Knowledge Management in Medium-Sized Software Consulting Companies
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Ispconfig Documentation Ispconfig Documentation I
ISPConfig Documentation ISPConfig Documentation I Table of Contents General...............................................................................................................................................1 1 What is ISPConfig?...............................................................................................................1 2 Terms and structure of the manual.......................................................................................1 3 Installation/Upgrade/Deinstallation.......................................................................................1 3.1 Installation....................................................................................................................1 3.2 Upgrade.......................................................................................................................1 3.3 Deinstallation................................................................................................................2 4 Login and Logout..................................................................................................................2 I Administrator Manual......................................................................................................................3 1 General.................................................................................................................................3 1.1 Login and Password.....................................................................................................3 1.2 ISPConfig Interface -

Installation Guide
install_guide.book Page i Monday, May 11, 2015 8:48 PM Installation Guide Installation Guide Schrödinger Software Release 2015-2 Schrödinger Press install_guide.book Page ii Monday, May 11, 2015 8:48 PM Installation Guide Copyright © 2015 Schrödinger, LLC. All rights reserved. While care has been taken in the preparation of this publication, Schrödinger assumes no responsibility for errors or omissions, or for damages resulting from the use of the information contained herein. Canvas, CombiGlide, ConfGen, Epik, Glide, Impact, Jaguar, Liaison, LigPrep, Maestro, Phase, Prime, PrimeX, QikProp, QikFit, QikSim, QSite, SiteMap, Strike, and WaterMap are trademarks of Schrödinger, LLC. Schrödinger, BioLuminate, and MacroModel are registered trademarks of Schrödinger, LLC. MCPRO is a trademark of William L. Jorgensen. DESMOND is a trademark of D. E. Shaw Research, LLC. Desmond is used with the permission of D. E. Shaw Research. All rights reserved. This publication may contain the trademarks of other companies. Schrödinger software includes software and libraries provided by third parties. For details of the copyrights, and terms and conditions associated with such included third party software, use your browser to open third_party_legal.html, which is in the docs folder of your Schrödinger software installation. This publication may refer to other third party software not included in or with Schrödinger software ("such other third party software"), and provide links to third party Web sites ("linked sites"). References to such other third party software or linked sites do not constitute an endorsement by Schrödinger, LLC or its affiliates. Use of such other third party software and linked sites may be subject to third party license agreements and fees. -
![Ispconfig 3 Manual]](https://docslib.b-cdn.net/cover/9381/ispconfig-3-manual-89381.webp)
Ispconfig 3 Manual]
[ISPConfig 3 Manual] ISPConfig 3 Manual Version 1.0 for ISPConfig 3.0.3 Author: Falko Timme <[email protected]> Last edited 09/30/2010 1 The ISPConfig 3 manual is protected by copyright. No part of the manual may be reproduced, adapted, translated, or made available to a third party in any form by any process (electronic or otherwise) without the written specific consent of projektfarm GmbH. You may keep backup copies of the manual in digital or printed form for your personal use. All rights reserved. This copy was issued to: Thomas CARTER - [email protected] - Date: 2010-11-20 [ISPConfig 3 Manual] ISPConfig 3 is an open source hosting control panel for Linux and is capable of managing multiple servers from one control panel. ISPConfig 3 is licensed under BSD license. Managed Services and Features • Manage one or more servers from one control panel (multiserver management) • Different permission levels (administrators, resellers and clients) + email user level provided by a roundcube plugin for ISPConfig • Httpd (virtual hosts, domain- and IP-based) • FTP, SFTP, SCP • WebDAV • DNS (A, AAAA, ALIAS, CNAME, HINFO, MX, NS, PTR, RP, SRV, TXT records) • POP3, IMAP • Email autoresponder • Server-based mail filtering • Advanced email spamfilter and antivirus filter • MySQL client-databases • Webalizer and/or AWStats statistics • Harddisk quota • Mail quota • Traffic limits and statistics • IP addresses 2 The ISPConfig 3 manual is protected by copyright. No part of the manual may be reproduced, adapted, translated, or made available to a third party in any form by any process (electronic or otherwise) without the written specific consent of projektfarm GmbH. -

Internet Domain Name System
IINNTTEERRNNEETT DDOOMMAAIINN NNAAMMEE SSYYSSTTEEMM http://www.tutorialspoint.com/internet_technologies/internet_domain_name_system.htm Copyright © tutorialspoint.com Overview When DNS was not into existence, one had to download a Host file containing host names and their corresponding IP address. But with increase in number of hosts of internet, the size of host file also increased. This resulted in increased traffic on downloading this file. To solve this problem the DNS system was introduced. Domain Name System helps to resolve the host name to an address. It uses a hierarchical naming scheme and distributed database of IP addresses and associated names IP Address IP address is a unique logical address assigned to a machine over the network. An IP address exhibits the following properties: IP address is the unique address assigned to each host present on Internet. IP address is 32 bits 4bytes long. IP address consists of two components: network component and host component. Each of the 4 bytes is represented by a number from 0 to 255, separated with dots. For example 137.170.4.124 IP address is 32-bit number while on the other hand domain names are easy to remember names. For example, when we enter an email address we always enter a symbolic string such as [email protected]. Uniform Resource Locator URL Uniform Resource Locator URL refers to a web address which uniquely identifies a document over the internet. This document can be a web page, image, audio, video or anything else present on the web. For example, www.tutorialspoint.com/internet_technology/index.html is an URL to the index.html which is stored on tutorialspoint web server under internet_technology directory. -

Implementation of Embedded Web Server Based on ARM11 and Linux Using Raspberry PI
International Journal of Recent Technology and Engineering (IJRTE) ISSN: 2277-3878, Volume-3 Issue-3, July 2014 Implementation of Embedded Web Server Based on ARM11 and Linux using Raspberry PI Girish Birajdar Abstract— As ARM processor based web servers not uses III. HARDWARE USED computer directly, it helps a lot in reduction of cost. In this We will use different hardware to implement this embedded project our aim is to implement an Embedded Web Server (EWS) based on ARM11 processor and Linux operating system using web server, which are described in this section. Raspberry Pi. it will provide a powerful networking solution with 1. Raspberry Pi : The Raspberry Pi is low cost ARM wide range of application areas over internet. We will run web based palm-size computer. The Raspberry Pi has server on an embedded system having limited resources to serve microprocessor ARM1176JZF-S which is a member of embedded web page to a web browser. ARM11 family and has ARMv6 architecture. It is build Index Terms— Embedded Web Server, Raspberry Pi, ARM, around a BCM2835 broadcom processor. ARM processor Ethernet etc. operates at 700 MHz & it has 512 MB RAM. It consumes 5V electricity at 1A current due to which power I. INTRODUCTION consumption of raspberry pi is less. It has many peripherals such as USB port, 10/100 ethernet, GPIO, HDMI & With evolution of World-Wide Web (WWW), its composite video outputs and SD card slot.SD card slot is application areas are increasing day by day. Web access used to connect the SD card which consist of raspberry linux functionality can be embedded in a low cost device which operating system. -

Domain Name System System Work?
What is the DNS? - how it works Isaac Maposa | Dev Anand Teelucksingh | Beran Gillen Community Onboarding Program | 11 March 2017 Agenda 1 2 3 What is the Domain Structure of the How does the Name System? Domain Name Domain Name System System Work? 4 5 6 Who makes the Stakeholders in the Engage with ICANN Domain Name Domain Name ??? System Work? System. | 2 What is the Domain Name System (DNS)? The Internet, what is it..? ● The Internet is a network of networks that interconnects devices to exchange information. ● In order to “talk” to each other, all of these devices must have a unique numerical address called an Internet Protocol address or IP Address. An example of an IP address is 94.127.53.132 ● When you visit a website from your browser, you are requesting the website from your device’s IP address to the web server’s IP address. ● However, you don’t type in the ip address of the web server, rather the domain name of for example www.google.com ● In so doing, you have queried the DNS. ● So what is this DNS???? | 4 What is the Domain Name System? ● The Domain Name System or DNS overcomes this problem of remembering IP addresses by mapping domain names to IP addresses. ● While this sounds like a phone book, it is not a centralised database. ● The DNS is a distributed database across a hierarchy of networks of servers and provide ways for devices and software (like browsers and email) to query the DNS to get an IP address. ● Domain names must be unique. -

Evaluating Web Development Frameworks for Delphi
Evaluating Web Development Frameworks for Delphi Updates, links, and more embt.co/WebDev2019 #DelphiWebDev Disclaimer ❏ This content is mostly focused on 3rd party frameworks and libraries ❏ While a lot of time was spent researching, some of the information may be outdated or otherwise incorrect through an error during research ❏ Links are provided to the sources, and you are encouraged to double check all information and seek clarification ❏ Any exclusion is just an oversight or a result of limited time and space and was not an intentional indication of quality or suitability ❏ This information presented here is not intended to indicate superiority or inferiority of one library over another for any use cases ❏ Please consider this a good faith effort to represent these libraries and frameworks impartially and accurately ❏ I will reach out to the projects, companies, and developers to seek corrections and additional information. ❏ Erratas and updates will be published at embt.co/WebDev2019 Thanks! Delphi and FireMonkey: Winning Combination for Cross- Platform Development → Single Codebase → Easy-to-tailor platform specific UIs → One programming language to learn and support What about Web Apps? Delphi’s incredible productivity for building amazing apps also extends to the web! https://blog.hootsuite.com/simon-kemp-social-media/ https://blog.hootsuite.com/simon-kemp-social-media/ People spend a daily average of 6 hours & 42 minutes using the internet https://blog.hootsuite.com/simon-kemp-social-media/ ❏Different kinds of web development -

MPKI for SSL Guide
Managing SSL Security in Multi-Server Environments VeriSign’s Easy-to-Use Web-Based Service Speeds SSL Certificate Management and Cuts Total Cost of Security ▬▬▬▬▬▬▬▬▬▬▬▬▬▬▬▬▬▬▬▬▬▬▬▬▬▬▬▬▬▬▬▬▬▬▬▬▬▬▬▬▬▬▬ A SMART STRATEGY FOR MANAGING SSL VeriSign MPKI for SSL SECURITY ON MULTIPLE SERVERS Simple: Web-based Protecting the confidentiality and integrity of sensitive service for managing information transmitted over your organization’s network is a all your SSL crucial step to building customer confidence, securely certificates—no interacting with business partners and complying with new upfront hardware or privacy regulations. Your company’s requirements may include software to install securing information exchange between Web servers and Efficient: Enroll, clients, server-to-server, and among other networking devices approve, issue, reject, such as server load balancers or SSL accelerators. For a revoke, renew with a complete solution, cross-network security must protect servers few clicks of a mouse facing both the Internet and private intranets. Time saving: Issue 1 SSL certificates on Secure Sockets Layer (SSL ) is the world’s standard technology demand used to protect information transmitted over the Web with the ubiquitous HTTP protocol. SSL protects against site spoofing, Secure: Certificate- data interception and tampering. Support for SSL is built into secured administrator all major operating systems, Web applications and server account access hardware. Leveraging both the powerful encryption of SSL and Value: Provides the confidence instilled by VeriSign’s authentication procedures, discounted, bulk your company can immediately protect sensitive data purchases of SSL transmitted between your servers and your customers, certificates employees and business partners. Managed PKI for SSL is VeriSign’s easy to use and flexible Web-based service for deploying and managing multiple SSL certificates across the organization. -

WHY USE a WIKI? an Introduction to the Latest Online Publishing Format
WHY USE A WIKI? An Introduction to the Latest Online Publishing Format A WebWorks.com White Paper Author: Alan J. Porter VP-Operations WebWorks.com a brand of Quadralay Corporation [email protected] WW_WP0309_WIKIpub © 2009 – Quadralay Corporation. All rights reserved. NOTE: Please feel free to redistribute this white paper to anyone you feel may benefit. If you would like an electronic copy for distribution, just send an e-mail to [email protected] CONTENTS Overview................................................................................................................................ 2 What is a Wiki? ...................................................................................................................... 2 Open Editing = Collaborative Authoring .................................................................................. 3 Wikis in More Detail................................................................................................................ 3 Wikis Are Everywhere ............................................................................................................ 4 Why Use a Wiki...................................................................................................................... 5 Getting People to Use Wikis ................................................................................................... 8 Populating the Wiki................................................................................................................. 9 WebWorks ePublisher and Wikis -

A Distributed, Wikipedia Based Web Application Benchmark
WikiBench: A distributed, Wikipedia based web application benchmark Master thesis by Erik-Jan van Baaren Student number 1278967 [email protected] Under the supervision of: Guillaume Pierre Guido Urdaneta Vrije Univesiteit Amsterdam Department of Computer Science May 13, 2009 Abstract Many different, novel approaches have been taken to improve throughput and scalability of distributed web application hosting systems and relational databases. Yet there are only a limited number of web application bench- marks available. We present the design and implementation of WikiBench, a distributed web application benchmarking tool based on Wikipedia. Wik- iBench is a trace based benchmark, able to create realistic workloads with thousands of requests per second to any system hosting the freely available Wikipedia data and software. We obtained completely anonymized, sam- pled access traces from the Wikimedia Foundation, and we created software to process these traces in order to reduce the intensity of its traffic while still maintaining the most important properties such as inter-arrival times and distribution of page popularity. This makes WikiBench usable for both small and large scale benchmarks. Initial benchmarks show a regular day of traffic with its ups and downs. By using median response times, we are able to show the effects of increasing traffic intensities on our system under test. Contents 1 Introduction 2 2 Related Work 4 2.1 TPC-W . 4 2.2 Web Polygraph . 6 3 System Model 8 3.1 Requirements . 9 3.2 WikiBench design . 11 3.3 TraceBench Design . 15 3.4 WikiBench Workflow . 16 4 Workload Creation 19 4.1 Changing the Request Rate . -

Web Application Hosting in the AWS Cloud AWS Whitepaper Web Application Hosting in the AWS Cloud AWS Whitepaper
Web Application Hosting in the AWS Cloud AWS Whitepaper Web Application Hosting in the AWS Cloud AWS Whitepaper Web Application Hosting in the AWS Cloud: AWS Whitepaper Copyright © Amazon Web Services, Inc. and/or its affiliates. All rights reserved. Amazon's trademarks and trade dress may not be used in connection with any product or service that is not Amazon's, in any manner that is likely to cause confusion among customers, or in any manner that disparages or discredits Amazon. All other trademarks not owned by Amazon are the property of their respective owners, who may or may not be affiliated with, connected to, or sponsored by Amazon. Web Application Hosting in the AWS Cloud AWS Whitepaper Table of Contents Abstract ............................................................................................................................................ 1 Abstract .................................................................................................................................... 1 An overview of traditional web hosting ................................................................................................ 2 Web application hosting in the cloud using AWS .................................................................................... 3 How AWS can solve common web application hosting issues ........................................................... 3 A cost-effective alternative to oversized fleets needed to handle peaks ..................................... 3 A scalable solution to handling unexpected traffic -
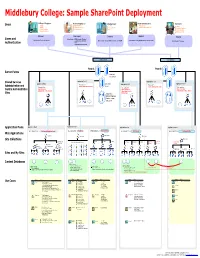
Visio-MIDD Sharepoint Architecture Design Sample.Vsd
College Colleagues Remote Employees Internal Users Farm Administrators Customers Trustees Work from Home Web Services Faculty Parents Alumni Affiliated Institutions Systems & Network Services Current Students Prospective Students External Professors Schools Abroad Staff Local Community Prospective Students Global Community Extranet Remotenet Intranet Adminet Internet Authentication = NTLM (Integrated Windows) Authentication = forms authentication using ISA Server 2006 SSO Authentication = Integrated Windows (Kerberos or NTLM) Authentication = Integrated Windows (Kerberos or NTLM) Authentication = Anonymous —or— Forms with an LDAP provider Application Pool 1 Application Pool 7 Application Pool 2 Application Pool 3 Application Pool 8 Web application: Web application: Central Administration Site Central Administration Site Web application: Web application: Web application: Shared Services Shared Services Shared Services Administration Site—Default Administration Site— Administration Site—Default PartnerWeb Application Pool 4 Application Pool 5 Application Pool 6 Application Pool 9 Web application: Intranet Applications Web application: My Sites Web application: Team Sites Web application: Intraweb Web application: Internet Site http://team <varies> http://my http://web http://www Team1 Team2 Team3 Delivered http://my/personal/<user> Handbook HR Policies Library Authoring Site Staging Site Production Site Content Collection Collection Collection HR Project from Events Management Banner, Registration Segue, etc Admissions Academics Athletics Database settings: Target size per database = TBD Database settings: Database settings: Database settings: Site size limits per site = TBD Target size per database = TBD Content Deployment Site level warning = 0 Site level warning = 0 Content Deployment Maximum number of sites = flexible Storage quota per site = TBD Maximum number of sites = 1 (one site collection per database). Maximum number of sites = 1 (one site collection per database).