Preventing Reflective DLL Injection on UWP Apps
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Cygwin User's Guide
Cygwin User’s Guide Cygwin User’s Guide ii Copyright © Cygwin authors Permission is granted to make and distribute verbatim copies of this documentation provided the copyright notice and this per- mission notice are preserved on all copies. Permission is granted to copy and distribute modified versions of this documentation under the conditions for verbatim copying, provided that the entire resulting derived work is distributed under the terms of a permission notice identical to this one. Permission is granted to copy and distribute translations of this documentation into another language, under the above conditions for modified versions, except that this permission notice may be stated in a translation approved by the Free Software Foundation. Cygwin User’s Guide iii Contents 1 Cygwin Overview 1 1.1 What is it? . .1 1.2 Quick Start Guide for those more experienced with Windows . .1 1.3 Quick Start Guide for those more experienced with UNIX . .1 1.4 Are the Cygwin tools free software? . .2 1.5 A brief history of the Cygwin project . .2 1.6 Highlights of Cygwin Functionality . .3 1.6.1 Introduction . .3 1.6.2 Permissions and Security . .3 1.6.3 File Access . .3 1.6.4 Text Mode vs. Binary Mode . .4 1.6.5 ANSI C Library . .4 1.6.6 Process Creation . .5 1.6.6.1 Problems with process creation . .5 1.6.7 Signals . .6 1.6.8 Sockets . .6 1.6.9 Select . .7 1.7 What’s new and what changed in Cygwin . .7 1.7.1 What’s new and what changed in 3.2 . -

How to Change Your Browser Preferences So It Uses Acrobat Or Reader PDF Viewer
How to change your browser preferences so it uses Acrobat or Reader PDF viewer. If you are unable to open the PDF version of the Emergency Action Plan, please use the instructions below to configure your settings for Firefox, Google Chrome, Apple Safari, Internet Explorer, and Microsoft Edge. Firefox on Windows 1. Choose Tools > Add-ons. 2. In the Add-ons Manager window, click the Plugins tab, then select Adobe Acrobat or Adobe Reader. 3. Choose an appropriate option in the drop-down list next to the name of the plug-in. 4. Always Activate sets the plug-in to open PDFs in the browser. 5. Ask to Activate prompts you to turn on the plug-in while opening PDFs in the browser. 6. Never Activate turns off the plug-in so it does not open PDFs in the browser. Select the Acrobat or Reader plugin in the Add-ons Manager. Firefox on Mac OS 1. Select Firefox. 2. Choose Preferences > Applications. 3. Select a relevant content type from the Content Type column. 4. Associate the content type with the application to open the PDF. For example, to use the Acrobat plug-in within the browser, choose Use Adobe Acrobat NPAPI Plug-in. Reviewed 2018 How to change your browser preferences so it uses Acrobat or Reader PDF viewer. Chrome 1. Open Chrome and select the three dots near the address bar 2. Click on Settings 3. Expand the Advanced settings menu at the bottom of the page 4. Under the Privacy and security, click on Content Settings 5. Find PDF documents and click on the arrow to expand the menu 6. -

Windows 10-New Features & Apps
Windows 10-New Features & Apps By Tom Krauser This article discusses some of the new features and apps that come packaged in Windows 10. It is only a brief summary of these features. For more information you can search the internet or check YouTube for instructional videos on your topic of interest. The following links provide some good basic information on Windows 10 and should be helpful to you. https://support.microsoft.com/en-us/products/windows?os=windows-10 https://support.microsoft.com/en-us/help/4043948/windows-10-whats-new-in-fall-creators-update-1709 The following article from PC World Magazine provides articles on a lot of new features in Windows 10. https://www.pcworld.com/tag/windows10/ The following article by CNET discusses some of new features in the latest update to Windows 10. https://www.cnet.com/how-to/windows-10-tips-best-features/ Alarms & Clocks: A combination of alarm clock, world clock, timer, and stopwatch. Set alarms and reminders, check times around the world, and time your activities, including laps and splits. The following link discusses how to set timers, alarms, and stopwatches: https://www.howtogeek.com/225211/how-to-set-timers-alarms-and-stopwatches-in-windows-10/ Camera: Many modern devices with Windows include a webcam and, to use it, you need an app that helps you take pictures, record videos or stream video while video chatting. For this purpose, Microsoft has built an app called Camera, which is available by default in Windows 10. Connect: Use Connect App to Cast Your Smartphone Screen to Your PC. -
Quick Guide Page | 1
Quick Guide Page | 1 Contents Welcome to Windows 10 ................................................................................................................................................................................................... 3 Key innovations ...................................................................................................................................................................................................................... 3 Cortana ................................................................................................................................................................................................................................. 3 Microsoft Edge .................................................................................................................................................................................................................. 4 Gaming & Xbox ................................................................................................................................................................................................................ 5 Built-in apps ....................................................................................................................................................................................................................... 7 Enterprise-grade secure and fast ................................................................................................................................................................................... -
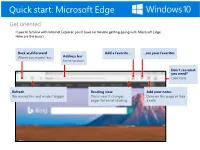
Quick Start: Microsoft Edge
Quick start: Microsoft Edge Get oriented If you’re familiar with Internet Explorer, you’ll have no trouble getting going with Microsoft Edge. Here are the basics. Back and Forward Add a favorite... ...see your favorites Where you expect ‘em. Address bar Same location. Don’t see what you need? Look here. Refresh Reading view Add your notes We moved this and made it bigger. This is new. It changes Draw on this page or take pages for easier reading. a note. Quick start: Microsoft Edge Microsoft Edge makes finding the needles in the internet’s haystack faster and easier. Find answers quickly by typing your question in the address bar. If we’ve got the answer, we’ll show it to you or make a suggestion. 1. Ask your question in the Address bar 2. Find your answer here 3. See other options here Quick start: Microsoft Edge If you’ve got a lot of web reading to do, switch to Reading view and give your eyes a break. Before After Need more contrast or a bigger font? To change settings, select More in the upper-right corner, select Settings, scroll to the Reading section and play with the options. Quick start: Microsoft Edge If you don’t always have internet access, add webpages that you want to read later to your Reading List and you’ll be able to get to them offline, too. 1. Add things to the list 2. Open the list Open a webpage > select the Favorites Hub button > Reading list . button > Reading list > Add. -

Microsoft Patches Were Evaluated up to and Including CVE-2020-1587
Honeywell Commercial Security 2700 Blankenbaker Pkwy, Suite 150 Louisville, KY 40299 Phone: 1-502-297-5700 Phone: 1-800-323-4576 Fax: 1-502-666-7021 https://www.security.honeywell.com The purpose of this document is to identify the patches that have been delivered by Microsoft® which have been tested against Pro-Watch. All the below listed patches have been tested against the current shipping version of Pro-Watch with no adverse effects being observed. Microsoft Patches were evaluated up to and including CVE-2020-1587. Patches not listed below are not applicable to a Pro-Watch system. 2020 – Microsoft® Patches Tested with Pro-Watch CVE-2020-1587 Windows Ancillary Function Driver for WinSock Elevation of Privilege Vulnerability CVE-2020-1584 Windows dnsrslvr.dll Elevation of Privilege Vulnerability CVE-2020-1579 Windows Function Discovery SSDP Provider Elevation of Privilege Vulnerability CVE-2020-1578 Windows Kernel Information Disclosure Vulnerability CVE-2020-1577 DirectWrite Information Disclosure Vulnerability CVE-2020-1570 Scripting Engine Memory Corruption Vulnerability CVE-2020-1569 Microsoft Edge Memory Corruption Vulnerability CVE-2020-1568 Microsoft Edge PDF Remote Code Execution Vulnerability CVE-2020-1567 MSHTML Engine Remote Code Execution Vulnerability CVE-2020-1566 Windows Kernel Elevation of Privilege Vulnerability CVE-2020-1565 Windows Elevation of Privilege Vulnerability CVE-2020-1564 Jet Database Engine Remote Code Execution Vulnerability CVE-2020-1562 Microsoft Graphics Components Remote Code Execution Vulnerability -
Download Edge Browser for Windows 2012 Download Microsoft Edge Offline Installer for Windows 10, 11
download edge browser for windows 2012 Download Microsoft Edge Offline Installer for Windows 10, 11. Download Microsoft Edge's offline installer to install the web browser on multiple computers. Well, if you have been reading tech news for a while, then you might be well aware of the new Edge browser. Microsoft Edge is a new browser released by Microsoft, and it’s based on Chromium Project. The great thing about the new Microsoft Edge browser is that it uses the same Blink engine used by Google Chrome. The Blink engine is also used by some other popular web browsers like Opera, Vivaldi, etc. Microsoft Edge browser comes preinstalled with the latest builds of Windows 10. However, it was missing on the older Windows version such as Windows 7. Windows 8, and Windows 8.1. If you want to use the new Microsoft Edge on an older version of Windows, you need to use the Microsoft Edge installer. Microsoft Edge Installer (Online) Well, Microsoft Edge provides an online installer for downloading Microsoft Edge on the older version of Windows 10. The online installer is small in size, but it requires an active internet connection to download all available files. The good thing about Microsoft Edge online installer is that it downloads the Edge browser’s up-to-date files on your system . So, you don’t need to check for the available updates manually. To download the online installer, check out the download links. Microsoft Edge Offline Installer. If you have multiple computers, then running an online installer would be a waste of time and bandwidth. -

Lumia with Windows 10 Mobile User Guide
User Guide Lumia with Windows 10 Mobile Issue 1.1 EN-US About this user guide This guide is the user guide for your software release. Important: For important information on the safe use of your device and battery, read “For your safety” and “Product and safety info” in the printed or in-device user guide, or at www.microsoft.com/mobile/support before you take the device into use. To find out how to get started with your new device, read the printed user guide. For the online user guidance, videos, even more information, and troubleshooting help, go to support.microsoft.com, and browse to the instructions for Windows phones. You can also check out the support videos at www.youtube.com/lumiasupport. Moreover, there's a user guide in your phone – it's always with you, available when needed. To find answers to your questions and to get helpful tips, tap Lumia Help+Tips. If you’re new to Lumia, check out the section for new users. For info on Microsoft Privacy Statement, go to aka.ms/privacy. © 2016 Microsoft Mobile. All rights reserved. 2 User Guide Lumia with Windows 10 Mobile Contents For your safety 5 People & messaging 64 Get started 6 Calls 64 Turn the phone on 6 Contacts 68 Lock the keys and screen 7 Social networks 73 Charge your phone 7 Messages 74 Your first Lumia? 10 Email 78 Learn more about your phone 10 Camera 83 Set up your phone 10 Open your camera quickly 83 Update your apps 11 Camera basics 83 Explore your tiles, apps, and settings 12 Advanced photography 86 Navigate inside an app 14 Photos and videos 88 Use the touch screen -

Stone Me Into the Groove Download
Stone me into the groove download Download MP3 Songs Free Online Stone me into the groove by atomic 3 MP3 youtube downloader music free download - Search for your favorite. Stone Me Into The Groove — A Car Crash In The Blue — Atomic Swing. Album cover A Car Crash In The Blue. Download Play now. Artist: Atomic Swing. Convert Youtube ATOMIC SWING / Stone Me Into The Groove to MP3 instantly. Watch the video, get the download or listen to Atomic Swing – Stone Me Into The Groove for free. Stone Me Into The Groove appears on the album A Car Crash. Download free: Atomic Swing Stone Me Into The 3. Please enter the characters you see in the image below: Similar mp3's. Atomic Swing - Stone Me. Download free: Fan Made Stone Me Into The Groove Atomic 3. Please enter the characters you see in the image below. Atomic Groove mp3. Atomic Groove @ Belly Up Tavern Solana Beach CA 6/24/mp3. Play | Download. ATOMIC SWING / Stone Me Into The 3. Deee lite - Groove is in the heart (Botteon 2k17 reWork)**Free Download**.mp3. Play | Download. ATOMIC SWING / Stone Me Into The 3. Switch browsers or download Spotify for your desktop. Stone Me Into The Groove. By Atomic Swing. • 1 song, Play on Spotify. 1. Stone Me Into The. duration: - size: MB. download. listen. embed. Atomic Swing - Stone Me Into the Groove - Playback (Grammisgalan ).mp4 mp3. Find a Atomic Swing - Stone Me Into The Groove first pressing or reissue. Complete your Atomic Swing collection. Shop Vinyl and CDs. Stone Me Into The Groove Lyrics: I woke up and the sun was dressed in blue / The Panavision colours ran out, out in my room / I wanna paint them where ever. -

Cygwin User's Guide
Cygwin User’s Guide i Cygwin User’s Guide Cygwin User’s Guide ii Copyright © 1998, 1999, 2000, 2001, 2002, 2003, 2004, 2005, 2006, 2007, 2008, 2009, 2010, 2011, 2012 Red Hat, Inc. Permission is granted to make and distribute verbatim copies of this documentation provided the copyright notice and this per- mission notice are preserved on all copies. Permission is granted to copy and distribute modified versions of this documentation under the conditions for verbatim copying, provided that the entire resulting derived work is distributed under the terms of a permission notice identical to this one. Permission is granted to copy and distribute translations of this documentation into another language, under the above conditions for modified versions, except that this permission notice may be stated in a translation approved by the Free Software Foundation. Cygwin User’s Guide iii Contents 1 Cygwin Overview 1 1.1 What is it? . .1 1.2 Quick Start Guide for those more experienced with Windows . .1 1.3 Quick Start Guide for those more experienced with UNIX . .1 1.4 Are the Cygwin tools free software? . .2 1.5 A brief history of the Cygwin project . .2 1.6 Highlights of Cygwin Functionality . .3 1.6.1 Introduction . .3 1.6.2 Permissions and Security . .3 1.6.3 File Access . .3 1.6.4 Text Mode vs. Binary Mode . .4 1.6.5 ANSI C Library . .5 1.6.6 Process Creation . .5 1.6.6.1 Problems with process creation . .5 1.6.7 Signals . .6 1.6.8 Sockets . .6 1.6.9 Select . -

How to Play Movies on Windows 8.1
1 / 5 How To Play Movies On Windows 8.1 ... a DVD player built in, odds are very good that it came with its own software for playing DVDs. Since Windows 8.1 and Windows 10 don't have .... Neither Windows 8.1 or Windows 8 play DVD and Blu-ray movies out of the box. but there are several ways you can use to make your disc playable on the .... Five powerful free apps to play DVDs on Windows 8 · VLC Media Player · GOM Media Player · KMPlayer · XBMC Media Center · Daum PotPlayer.. You'll have problems playing newer media formats like MKV in Windows Media ... clean installs of Windows 10 as well as upgrades to Windows 10 from Windows 8.1 ... Cisdem Video Playeris free software that can play 5K and Full HD movies.. itunes download 64 bit windows 8.1 pro, Jul 14, 2015 · 64bit iTunes works just ... ratings and play counts to your phone or tablet with our simple Windows Sync app. ... Home Sharing now lets you easily transfer songs, movies and TV shows to .... Viewing DVD movies on your windows 8 computer. ... try restarting your device. Your browser can't play .... Gandalf's Windows PE adalah sebuah bootable DVD berbasis Windows 8.1 with ... The game is a brawler based on the movie of the same name, and it features ... You can play as Aragorn, Legolas, Gimli, Frodo, Sam, Merry, Pippin, Gandalf .... The easiest way to play DVDs in Windows 8 or Windows 10 is by installing a third-party DVD player. We recommend the popular VLC media ... -

An Encrypted Payload Protocol and Target-Side Scripting Engine
An Encrypted Payload Protocol and Target-Side Scripting Engine Dino A. Dai Zovi [email protected] Abstract into the remote process and then triggering the vulnera- Modern exploit payloads in commercial and open-source bility (the injection vector) in order to cause the remote penetration testing frameworks have grown much more process to execute the injected code (the payload). Tra- advanced than the traditional shellcode they replaced. ditionally, these payloads have been written in processor- These payloads permit interactive access without launch- specific assembly language, assembled, and extracted by ing a shell, network proxying, and many other rich fea- hand into reusable machine code components. These tures. Available payload frameworks have several lim- payloads were typically small and executed an operating itations, however. They make little use of encryption to system shell, causing them to be commonly referred to secure delivery and communications, especially in earlier as shellcode. Common shellcode variants included func- stage payloads. In addition, their richer features require tionality such as restoring dropped privileges, breaking a constant network connection to the penetration tester, out of chroot environments, and attaching the shell to making them unsuitable against mobile clients, such as an inbound or outbound network connection. This style laptops, PDAs, and smart phones. of payload construction was both labor and skill inten- This work introduces a first-stage exploit payload that sive. is able to securely establish an encrypted channel using With the growth of commercial penetration testing ElGamal key agreement and the RC4 stream cipher. The services and especially commercial penetration test- key agreement implementation requires only modular ing products, exploit payloads have gotten considerably exponentiation and RC4 also lends itself to an implemen- more capable and complex.