A Practical, Lightweight, and Flexible Confinement Framework in Ebpf
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Automatic Benchmark Profiling Through Advanced Trace Analysis Alexis Martin, Vania Marangozova-Martin
Automatic Benchmark Profiling through Advanced Trace Analysis Alexis Martin, Vania Marangozova-Martin To cite this version: Alexis Martin, Vania Marangozova-Martin. Automatic Benchmark Profiling through Advanced Trace Analysis. [Research Report] RR-8889, Inria - Research Centre Grenoble – Rhône-Alpes; Université Grenoble Alpes; CNRS. 2016. hal-01292618 HAL Id: hal-01292618 https://hal.inria.fr/hal-01292618 Submitted on 24 Mar 2016 HAL is a multi-disciplinary open access L’archive ouverte pluridisciplinaire HAL, est archive for the deposit and dissemination of sci- destinée au dépôt et à la diffusion de documents entific research documents, whether they are pub- scientifiques de niveau recherche, publiés ou non, lished or not. The documents may come from émanant des établissements d’enseignement et de teaching and research institutions in France or recherche français ou étrangers, des laboratoires abroad, or from public or private research centers. publics ou privés. Automatic Benchmark Profiling through Advanced Trace Analysis Alexis Martin , Vania Marangozova-Martin RESEARCH REPORT N° 8889 March 23, 2016 Project-Team Polaris ISSN 0249-6399 ISRN INRIA/RR--8889--FR+ENG Automatic Benchmark Profiling through Advanced Trace Analysis Alexis Martin ∗ † ‡, Vania Marangozova-Martin ∗ † ‡ Project-Team Polaris Research Report n° 8889 — March 23, 2016 — 15 pages Abstract: Benchmarking has proven to be crucial for the investigation of the behavior and performances of a system. However, the choice of relevant benchmarks still remains a challenge. To help the process of comparing and choosing among benchmarks, we propose a solution for automatic benchmark profiling. It computes unified benchmark profiles reflecting benchmarks’ duration, function repartition, stability, CPU efficiency, parallelization and memory usage. -

Automated Performance Testing for Virtualization with Mmtests
Automated Performance Testing For Virtualization with MMTests Dario Faggioli <[email protected]> Software Engineer - Virtualization Specialist, SUSE GPG: 4B9B 2C3A 3DD5 86BD 163E 738B 1642 7889 A5B8 73EE https://about.me/dario.faggioli https://www.linkedin.com/in/dfaggioli/ https://twitter.com/DarioFaggioli (@DarioFaggioli) Testing / Benchmarking / CI Tools & Suites • OpenQA • Jenkins • Kernel CI • Autotest / Avocado-framework / Avocado-vt • Phoronix Test Suite • Fuego • Linux Test Project • Xen-Project’s OSSTests • … • ... SRSLY THINKING I’ll TALK ABOUT & SUGGEST USING ANOTHER ONE ? REALLY ? Benchmarking on Baremetal What’s the performance impact of kernel code change “X” ? Baremetal Baremetal Kernel Kernel (no X) VS. (with X) CPU MEM CPU MEM bench bench bench bench I/O I/O bench bench Benchmarking in Virtualization What’s the performance impact of kernel code change “X” ? Baremetal Baremetal Baremetal Baremetal Kernel Kernel Kernel (no X) Kernel (no X) (with X) (with X) VM VS. VM VS. VM VS. VM Kernel Kernel Kernel (no X) Kernel (no X) (with X) (with X) CPU MEM CPU MEM CPU MEM CPU MEM bench bench bench bench bench bench bench bench I/O I/O I/O I/O bench bench bench bench Benchmarking in Virtualization What’s the performance impact of kernel code change “X” ? Baremetal Baremetal Baremetal Baremetal Kernel Kernel Kernel (no X) Kernel (no X) (with X) (with X) VM VS. VM VS. VM VS. VM Kernel Kernel Kernel (no X) Kernel (no X) (with X) (with X) We want to run the benchmarks inside VMs CPU MEM CPU MEM CPU MEM CPU MEM bench bench bench bench bench bench bench bench I/O I/O I/O I/O bench bench bench bench Benchmarking in Virtualization What’s the performance impact of kernel code change “X” ? Baremetal Baremetal Baremetal Baremetal Kernel Kernel Kernel (no X) Kernel (no X) (with X) (with X) VM VS. -

Zhodnocení Použitelnosti Raspberry Pi Pro Distribuované Výpočty
Univerzita Karlova v Praze Matematicko-fyzikální fakulta BAKALÁŘSKÁ PRÁCE Petr Stefan Zhodnocení použitelnosti Raspberry Pi pro distribuované výpoèty Katedra softwarového inženýrství Vedoucí bakaláøské práce: RNDr. Martin Kruli¹, Ph.D. Studijní program: Informatika Studijní obor: Obecná informatika Praha 2015 Prohla¹uji, že jsem tuto bakaláøskou práci vypracoval(a) samostatně a výhradně s použitím citovaných pramenù, literatury a dalších odborných zdrojù. Beru na vědomí, že se na moji práci vztahují práva a povinnosti vyplývající ze zákona è. 121/2000 Sb., autorského zákona v platném znění, zejména skuteènost, že Univerzita Karlova v Praze má právo na uzavření licenční smlouvy o užití této práce jako ¹kolního díla podle x60 odst. 1 autorského zákona. V Praze dne 29. èervence 2015 Petr Stefan i ii Název práce: Zhodnocení použitelnosti Raspberry Pi pro distribuované výpoèty Autor: Petr Stefan Katedra: Katedra softwarového inženýrství Vedoucí bakaláøské práce: RNDr. Martin Kruli¹, Ph.D., Katedra softwarového inženýrství Abstrakt: Cílem práce bylo zhodnotit výkonnostní vlastnosti mikropočítače Rasp- berry Pi, a to především z hlediska možnosti sestavení výpoèetního klastru z více těchto jednotek. Součástí práce bylo vytvoření sady testù pro měření výpočetního výkonu procesoru, propustnosti operační paměti, rychlosti zápisu a čtení z per- sistentního úložiště (paměťové karty) a propustnosti síťového rozhraní Ethernet. Na základě porovnání výsledků získaných měřením na Raspberry Pi a na vhod- ném reprezentativním vzorku dalších běžně dostupných počítačů bylo provedeno doporučení, zda je konstrukce Raspberry Pi klastru opodstatněná. Tyto výsledky rovněž poskytly přibližné ekonomické a výkonnostní projekce takového řešení. Klíčová slova: Raspberry Pi výkon distribuovaný výpoèet benchmark Title: Assessing Usability of Raspberry Pi for Distributed Computing Author: Petr Stefan Department: Department of Software Engineering Supervisor: RNDr. -
System76.Pdf
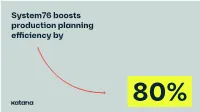
System76 boosts production planning efficiency by 80% Katana gives System76 the real-time overview they need to manage production scheduling and scale their manufacturing operations effectively. With the help of Katana, their team spends 50% less time on admin while boosting production efficiency by 80%. Sarah Zinger, Director of Production Logistics at System76 “We knew we needed something more than just a spreadsheet but we didn't like the idea of paying a crazy amount for a huge system that we would not fully use. Katana was simplistic and answered what we needed without a ton of fluff or other elements that we did not need. “ After switching to Katana from spreadsheets, System76 made day-to-day operations 50% more efficient System76 improved inventory control and increased production planning efficiency by close to 80% as a result of prioritizing and scheduling production with Katana Previously, System76 struggled to track inventory and order fulfillment, and Katana gave their team a clear delineation of the order of operations for each product in their catalog About Hornby Organic System76 is a computer manufacturer based in Denver, Colorado, specializing in Linux-based laptops, desktops, and servers. The company is an advocate for free COMPANY and open-source software, offering either Ubuntu or their own Ubuntu-based Linux distribution, Pop!_OS, as the default operating system. WEBSITE system76.com LOCATION USA EMPLOYEES Widely regarded as the gold standard in Linux-based computing, System76 offers 60+ a unique combination of purpose-engineered hardware and software optimized INDUSTRY for its machines. This and a focus on customizability make System76 highly Electronics and high tech regarded among developers and technology professionals. -

Automatic Benchmark Profiling Through Advanced Trace Analysis
View metadata, citation and similar papers at core.ac.uk brought to you by CORE provided by Hal - Université Grenoble Alpes Automatic Benchmark Profiling through Advanced Trace Analysis Alexis Martin, Vania Marangozova-Martin To cite this version: Alexis Martin, Vania Marangozova-Martin. Automatic Benchmark Profiling through Advanced Trace Analysis. [Research Report] RR-8889, Inria - Research Centre Grenoble { Rh^one-Alpes; Universit´eGrenoble Alpes; CNRS. 2016. <hal-01292618> HAL Id: hal-01292618 https://hal.inria.fr/hal-01292618 Submitted on 24 Mar 2016 HAL is a multi-disciplinary open access L'archive ouverte pluridisciplinaire HAL, est archive for the deposit and dissemination of sci- destin´eeau d´ep^otet `ala diffusion de documents entific research documents, whether they are pub- scientifiques de niveau recherche, publi´esou non, lished or not. The documents may come from ´emanant des ´etablissements d'enseignement et de teaching and research institutions in France or recherche fran¸caisou ´etrangers,des laboratoires abroad, or from public or private research centers. publics ou priv´es. Automatic Benchmark Profiling through Advanced Trace Analysis Alexis Martin , Vania Marangozova-Martin RESEARCH REPORT N° 8889 March 23, 2016 Project-Team Polaris ISSN 0249-6399 ISRN INRIA/RR--8889--FR+ENG Automatic Benchmark Profiling through Advanced Trace Analysis Alexis Martin ∗ † ‡, Vania Marangozova-Martin ∗ † ‡ Project-Team Polaris Research Report n° 8889 — March 23, 2016 — 15 pages Abstract: Benchmarking has proven to be crucial for the investigation of the behavior and performances of a system. However, the choice of relevant benchmarks still remains a challenge. To help the process of comparing and choosing among benchmarks, we propose a solution for automatic benchmark profiling. -

Xeon Platinum 8280 Vs. AMD EPYC 7742 - Ubuntu Linux
www.phoronix-test-suite.com Xeon Platinum 8280 vs. AMD EPYC 7742 - Ubuntu Linux AMD EPYC and Intel Xeon benchmarks by Michael Larabel... Mix of single and multi-threaded workloads. Admittedly somewhat random tests with the intent of just being to doing some validation on Phoronix Test Suite 9.4 and checking out the graphing code, PDF generation, etc. Take the actual results as you wish. Automated Executive Summary 2 x EPYC 7742 had the most wins, coming in first place for 61% of the tests. Based on the geometric mean of all complete results, the fastest (2 x EPYC 7742) was 1.2x the speed of the slowest (2 x Xeon Platinum 8280). The results with the greatest spread from best to worst included: Tungsten Renderer (Scene: Volumetric Caustic) at 3.53x - MBW (Test: Memory Copy - Array Size: 4096 MiB) at 3.22x - Parboil (Test: OpenMP MRI Gridding) at 3.02x - Hackbench (Count: 32 - Type: Process) at 3.01x - Tachyon (Total Time) at 2.62x - C-Ray (Total Time - 4K, 16 Rays Per Pixel) at 2.37x - dav1d (Video Input: Chimera 1080p) at 2.33x Xeon Platinum 8280 vs. AMD EPYC 7742 - Ubuntu Linux - Coremark (CoreMark Size 666 - Iterations Per Second) at 2.3x - dav1d (Video Input: Summer Nature 1080p) at 2.17x - GraphicsMagick (Operation: Sharpen) at 2.17x. Test Systems: 2 x Xeon Platinum 8280 Processor: 2 x Intel Xeon Platinum 8280 @ 4.00GHz (56 Cores / 112 Threads), Motherboard: GIGABYTE MD61-SC2-00 v01000100 (T15 BIOS), Chipset: Intel Sky Lake-E DMI3 Registers, Memory: 12 x 32 GB DDR4-2933MT/s HMA84GR7CJR4N-WM, Disk: 280GB INTEL SSDPED1D280GA, Graphics: -

Fair Benchmarking for Cloud Computing Systems
Fair Benchmarking for Cloud Computing Systems Authors: Lee Gillam Bin Li John O’Loughlin Anuz Pranap Singh Tomar March 2012 Contents 1 Introduction .............................................................................................................................................................. 3 2 Background .............................................................................................................................................................. 4 3 Previous work ........................................................................................................................................................... 5 3.1 Literature ........................................................................................................................................................... 5 3.2 Related Resources ............................................................................................................................................. 6 4 Preparation ............................................................................................................................................................... 9 4.1 Cloud Providers................................................................................................................................................. 9 4.2 Cloud APIs ...................................................................................................................................................... 10 4.3 Benchmark selection ...................................................................................................................................... -

Aligning Intent and Behavior in Software Systems: How Programs Communicate & Their Distribution and Organization
© 2020 William B. Dietz ALIGNING INTENT AND BEHAVIOR IN SOFTWARE SYSTEMS: HOW PROGRAMS COMMUNICATE & THEIR DISTRIBUTION AND ORGANIZATION BY WILLIAM B. DIETZ DISSERTATION Submitted in partial fulfillment of the requirements for the degree of Doctor of Philosophy in Computer Science in the Graduate College of the University of Illinois at Urbana-Champaign, 2020 Urbana, Illinois Doctoral Committee: Professor Vikram Adve, Chair Professor John Regehr, University of Utah Professor Tao Xie Assistant Professor Sasa Misailovic ABSTRACT Managing the overwhelming complexity of software is a fundamental challenge because complex- ity is the root cause of problems regarding software performance, size, and security. Complexity is what makes software hard to understand, and our ability to understand software in whole or in part is essential to being able to address these problems effectively. Attacking this overwhelming complexity is the fundamental challenge I seek to address by simplifying how we write, organize and think about programs. Within this dissertation I present a system of tools and a set of solutions for improving the nature of software by focusing on programmer’s desired outcome, i.e. their intent. At the program level, the conventional focus, it is impossible to identify complexity that, at the system level, is unnecessary. This “accidental complexity” includes everything from unused features to independent implementations of common algorithmic tasks. Software techniques driving innovation simultaneously increase the distance between what is intended by humans – developers, designers, and especially the users – and what the executing code does in practice. By preserving the declarative intent of the programmer, which is lost in the traditional process of compiling and linking and building software, it is easier to abstract away unnecessary details. -

Download Vol 8, No 3&4, Year 2015
The International Journal on Advances in Systems and Measurements is published by IARIA. ISSN: 1942-261x journals site: http://www.iariajournals.org contact: [email protected] Responsibility for the contents rests upon the authors and not upon IARIA, nor on IARIA volunteers, staff, or contractors. IARIA is the owner of the publication and of editorial aspects. IARIA reserves the right to update the content for quality improvements. Abstracting is permitted with credit to the source. Libraries are permitted to photocopy or print, providing the reference is mentioned and that the resulting material is made available at no cost. Reference should mention: International Journal on Advances in Systems and Measurements, issn 1942-261x vol. 8, no. 3 & 4, year 2015, http://www.iariajournals.org/systems_and_measurements/ The copyright for each included paper belongs to the authors. Republishing of same material, by authors or persons or organizations, is not allowed. Reprint rights can be granted by IARIA or by the authors, and must include proper reference. Reference to an article in the journal is as follows: <Author list>, “<Article title>” International Journal on Advances in Systems and Measurements, issn 1942-261x vol. 8, no. 3 & 4, year 2015, http://www.iariajournals.org/systems_and_measurements/ IARIA journals are made available for free, proving the appropriate references are made when their content is used. Sponsored by IARIA www.iaria.org Copyright © 2015 IARIA International Journal on Advances in Systems and Measurements Volume 8, Number -

Phoronix Test Suite V4.0.1 (Suldal)
www.phoronix-test-suite.com Phoronix Test Suite v4.0.1 (Suldal) User Manual Phoronix Test Suite v4.0.1 Test Client Documentation Getting Started Overview The Phoronix Test Suite is the most comprehensive testing and benchmarking platform available for Linux, Solaris, Mac OS X, and BSD operating systems. The Phoronix Test Suite allows for carrying out tests in a fully automated manner from test installation to execution and reporting. All tests are meant to be easily reproducible, easy-to-use, and support fully automated execution. The Phoronix Test Suite is open-source under the GNU GPLv3 license and is developed by Phoronix Media in cooperation with partners. Version 1.0 of the Phoronix Test Suite was publicly released in 2008. The Phoronix Test Suite client itself is a test framework for providing seamless execution of test profiles and test suites. There are more than 200 tests available by default, which are transparently available via OpenBenchmarking.org integration. Of these default test profiles there is a range of sub-systems that can be tested and a range of hardware from mobile devices to desktops and worksrtations/servers. New tests can be easily introduced via the Phoronix Test Suite's extensible test architecture, with test profiles consisting of XML files and shell scripts. Test profiles can produce a quantitative result or other qualitative/abstract results like image quality comparisons and pass/fail. Using Phoronix Test Suite modules, other data can also be automatically collected at run-time such as the system power consumption, disk usage, and other software/hardware sensors. Test suites contain references to test profiles to execute as part of a set or can also reference other test suites. -

Getting Started with Ubuntu and Kubuntu
Getting Started With Ubuntu and Kubuntu IN THIS PART Chapter 1 The Ubuntu Linux Project Chapter 2 Installing Ubuntu and Kubuntu Chapter 3 Installing Ubuntu and Kubuntu on Special-Purpose Systems COPYRIGHTED MATERIAL 94208c01.indd 1 3/16/09 11:43:23 PM 94208c01.indd 2 3/16/09 11:43:24 PM The Ubuntu Linux Project ersonal computers and their operating systems have come a long way since the late 1970s, when the first home computer hit the market. At IN THIS cHAPTER that time, you could only toggle in a program by flipping switches on the P Introducing Ubuntu Linux front of the machine, and the machine could then run that program and only that program until you manually loaded another, at which time the first program Choosing Ubuntu was kicked off the system. Today’s personal computers provide powerful graph- ics and a rich user interface that make it easy to select and run a wide variety of Reviewing hardware and software concurrently. software requirements The first home computer users were a community of interested people who just Using Ubuntu CDs wanted to do something with these early machines. They formed computer clubs and published newsletters to share their interests and knowledge — and often the Getting help with Ubuntu Linux software that they wrote for and used on their machines. Sensing opportunities and a growing market, thousands of computer companies sprang up to write and Getting more information sell specific applications for the computer systems of the day. This software ranged about Ubuntu from applications such as word processors, spreadsheets, and games to operating systems that made it easier to manage, load, and execute different programs. -

Getting Started with Ubuntu 13.04
Copyright © – by e Ubuntu Manual Team. Some rights reserved. c b a is work is licensed under the Creative Commons Aribution–Share Alike . License. To view a copy of this license, see Appendix A, visit http://creativecommons.org/licenses/by-sa/./, or send a leer to Creative Commons, Second Street, Suite , San Francisco, California, , USA. Geing Started with Ubuntu . can be downloaded for free from http:// ubuntu-manual.org/ or purchased from http://ubuntu-manual.org/buy/ gswu/en_US. A printed copy of this book can be ordered for the price of printing and delivery. We permit and even encourage you to distribute a copy of this book to colleagues, friends, family, and anyone else who might be interested. http://ubuntu-manual.org Revision number: Revision date: -- :: - Contents Prologue Welcome Ubuntu Philosophy A brief history of Ubuntu Is Ubuntu right for you? Contact details About the team Conventions used in this book Installation Geing Ubuntu Trying out Ubuntu Installing Ubuntu—Geing started Finishing Installation e Ubuntu Desktop Understanding the Ubuntu desktop Unity Using the Launcher e Dash Workspaces Managing windows Browsing files on your computer Files file manager Searching for files and folders on your computer Customizing your desktop Accessibility Session options Geing help Working with Ubuntu All the applications you need Geing online Browsing the web Reading and composing email Using instant messaging Viewing and editing photos Watching videos and movies Listening to audio and music Burning s and s Working with documents, spreadsheets, and presentations Ubuntu One Hardware Using your devices Hardware identification Displays Connecting and using your printer .