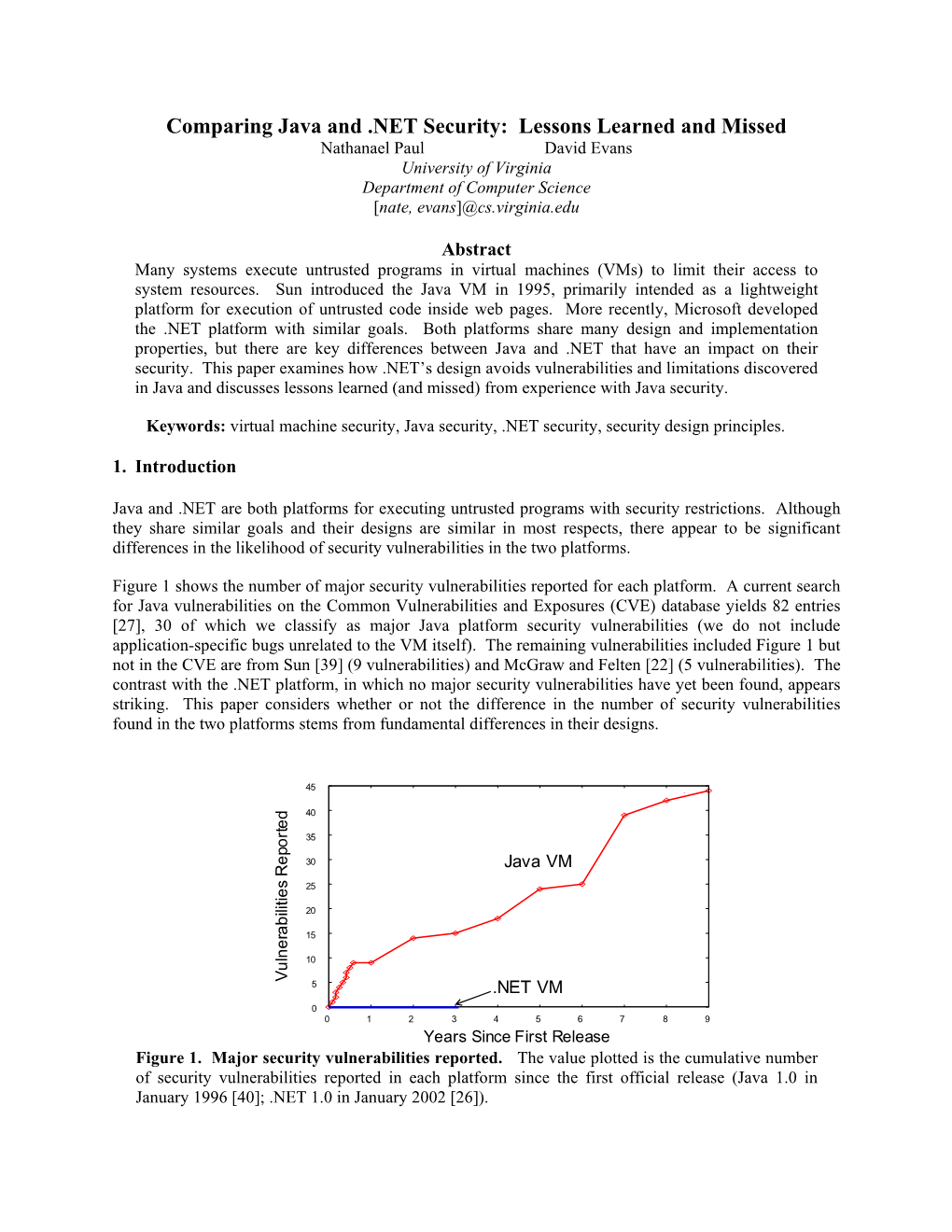
Comparing Java and .NET Security
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Top 40 .NET Interview Questions & Answers
https://career.guru99.com/ Guru99 Provides FREE ONLINE TUTORIAL on Various courses like Java | MIS | MongoDB | BigData | Cassandra | Web Services ------------------------------------------------------------------------------------------------------------------------------- SQLite | JSP | Informatica | Accounting | SAP Training | Python ------------------------------------------------------------------------------------------------------------------------------- Excel | ASP Net | HBase | Testing | Selenium | CCNA | NodeJS ------------------------------------------------------------------------------------------------------------------------------- TensorFlow | Data Warehouse | R Programming | Live Projects | DevOps ------------------------------------------------------------------------------------------------------------------------------- Top 40 .NET Interview Questions & Answers 1) Explain what is .NET Framework? The.Net Framework is developed by Microsoft. It provides technologies and tool that is required to build Networked Applications as well as Distributed Web Services and Web Applications. 2) What does .NET Framework provides? .NET Framework renders the necessary compile time and run time foundation to build and run any language that conforms to the Common Language Specification (CLS). 3) Mention what are main components of .Net framework? The main components of .Net framework are Common Language Runtime (CLR) .Net Framework Class Library (FCL) Application Domains Runtime Host Cross-Language Interoperability Side-by-Side Execution -

IJIRT | Volume 2 Issue 6 | ISSN: 2349-6002
© November 2015 | IJIRT | Volume 2 Issue 6 | ISSN: 2349-6002 .Net Surbhi Bhardwaj Dronacharya College of Engineering Khentawas, Haryana INTRODUCTION as smartphones. Additionally, .NET Micro .NET Framework (pronounced dot net) is Framework is targeted at severely resource- a software framework developed by Microsoft that constrained devices. runs primarily on Microsoft Windows. It includes a large class library known as Framework Class Library (FCL) and provides language WHAT IS THE .NET FRAMEWORK? interoperability(each language can use code written The .NET Framework is a new and revolutionary in other languages) across several programming platform created by Microsoft for languages. Programs written for .NET Framework developingapplications. execute in a software environment (as contrasted to hardware environment), known as Common It is a platform for application developers. Language Runtime (CLR), an application virtual It is a Framework that supports Multiple machine that provides services such as Language and Cross language integration. security, memory management, and exception handling. FCL and CLR together constitute .NET IT has IDE (Integrated Development Framework. Environment). FCL provides user interface, data access, database Framework is a set of utilities or can say connectivity, cryptography, web building blocks of your application system. application development, numeric algorithms, .NET Framework provides GUI in a GUI and network communications. Programmers manner. produce software by combining their own source code with .NET Framework and other libraries. .NET is a platform independent but with .NET Framework is intended to be used by most new help of Mono Compilation System (MCS). applications created for the Windows platform. MCS is a middle level interface. Microsoft also produces an integrated development .NET Framework provides interoperability environment largely for .NET software called Visual between languages i.e. -

Moscow ML .Net Owner's Manual
Moscow ML .Net Owner's Manual Version 0.9.0 of November 2003 Niels Jørgen Kokholm, IT University of Copenhagen, Denmark Peter Sestoft, Royal Veterinary and Agricultural University, Copenhagen, Denmark This document describes Moscow ML .Net 0.9.0, a port of Moscow ML 2.00 to the .Net platform. The focus is on how Moscow ML .Net differs from Moscow ML 2.0. Three other documents, the Moscow ML Owner’s Manual [7], the Moscow ML Language Overview [5] and the Moscow ML Library Documentation [6] describe general aspects of the Moscow ML system. Moscow ML implements Standard ML (SML), as defined in the 1997 Definition of Standard ML, including the SML Modules language and some extensions. Moreover, Moscow ML supports most re- quired parts of the SML Basis Library. It supports separate compilation and the generation of stand-alone executables. The reader is assumed to be familiar with the .Net platform [2]. Contents 1 Characteristics of Moscow ML .Net 2 1.1 Compiling and linking 2 1.2 Command-line options 3 1.3 Additional primitives in the built-in units 3 1.4 The libraries 4 2 Installation 5 3 External programming interface 5 3.1 How external assemblies are found and loaded 5 3.2 How to call a .Net static method from Moscow ML .Net. 6 3.2.1 An example 7 3.2.2 Passing arguments and using results 7 3.2.3 Representation of ML Values 8 3.2.4 Notes 8 3.2.5 An experimental auto-marshalling import mechanism: clr_val 8 3.3 How to call an ML function from .Net 10 3.3.1 Example 10 3.3.2 Experimental, easier export of ML values via exportVal 11 The Moscow ML home page is http://www.dina.kvl.dk/~sestoft/mosml.html 1 1 Characteristics of Moscow ML .Net Unlike most other ports of Moscow ML, this port is not based on porting the Caml Light runtime, but is based on the creation of a new backend that generates .Net CIL code. -

NET Framework
Advanced Windows Programming .NET Framework based on: A. Troelsen, Pro C# 2005 and .NET 2.0 Platform, 3rd Ed., 2005, Apress J. Richter, Applied .NET Frameworks Programming, 2002, MS Press D. Watkins et al., Programming in the .NET Environment, 2002, Addison Wesley T. Thai, H. Lam, .NET Framework Essentials, 2001, O’Reilly D. Beyer, C# COM+ Programming, M&T Books, 2001, chapter 1 Krzysztof Mossakowski Faculty of Mathematics and Information Science http://www.mini.pw.edu.pl/~mossakow Advanced Windows Programming .NET Framework - 2 Contents The most important features of .NET Assemblies Metadata Common Type System Common Intermediate Language Common Language Runtime Deploying .NET Runtime Garbage Collection Serialization Krzysztof Mossakowski Faculty of Mathematics and Information Science http://www.mini.pw.edu.pl/~mossakow Advanced Windows Programming .NET Framework - 3 .NET Benefits In comparison with previous Microsoft’s technologies: Consistent programming model – common OO programming model Simplified programming model – no error codes, GUIDs, IUnknown, etc. Run once, run always – no "DLL hell" Simplified deployment – easy to use installation projects Wide platform reach Programming language integration Simplified code reuse Automatic memory management (garbage collection) Type-safe verification Rich debugging support – CLR debugging, language independent Consistent method failure paradigm – exceptions Security – code access security Interoperability – using existing COM components, calling Win32 functions Krzysztof -

The Microsoft Way: COM, OLE/Activex, COM+, and .NET CLR
8557 Chapter 15 p329-380 8/10/02 12:24 pm Page 329 CHAPTER FIFTEEN The Microsoft way: COM, OLE/ActiveX, COM+, and .NET CLR In a sense, Microsoft is taking the easiest route. Instead of proposing a global standard and hoping to port its own systems to it, it continually re-engineers its existing application and platform base. Component technology is intro- duced gradually, gaining leverage from previous successes, such as the original Visual Basic controls (VBX – non-object-oriented components!), object link- ing and embedding (OLE), OLE database connectivity (ODBC), ActiveX, Microsoft Transaction Server (MTS), or active server pages (ASP). In the standards arena, Microsoft focuses mostly on internet (IETF) and web (W3C) standards. More recently, some of its .NET specifications (CLI and C#) where adopted by ECMA – a European standards body with a fast track to ISO (ECMA, 2001a, 2001b). Microsoft is not trying to align its approaches with OMG or Java standards. While Java figured prominently in Microsoft’s strategy for a while, it has been relegated to a mere continuation of support of its older Visual J++ product – in part as a result of a settlement between Sun and Microsoft. In addition, under the name Visual J# .NET, Microsoft offers a migration tool to .NET, primarily targeting users of Visual J++ 6.0. As part of the .NET initiative, Microsoft is promoting language neutrality as a major tenet of CLR and aims to establish a new language, C#. C# adopts many of the successful traits of Java, while adding several distinctive features of its own (such as value types) and not supporting key Java features (such as inner classes). -

Programming with Windows Forms
A P P E N D I X A ■ ■ ■ Programming with Windows Forms Since the release of the .NET platform (circa 2001), the base class libraries have included a particular API named Windows Forms, represented primarily by the System.Windows.Forms.dll assembly. The Windows Forms toolkit provides the types necessary to build desktop graphical user interfaces (GUIs), create custom controls, manage resources (e.g., string tables and icons), and perform other desktop- centric programming tasks. In addition, a separate API named GDI+ (represented by the System.Drawing.dll assembly) provides additional types that allow programmers to generate 2D graphics, interact with networked printers, and manipulate image data. The Windows Forms (and GDI+) APIs remain alive and well within the .NET 4.0 platform, and they will exist within the base class library for quite some time (arguably forever). However, Microsoft has shipped a brand new GUI toolkit called Windows Presentation Foundation (WPF) since the release of .NET 3.0. As you saw in Chapters 27-31, WPF provides a massive amount of horsepower that you can use to build bleeding-edge user interfaces, and it has become the preferred desktop API for today’s .NET graphical user interfaces. The point of this appendix, however, is to provide a tour of the traditional Windows Forms API. One reason it is helpful to understand the original programming model: you can find many existing Windows Forms applications out there that will need to be maintained for some time to come. Also, many desktop GUIs simply might not require the horsepower offered by WPF. -

Appendixes APPENDIX A
PART 8 Appendixes APPENDIX A COM and .NET Interoperability The goal of this book was to provide you with a solid foundation in the C# language and the core services provided by the .NET platform. I suspect that when you contrast the object model provided by .NET to that of Microsoft’s previous component architecture (COM), you’ll no doubt be con- vinced that these are two entirely unique systems. Regardless of the fact that COM is now considered to be a legacy framework, you may have existing COM-based systems that you would like to inte- grate into your new .NET applications. Thankfully, the .NET platform provides various types, tools, and namespaces that make the process of COM and .NET interoperability quite straightforward. This appendix begins by examin- ing the process of .NET to COM interoperability and the related Runtime Callable Wrapper (RCW). The latter part of this appendix examines the opposite situation: a COM type communicating with a .NET type using a COM Callable Wrapper (CCW). ■Note A full examination of the .NET interoperability layer would require a book unto itself. If you require more details than presented in this appendix, check out my book COM and .NET Interoperability (Apress, 2002). The Scope of .NET Interoperability Recall that when you build assemblies using a .NET-aware compiler, you are creating managed code that can be hosted by the common language runtime (CLR). Managed code offers a number of ben- efits such as automatic memory management, a unified type system (the CTS), self-describing assemblies, and so forth. As you have also seen, .NET assemblies have a particular internal compo- sition. -

Diploma Thesis
Faculty of Computer Science Chair for Real Time Systems Diploma Thesis Porting DotGNU to Embedded Linux Author: Alexander Stein Supervisor: Jun.-Prof. Dr.-Ing. Robert Baumgartl Dipl.-Ing. Ronald Sieber Date of Submission: May 15, 2008 Alexander Stein Porting DotGNU to Embedded Linux Diploma Thesis, Chemnitz University of Technology, 2008 Abstract Programming PLC systems is limited by the provided libraries. In contrary, hardware-near programming needs bigger eorts in e. g. initializing the hardware. This work oers a foundation to combine advantages of both development sides. Therefore, Portable.NET from the DotGNU project has been used, which is an im- plementation of CLI, better known as .NET. The target system is the PLCcore- 5484 microcontroller board, developed by SYS TEC electronic GmbH. Built upon the porting, two variants to use interrupt routines withing the Portabe.NET runtime environment have been analyzed. Finally, the reaction times to occuring interrupt events have been examined and compared. Die Programmierung für SPS-Systeme ist durch die gegebenen Bibliotheken beschränkt, während hardwarenahe Programmierung einen gröÿeren Aufwand durch z.B. Initialisierungen hat. Diese Arbeit bietet eine Grundlage, um die Vorteile bei- der Entwicklungsseiten zu kombinieren. Dafür wurde Portable.NET des DotGNU- Projekts, eine Implementierung des CLI, bekannter unter dem Namen .NET, be- nutzt. Das Zielsystem ist das PLCcore-5484 Mikrocontrollerboard der SYS TEC electronic GmbH. Aufbauend auf der Portierung wurden zwei Varianten zur Ein- bindung von Interrupt-Routinen in die Portable.NET Laufzeitumgebung untersucht. Abschlieÿend wurden die Reaktionszeiten zu eintretenden Interrupts analysiert und verglichen. Acknowledgements I would like to thank some persons who had inuence and supported me in my work. -

Sitecore CMS 7.0 Installation Guide Rev: 2014-10-21
Sitecore CMS 7.0 Installation Guide Rev: 2014-10-21 Sitecore CMS 7.0 Installation Guide Installation guide for administrators and developers Sitecore® is a registered trademark. All other brand and product names are the property of their respective holders. The contents of this document are the property of Sitecore. Copyright © 2001-2014 Sitecore. All rights reserved. Sitecore CMS 7.0 Installation Guide Table of Contents Chapter 1 Introduction ................................................................................................................................ 4 1.1 Getting Started .............................................................................................................................. 5 1.2 Preparing to Install Sitecore CMS 7.0 ........................................................................................... 6 Chapter 2 Sitecore CMS 7.0 Requirements ............................................................................................... 7 2.1 Sitecore Hosting Environment Requirements ............................................................................... 8 2.1.1 IIS Requirements....................................................................................................................... 8 2.1.2 Operating System Requirements .............................................................................................. 8 2.1.3 .NET Framework Requirements ................................................................................................ 9 2.1.4 Visual Studio Requirements -

Powershell – Cybersecurity Perspective
CERT-EU Security Whitepaper 2019-001 PowerShell – Cybersecurity Perspective Ciprian-Nicolae BOLDEA, Krzysztof SOCHA ver. 1.0 July 19, 2019 TLP: WHITE Contents 1 Summary 2 2 Background 2 3 Important Features for Cybersecurity2 3.1 Execution Policies.................................... 2 3.2 PowerShell Versions.................................. 3 3.3 PowerShell Language Modes.............................. 3 3.4 Signing......................................... 3 3.5 Securing Privileged Access............................... 3 3.6 PowerShell Logging................................... 4 3.7 Transcription...................................... 4 3.8 Ways of Running PowerShell.............................. 4 3.9 PowerShell for Remote Administration........................ 4 4 Prevention and Detection of PowerShell Attacks4 4.1 Execution Policies Bypass............................... 4 4.2 PowerShell Downgrade Attacks............................ 5 4.3 Migration to Windows 10............................... 5 4.4 Advanced Threat Protection.............................. 6 4.5 Advanced Threat Analytics............................... 6 4.6 Detection of attacks................................... 6 5 Conclusions 6 6 Annex A – Definitions7 7 Annex B – Log Sources and Events for the Detection of PowerShell Attacks7 7.1 Relevant Windows Events............................... 7 7.1.1 Windows PowerShell event log entries indicating the start and stop of PowerShell activity............................... 7 7.1.2 System event log entries indicating a configuration -

Outils De Développement Pour .NET Framework
Outils de développement pour .NET Framework 8QGHU&RQVWUXFWLRQ (Q&RQVWUXFWLRQ Didier Donsez 8QLYHUVLWp-RVHSK)RXULHU *UHQREOH ,0$,0$*/65$'(/( 'LGLHU'RQVH]#LPDJIU 'LGLHU'RQVH]#LHHHRUJ Didier Donsez, 2003, Outils de développement pour 1 .NET 2 Petit rappel sur .NET et C# I .NET • Développement Multi langage • C#, C++, Java Script, Eiffel, Component Pascal, APL, Cobol, Oberon, Perl, Python, Scheme, Smalltalk, Standard ML, Haskell, Mercury, Oberon et Java/J++ • CIL (Common Intermediate Language) • CTS (Common Type System) 7 • CLI (Common Language Infrastructure) ( 1 U X R • CLR (CLI Runtime implémenté par MicroSoft) S W Q H • JIT, pré-JIT (à l’installation, ou développement) P H S S R O I H C# : le langage « Post-Java » Y p G H G • « Syncrétisation » de Java et de C++ V O L W X 2 I Standardisation ECMA (European Computer Manufacturers Association) · http://www.ecma.ch ] H V Q • ECMA-334 CLI (Format COFF, CTS, Metadata, …) R ' U H L G • ECMA-335 C# L ' 3 1RQ0LFUR6RIW .NET I Motivations • .NET sur des OS non Windows (Unix, Linux, MacOS X, …) • Implémentations libres • Outils libres I Project 7 ( 1 U • ROTOR (MicroSoft) sauf Linux (Shared Sources) X R S W Q H • Mono project (Ximian) P H S S R O H Y • DotGNU (Free Software Foundation) p G H G V O L W X 2 ] H V Q R ' U H L G L ' 4 Implémentations I MicroSoft · Commerciales · .NET CLR · Compact .NET CLR • Code partagé • « Rotor » : Shared Source CLI 7 ( 1 U 3.6 Mloc ( 10,721 fichiers) X R S W Q H KWWSPVGQPLFURVRIWFRPQHWVVFOL P H S S R • GC moins performant, JIT différent -

Comparative Studies of Six Programming Languages
Comparative Studies of Six Programming Languages Zakaria Alomari Oualid El Halimi Kaushik Sivaprasad Chitrang Pandit Concordia University Concordia University Concordia University Concordia University Montreal, Canada Montreal, Canada Montreal, Canada Montreal, Canada [email protected] [email protected] [email protected] [email protected] Abstract Comparison of programming languages is a common topic of discussion among software engineers. Multiple programming languages are designed, specified, and implemented every year in order to keep up with the changing programming paradigms, hardware evolution, etc. In this paper we present a comparative study between six programming languages: C++, PHP, C#, Java, Python, VB ; These languages are compared under the characteristics of reusability, reliability, portability, availability of compilers and tools, readability, efficiency, familiarity and expressiveness. 1. Introduction: Programming languages are fascinating and interesting field of study. Computer scientists tend to create new programming language. Thousand different languages have been created in the last few years. Some languages enjoy wide popularity and others introduce new features. Each language has its advantages and drawbacks. The present work provides a comparison of various properties, paradigms, and features used by a couple of popular programming languages: C++, PHP, C#, Java, Python, VB. With these variety of languages and their widespread use, software designer and programmers should to be aware