CIS Microsoft Windows Server 2012 R2 Benchmark
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Windows Live Movie Maker: Create, Edit, and View Movies
Windows Live Movie Maker: Create, Edit, and View Movies By Andy Rathbone from Windows 7 For Dummies To create, edit, and view digital movies in Windows 7, you must download Windows Live Movie Maker. Windows Live Movie Maker — a stripped-down version of the movie-editing program that came with XP and Vista — works best for creating short videos. Download Movie Maker from Microsoft's Live Essentials Web page. You also need Windows Live Photo Gallery to import the movies from your camcorder. To make a movie, you follow three basic steps: 1. Import. For some reason, Windows Live Movie Maker can't import your video from your video camera. You must import it through Windows Live Photo Gallery, instead. 2. Edit. This step combines your video clips, music, and pictures into a structured movie. Edit each clip down to its best moments and add transitions between the clips — the way one clip fades into the next. Toss in a soundtrack, as well. 3. Publish. When you finish editing, Movie Maker combines your batch of clips or photos into a complete movie, ready to be played back on your computer or saved to a DVD. Creating movies requires a lot of free hard drive space. A 15-minute movie can consume 2.5GB. If Movie Maker complains about space, you have two choices: Create smaller videos or upgrade your computer with a second hard drive. Step 1: Import video, pictures, and music If you've already imported footage from a digital camcorder, jump ahead to Step 4 in the steps in this section and begin there. -

Internet Explorer 9 Features
m National Institute of Information Technologies NIIT White Paper On “What is New in Internet Explorer 9” Submitted by: Md. Yusuf Hasan Student ID: S093022200027 Year: 1st Quarter: 2nd Program: M.M.S Date - 08 June 2010 Dhaka - Bangladesh Internet Explorer History Abstract: In the early 90s—the dawn of history as far as the World Wide Web is concerned—relatively few users were communicating across this Internet Explorer 9 (abbreviated as IE9) is the upcoming global network. They used an assortment of shareware and other version of the Internet Explorer web browser from software for Microsoft Windows operating system. In 1995, Microsoft Microsoft. It is currently in development, but developer hosted an Internet Strategy Day and announced its commitment to adding Internet capabilities to all its products. In fulfillment of that previews have been released. announcement, Microsoft Internet Explorer arrived as both a graphical Web browser and the name for a set of technologies. IE9 will have complete or nearly complete support for all 1995: Internet Explorer 1.0: In July 1995, Microsoft released the CSS 3 selectors, border-radius CSS 3 property, faster Windows 95 operating system, which included built-in support for JavaScript and embedded ICC v2 or v4 color profiles dial-up networking and TCP/IP (Transmission Control support via Windows Color System. IE9 will feature Protocol/Internet Protocol), key technologies for connecting to the hardware accelerated graphics rendering using Direct2D, Internet. In response to the growing public interest in the Internet, Microsoft created an add-on to the operating system called Internet hardware accelerated text rendering using Direct Write, Explorer 1.0. -

Security Policy Page 1 of 20
Security Policy Page 1 of 20 Security Policy This security policy contains data to configure services and network security based on the server’s role, as well as data to configure registry and auditing settings. Server: VENGWIN207 Services Service Name Startup Mode Description Issues, manages, and removes X.509 certificates for such applications such as Active Directory Certificate S/MIME and SSL. If the service is stopped, Disabled Services certificates will not be issued. If this service is disabled, any services that explicitly depend on it will fail to start. AD DS Domain Controller service. If this service is stopped, users will be unable to log Active Directory Domain Services Disabled on to the network. If this service is disabled, any services that explicitly depend on it will fail to start. AD FS Web Agent Authentication The AD FS Web Agent Authentication Service Disabled Service validates incoming tokens and cookies. Adobe Acrobat Updater keeps your Adobe Adobe Acrobat Update Service Automatic software up to date. Sends logging messages to the logging database when logging is enabled for the Active Directory Rights Management Services role. If this service is disabled or stopped AdRmsLoggingService Disabled when logging is enabled, logging messages will be stored in local message queues and sent to the logging database when the service is started. Processes application compatibility cache Application Experience Disabled requests for applications as they are launched Provides administrative services for IIS, for example configuration history and Application Pool account mapping. If this Application Host Helper Service Disabled service is stopped, configuration history and locking down files or directories with Application Pool specific Access Control Entries will not work. -

Tweakhound, Windows 7 Beta Default Services
Sheet1 Name Startup Type Adaptive Brightness Manual AppID Service Manual Application Experience Manual Application Information Manual Application Layer Gateway Service Manual Application Management Manual Background Intelligent Transfer Service Automatic (Delayed Start) Base Filtering Engine Automatic BitLocker Drive Encryption Service Manual Block Level Backup Engine Service Manual Bluetooth Support Service Manual BranchCache Manual Certificate Propagation Manual CNG Key Isolation Manual COM+ Event System Automatic COM+ System Application Manual Computer Browser Automatic Credential Manager Service Manual Cryptographic Services Automatic DCOM Server Process Launcher Automatic Desktop Window Manager Session Manager Automatic DHCP Client Automatic Diagnostic Policy Service Automatic Diagnostic Service Host Manual Diagnostic System Host Manual Disk Defragmenter Manual Distributed Link Tracking Client Automatic Distributed Transaction Coordinator Manual DNS Client Automatic Encrypting File System (EFS) Manual Extensible Authentication Protocol Manual Fax Manual Function Discovery Provider Host Manual Function Discovery Resource Publication Automatic Group Policy Client Automatic Health Key and Certificate Management Manual HomeGroup Listener Manual HomeGroup Provider Manual Human Interface Device Access Manual IKE and AuthIP IPsec Keying Modules Automatic Interactive Services Detection Manual Internet Connection Sharing (ICS) Disabled IP Helper Automatic IPsec Policy Agent Manual KtmRm for Distributed Transaction Coordinator Manual Link-Layer -

The Spyrats of Oceanlotus Malware Analysis White Paper Contents
The SpyRATs of OceanLotus Malware Analysis White Paper Contents Introduction ............................................................................................4 C2 .............................................................................................................. 32 Protocol ............................................................................................ 32 Components ............................................................................................4 Commands ...................................................................................... 33 Backdoor Error Codes ................................................................. 34 Roland RAT ..............................................................................................4 CobaltStrike Beacon #1 ................................................................... 35 Overview ...................................................................................................4 Overview ................................................................................................ 35 Features ....................................................................................................4 Deployment .......................................................................................... 36 Behavior ....................................................................................................5 C2 .................................................................................................................7 CobaltStrike -
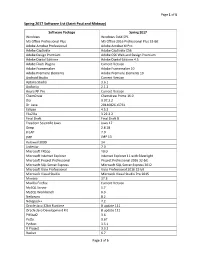
Spring 2017 Software List (Saint Paul and Midway)
Page 1 of 5 Spring 2017 Software List (Saint Paul and Midway) Software Package Spring 2017 Windows Windows 7x64 SP1 MS Office Professional Plus MS Office 2016 Professional Plus 32-Bit Adobe Acrobat Professional Adobe Acrobat XI Pro Adobe Captivate Adobe Captivate CS6 Adobe Design Premium Adobe CS6 Web and Design Premium Adobe Digital Editions Adobe Digital Editions 4.5 Adobe Flash Plugins Current Version Adobe Framemaker Adobe Framemaker 10 Adobe Premiere Elements Adobe Premiere Elements 10 Android Studio Current Version Aptana Studio 3.6.1 Audacity 2.1.2 Axure RP Pro Current Version ChemDraw Chemdraw Prime 16.0 Dia 0.97.2.2 Dr. Java 20140826-r5761 Eclipse 4.5.2 FileZilla 3.22.2.2 Final Draft Final Draft 8 Freedom Scientific Jaws Jaws 17 Gimp 2.8.18 JFLAP 7.0 JMP JMP 13 Kurzweil 3000 14 Lodestar 7.0 Microsoft FXCop 10.0 Microsoft Internet Explorer Internet Explorer 11 with Silverlight Microsoft Project Professional Project Professional 2016 32-bit Microsoft SQL Server Express Microsoft SQL Server Express 2012 Microsoft Visio Professional Visio Professional 2016 32-bit Microsoft Visual Studio Microsoft Visual Studio Pro 2015 Minitab 17.3 Mozilla Firefox Current Version MySQL Server 5.7 MySQL Workbench 6.3 Netbeans 8.2 Notepad++ 7.2 Oracle Java 32bit Runtime 8 update 111 Oracle Java Development Kit 8 update 111 PHStat2 3.6 Putty 0.67 Python 3.5.1 R Project 3.3.2 Racket 6.7 Page 1 of 5 Page 2 of 5 Software Package Spring 2017 Raptor Current Version SAP Client SAP Client 7.4.9 SAP Lumira 1.31.1 SAP Crystal Reports Current Version SPSS SPSS -

Program Windows Movie Maker (2012)
PaSA – CA – SZŠ INF/API: video editor Windows Movie Maker PaSA – CA – SZŠ INF/API: video editor Windows Movie Maker Program Windows Movie Maker (2012) Prehľad (čo je program Movie Maker) (ak chcete porozprávať svoj príbeh a vytvoriť zo svojich fotografií a videí ukážkový film už po pár kliknutiach, vaše Či už uprednostňujete Hollywood alebo nezávislú scénu, v programe Movie Maker ste režisérom vy. vlastné filmové štúdio získate jediným stiahnutím: http://go.microsoft.com/fwlink/p/?LinkID=255475 ) Import a úprava prezentácií a videí Zdroj: http://windows.microsoft.com/sk-sk/windows-live/movie-maker#t1=overview http://windows.microsoft.com/sk-sk/windows/music-video-photo-download Fotografie a videozáznamy z počítača alebo kamery môžete rýchlo pridať do programu Movie Maker . Tam potom http://sk.wikipedia.org/wiki/Windows_Movie_Maker , ... môžete doladiť svoj film podľa vlastných predstáv. Jednotlivé sekvencie môžete presúvať, zrýchľovať alebo spomaľovať – je len na vás, ako sa rozhodnete. Obsah: *) Úprava zvukovej stopy a pridanie motívu Charakteristika programu Niektoré systémové požiadavky Obohaťte svoj film o zvukovú stopu a motív . Program Movie Maker automaticky pridá prechody a efekty , aby film *) Prehľad ( čo je program Movie Maker) pôsobil elegantným a profesionálnym dojmom. Import fotografií a videí Zdieľanie filmu online (okrem toho naďalej môžete vaše video vypáliť na CD alebo DVD pre vaše domáce kino Úprava filmov alebo importovať do flashu) Úprava zvuku Výber motívu Po dokončení môžete svoj film zdieľať na Facebooku, YouTube alebo v iných sociálnych sieťach a lokalitách na Zdieľanie na webe zdieľanie videa. Pošlite prepojenie na svoj film v e-maile členom rodiny a priateľom, aby si ho mohli pozrieť . -

MBS Winicm Plugin Documentation
MBS WinICM Plugin Documentation Christian Schmitz July 16, 2017 2 0.1 Introduction This is the PDF version of the documentation for the Xojo (Real Studio) Plug-in from Monkeybread Software Germany. Plugin part: MBS WinICM Plugin 0.2 Content • 1 List of all topics 3 • 2 List of all classes 13 • 3 List of all modules 15 • 4 All items in this plugin 17 • 5 List of Questions in the FAQ 103 • 6 The FAQ 113 Chapter 1 List of Topics • 4 Windows ICM 17 { 4.1.1 class WindowsICMColorMBS 17 ∗ 4.1.3 a as Integer 17 ∗ 4.1.4 b as Integer 17 ∗ 4.1.5 black as Integer 18 ∗ 4.1.6 blue as Integer 18 ∗ 4.1.7 ch1 as Integer 18 ∗ 4.1.8 ch2 as Integer 18 ∗ 4.1.9 ch3 as Integer 18 ∗ 4.1.10 cyan as Integer 19 ∗ 4.1.11 gray as Integer 19 ∗ 4.1.12 green as Integer 19 ∗ 4.1.13 Index as Integer 19 ∗ 4.1.14 L as Integer 19 ∗ 4.1.15 magenta as Integer 20 ∗ 4.1.16 red as Integer 20 ∗ 4.1.17 XYZ X as Integer 20 ∗ 4.1.18 XYZ Y as Integer 20 ∗ 4.1.19 XYZ Z as Integer 20 ∗ 4.1.20 yellow as Integer 20 ∗ 4.1.21 Yxy x as Integer 21 ∗ 4.1.22 Yxy y as Integer 21 ∗ 4.1.23 Yxy YY as Integer 21 ∗ 4.1.24 Channel(index as Integer) as Integer 21 ∗ 4.1.26 COLOR 3 CHANNEL = 6 21 ∗ 4.1.27 COLOR 5 CHANNEL = 8 22 ∗ 4.1.28 COLOR 6 CHANNEL = 9 22 3 4 CHAPTER 1. -
Building a Windows 10 Image Creating Your Base Configuration
Building a Windows 10 Image Creating your Base Configuration Installation of Windows 10 Reference: http://www.tenforums.com/tutorials/2113-system-image-create-hardware-independent-system-i mage.html#post151664 1. Boot computer off installation media (DVD or USB with Windows 10 EDU) 2. The installer process will begin. Clean the drive you want to install -- delete all items/partitions. Windows 10 will rebuild the “WinRE” (recovery environment) partition. a. For images, you do not want a partition larger than the lowest common denominator drive size that may host the image (ie 128GB). b. If you are installing on a machine with a drive larger, create a partition of 128GB and leave the remaining portion “unallocated”. 3. Allow the installation to run. Using a VLM Windows 10 installer, we should not be prompted for a product key during the install. 4. Once installation is completed, you will then go into the “first run” (out of box) Windows setup screens. 5. Do NOT start the process of clicking through items. You need to immediately change Windows into Sysprep “Audit” mode. 1 6. Windows reboots, and enters Audit Mode using the built-in “Administrator” account. When the desktop loads, you will notice the Sysprep box open in the middle of your screen. Close it for now by pressing the Cancel button. a. NOTE on AUDIT MODE: Throughout image construction process, remain in AUDIT Mode. When reboots are required, system will boot back up and auto-login to Administrator account. Sysprep box will be presented. Simply hit CANCEL option each time. Creation of “Base” Image In this stage, you will start setup and customization of your “template” profile. -
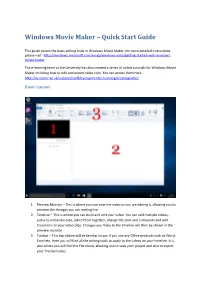
Windows Movie Maker – Quick Start Guide
Windows Movie Maker – Quick Start Guide This guide covers the basic editing tools in Windows Movie Maker, for more detailed instructions please visit - http://windows.microsoft.com/en-gb/windows-vista/getting-started-with-windows- movie-maker The e-learning team at the University has also created a series of online tutorials for Windows Movie Maker including how to edit and export video clips. You can access them here - http://as.exeter.ac.uk/support/staffdevelopment/e-learning/creatingvideo/ Basic Layout 1. Preview Monitor – This is where you can view the video as you are editing it, allowing you to preview the changes you are making live. 2. Timeline – This is where you can build and edit your video. You can add multiple videos, pictures and audio clips, splice them together, change the start and end points and add transitions to your video clips. Changes you make to the timeline will then be shown in the preview monitor. 3. Toolbar – This top ribbon will be familiar to you if you use any Office products such as Word, Excel etc. Here you will find all the editing tools to apply to the videos on your timeline. It is also where you will find the File menu, allowing you to save your project and also to export your finished video. Importing Video To get started you need to import a video that you have filmed. Click Home > Add videos and photos This will open up a new window, allowing you to browse your computer for video files. Choose a video and then select Open. -

Building a PC-Based Music Server / Transport
Building A PC-based Music Server / Transport Installation Guide for Windows 8.1 Contents References ................................................................................................. 3 Overview - The Principles of Computer Audio ............................................ 6 The Advantages of Computer Audio [from DCS guide to Computer Audio] .............................................................................................................. 6 The Disadvantages of Computer Audio [from DCS guide to Computer Audio] .................................................................................................... 7 The Computer as a Music File Transport ................................................. 8 “VerseTrasport” Hardware Components...................................................... 9 “VerseTrasport” Software Components ..................................................... 10 Digital-To-Analog Converter ................................................................... 11 VerseTrasport H/W Installation Procedure ................................................ 13 VerseTrasport S/W Installation Procedure................................................. 13 Install Windows 8.1 PRO ....................................................................... 13 Install ASUS Motherboard Drivers .......................................................... 13 Install AQUA DAC Drivers (Thesycon USB ASIO Driver Class 2.0 USB Audio drivers version 1.61b) .......................................................................... -

Video Editing with Microsoft Movie Maker Contents
Video Editing with Microsoft Movie Maker Contents Introduction ..................................................................................................................... 2 Creating a new project ..................................................................................................... 2 Importing footage ............................................................................................................ 3 Import from DV tape ..................................................................................................... 3 Question ................................................................................................................... 4 Getting started ................................................................................................................. 4 Editor view ....................................................................................................................... 5 Editing a clip ..................................................................................................................... 6 Splitting clips .................................................................................................................... 6 Splitting a clip ............................................................................................................... 7 Question ................................................................................................................... 7 Trimming clips .................................................................................................................