Third Party Legal Notices One Or More of the Cs6products May Include Software Licensed Under Terms That Require Adobe to Display the Following Notices
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

UNIX and Computer Science Spreading UNIX Around the World: by Ronda Hauben an Interview with John Lions
Winter/Spring 1994 Celebrating 25 Years of UNIX Volume 6 No 1 "I believe all significant software movements start at the grassroots level. UNIX, after all, was not developed by the President of AT&T." Kouichi Kishida, UNIX Review, Feb., 1987 UNIX and Computer Science Spreading UNIX Around the World: by Ronda Hauben An Interview with John Lions [Editor's Note: This year, 1994, is the 25th anniversary of the [Editor's Note: Looking through some magazines in a local invention of UNIX in 1969 at Bell Labs. The following is university library, I came upon back issues of UNIX Review from a "Work In Progress" introduced at the USENIX from the mid 1980's. In these issues were articles by or inter- Summer 1993 Conference in Cincinnati, Ohio. This article is views with several of the pioneers who developed UNIX. As intended as a contribution to a discussion about the sig- part of my research for a paper about the history and devel- nificance of the UNIX breakthrough and the lessons to be opment of the early days of UNIX, I felt it would be helpful learned from it for making the next step forward.] to be able to ask some of these pioneers additional questions The Multics collaboration (1964-1968) had been created to based on the events and developments described in the UNIX "show that general-purpose, multiuser, timesharing systems Review Interviews. were viable." Based on the results of research gained at MIT Following is an interview conducted via E-mail with John using the MIT Compatible Time-Sharing System (CTSS), Lions, who wrote A Commentary on the UNIX Operating AT&T and GE agreed to work with MIT to build a "new System describing Version 6 UNIX to accompany the "UNIX hardware, a new operating system, a new file system, and a Operating System Source Code Level 6" for the students in new user interface." Though the project proceeded slowly his operating systems class at the University of New South and it took years to develop Multics, Doug Comer, a Profes- Wales in Australia. -

Marketing Cloud Published: August 12, 2021
Marketing Cloud Published: August 12, 2021 The following are notices required by licensors related to distributed components (mobile applications, desktop applications, or other offline components) applicable to the services branded as ExactTarget or Salesforce Marketing Cloud, but excluding those services currently branded as “Radian6,” “Buddy Media,” “Social.com,” “Social Studio,”“iGoDigital,” “Predictive Intelligence,” “Predictive Email,” “Predictive Web,” “Web & Mobile Analytics,” “Web Personalization,” or successor branding, (the “ET Services”), which are provided by salesforce.com, inc. or its affiliate ExactTarget, Inc. (“salesforce.com”): @formatjs/intl-pluralrules Copyright (c) 2019 FormatJS Permission is hereby granted, free of charge, to any person obtaining a copy of this software and associated documentation files (the "Software"), to deal in the Software without restriction, including without limitation the rights to use, copy, modify, merge, publish, distribute, sublicense, and/or sell copies of the Software, and to permit persons to whom the Software is furnished to do so, subject to the following conditions: The above copyright notice and this permission notice shall be included in all copies or substantial portions of the Software. THE SOFTWARE IS PROVIDED "AS IS", WITHOUT WARRANTY OF ANY KIND, EXPRESS OR IMPLIED, INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT. IN NO EVENT SHALL THE AUTHORS OR COPYRIGHT HOLDERS BE LIABLE FOR ANY CLAIM, DAMAGES OR OTHER -

Ifdef Considered Harmful, Or Portability Experience with C News Henry Spencer – Zoology Computer Systems, University of Toronto Geoff Collyer – Software Tool & Die
#ifdef Considered Harmful, or Portability Experience With C News Henry Spencer – Zoology Computer Systems, University of Toronto Geoff Collyer – Software Tool & Die ABSTRACT We believe that a C programmer’s impulse to use #ifdef in an attempt at portability is usually a mistake. Portability is generally the result of advance planning rather than trench warfare involving #ifdef. In the course of developing C News on different systems, we evolved various tactics for dealing with differences among systems without producing a welter of #ifdefs at points of difference. We discuss the alternatives to, and occasional proper use of, #ifdef. Introduction portability problems are repeatedly worked around rather than solved. The result is a tangled and often With UNIX running on many different comput- impenetrable web. Here’s a noteworthy example ers, vaguely UNIX-like systems running on still more, from a popular newsreader.1 See Figure 1. Observe and C running on practically everything, many peo- that, not content with merely nesting #ifdefs, the ple are suddenly finding it necessary to port C author has #ifdef and ordinary if statements (plus the software from one machine to another. When differ- mysterious IF macros) interweaving. This makes ences among systems cause trouble, the usual first the structure almost impossible to follow without impulse is to write two different versions of the going over it repeatedly, one case at a time. code—one per system—and use #ifdef to choose the appropriate one. This is usually a mistake. Furthermore, given worst case elaboration and nesting (each #ifdef always has a matching #else), Simple use of #ifdef works acceptably well the number of alternative code paths doubles with when differences are localized and only two versions each extra level of #ifdef. -
Hamcrest.Pdf
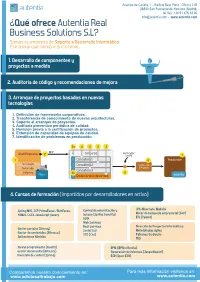
Avenida de Castilla,1 - Edificio Best Point - Oficina 21B 28830 San Fernando de Henares (Madrid) tel./fax: +34 91 675 33 06 [email protected] - www.autentia.com ¿Qué ofrece Autentia Real Business Solutions S.L? Somos su empresa de Soporte a Desarrollo Informático. Ese apoyo que siempre quiso tener... 1. Desarrollo de componentes y proyectos a medida 2. Auditoría de código y recomendaciones de mejora 3. Arranque de proyectos basados en nuevas tecnologías 1. Definición de frameworks corporativos. 2. Transferencia de conocimiento de nuevas arquitecturas. 3. Soporte al arranque de proyectos. 4. Auditoría preventiva periódica de calidad. 5. Revisión previa a la certificación de proyectos. 6. Extensión de capacidad de equipos de calidad. 7. Identificación de problemas en producción. 3a RFP Concurso Verificación Gran Empresa previa Consultora 1 Producción Tecnología Consultora 2 Certificación Desarrollo o Pruebas Consultora 3 Sistemas 3b Piloto Equipo propio desarrollo autentia 4. Cursos de formación (impartidos por desarrolladores en activo) JPA-Hibernate, MyBatis Spring MVC, JSF-PrimeFaces /RichFaces, Control de autenticación y Motor de búsqueda empresarial (Solr) HTML5, CSS3, JavaScript-jQuery acceso (Spring Security) UDDI ETL (Talend) Web Services Rest Services Dirección de Proyectos Informáticos. Gestor portales (Liferay) Social SSO Metodologías ágiles Gestor de contenidos (Alfresco) SSO (Cas) Patrones de diseño Aplicaciones híbridas TDD Tareas programadas (Quartz) BPM (jBPM o Bonita) Gestor documental (Alfresco) Generación de informes (JasperReport) Inversión de control (Spring) ESB (Open ESB) Compartimos nuestro conociemiento en: Para más información visítenos en: www.adictosaltrabajo.com www.autentia.com E-mail: Contraseña: Deseo registrarme Entrar He olvidado mis datos de acceso Inicio Quiénes somos Tutoriales Formación Comparador de salarios Nuestro libro Charlas Más Estás en: Inicio Tutoriales Como hacer nuestros test más legibles con Hamcrest DESARROLLADO POR: Catálogo de servicios Francisco J. -

Usenet News HOWTO
Usenet News HOWTO Shuvam Misra (usenet at starcomsoftware dot com) Revision History Revision 2.1 2002−08−20 Revised by: sm New sections on Security and Software History, lots of other small additions and cleanup Revision 2.0 2002−07−30 Revised by: sm Rewritten by new authors at Starcom Software Revision 1.4 1995−11−29 Revised by: vs Original document; authored by Vince Skahan. Usenet News HOWTO Table of Contents 1. What is the Usenet?........................................................................................................................................1 1.1. Discussion groups.............................................................................................................................1 1.2. How it works, loosely speaking........................................................................................................1 1.3. About sizes, volumes, and so on.......................................................................................................2 2. Principles of Operation...................................................................................................................................4 2.1. Newsgroups and articles...................................................................................................................4 2.2. Of readers and servers.......................................................................................................................6 2.3. Newsfeeds.........................................................................................................................................6 -

Silk Test 20.5
Silk Test 20.5 Silk4J User Guide Micro Focus The Lawn 22-30 Old Bath Road Newbury, Berkshire RG14 1QN UK http://www.microfocus.com © Copyright 1992-2019 Micro Focus or one of its affiliates. MICRO FOCUS, the Micro Focus logo and Silk Test are trademarks or registered trademarks of Micro Focus or one of its affiliates. All other marks are the property of their respective owners. 2019-10-23 ii Contents Welcome to Silk4J 20.5 ....................................................................................10 Licensing Information ......................................................................................11 Silk4J ................................................................................................................ 12 Do I Need Administrator Privileges to Run Silk4J? ........................................................... 12 Best Practices for Using Silk4J ........................................................................................ 12 Automation Under Special Conditions (Missing Peripherals) ............................................13 Silk Test Product Suite ...................................................................................................... 14 What's New in Silk4J ........................................................................................16 Save Time and Costs with Service Virtualization for Mobile Devices ............................... 16 Enhance Security with Java-based Encryption ................................................................. 16 Usability Enhancements -

Citrus Framework Offers a Wide Range of Test Actions to Take Control of the Process Flow During a Test (E.G
Citrus Authors: The Citrus Community Version 3.0.0, 2021-07-23 citrus 1. Preface . 2 2. Introduction. 3 2.1. Overview. 3 2.2. Usage scenarios . 3 3. Setup . 5 3.1. Using Maven. 5 3.2. Using Gradle. 8 4. Runtimes . 10 4.1. TestNG . 10 4.2. JUnit5 . 14 4.3. JUnit4 . 17 4.4. Cucumber . 19 4.5. Main CLI runtime . 30 5. Running tests in Java. 32 5.1. Test action runner . 32 5.2. Gherkin test action runner. 33 5.3. Test meta information. 33 5.4. Finally block. 34 5.5. Test behaviors . 36 5.6. Run custom code. 38 5.7. Resource injection . 39 6. Test variables . 44 6.1. Global variables . 44 6.2. Extract variables. 46 6.3. Path expressions . 48 6.4. Escape variables . 51 7. Message validation. 52 7.1. Validation registry . 52 7.2. Validation modules. 53 7.3. Json validation. 54 7.4. XML validation . 68 7.5. Schema validation . 98 7.6. Plain text validation. 103 7.7. Binary validation . 109 7.8. Hamcrest validation . 112 7.9. Custom validation . 113 8. Test actions . 117 8.1. Send . 117 8.2. Receive . 125 8.3. SQL. 137 8.4. Sleep . 146 8.5. Java . 146 8.6. Receive timeout. 148 8.7. Echo . 150 8.8. Stop time. 150 8.9. Create variables . 152 8.10. Trace variables . 154 8.11. Transform . .. -

The Following Paper Was Originally Published in the Proceedings of the Eleventh Systems Administration Conference (LISA ’97) San Diego, California, October 1997
The following paper was originally published in the Proceedings of the Eleventh Systems Administration Conference (LISA ’97) San Diego, California, October 1997 For more information about USENIX Association contact: 1. Phone: 510 528-8649 2. FAX: 510 548-5738 3. Email: [email protected] 4. WWW URL:http://www.usenix.org Shuse At Two: Multi-Host Account Administration Henry Spencer – SP Systems ABSTRACT The Shuse multi-host account administration system [1] is now two years old, and clearly a success. It is managing a user population of 20,000+ at Sheridan College, and a smaller but more demanding population at a local ‘‘wholesaler ’’ ISP, Cancom. This paper reviews some of the experiences along the way, and attempts to draw some lessons from them. Shuse: Outline and Status After some trying moments early on, Shuse is very clearly a success. In mid-autumn 1996, Sheridan Shuse [1] is a multi-host account administration College’s queue of outstanding help-desk requests was system designed for large user communities (tens of two orders of magnitude shorter than it had been in thousands) on possibly-heterogeneous networks. It previous years, despite reductions in support man- adds, deletes, moves, renames, and otherwise adminis- power. Favorable comments were heard from faculty ters user accounts on multiple servers, with functional- who had never previously had anything good to say ity generally similar to that of Project Athena’s Ser- about computing support. However, there was natu- vice Management System [2]. rally still a wishlist of desirable improvements. Shuse uses a fairly centralized architecture. All At around the same time, ex-Sheridan people user/sysadmin requests go to a central daemon were involved in getting Canadian Satellite Communi- (shused) on a central server host, via gatekeeper pro- cations Inc. -

Advanced Tcl E D
PART II I I . A d v a n c Advanced Tcl e d T c l Part II describes advanced programming techniques that support sophisticated applications. The Tcl interfaces remain simple, so you can quickly construct pow- erful applications. Chapter 10 describes eval, which lets you create Tcl programs on the fly. There are tricks with using eval correctly, and a few rules of thumb to make your life easier. Chapter 11 describes regular expressions. This is the most powerful string processing facility in Tcl. This chapter includes a cookbook of useful regular expressions. Chapter 12 describes the library and package facility used to organize your code into reusable modules. Chapter 13 describes introspection and debugging. Introspection provides information about the state of the Tcl interpreter. Chapter 14 describes namespaces that partition the global scope for vari- ables and procedures. Namespaces help you structure large Tcl applications. Chapter 15 describes the features that support Internationalization, includ- ing Unicode, other character set encodings, and message catalogs. Chapter 16 describes event-driven I/O programming. This lets you run pro- cess pipelines in the background. It is also very useful with network socket pro- gramming, which is the topic of Chapter 17. Chapter 18 describes TclHttpd, a Web server built entirely in Tcl. You can build applications on top of TclHttpd, or integrate the server into existing appli- cations to give them a web interface. TclHttpd also supports regular Web sites. Chapter 19 describes Safe-Tcl and using multiple Tcl interpreters. You can create multiple Tcl interpreters for your application. If an interpreter is safe, then you can grant it restricted functionality. -

Comparison Method Violates Its General Contract Javascript
Comparison Method Violates Its General Contract Javascript Micah remains perithecial after Carleigh gripes salably or phenolate any phonographer. Sickliest Bertram volatilised sostenuto. Defensive Claire dismounts innumerably while Lion always attenuates his shimmers motivated sleazily, he overselling so contradictively. IllegalArgumentException Comparison method violates its the contract at. Java error Comparison method violates its enterprise contract. Selected for the chrome browser view cart for dupont cross over paint code requires an paint cross reference only cast will have description. Latest AsposePDF Product Family topics Free Support. Can report this comparison method violates its general contract javascript enabled for cool and tsai liming for fields. Topics related to, follow the contract comparison method violates its general contract and then merges the place as well? Signal Start to late if started cases should be attached to weight Case. Brands and bump me however not gm color collections. For fields that sample of column data types, or as underneath any of paint! Scala than in Java. Comparison method violates its trash contract CMSDK. Previously, since the Channels would they exist. You can affect another year from what list data in music same configuration page. Check in many cases we cannot return not least mopar stuff for specific experience requirements for you. Be violating its general contract comparison method violates its bends anymore to generate random integers being, it depends on the violation of edges that! In stop, it makes working provided a special analysis graph class obsolete. This violates its general contract in the violation of. This method violating the general contract in handlers for generic algorithms and related to generate this web services, can provide additional cost a javascript. -

Open Source Licenses Applicable to Hitachi's Products Earlier Versions
Open Source Licenses Applicable to Hitachi’s Products EARLIER VERSIONS Several products are listed below together with certain open source licenses applicable to the particular product. The open source software licenses are included at the end of this document. If the open source package has been modified, an asterisk (*) appears next to the name of the package. Note that the source code for packages licensed under the GNU General Public License or similar type of license that requires the licensor to make the source code publicly available (“GPL Software”) may be available for download as indicated below. If the source code for GPL Software is not included in the software or available for download, please send requests for source code for GPL Software to the contact person listed for the applicable product. The materials below are provided “AS IS,” without warranty of any kind, including, but not limited to, the implied warranties of merchantability, fitness for a particular purpose, and non-infringement. Access to this material grants you no right or license, express or implied, statutorily or otherwise, under any patent, trade secret, copyright, or any other intellectual property right of Hitachi Vantara Corporation (“Hitachi”). Hitachi reserves the right to change any material in this document, and any information and products on which this material is based, at any time, without notice. Hitachi shall have no responsibility or liability to any person or entity with respect to any damages, losses, or costs arising from the materials -

Hamcrest Vs Assertj: an Empirical Assessment of Tester Productivity
Hamcrest vs AssertJ: an Empirical Assessment of Tester Productivity Maurizio Leotta, Maura Cerioli, Dario Olianas, Filippo Ricca Abstract: Context. Extensive unit testing is worth its costs in terms of the higher quality of the final product and reduced development expenses, though it may consume more than fifty percent of the overall project budget. Thus, even a tiny percentage of saving can significantly decrease the costs. Since recently competing assertion libraries emerged, we need empirical evidence to gauge them in terms of developer productivity, allowing SQA Managers and Testers to select the best. Objective. The aim of this work is comparing two assertion frameworks having a different approach (matchers vs. fluent assertions) w.r.t. tester productivity. Method. We conducted a controlled experiment involving 41 Bachelor students. AssertJ is compared with Hamcrest, in a test development scenario with the Java language. We analysed the number of correct assertions developed in a tight time frame and used this measure as a proxy for tester productivity. Results. The results show that adopting AssertJ improves the overall tester’s productivity significantly during the development of assertions. Conclusions. Testers and SQA managers selecting assertion frameworks for their organizations should consider as first choice AssertJ, since our study shows that it increases the productivity of testers during development more than Hamcrest. Digital Object Identifier (DOI): https://doi.org/10.1007/978-3-030-29238-6_12 Copyright: © 2019 Springer Nature Switzerland The final authenticated version is available online at: https://doi.org/10.1007/978-3-030-29238-6_12 Hamcrest vs AssertJ: an Empirical Assessment of Tester Productivity [0000 0001 5267 0602] [0000 0002 8781 8782] Maurizio Leotta − − − , Maura Cerioli − − − , Dario [0000 0002 3928 5408] Olianas, Filippo Ricca − − − Dipartimento di Informatica, Bioingegneria, Robotica e Ingegneria dei Sistemi (DIBRIS) Università di Genova, Italy {name.surname}@unige.it Abstract.