone Compatibility • Compatible with iPhone models 4S and above using iOS versions 7 or higher. Last Updated: February 14, 2017 • Compatible with phone models using Android versions 4.1 (Jelly Bean) or higher, and that have the following four sensors: Accelerometer, Gyroscope, Magnetometer, GPS/Location Services. • Phone compatibility information is provided by phone manufacturers and third-party sources. While every attempt is made to ensure the accuracy of this information, this list should only be used as a guide. As phones are consistently introduced to market, this list may not be all inclusive and will be updated as new information is received. Please check your phone for the required sensors and operating system. Brand Phone Compatible Non-Compatible Acer Acer Iconia Talk S • Acer Acer Jade Primo • Acer Acer Liquid E3 • Acer Acer Liquid E600 • Acer Acer Liquid E700 • Acer Acer Liquid Jade • Acer Acer Liquid Jade 2 • Acer Acer Liquid Jade Primo • Acer Acer Liquid Jade S • Acer Acer Liquid Jade Z • Acer Acer Liquid M220 • Acer Acer Liquid S1 • Acer Acer Liquid S2 • Acer Acer Liquid X1 • Acer Acer Liquid X2 • Acer Acer Liquid Z200 • Acer Acer Liquid Z220 • Acer Acer Liquid Z3 • Acer Acer Liquid Z4 • Acer Acer Liquid Z410 • Acer Acer Liquid Z5 • Acer Acer Liquid Z500 • Acer Acer Liquid Z520 • Acer Acer Liquid Z6 • Acer Acer Liquid Z6 Plus • Acer Acer Liquid Zest • Acer Acer Liquid Zest Plus • Acer Acer Predator 8 • Alcatel Alcatel Fierce • Alcatel Alcatel Fierce 4 • Alcatel Alcatel Flash Plus 2 • Alcatel Alcatel Go Play • Alcatel Alcatel Idol 4 • Alcatel Alcatel Idol 4s • Alcatel Alcatel One Touch Fire C • Alcatel Alcatel One Touch Fire E • Alcatel Alcatel One Touch Fire S • 1 Phone Compatibility • Compatible with iPhone models 4S and above using iOS versions 7 or higher. -

Fnac Reprise
FNAC REPRISE Liste des smartphones éligibles au programme de reprise au 19/08/2016 ACER LIQUID Z4 APPLE IPHONE 5 BLACK 64GB ACER INCORPORATED LIQUID Z530S APPLE IPHONE 5 WHITE 16GB ACER INCORPORATED LIQUID Z630S APPLE IPHONE 5 WHITE 32GB ALBA ALBA 4.5INCH 5MP 4G 8GB APPLE IPHONE 5 WHITE 64GB ALBA DUAL SIM APPLE IPHONE 5C ALCATEL IDOL 3 8GB APPLE IPHONE 5C BLUE 16GB ALCATEL ONE TOUCH 228 APPLE IPHONE 5C BLUE 32GB ALCATEL ONE TOUCH 903 APPLE IPHONE 5C BLUE 8GB ALCATEL ONE TOUCH 903X APPLE IPHONE 5C GREEN 16GB ALCATEL ONE TOUCH IDOL 2 MINI S APPLE IPHONE 5C GREEN 32GB ALCATEL ONE TOUCH TPOP APPLE IPHONE 5C GREEN 8GB ALCATEL ONETOUCH POP C3 APPLE IPHONE 5C PINK 16GB AMAZON FIRE PHONE APPLE IPHONE 5C PINK 32GB APPLE APPLE WATCH EDITION 42MM APPLE IPHONE 5C PINK 8GB APPLE IPHONE 3G APPLE IPHONE 5C WHITE 16GB APPLE IPHONE 3G BLACK 16GB APPLE IPHONE 5C WHITE 32GB APPLE IPHONE 3G BLACK 8GB APPLE IPHONE 5C WHITE 8GB APPLE IPHONE 3G WHITE 16GB APPLE IPHONE 5C YELLOW 16GB APPLE IPHONE 3GS APPLE IPHONE 5C YELLOW 32GB APPLE IPHONE 3GS 8GB APPLE IPHONE 5C YELLOW 8GB APPLE IPHONE 3GS BLACK 16GB APPLE IPHONE 5S APPLE IPHONE 3GS BLACK 32GB APPLE IPHONE 5S BLACK 16GB APPLE IPHONE 3GS WHITE 16GB APPLE IPHONE 5S BLACK 32GB APPLE IPHONE 3GS WHITE 32GB APPLE IPHONE 5S BLACK 64GB APPLE IPHONE 4 APPLE IPHONE 5S GOLD 16GB APPLE IPHONE 4 BLACK 16GB APPLE IPHONE 5S GOLD 32GB APPLE IPHONE 4 BLACK 32GB APPLE IPHONE 5S GOLD 64GB APPLE IPHONE 4 BLACK 8GB APPLE IPHONE 5S WHITE 16GB APPLE IPHONE 4 WHITE 16GB APPLE IPHONE 5S WHITE 32GB APPLE IPHONE 4 WHITE 32GB APPLE IPHONE -

Mobilní Tefony S OTG - USB Host Aktuální, Nám Známý Seznam Mobilních Telefonů K 2.2.2016
Mobilní tefony s OTG - USB Host Aktuální, nám známý seznam mobilních telefonů k 2.2.2016 Seznam mobilních telefonů Poznámka Accer Iconia Tab A200 Accer Iconia Tab A210 Accer Iconia Tab A3 Acer Liquid Z630 16GB LTE Alcatel One Touch Evo 8HD Allview C6 Allview P4 LIFE Dual SIM Allview P6 Energy Dual SIM Allview V1 VIPER S4G Dual SIM Allview W1 S Dual SIM Allview X2 SOUL Extreme Dual SIM Allview X2 SOUL Pro Dual SIM Asus Transformer Pad TF103C ASUS ZenFone 2 ZE551ML 32GB Glamor Dual SIM ASUS ZenFone 2 ZE551ML 32GB Osmium Dual SIM EVOLVEO StrongPhone Q6 LTE EVOLVEO StrongPhone Q8 LTE černý Gionee Elife E7 Gionee Elife S5.5 HTC Butterfly HTC Butterfly S HTC Desire 500 HTC Desire 600 HTC Desire 601 HTC Desire 700 HTC Desire 700 Dual Sim HTC Desire U HTC Desire X HTC HTC J HTC One HTC One (M8) CDMA HTC One (M8) Dual Sim HTC One M8 HTC One M8 Prima HTC One Max HTC One Mini HTC One X HTC One X+ Huawei Ascend D quad Huawei Ascend D1 Huawei Ascend D1 XL U9500E Huawei Ascend G7 Huawei Ascend Honor 3 Huawei Ascend Mate2 4G Huawei Ascend Mate7 Huawei Ascend P1 Huawei Ascend P6 Huawei Ascend P6 S Huawei Ascend P7 mini Huawei Ascend P7 Sapphire Edition 145 Huawei Ascend P7 Huawei MediaPad Huawei MediaPad 7 Lite Huawei MediaPad S7-301w HUAWEI P8 iGET Blackview Alife P1 G Dual SIM iGET Blackview Alife P1 Pro Dual SIM iGET Blackview BV5000 Dual SIM BlackBerry Z30 Lava Lris Pro 30+ Lenovo A6010 Lenovo IdeaTab A1000 Lenovo IdeaTab A3000 Lenovo IdeaTab S5000 Lenovo IdeaTab S6000 Lenovo IdeaTab S6000F Lenovo IdeaTab S6000H Lenovo IdeaTab S6000L Lenovo Lenovo -

Boldbeast Call Recorder 9.1 Pro Apk
Boldbeast call recorder 9.1 pro apk Continue Call Recorder - Boldbeast Size: 2.95 MB Version: 9.1 File Type: APK System: Android 2.3 or above Description : Two reasons you need this app - you need a real business level call registrar, secure, clean, stable. You need high-quality records. Call recording features - Boldbeast apps: - Recording a phone call. Recording voice memos, meetings, lectures, etc. - Record management - search, playback, browsing, deletion, sending, backup, etc. Features Call Recorder - Boldbeast Mod : - All unlocked Installation Instructions: - Have you visited this site on your mobile phone? 1. Download the Apk file on your mobile phone. 2. Set and run it. 3. That's it, Enjoy! Have you visited this site on your desktop or laptop? 1. Download the Apk file on Pc. 2. Transfer the Apk file from PC to Android Phone (Via USB, Bluetooth, Wi-Fi). 3. Install and run it. 4. That's it, Enjoy! We provide call recorder (No Advertising) 13.7 APKs file for Android 4.1 and up. Call Recorder (No Advertising) is a free Tools app. It's easy to download and install on your cell phone. Please note that ApkPlz only share the original and free clean APK installer for Call Recorder (No Advertising) 13.7 APKs without any changes. The average score is 3.10 out of 5 stars in the playstore. If you want to know more about Call Recorder (No Advertising), you can visit the Boldbeast Software Support Center for more information All apps and games here only for home or personal use. If any download apk infringes your copyright, please contact us. -
Ваш HTC Desire 600 Dual Sim Расширенное Руководство Пользователя 2 Содержание Содержание
Ваш HTC Desire 600 dual sim Расширенное руководство пользователя 2 Содержание Содержание Распаковка HTC Desire 600 7 Задняя крышка 8 Две SIM-карты 10 Карта памяти 11 Аккумулятор 12 Включение и выключение питания 14 Хотите несколько быстрых рекомендаций по использованию вашего телефона? 15 Настройка телефона Первоначальная настройка нового телефона 16 Передача содержимого из телефона на базе Android 17 Передача содержимого из iPhone 19 Передача содержимого со старого телефона по Bluetooth 19 Передача контактов и другого содержимого в HTC Desire 600 20 Передача фотоснимков, видеозаписей и музыки между телефоном и компьютером 20 Начальный экран 21 Знакомство с настройками 21 Обновление программного обеспечения HTC Desire 600 22 Ваша первая неделя с новым телефоном Сведения о телефоне 23 Основные сведения о телефоне 25 Каналы Начального экрана 33 Уведомления 35 Работа с текстом 37 Аккумулятор 42 Камера и Галерея Камера 46 Галерея 51 Индивидуальная настройка Сделайте HTC Desire 600 по-настоящему вашим 59 Изменение фонового рисунка 59 Добавление виджета на Начальный экран 59 Добавление приложений и других ярлыков на Начальный экран 61 Переупорядочивание или удаление виджетов и значков на Начальном экране 61 Индивидуальная настройка панели запуска 62 Группирование приложений в папку 63 3 Содержание Добавление панели Начального экрана 64 Изменение мелодии звонка, уведомлений и звуков 64 Переупорядочивание вкладок приложений 65 Настройка стиля экрана блокировки 65 Скрытие информации о пропущенных вызовах и сообщениях на экране блокировки 65 Защита HTC Desire 600 с помощью персональной идентификации 66 Телефонные вызовы Выполнение вызова с помощью функции "Интеллектуальный набор номера" 67 Звонок в ответ на пропущенный вызов 68 Быстрый набор 68 Звонок по телефонному номеру из SMS-сообщения 69 Звонок по телефонному номеру из сообщения эл. -

Manufacturer Device Model Consumers Count Apple Iphone
Manufacturer Device Model Consumers Count Apple iPhone 24,666,239 Apple iPad 13,155,907 samsung SM-J500M 1,079,744 Apple iPod touch 1,070,538 samsung SM-G531H 1,043,553 samsung SM-G935F 1,026,327 samsung SM-T113 894,096 samsung SM-J700M 888,680 motorola MotoG3 860,116 samsung SM-J700F 847,315 samsung SM-G920F 834,655 samsung SM-G900F 827,050 samsung SM-G610F 786,659 HUAWEI ALE-L21 783,180 OPPO A37f 701,488 samsung SM-G955U 699,321 samsung SM-G930F 685,195 samsung SM-J510FN 673,415 samsung SM-G950U 654,635 samsung SM-G530H 651,695 samsung SM-J710F 647,723 motorola Moto G (4) 640,091 samsung SM-T110 627,013 samsung SM-J200G 611,728 OPPO A1601 588,226 samsung SM-G925F 571,858 samsung SM-G930V 557,813 samsung SM-A510F 533,209 ZTE Z981 532,290 samsung GT-I9300 516,580 samsung SM-J320FN 511,109 Xiaomi Redmi Note 4 507,119 samsung GT-I9505 504,325 samsung GT-I9060I 488,253 samsung SM-J120H 472,748 samsung SM-G900V 458,996 Xiaomi Redmi Note 3 435,822 samsung SM-A310F 435,163 samsung SM-T560 435,042 motorola XT1069 433,667 motorola Moto G Play 422,147 LGE LG-K430 406,009 samsung GT-I9500 392,674 Xiaomi Redmi 3S 388,092 samsung SM-J700H 384,922 samsung SM-G532G 384,884 samsung SM-N9005 382,982 samsung SM-G531F 382,728 motorola XT1033 380,899 Generic Android 7.0 374,405 motorola XT1068 373,075 samsung SM-J500FN 372,029 samsung SM-J320M 366,049 samsung SM-J105B 351,985 samsung SM-T230 348,374 samsung SM-T280 347,350 samsung SM-T113NU 341,313 samsung SM-T350 338,525 samsung SM-G935V 337,090 samsung SM-J500F 332,972 samsung SM-J320F 329,165 motorola -

Venkateshwara Enterprises
Venkateshwara Enterprises https://www.indiamart.com/venkateshwara-enterprise/ Venkateshwara Enterprises is one of the leading mobile servicing companies in Bangalore which is well equipped with high technical knowledge staff. We are a company in the business of retailing mobile phones, smart phones, tablet devices ... About Us Venkateshwara Enterprises is one of the leading mobile servicing companies in Bangalore which is well equipped with high technical knowledge staff. We are a company in the business of retailing mobile phones, smart phones, tablet devices and accessories. Venkateshwara Enterprises currently has 6 outlets across Bangalore, We offer services in wide range of mobile products. We believe that reliability is the most important factor hence we never compromise in quality. Our Strategic business alliances for broad spectrum of products and services allow us to offer most cost-effective solutions to the customers. We aim to understand and anticipate what a customer needs and how we can help him improve his company. All major handset brands like Nokia, Sony Ericsson, LG, Samsung, Motorola, Apple, Micromax, HTC and Blackberry are available at the store. For more information, please visit https://www.indiamart.com/venkateshwara-enterprise/aboutus.html HTC P r o d u c t s & S e r v i c e s HTC T327W Desire U (DS) HTC One 802d Mobile Phones Mobile Phones HTC Desire 600 Mobile HTC One Mini Mobile Phones Phones BLACK BERRY P r o d u c t s & S e r v i c e s 9720 Blackberry Bold Smart Q 10 Blackberry Mobile Phone Phones Q 5 Blackberry -
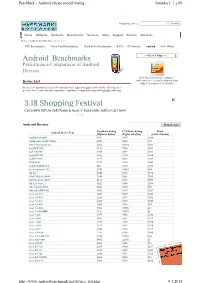
Androidtm Benchmarks 3.18 Shopping Festival
PassMark - Android phone model listing Stránka č. 1 z 69 Shopping cart | Search Home Software Hardware Benchmarks Services Store Support Forums About Us Home » Android Benchmarks » Device List CPU Benchmarks Video Card Benchmarks Hard Drive Benchmarks RAM PC Systems Android iOS / iPhone TM ----Select A Page ---- Android Benchmarks Performance Comparison of Android Devices How does your device compare? Device List Add your device to our benchmark chart with PerformanceTest Mobile ! Below is an alphabetical list of all Android device types that appear in the charts. Clicking on a specific device name will take you to the charts where it appears in and will highlight it for you. 3.18 Shopping Festival Up to 50% Off On Cell Phone & Acce. 3-Days Only, Add to Cart now! Android Devices Find Device PassMark Rating CPUMark Rating Rank Android Device Type (higher is better) (higher is better) (lower is better) 1005tg N10-QM 935 3377 4086 1080p-n003 1080P-N003 2505 9820 874 1life 1Life.smart.air 2282 10103 1243 3-q RC9731C 2154 5756 1487 3q LC0720C 1646 4897 2531 3q QS0717D 1363 1760 3236 3q RC9712C 2154 5223 1485 9300 9300 1275 3364 3443 A-link PAD10 ICS 616 1130 4389 A.c.ryan dyno 7.85 2749 11065 634 A2 A2 1240 2784 3518 A800 XOLO_A800 1344 3661 3285 A830 Lenovo A830 2114 8313 1559 Ab-s_a Aqua_7 1522 3640 2834 Abc Vision7-DCI 2602 6880 753 Abroad ABROAD 1438 3379 3057 Acer A1-713 2229 9069 1349 Acer A1-810 2265 8337 1282 Acer A1-811 2233 8524 1343 Acer A1-830 3005 9196 540 Acer A1-840 3962 23996 281 Acer A1-840FHD 5124 28591 61 Acer A101 1577 3758 2702 Acer A110 1964 8623 1917 Acer A200 1557 3829 2746 Acer A210 2135 8313 1516 Acer A211 1848 8130 2137 Acer A3-A10 2351 8128 1100 Acer A3-A20FHD 3269 11265 456 Acer AA3-600 5451 22392 25 Acer AO722 2603 5185 751 Acer B1-710 1339 3900 3297 Acer B1-711 2293 8583 1220 Acer b1-720 2058 4371 1701 Acer B1-730HD 3068 9045 516 Acer B1-A71 1308 4119 3362 http://www.androidbenchmark.net/device_list.php 9.3.2015 PassMark - Android phone model listing Stránka č.