On Computing Mobile Agent Routes for Data Fusion in Distributed Sensor Networks
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Dr.K.G.Asha Manjari
DR.K.G.ASHA MANJARI PROFESSOR Department of studies in Earth science Centre for Advanced study in Precambrian Geology University of Mysore, Manasagangotri, Mysore-570 006 [email protected] +91-9448600554 ADDRESS Office Dept. of Studies in Earth science, University of Mysore, Manasagangotri, Mysore- 570 006, Karnataka, INDIA. +91-821-2419721, Mob: +91-9448600554 E-mail: [email protected] Residential 10/B, SPARSHA, 2nd Main, 2nd Cross, Bogadhi IInd Stage MYSORE-570 026, Karnataka, INDIA. ACADEMIC QUALIFICATIONS EDUCATIONAL QUALIFICATION: Bachelor of science, University of Mysore, Mysore, India- 1981 Master of science, University of Mysore, Mysore, India-First Rank-1983 Doctor of Philosophy, University of Mysore, Mysore, India-1989 Recipient of Mysore University Padmamma Salighrama Gold Medal and Prof. Nikkam’s Science Rotation Gold Medal in M.Sc.-1983 Young Scientist Travel Grant from DST and CSIR to attend IGCP 301at USA in 1992 Visiting Scientist at Rice University, Houston, USA 1992. Recipient of Young Scientist Research Project from DST 1994. Recipient of Prof. Satish Dhawan Young Scientist Award from KSCST, Government of Karnataka in 2006 Recipient of Bharat Jyoti Award from India International Friendship Society, New Delhi 2012 TITLE OF THE DOCTORAL THESIS Chemical Petrology of the Granulite and other associated rock types around Nilgiri hills Tamilnadu, India. VISITS ABROAD: USA, Sri Lanka , Singapore and China TEACHING EXPERIENCE: Twenty-six years to Post-graduate (Geology, Applied Geology & Earth Science & Resource Management) Guiding students for Ph.D degree. Successfully guided students for Minor and Major (dissertation work) Projects. MEMBERSHIP OF PROFESSIONAL BODIES Life Fellow and member of advisory committee of Mineralogical Society of India. -

Group Housing
LIST OF ALLOTED PROPERTIES DEPARTMENT NAME- GROUP HOUSING S# RID PROPERTY NO. APPLICANT NAME AREA 1 60244956 29/1013 SEEMA KAPUR 2,000 2 60191186 25/K-056 CAPT VINOD KUMAR, SAROJ KUMAR 128 3 60232381 61/E-12/3008/RG DINESH KUMAR GARG & SEEMA GARG 154 4 60117917 21/B-036 SUDESH SINGH 200 5 60036547 25/G-033 SUBHASH CH CHOPRA & SHWETA CHOPRA 124 6 60234038 33/146/RV GEETA RANI & ASHOK KUMAR GARG 200 7 60006053 37/1608 ATEET IMPEX PVT. LTD. 55 8 39000209 93A/1473 ATS VI MADHU BALA 163 9 60233999 93A/01/1983/ATS NAMRATA KAPOOR 163 10 39000200 93A/0672/ATS ASHOK SOOD SOOD 0 11 39000208 93A/1453 /14/AT AMIT CHIBBA 163 12 39000218 93A/2174/ATS ARUN YADAV YADAV YADAV 163 13 39000229 93A/P-251/P2/AT MAMTA SAHNI 260 14 39000203 93A/0781/ATS SHASHANK SINGH SINGH 139 15 39000210 93A/1622/ATS RAJEEV KUMAR 0 16 39000220 93A/6-GF-2/ATS SUNEEL GALGOTIA GALGOTIA 228 17 60232078 93A/P-381/ATS PURNIMA GANDHI & MS SHAFALI GA 200 18 60233531 93A/001-262/ATS ATUULL METHA 260 19 39000207 93A/0984/ATS GR RAVINDRA KUMAR TYAGI 163 20 39000212 93A/1834/ATS GR VIJAY AGARWAL 0 21 39000213 93A/2012/1 ATS KUNWAR ADITYA PRAKASH SINGH 139 22 39000211 93A/1652/01/ATS J R MALHOTRA, MRS TEJI MALHOTRA, ADITYA 139 MALHOTRA 23 39000214 93A/2051/ATS SHASHI MADAN VARTI MADAN 139 24 39000202 93A/0761/ATS GR PAWAN JOSHI 139 25 39000223 93A/F-104/ATS RAJESH CHATURVEDI 113 26 60237850 93A/1952/03 RAJIV TOMAR 139 27 39000215 93A/2074 ATS UMA JAITLY 163 28 60237921 93A/722/01 DINESH JOSHI 139 29 60237832 93A/1762/01 SURESH RAINA & RUHI RAINA 139 30 39000217 93A/2152/ATS CHANDER KANTA -

Another Global History of Science: Making Space for India and China
BJHS: Themes 1: 115–143, 2016. © British Society for the History of Science 2016. This is an Open Access article, distributed under the terms of the Creative Commons Attribution licence (http://creativecommons.org/licenses/by/4.0/), which permits unrestricted re-use, distribution, and reproduction in any medium, provided the original work is properly cited. doi:10.1017/bjt.2016.4 First published online 22 March 2016 Another global history of science: making space for India and China ASIF SIDDIQI* Abstract. Drawing from recent theoretical insights on the circulation of knowledge, this article, grounded in real-world examples, illustrates the importance of ‘the site’ as an analytical heur- istic for revealing processes, movements and connections illegible within either nation-centred histories or comparative national studies. By investigating place instead of project, the study reframes the birth of modern rocket developments in both China and India as fundamentally intertwined within common global networks of science. I investigate four seemingly discon- nected sites in the US, India, China and Ukraine, each separated by politics but connected and embedded in conduits that enabled the flow of expertise during (and in some cases despite) the Cold War. By doing so, it is possible to reconstruct an exemplar of a kind of global history of science, some of which takes place in China, some in India, and some else- where, but all of it connected. There are no discrete beginnings or endings here, merely points of intervention to take stock of processes in action. Each site produces objects and knowledge that contribute to our understanding of the other sites, furthering the overall narra- tive on Chinese and Indian efforts to formalize a ‘national’ space programme. -

Indian Institute of Space Science and Technology (IIST) NEWSLETTER Vol.4, No.1, January 2019
Indian Institute of Space Science and Technology (IIST) NEWSLETTER www.iist.ac.in Vol.4, No.1, January 2019 Director’s Message th Greetings! 6 IIST Convocation I am delighted to announce the re-launch of Indian Institute of Space Dr. V K Dadhwal, Director IIST's News Letter from January 2019. This Science and Technology (IIST) and Chairman BoM, IIST task has been assigned to a new Newsletter th conducted its 6 convocation along with Deans, Senior Committee which will regularly bringing on 18 t h July 2018 at Dr. Professors and Heads of the out two issues annually to share and widely Srinivasan Auditorium, VSSC. Departments. Dr. B N Suresh, circulate on the important events at the The convocation started at Chancellor, IIST opened the institute. Featured in the current issue are the 14.00 hrs with the academic convocation proceedings. host of activities and happenings at the procession led by Prof. A institute during 1st July 2018 to 31st December Chandrasekar, Registrar, IIST th and was joined by Dr. B N Dr. V K Dadhwal, Director 2018. Highlights of the issue include the 6 and Chairman, BoM, IIST in convocation held on 18th July 2018, Dr. Abdul Suresh, Chancellor, IIST, Dr. K S i v a n , C h a i r m a n , h i s w e l c o m e s p e e c h Kalam Lecture, Foundation day celebration, Governing Council, IIST, e l a b o r a t e d o n t h e International and National conferences, Chairman ISRO and Secretary achievements of IIST over the Seminars and workshops organised by us. -

6 Dr. A. P. J. Abdul Kalam Lecture Legion D'honneur' (2002) by the President of the French Republic, France
About the Speaker Dr Krishnaswamy Kasturirangan completed his BSc with Honours and MSc in Physics from Bombay University and received his Doctorate in Experimental High Energy Astronomy in 1971. His interests include astrophysics, space science and technology as well as science related policies. भारतीय अतं र वान एवं ौयोगक संथान Dr Kasturirangan was with the ISRO for over a period of nearly 35 years including nearly 10 years Indian Institute of Space Science and Technology as its Chairman from 1994-2003. He was a Member, Rajya Sabha (2003-2009) and concurrently the वलयमला, तवनंतपरम Director of NIAS, Bangalore. He served as a Member of the erstwhile Planning Commission (2009- ु Valiamala, Thiruvananthapuram 2014). Dr Kasturirangan served the Karnataka Knowledge Commission as its Chairman and was entrusted as the Chairman of the Committee for drafting the new National Education Policy. Presently he is the Chairman, Governing Board, IUCAA, Pune; Chancellor, Central University of Rajasthan; Chairperson, NIIT University, Neemrana; Member, Atomic Energy Commission; Emeritus Professor at NIAS, Bangalore and Honorary Distinguished Advisor, ISRO. Dr Kasturirangan is a Member of several International and National Science Academies. He is a Member of the International Astronomical Union, Fellow of TWAS, Honorary Fellow of the Cardiff University, UK and Academician of the Pontifical Academy of Sciences, Vatican City. Dr Kasturirangan is the only Indian to be conferred the Honorary Membership of the International Academy of Astronautics. Dr Kasturirangan was the first to occupy the Satish Dhawan Chair of Engineering Eminence (2015- 2017). He also occupied as the Chairman, BG, IIT, Chennai (2000-2005), Chairman, Council, IISc, Bangalore (2004-2015), Chancellor, JNU, New Delhi (2012-17), Chairman, Council, RRI, Bangalore (2000-2016). -

Handbook 2018-19
FACULTY OF ENGINEERING AND TECHNOLOGY Handbook 2018-19 SRM Nagar, Kattankulathur - 603 203 Kancheepuram District, Tamilnadu Telephone: 044- 27417499, 27417000 Fax: 044-27453903 URL: www.srmuniv.ac.in “Motivation gets you going, but, Discipline keeps you growing.” — John C. Maxwell Best Wishes for a Productive and Enjoyable Academic Year 2018–19 PERSONAL MEMORANDA 1. NAME : ________________________ 2. REGISTER NO. : ________________________ 3. YEAR & COURSE : ________________________ 4. BRANCH / SECTION : ________________________ 5. HOSTEL BLOCK & ROOM NO. : ________________________ 6. BUS PASS NO. : ________________________ 7. TRAIN PASS NO. : ________________________ 8. AADHAR CARD NO. : ________________________ 9. ADDRESS FOR COMMUNICATION : ________________________ ________________________ ________________________ 10. PERMANENT ADDRESS : ________________________ : ________________________ : ________________________ 11. MOBILE NO. : ________________________ 12. E-MAIL ID : ________________________ 13. DATE OF BIRTH : ________________________ 14. BLOOD GROUP : ________________________ 15. HEIGHT & WEIGHT : ________________________ 16. IDENTIFICATION MARKS : ________________________ FROM THE CHANCELLOR SRM Institute of Science and Technology engineering programs endeavor to be at the forefront of innovation. They also foster multi-disciplinary collaborations aimed at solving the most pressing global problems. Our mission is to seek solutions to global challenges by using the power of engineering principles, techniques and systems. We -

Satish Dhawan
CORRESPONDENCE Satish Dhawan The Special Section in Current Science, minded the Cabinet of the pending Committee (ICC) were SD’s initiatives 2020, 119(9), 1417–1488, celebrating the INSAT-I proposal. Instead of asking the and management innovations. SD’s pres- birth centenary of Satish Dhawan (SD), then post-election inactive main group, entation style ‘Red Book’, in A4-size the first Chairman of the Space Commis- the Cabinet, while approving APPLE landscape-orientation, on his group’s re- sion and Secretary, Department of Space investment, asked DoS to bring up the port and recommendations to the main (DoS), Government of India, besides INSAT-I proposal within a month. This group on INSAT-I is a classic document; several other leadership roles that he had was obviously facilitated by the ‘last ahead of its times in a style, that would played in institutions like the Indian In- ICS’ Cabinet Secretary Nirmal Mukher- later be generically known as a ‘power stitute of Science (IISc), Bangalore, that jee, who as Secretary Civil Aviation – point’ presentation. he headed, served, guided or set-up, is a under which Ministry IMD was then – Another important step for the imple- collector’s item. had got to understand the transformative mentation and oversight of the multi- Here, I would like to add an under- role and function of INSAT while partic- agency INSAT project was the creation recognized dimension to the seminal and ipating actively in the SD-led INSAT-I of the unique INSAT Coordination defining role that SD played in so many System Definition Sub-Group of Secreta- Committee of Secretaries chaired by Sec- aspects of satellite-based services for ries. -

513691 Journal of Space Law 35.1.Ps
JOURNAL OF SPACE LAW VOLUME 35, NUMBER 1 Spring 2009 1 JOURNAL OF SPACE LAW UNIVERSITY OF MISSISSIPPI SCHOOL OF LAW A JOURNAL DEVOTED TO SPACE LAW AND THE LEGAL PROBLEMS ARISING OUT OF HUMAN ACTIVITIES IN OUTER SPACE. VOLUME 35 SPRING 2009 NUMBER 1 Editor-in-Chief Professor Joanne Irene Gabrynowicz, J.D. Executive Editor Jacqueline Etil Serrao, J.D., LL.M. Articles Editors Business Manager P.J. Blount Michelle Aten Jason A. Crook Michael S. Dodge Senior Staff Assistant Charley Foster Melissa Wilson Gretchen Harris Brad Laney Eric McAdamis Luke Neder Founder, Dr. Stephen Gorove (1917-2001) All correspondence with reference to this publication should be directed to the JOURNAL OF SPACE LAW, P.O. Box 1848, University of Mississippi School of Law, University, Mississippi 38677; [email protected]; tel: +1.662.915.6857, or fax: +1.662.915.6921. JOURNAL OF SPACE LAW. The subscription rate for 2009 is $100 U.S. for U.S. domestic/individual; $120 U.S. for U.S. domestic/organization; $105 U.S. for non-U.S./individual; $125 U.S. for non-U.S./organization. Single issues may be ordered at $70 per issue. For non-U.S. airmail, add $20 U.S. Please see subscription page at the back of this volume. Copyright © Journal of Space Law 2009. Suggested abbreviation: J. SPACE L. ISSN: 0095-7577 JOURNAL OF SPACE LAW UNIVERSITY OF MISSISSIPPI SCHOOL OF LAW A JOURNAL DEVOTED TO SPACE LAW AND THE LEGAL PROBLEMS ARISING OUT OF HUMAN ACTIVITIES IN OUTER SPACE. VOLUME 35 SPRING 2009 NUMBER 1 CONTENTS Foreword .............................................. -

Artsand Philanthropy
Arts and Philanthropy Art is a universal language where visual expression evokes raw emotions and is thus an effective medium of conveying the very important message of peace “and harmony. Indeed, powerful images of paintings can leave an everlasting impact on peoples’ minds. Unlike words which are spoken, heard and sometimes forgotten, art on canvas stays forever and so does the message it conveys. — Satish Kumar Modi at the Inaugural Ceremony of the UNESCO Global Forum on the ‘Power of Peace’ ”at Bali, Indonesia. (cover image) — ‘Golden Life’, oil on canvas by Deepak Kumar, student of Final Year, Fine Art, IIFA Inspired by Lord Buddha’s life and teachings, the artist has tried to convey the fact that thoughts based on truthfulness, love and compassion — the ‘golden thoughts’— enable a person to lead a life full of peace, contentment and happiness — a ‘golden life’. (this page) — Collage of experiments — understanding the relation between space and form, Foundation Course, First Year, IIFA. Arts p International Institute of Fine Arts (IIFA) p Art exhibitions p New Arts University, National Capital Region “ p Art show on CNBC p — S.K. Modi Khoj International Artists’ workshop Prof. John Edwards of Charles Wallace Trust demonstrating drawing & colours to Final Year students at IIFA. International Institute of Fine Arts (IIFA) In July 2000 Satish and Abha Modi set up the International Institute of Fine Arts, IIFA, an institute that could nurture young artists, ignite their imagination and motivate them in the field of art and design. Their vision was to promote art and culture and provide quality education in conformity with global standards. -

Journal Abstract3.Pdf
Indian Journal of Cryogenics Vol. 34. No. 1-4, 2009 CONTENTS (Part -A of NSC-22 Proceedings) Preface Plenary Paper 1. Hundred years liquid helium 1 — A.T.A.M. de Waele 2. Cryogenics in launch vehicles and satellites 11 — Dathan M.C, Murthy M.B.N and Raghuram T.S 3. Nano-Kelvins in the laboratory 18 — Unnikrishnan. C. S. Cryo Component Development & Analysis 4. Development of plate and fin heat exchangers 27 — Mukesh Goyal, Rajendran Menon, Trilok Singh 5. Helium Liquefaction/Refrigeration System Based on Claude Cycle: A Parametric Study 33 — Rijo Jacob Thomas, Sanjay Basak, Parthasarathi Ghosh and Kanchan Chowdhury 6. Computation of liquid helium two phase flow in horizontal and vertical transfer lines 39 — Tejas Rane, Anindya Chakravarty, R K Singh and Trilok Singh 7. Experience in design and operation of a cryogenics system for argon cover gas 45 purification in LMFBRs — B.Muralidharan, M.G.Hemanath, K.Swaminathan, C.R.Venkatasubramani, A.Ashok kumar, Vivek Nema and K.K.Rajan 8. Design and implementation of an adiabatic demagnetization set up on a dilution refrigerator 51 to reach temperatures below 100mK — L. S. Sharath Chandra, Deepti Jain, Swati Pandya, P. N. Vishwakarma and V. Ganesan 9. Thermal design of recuperator heat exchangers for helium recondensation 57 systems using hybrid cryocoolers — G.Jagadish, G.S.V.L.Narasimham, Subhash Jacob 10. Experimental investigation on performance of aluminum tape and multilayer insulation 65 between 80 K and 4.2 K — Anup Choudhury, R S Meena, M Kumar, J Polinski, Maciej Chorowski and T S Datta 11. Finite element analysis of a spiral flexure bearing for miniature linear compressor 71 — Gawali B. -

Recipients of Life Time Achievement Awards
RECIPIENTS OF LIFE TIME ACHIEVEMENT AWARDS 2017 Mr. Azim Premji Mr. Azim Premji, Chairman, Wipro Limited was responsible for guiding Wipro through four decades of diversification and growth to finally emerge as one of the global leaders in the software industry. He is informally known as the Czar of the Indian IT Industry. In 2001, he founded Azim Premji Foundation, a non-profit organisation, with a vision to significantly contribute to achieving quality universal education that facilitates a just, equitable, humane and sustainable society. Prof. TK Ghose Prof. TK Ghose, formerly Founder Chair of Department of Biochemical Engineering and Biotechnology, IIT Delhi is a pioneer academician in creating awareness of the discipline of Biochemical Engineering and Biotechnology in the Country. His contributions enabled Govt. of India to create the DBT under HRD Ministry for further progress of this field. 2016 Dr. Prem Shanker Goel Dr. PS Goel, born on April 20, 1947 is presently Honorary Distinguished Professor, ISRO Hqrs. and Raja Ramanna Chair Visiting Professor, National Institute of Advanced Studies, Bangalore . He was Formerly Secretary, Ministry of Earth Sciences and Chairman, Earth Commission; and Director, ISRO Satellite Centre, Bangalore and Formerly Chairman, Recruitment and Assessment Centre, DRDO, Ministry of Defence, Govt. of India Delhi. Dr Goel has contributed immensely to the advancement of satellite technology in India. His array of achievements extended much beyond satellite technology into space science -the Chandrayaan -1 and Astrosat Missions, Launch Vehicles- ASLV & PSLV, Light Combat Aircraft; Earth sciences; ocean development; fuel cells; disaster warning; meteorology and National security. He received several prestigious awards and honours including the Padma Shri Award by President of India. -
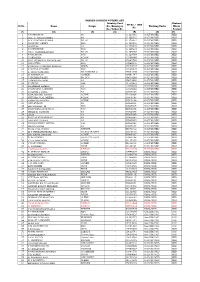
Sl.No. Name Desgn. Identity Card No./Employee No./Token No. PF No./ NPS No. Working Under Station Where Posted (1) (2) (3)
NANDED DIVISION-VOTERS LIST Identity Card Station PF No./ NPS Sl.No. Name Desgn. No./Employee Working Under Where No. No./Token No. Posted (1) (2) (3) (4) (5) (6) (7) 1 S.S.SRINIVAS SO - 01121091 Sr.DFM/NED NED 2 Smt. C. THILOTAMMA AA - 01128103 Sr.DFM/NED NED 3 M.V.V.SATISH KUMAR SO (A) - 01128814 Sr.DFM/NED NED 4 NAGESH LOKREY SSO - 01128905 Sr.DFM/NED NED 5 D.VITTAL AA - 01129235 Sr.DFM/NED NED 6 K.SURENDER SSO - 01129272 Sr.DFM/NED NED 7 CH.V. SUBRAMANYAM SO (A) - 01129363 Sr.DFM/NED NED 8 P.BALAYOGI SSO - 01129764 Sr.DFM/NED NED 9 V.SRIDHAR ACLRK - 01509895 Sr.DFM/NED NED 10 SMT. GOMATHY NATARAJAN SO (A) - 02662280 Sr.DFM/NED NED 11 G.RAJITHA SSO - 03968005 Sr.DFM/NED NED 12 S.RAGHU CHANDRA SEKHAR SE(IT) - 05504557 Sr.DFM/NED NED 13 S.GAYAZ AHAMED SSO - 05508678 Sr.DFM/NED NED 14 K. TIRUPATHI RAO SR CASHIER-2 - 05683336 Sr.DFM/NED NED 15 M.NAGARAJU CASHIR - 09461747 Sr.DFM/NED NED 16 P.HAZARAT BABU SR.DCP - 09810286 Sr.DFM/NED NED 17 P.SWARUPA RANI AA - 09873995 Sr.DFM/NED NED 18 K.ARUNA JAA - 11750250 Sr.DFM/NED NED 19 SHAMEEM AHMED AA - 11900039 Sr.DFM/NED NED 20 V.SUVARNA LAKSHMI SSO - 11900260 Sr.DFM/NED NED 21 AVANTHI J PATIL AA - IE070020 Sr.DFM/NED NED 22 K.RAJENDER REDDY ACLRK - IE100068 Sr.DFM/NED NED 23 SHIVARAJ LAL MEENA ACLRK - IK050195 Sr.DFM/NED NED 24 KAMLESH MEENA ACLRK - IK050196 Sr.DFM/NED NED 25 ANIL KUMAR AA - IK060084 Sr.DFM/NED NED 26 RAJ KUMAR .