Powershell Is Dead… Long Live C Sharp
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Top 40 .NET Interview Questions & Answers
https://career.guru99.com/ Guru99 Provides FREE ONLINE TUTORIAL on Various courses like Java | MIS | MongoDB | BigData | Cassandra | Web Services ------------------------------------------------------------------------------------------------------------------------------- SQLite | JSP | Informatica | Accounting | SAP Training | Python ------------------------------------------------------------------------------------------------------------------------------- Excel | ASP Net | HBase | Testing | Selenium | CCNA | NodeJS ------------------------------------------------------------------------------------------------------------------------------- TensorFlow | Data Warehouse | R Programming | Live Projects | DevOps ------------------------------------------------------------------------------------------------------------------------------- Top 40 .NET Interview Questions & Answers 1) Explain what is .NET Framework? The.Net Framework is developed by Microsoft. It provides technologies and tool that is required to build Networked Applications as well as Distributed Web Services and Web Applications. 2) What does .NET Framework provides? .NET Framework renders the necessary compile time and run time foundation to build and run any language that conforms to the Common Language Specification (CLS). 3) Mention what are main components of .Net framework? The main components of .Net framework are Common Language Runtime (CLR) .Net Framework Class Library (FCL) Application Domains Runtime Host Cross-Language Interoperability Side-by-Side Execution -

Moscow ML .Net Owner's Manual
Moscow ML .Net Owner's Manual Version 0.9.0 of November 2003 Niels Jørgen Kokholm, IT University of Copenhagen, Denmark Peter Sestoft, Royal Veterinary and Agricultural University, Copenhagen, Denmark This document describes Moscow ML .Net 0.9.0, a port of Moscow ML 2.00 to the .Net platform. The focus is on how Moscow ML .Net differs from Moscow ML 2.0. Three other documents, the Moscow ML Owner’s Manual [7], the Moscow ML Language Overview [5] and the Moscow ML Library Documentation [6] describe general aspects of the Moscow ML system. Moscow ML implements Standard ML (SML), as defined in the 1997 Definition of Standard ML, including the SML Modules language and some extensions. Moreover, Moscow ML supports most re- quired parts of the SML Basis Library. It supports separate compilation and the generation of stand-alone executables. The reader is assumed to be familiar with the .Net platform [2]. Contents 1 Characteristics of Moscow ML .Net 2 1.1 Compiling and linking 2 1.2 Command-line options 3 1.3 Additional primitives in the built-in units 3 1.4 The libraries 4 2 Installation 5 3 External programming interface 5 3.1 How external assemblies are found and loaded 5 3.2 How to call a .Net static method from Moscow ML .Net. 6 3.2.1 An example 7 3.2.2 Passing arguments and using results 7 3.2.3 Representation of ML Values 8 3.2.4 Notes 8 3.2.5 An experimental auto-marshalling import mechanism: clr_val 8 3.3 How to call an ML function from .Net 10 3.3.1 Example 10 3.3.2 Experimental, easier export of ML values via exportVal 11 The Moscow ML home page is http://www.dina.kvl.dk/~sestoft/mosml.html 1 1 Characteristics of Moscow ML .Net Unlike most other ports of Moscow ML, this port is not based on porting the Caml Light runtime, but is based on the creation of a new backend that generates .Net CIL code. -

The Microsoft Way: COM, OLE/Activex, COM+, and .NET CLR
8557 Chapter 15 p329-380 8/10/02 12:24 pm Page 329 CHAPTER FIFTEEN The Microsoft way: COM, OLE/ActiveX, COM+, and .NET CLR In a sense, Microsoft is taking the easiest route. Instead of proposing a global standard and hoping to port its own systems to it, it continually re-engineers its existing application and platform base. Component technology is intro- duced gradually, gaining leverage from previous successes, such as the original Visual Basic controls (VBX – non-object-oriented components!), object link- ing and embedding (OLE), OLE database connectivity (ODBC), ActiveX, Microsoft Transaction Server (MTS), or active server pages (ASP). In the standards arena, Microsoft focuses mostly on internet (IETF) and web (W3C) standards. More recently, some of its .NET specifications (CLI and C#) where adopted by ECMA – a European standards body with a fast track to ISO (ECMA, 2001a, 2001b). Microsoft is not trying to align its approaches with OMG or Java standards. While Java figured prominently in Microsoft’s strategy for a while, it has been relegated to a mere continuation of support of its older Visual J++ product – in part as a result of a settlement between Sun and Microsoft. In addition, under the name Visual J# .NET, Microsoft offers a migration tool to .NET, primarily targeting users of Visual J++ 6.0. As part of the .NET initiative, Microsoft is promoting language neutrality as a major tenet of CLR and aims to establish a new language, C#. C# adopts many of the successful traits of Java, while adding several distinctive features of its own (such as value types) and not supporting key Java features (such as inner classes). -

Appendixes APPENDIX A
PART 8 Appendixes APPENDIX A COM and .NET Interoperability The goal of this book was to provide you with a solid foundation in the C# language and the core services provided by the .NET platform. I suspect that when you contrast the object model provided by .NET to that of Microsoft’s previous component architecture (COM), you’ll no doubt be con- vinced that these are two entirely unique systems. Regardless of the fact that COM is now considered to be a legacy framework, you may have existing COM-based systems that you would like to inte- grate into your new .NET applications. Thankfully, the .NET platform provides various types, tools, and namespaces that make the process of COM and .NET interoperability quite straightforward. This appendix begins by examin- ing the process of .NET to COM interoperability and the related Runtime Callable Wrapper (RCW). The latter part of this appendix examines the opposite situation: a COM type communicating with a .NET type using a COM Callable Wrapper (CCW). ■Note A full examination of the .NET interoperability layer would require a book unto itself. If you require more details than presented in this appendix, check out my book COM and .NET Interoperability (Apress, 2002). The Scope of .NET Interoperability Recall that when you build assemblies using a .NET-aware compiler, you are creating managed code that can be hosted by the common language runtime (CLR). Managed code offers a number of ben- efits such as automatic memory management, a unified type system (the CTS), self-describing assemblies, and so forth. As you have also seen, .NET assemblies have a particular internal compo- sition. -

Sitecore CMS 7.0 Installation Guide Rev: 2014-10-21
Sitecore CMS 7.0 Installation Guide Rev: 2014-10-21 Sitecore CMS 7.0 Installation Guide Installation guide for administrators and developers Sitecore® is a registered trademark. All other brand and product names are the property of their respective holders. The contents of this document are the property of Sitecore. Copyright © 2001-2014 Sitecore. All rights reserved. Sitecore CMS 7.0 Installation Guide Table of Contents Chapter 1 Introduction ................................................................................................................................ 4 1.1 Getting Started .............................................................................................................................. 5 1.2 Preparing to Install Sitecore CMS 7.0 ........................................................................................... 6 Chapter 2 Sitecore CMS 7.0 Requirements ............................................................................................... 7 2.1 Sitecore Hosting Environment Requirements ............................................................................... 8 2.1.1 IIS Requirements....................................................................................................................... 8 2.1.2 Operating System Requirements .............................................................................................. 8 2.1.3 .NET Framework Requirements ................................................................................................ 9 2.1.4 Visual Studio Requirements -

Powershell – Cybersecurity Perspective
CERT-EU Security Whitepaper 2019-001 PowerShell – Cybersecurity Perspective Ciprian-Nicolae BOLDEA, Krzysztof SOCHA ver. 1.0 July 19, 2019 TLP: WHITE Contents 1 Summary 2 2 Background 2 3 Important Features for Cybersecurity2 3.1 Execution Policies.................................... 2 3.2 PowerShell Versions.................................. 3 3.3 PowerShell Language Modes.............................. 3 3.4 Signing......................................... 3 3.5 Securing Privileged Access............................... 3 3.6 PowerShell Logging................................... 4 3.7 Transcription...................................... 4 3.8 Ways of Running PowerShell.............................. 4 3.9 PowerShell for Remote Administration........................ 4 4 Prevention and Detection of PowerShell Attacks4 4.1 Execution Policies Bypass............................... 4 4.2 PowerShell Downgrade Attacks............................ 5 4.3 Migration to Windows 10............................... 5 4.4 Advanced Threat Protection.............................. 6 4.5 Advanced Threat Analytics............................... 6 4.6 Detection of attacks................................... 6 5 Conclusions 6 6 Annex A – Definitions7 7 Annex B – Log Sources and Events for the Detection of PowerShell Attacks7 7.1 Relevant Windows Events............................... 7 7.1.1 Windows PowerShell event log entries indicating the start and stop of PowerShell activity............................... 7 7.1.2 System event log entries indicating a configuration -

Unit I - Visual Basic .Net and Frame Work
UNIT I - VISUAL BASIC .NET AND FRAME WORK The Common Type System- The Common Language Specification- The Common Language Runtime -Microsoft Intermediate Language- Metadata- Executable Code-Managed Execution- Side−by−Side Execution- Understanding Assemblies- Assembly- - Strong Names Introduction to Visual Basic .NET Development environment. COMMON TYPE SYSTEM A key piece of functionality that enables Multiple Language Support is a Common Type System, in which all commonly used data types, even base types such as Longs and Booleans are actually implemented as objects. Since all languages are using the same library of types, calling one language from another doesn't require type conversion or weird calling conventions. For example, what we called an Integer in VB6 and earlier, is now known as a Short in Visual Basic.NET. The common type system defines how types are declared, used, and managed in the runtime, and is also an important part of the runtime's support for cross-language integration. The common type system performs the following functions: Establishes a framework that helps enable cross-language integration, type safety, and high performance code execution. Provides an object-oriented model that supports the complete implementation of many programming languages. Defines rules that languages must follow, which helps ensure that objects written in different languages can interact with each other. THE COMMON LANGUAGE SPECIFICATION Languages that fit into.NET must satisfy the Common Language Specification (CLS), which sets the constraints the languages must meet. If a language adheres to this spec, it gets an appropriate level of language interoperability. There are actually three categories of compliance to the CLS that .NET languages can subscribe to. -

Dot Net Interview Questions and Answers Guide
Dot Net Interview Questions And Answers Guide. Global Guideline. http://www.globalguideline.com/ Dot Net Interview Questions And Answers Dot Net Job Interview Preparation Guide. Question # 1 How many languages .NET is supporting now? Answer:- When .NET was introduced it came with several languages. VB.NET, C#, COBOL and Perl, etc. The site DotNetLanguages.Net says 44 languages are supported by .NET Read More Answers. Question # 2 How is .NET able to support multiple languages? Answer:- A language should comply with the Common Language Runtime standard to become a .NET language. In .NET, code is compiled to Microsoft Intermediate Language (MSIL for short). This is called as Managed Code. This Managed code is run in .NET environment. So after compilation to this IL the language is not a barrier. A code can call or use a function written in another language. Read More Answers. Question # 3 How ASP .NET different from ASP? Answer:- Scripting is separated from the HTML, Code is compiled as a DLL, these DLLs can be executed on the server. Read More Answers. Question # 4 What is smart navigation in .NET? Answer:- The cursor position is maintained when the page gets refreshed due to the server side validation and the page gets refreshed. Read More Answers. Question # 5 What is view state in .NET? Answer:- The web is stateless. But in ASP.NET, the state of a page is maintained in the in the page itself automatically. How? The values are encrypted and saved in hidden controls. this is done automatically by the ASP.NET. This can be switched off / on for a single control Read More Answers. -

Office Add-Ins Sharepoint Security Onenote 2010
THE MICROSOFT JOURNAL FOR DEVELOPERS JULY 2010 VOL 25 NO 7 OFFICE ADD-INS COLUMNS 3 Solutions for Accessing SharePoint Data in Offi ce 2010 EDITOR’S NOTE Donovan Follette and Paul Stubbs . 20 Over-Educated, Yet Under-Qualifi ed? SHAREPOINT SECURITY Keith Ward page 4 Trim SharePoint Search Results for Better Security CUTTING EDGE Ashley Elenjickal and Pooja Harjani . 36 Expando Objects in C# 4.0 Dino Esposito page 6 ONENOTE 2010 DATA POINTS Creating OneNote 2010 Extensions with the OneNote Object Model Windows Azure Table Andy Gray . 44 Storage–Not Your Father’s Database Julie Lerman page 16 OFFICE SERVICES SECURITY BRIEFS Merging Word Documents on the Server Side with SharePoint 2010 View State Security Manvir Singh and Ankush Bhatia . 50 Bryan Sullivan page 82 SMART CLIENT THE WORKING PROGRAMMER Building Distributed Apps with NHibernate and Rhino Service Bus Going NoSQL with MongoDB, Oren Eini . 58 Part 3 Ted Neward page 88 C# 4.0 UI FRONTIERS New C# Features in the .NET Framework 4 The Fluid UI in Silverlight 4 Chris Burrows . 68 Charles Petzold page 92 DON’T GET ME STARTED DESIGN PATTERNS Rejectionists Rejected Problems and Solutions with Model-View-ViewModel David Platt page 96 Robert McCarter . 74 Untitled-5 2 3/5/10 10:16 AM Sure, Visual Studio 2010 has a lot of great functionality— we’re excited that it’s only making our User Interface components even better! We’re here to help you go beyond what Visual Studio 2010 gives you so you can create Killer Apps quickly, easily and without breaking a sweat! Go to infragistics.com/beyondthebox today to expand your toolbox with the fastest, best-performing and most powerful UI controls available. -

NET Framework Rootkits: Backdoors Inside Your Framework
.NET Framework Rootkits: Backdoors inside your Framework March, 2009 (Revised) Erez Metula [email protected] [email protected] 1 .NET Framework Rootkits – Backdoors Inside Your Framework Table of content TABLE OF CONTENT .........................................................................................................................2 ABSTRACT ............................................................................................................................................3 INTRODUCTION..................................................................................................................................4 HOW CAN THE FRAMEWORK BE CHANGED?..........................................................................................4 MODIFYING THE FRAMEWORK CORE .......................................................................................6 OVERVIEW - STEPS & TOOLS FOR CHANGING THE FRAMEWORK ...........................................................6 LOCATE THE DLL IN THE GAC ............................................................................................................6 ANALYZE THE DLL..............................................................................................................................7 DECOMPILE THE DLL USING ILDASM ...................................................................................................9 MODIFYING THE MSIL CODE .............................................................................................................10 RECOMPILE -

Dot Net Interview Questions
Dear Friends, Hi I am satish marwat, this documents contains all the important questions that usually asked during the .NET interview, I had downloaded all the material from the Internet from various websites and collected to form a single film, u will find few repeated questions also, all the material are from the various websites, so I had just bind it into a single file. So for any mistake I am not responsible, this is just for the view purpose. My view was only to collect a material to a single file. Please, if u find any mistake in this file, please contact me to my email address [email protected], so that I can able to correct it. ALL THE BEST Thanks Satish J Satish Marwat Dot Net Web Resources [email protected] 1 Page .NET FRAME WORK Introduction 1.1 What is .NET? .NET is a general-purpose software development platform, similar to Java. At its core is a virtual machine that turns intermediate language (IL) into machine code. High-level language compilers for C#, VB.NET and C++ are provided to turn source code into IL. C# is a new programming language, very similar to Java. An extensive class library is included, featuring all the functionality one might expect from a contempory development platform - windows GUI development (Windows Form s), database access (ADO.NET), web development (ASP.NET), web services, XML etc. 1.2 When was .NET announced? Bill Gates delivered a keynote at Forum 2000, held June 22, 2000, outlining the .NET 'vision'. The July 2000 PDC had a number of sessions on .NET technology, and delegates were given CDs containing a pre-release version of the .NET framework/SDK and Visual Studio.NET. -
Comparing Java and .NET Security
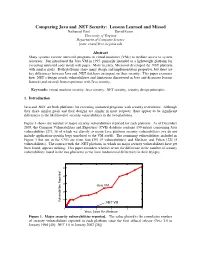
Comparing Java and .NET Security: Lessons Learned and Missed Nathanael Paul David Evans University of Virginia Department of Computer Science [nate, evans ]@cs.virginia.edu Abstract Many systems execute untrusted programs in virtual machines (VMs) to mediate access to system resources. Sun introduced the Java VM in 1995, primarily intended as a lightweight platform for executing untrusted code inside web pages. More recently, Microsoft developed the .NET platform with similar goals. Both platforms share many design and implementation properties, but there are key differences between Java and .NET that have an impact on their security. This paper examines how .NET’s design avoids vulnerabilities and limitations discovered in Java and discusses lessons learned (and missed) from experience with Java security. Keywords: virtual machine security, Java security, .NET security, security design principles. 1. Introduction Java and .NET are both platforms for executing untrusted programs with security restrictions. Although they share similar goals and their designs are similar in most respects, there appear to be significant differences in the likelihood of security vulnerabilities in the two platforms. Figure 1 shows the number of major security vulnerabilities reported for each platform. As of December 2005, the Common Vulnerabilities and Exposures (CVE) database contains 150 entries concerning Java vulnerabilities [27], 38 of which we classify as major Java platform security vulnerabilities (we do not include application-specific bugs unrelated to the VM itself). The remaining vulnerabilities included in Figure 1 but not in the CVE are from Sun [39] (9 vulnerabilities) and McGraw and Felten [22] (5 vulnerabilities). The contrast with the .NET platform, in which no major security vulnerabilities have yet been found, appears striking.