National Information Security Policy and Guidelines V5.0
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Les Services De Renseignement Et De Sécurité D'asie Du
Centre Français de Recherche sur le Renseignement 1 LES SERVICES DE RENSEIGNEMENT ET DE SÉCURITÉ D’ASIE DU SUD Général Alain LAMBALLE Rapport de recherche #20 Juillet 2017 2 PRÉSENTATION DE L’AUTEUR Le général de brigade (cadre de réserve) Alain Lamballe, Il participe à de nombreux colloques et est régulièrement spécialiste reconnu de l’Asie du Sud, a effectué l’essentiel de sollicité pour des conférences, en France et à l’étranger. sa carrière militaire dans le renseignement et les relations Il se déplace régulièrement dans tous les pays d’Asie du Sud. internationales. Il a été directeur de séminaire sur l’Asie du Sud au Collège Interarmées de Défense/École de guerre et chargé de cours Le général Lamballe est issu de l’académie militaire de St-Cyr sur l’Asie du Sud à l’École des Hautes Études Politiques, et titulaire d’un doctorat de 3e cycle en sociologie politique à l’École des Hautes Études Internationales et à l’École (École des Hautes Études en Sciences Sociales, Paris). Supérieure de Journalisme. Il est intervenu sur cette région Il est diplômé de l’Institut National des Langues et Civilisations du monde au Centre d’Études Diplomatiques et Stratégiques. Orientales (INALCO) en hindi, ourdou et hongrois, du Centre Il a participé à des émissions radio et télévision. Il a présidé des Hautes Études sur l’Afrique et l’Asie Modernes (CHEAM), l’association des auditeurs moyen-orientaux et asiatiques de de l’université de Delhi (en hindi). l’Institut des Hautes Études de Défense Nationale. Il possède également des diplômes militaires de langues Il contribue à la rédaction sur support électronique d’Asie21, étrangères (anglais, italien, allemand, hindi). -
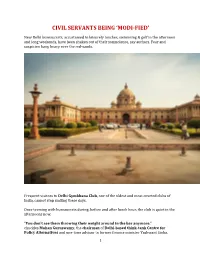
Civil Servants Being Modi-Fied
CIVIL SERVANTS BEING ‘MODI-FIED’ New Delhi bureaucrats, accustomed to leisurely lunches, swimming & golf in the afternoon and long weekends, have been shaken out of their somnolence, say authors. Fear and suspicion hang heavy over the red-sands. Frequent visitors to Delhi Gymkhana Club, one of the oldest and most coveted clubs of India, cannot stop smiling these days. Once teeming with bureaucrats during, before and after lunch hour, the club is quiet in the afternoons now. "You don't see them throwing their weight around in the bar anymore," chuckles Mohan Guruswamy, the chairman of Delhi-based think-tank Centre for Policy Alternatives and one-time advisor to former finance minister Yashwant Sinha. 1 The scene at India International Centre, another favourite hangout of bureaucrats, is similar. "It's now easier to get a table at IIC during lunch," says Guruswamy, clearly enjoying the development And the driveways of the Delhi Golf Club are deserted during office hours. "People would leave early in the evening to swim or play golf without completing the day's work. All that has changed," says a secretary with a ministry. For the civil servants posted at the Centre, life has seen an upheaval in the three months since Narendra Modi took over as the prime minister. Leisure has shrunk; work production has increased. 2 Officially, central government officers are still on a five-day week schedule, but most of them -- along with their clerks, peons and drivers -- are working almost every Saturday. If they are not clearing files, they're preparing for the week ahead because there is no telling when the Prime Minister's Office will call asking for a file. -

Mid-Career Interactions Between the Armed Forces and Civil Services Officers in Collaboration with the Ministry of Defence for the Last Many Years
~ 'fIi(i"f>Ii( i"f>IMi"f>. ~ rlli"f>l~d o~ -qw;r'1'=:i4I('1~ (PIMi"f> 3l1xyfu~ ~ P.K. Das, IAS yfu~ lJ1lflT Joint Secretary ~-4.~u1~~ VW~VJ el: 26106314 "flIT '16,<1<'1') ~. ~ ~-110067 Government of India Ministry of Personnel, Public Grievances & Pensions Department of Personnel & Training Training Division Block-IV, Old JNU Campus New Mehrauli Road, , New Delhi·110067 ; D.O.No.110111126/2014-Trg.(MCI) th !"r Dated 8 December, 2014 .l. Dear The Department of Personnel & Training has been organising Mid-Career Interactions between the Armed Forces and Civil Services officers in collaboration with the Ministry of Defence for the last many years. The basic objective of the programme is to increase exposure of the Civil Service Officers to the Armed Forces, so as to create better understanding and coordination for handling internal situations and helping them to combat future challenges to national security in an organised and professional manner. 2. A three day Mid Career Interaction between Armed Forces and Civil Services Officers on the theme 'Human Rights' is being organised at Indian Institute of Public Administration (lIP A) , New Delhi, during 10 - 12 February, 2015 for Armed Forces Officers and Civil Service Officers from the states of Delhi, Haryana, Punjab, Rajasthan, J & . K and the Civil Service officers working in the Ministries of Home Affairs, Defence, Women & Child Development, Social Justice & Empowerment, Tribal Affairs and Department of Personnel & Training. 3. You are therefore requested to nominate 3 - 4 senior level civil service officers of the rank of Director/Dy. -

Secretaries to the Government of India (As on 16/1/2013) SN Ministry
Secretaries to the Government of India (As On 16/1/2013) SN Ministry/Department Officer Name Service Email /Cadre 1 President Secretariat 1 - Secretary to the President Smt. Omita Paul (IIS:73)# 2 Vice President Secretariat 1 - Secretary to the Vice Shri Girija Sankar Patnaik (UT:80) [email protected] President 3 Prime Minister Office 1 - Principal Secretary to the Shri Pulok Chatterji (UP:74) [email protected] Prime Minister 2-Secretary Shri R.Ramanujam (MP:79) 4 Cabinet Secretariat 1 - Cabinet Secretary Shri Ajit Kumar Seth (UP:74) [email protected] 2 – Secretary (R) Shri S. K. Tripathi [email protected] 3 - Secretary(Security) Yashovardhan Azad IPS (MP:76) 4 - Secretary(Performance Mgt) Dr. Prajapati Trivedi Economist# [email protected] & Chairman, NACWC 5-Secretary (Coordination & Shri Alok Rawat ( SK:77) [email protected] PG) 5 M/O Agriculture 1 - D/O Agriculture and Shri Ashish Bahuguna (RJ:78) [email protected] Cooperation 2 - D/O Agricultural Research Dr S Ayyappan Scientist$ [email protected] and Education 3 - D/O Animal Husbandry, Shri Gokul Chandra Pati (OR:78) [email protected] Dairying and Fisheries 6 D/O Atomic Energy Dr. Ratan Kumar Sinha Scientist$ [email protected] 7 M/O Chemicals & Fertilizers 1 - D/O Chemicals and Petro Shri Indrajit Pal (AP:77) [email protected] Chemicals 2 - D/O Fertilizers Shri Sudhir Mittal (PB:78) [email protected] 3 - D/O Pharmaceuticals Shri Dilsher Singh Kalha (PB:77) [email protected] 8 M/O Civil Aviation Shri K.N.Srivastava (KN:78) [email protected] 9 M/O Coal Shri S.K. -

Rajya Sabha 159
PARLIAMENT OF INDIA RAJYA SABHA 159 DEPARTMENT-RELATED PARLIAMENTARY STANDING COMMITTEE ON HOME AFFAIRS ONE HUNDRED AND FIFTY NINTH REPORT ON THE CITIZENSHIP (AMENDMENT) BILL, 2011 (PRESENTED TO RAJYA SABHA ON 28TH MARCH, 2012) (LAID ON THE TABLE OF LOK SABHA ON 28TH MARCH, 2012) RAJYA SABHA SECRETARIAT NEW DELHI MARCH, 2012/CHAITRA, 1933 (SAKA) 107 Website:http://rajyasabha.nic.in E-mail:[email protected] C.S.(H.A.)-310 PARLIAMENT OF INDIA RAJYA SABHA DEPARTMENT-RELATED PARLIAMENTARY STANDING COMMITTEE ON HOME AFFAIRS ONE HUNDRED AND FIFTY NINTH REPORT ON THE CITIZENSHIP (AMENDMENT) BILL, 2011 (PRESENTED TO RAJYA SABHA ON 28TH MARCH, 2012) (LAID ON THE TABLE OF LOK SABHA ON 28TH MARCH, 2012) RAJYA SABHA SECRETARIAT NEW DELHI MARCH, 2012/CHAITRA, 1933 (SAKA) CONTENTS PAGES 1. COMPOSITION OF THE COMMITTEE ........................................................................................ (i)-(ii) 2. PREFACE ................................................................................................................................. (iii)-(iv) 3. REPORT .................................................................................................................................. 1—25 CHAPTER I : Background of The Bill ....................................................................... 1—4 CHAPTER II : Presentation of The Ministry of Home Affairs ............................... 5—14 CHAPTER III : Consideration of views/suggestions made in the Memoranda receive on the Bill ............................................................................... -

High Court of Delhi Advance Cause List
HIGH COURT OF DELHI ADVANCE CAUSE LIST LIST OF BUSINESS FOR th WEDNESDAY, THE 19 FEBRUARY, 2020 INDEX PAGES 1. APPELLATE JURISDICTION 01 TO 68 2. COMPANY JURISDICTION 69 TO 73 3. ORIGINAL JURISDICTION 74 TO 89 4. REGISTRAR GENERAL/ 90 TO 101 REGISTRAR (APPLT.)/ REGISTRAR (LISTING)/ REGISTRAR(ORGL.)/ JOINT REGISTRARS(ORGL). 19.02.2020 1 (APPELLATE JURISDICTION) 19.02.2020 [Note : Unless otherwise specified, before all appellate side courts, fresh matters shown in the supplementary lists will be taken up first.] COURT NO. 1 (DIVISION BENCH-I) HON'BLE THE CHIEF JUSTICE HON'BLE MR. JUSTICE C.HARI SHANKAR FOR ADMISSION _______________ 1. W.P.(C) 3431/2017 DEEPAK KHOSLA PET IN PERSON,JAYANT K CM APPL. 15005/2017 Vs. LD REGISTRAR (RULES MEHTA,SK TRIPATHI CM APPL. 15006/2017 COMMITTEE) HIGH COURT OF CM APPL. 15007/2017 DELHI AND ORS 2. W.P.(C) 1885/2019 ASAD ASHRAF SOURAV ROY,ARUN Vs. UNION OF INDIA AND ORS. BHARDWAJ,NARESH KAUSHIK,PR CHOPRA,K ENATOLI SEMA,NARESHKAUSHIK 3. W.P.(C) 8921/2019 M/S CAMRON EXPORTS THROUGH AKHIL KRISHAN MAGGU,AMIT ITS PARTNER SH. NARAYAN KAMAT BANSAL Vs. COMMISSIONER OF CUSTOMS INLAND CONTAINER DEPOT AFTER NOTICE MISC. MATTERS ____________________________ 4. CONT.CAS(C) 888/2019 DSGMC & ANR S S AHLUWALIA,AVNISH AHLAWAT WITH W.P.(C) 7550/2017 Vs. A K SINGH & ORS W.P.(C) 10259/2017 W.P.(C) 10550/2019 5. W.P.(C) 10259/2017 DSGMC AND ORS. S.S.AHLUWALIA,SANJOY GHOSE CM APPL. 41866/2017 Vs. GOVT OF NCT AND ORS 6. -

President's Report 2017
ANNUAL REPORT OF THE PRESIDENT OF THE COUNCIL : 2017 1. Gentlemen, it gives me great pleasure to welcome you to the second meeting of the present Council. The USI is a unique, autonomous Institution with unequalled expertise in the field of National Security and matters pertaining to the Defence Services. It has built an outstanding reputation over the last 147 years. It is my privilege to present the report of the Institution for the year 2017. A copy of the report has been placed on the table and will be included in the minutes of the meeting. MEMBERSHIP 2. The Institution began with a membership of 215 members and was 3500 when it moved to its present premises in 1996. Today we have 14,321 Members. It is heartening to report that during the current year 137 new Life Members, 43 Associate Members, 107 Ordinary Members and 1217 Course Members were enrolled. This continuous growth exemplifies the support and trust the Institution enjoys. FINANCES 3. The Institution does not get any grant / aid from the Ministry of Defence or the Services. It continues to carry out all its activities from the resources generated within. Since the USI Centres {Center for Strategic Studies and Simulation (CS3) and Center for Armed Forces Historical Research (CAFHR)} are not able to meet their annual expenditure, they are allocated resources from the Corpus Fund. Further, our building and equipment being more than two decades old, now require greater allocation of funds for their renovation and upkeep. 4. The Audit Report and Balance Sheet for 2016-17, Revised Estimates for 2017-18 and Budget Estimates for 2018-19 are already with you. -

Universidade Federal Do Rio Grande Do Sul Faculdade De Ciências Econômicas Programa De Pós-Graduação Em Estudos Estratégicos Internacionais
UNIVERSIDADE FEDERAL DO RIO GRANDE DO SUL FACULDADE DE CIÊNCIAS ECONÔMICAS PROGRAMA DE PÓS-GRADUAÇÃO EM ESTUDOS ESTRATÉGICOS INTERNACIONAIS GUSTAVO MÖLLER NATIONAL INTELLIGENCE SYSTEMS AS NETWORKS: BRAZIL, RUSSIA, INDIA, CHINA, AND SOUTH AFRICA Porto Alegre 2015 GUSTAVO MÖLLER NATIONAL INTELLIGENCE SYSTEMS AS NETWORKS: BRAZIL, RUSSIA, INDIA, CHINA, AND SOUTH AFRICA Dissertação submetida ao Programa de Pós- Graduação em Estudos Estratégicos Internacionais da Faculdade de Ciências Econômicas da UFRGS, como requisito parcial para obtenção do título de Mestre em Estudos Estratégicos Internacionais. Orientador: Dr. Marco Aurélio Chaves Cepik Porto Alegre 2015 GUSTAVO MÖLLER NATIONAL INTELLIGENCE SYSTEMS AS NETWORKS: BRAZIL, RUSSIA, INDIA, CHINA, AND SOUTH AFRICA Dissertação submetida ao Programa de Pós- Graduação em Estudos Estratégicos Internacionais da Faculdade de Ciências Econômicas da UFRGS, como requisito parcial para obtenção do título de Mestre em Estudos Estratégicos Internacionais. Aprovada em: Porto Alegre, 30 de setembro de 2015. BANCA EXAMINADORA: Prof. Dr. Marco Aurélio Chaves Cepik – Orientador UFRGS Prof. Dr. Carlos Hoppen UFRGS Prof. Dr. Paulo Sergio Peres UFRGS Prof. Dr. Eduardo Xavier Ferreira Migon ECEME AGRADECIMENTOS Aos meus pais, Rejane e Luís, por acreditarem em minha capacidade de chegar onde estou, apesar dos muitos contratempos. , Juliana, que apesar de ausente fisicamente, esteve presente. Ao restante da , e ao meu primo e irmão, Adriano. Ao meu orientador, Prof. Marco Cepik, por ter me proporcionado diversas oportunidades ao longo desses quase seis anos e ter sempre incentivado e apoiado todas minhas iniciativas profissionais e pessoais. Aos professores doutores e grandes pesquisadores Russel Swenson e Peter Gill, por gentilmente revisarem versões preliminares do artigo. A todos os colegas Cegovianos, atuais e aposentados. -

I PONTIFICIA UNIVERSIDAD CATÓLICA DEL ECUADOR
PONTIFICIA UNIVERSIDAD CATÓLICA DEL ECUADOR FACULTAD DE JURISPRUDENCIA ESCUELA DE DERECHO DISERTACIÓN PREVIA A LA OBTENCIÓN DEL TÍTULO DE ABOGADA “EL DERECHO A LA INTIMIDAD Y SU PROTECCIÓN CONTRA EL ESPIONAJE ESTATAL” KARLA ESTEFANÍA GELLIBERT GALARZA DIRECTOR: DR. ARTURO DONOSO CASTELLÓN QUITO, 2015 i SÍNTESIS La presente disertación se ha centrado en el estudio e investigación del derecho a la intimidad y la vulneración que ha tenido y tiene, cuando los Estados se ven en la necesidad de protegerse a sí mismos de inminentes ataques contra su seguridad y soberanía, justificando, muchas veces, su excesivo uso de poder, con argumentos muy propios de un Estado totalitario, y no toman en cuenta que, quienes resultan más perjudicados por su actuación, son sus habitantes, ya que no sólo su privacidad e intimidad son vulneradas, si no que se forma una cadena de afectaciones a nivel emocional, psicológico, mental, moral, y físico. La problematización que dio nacimiento a la presente disertación fue la duda que se origina al no saber si lo que tiene más peso es la soberanía estatal o los derechos de las personas; el no saber con exactitud si el Estado debe está en óptimas condiciones para que sus habitantes vivan bien, o si primero las personas deben estar plenamente protegidas y libres para que el Estado camine. Como objeto de esta disertación, he analizado que la sociedad contemporánea, con sus avances tecnológicos y científicos, hace que el ser humano se torne vulnerable, entre otros aspectos, frente al poder de la información y de los medios de comunicación. La vida personal, que antes era algo que se compartía con pocos y que terceros tenían un restringido acceso a ella, ahora es algo que quedó en el pasado, y los Estados, dentro de su rol de brindar seguridad a sus ciudadanos, juegan un papel de doble filo. -

Barkatullah Vishwavidyalaya, Bhopal ELECTORAL ROLL for the ELECTION to COURT from AMONGST the REGISTERED GRADUATES of BARKATULLAH VISHWAVIDYALAYA YEAR 1990
Barkatullah Vishwavidyalaya, Bhopal ELECTORAL ROLL FOR THE ELECTION TO COURT FROM AMONGST THE REGISTERED GRADUATES OF BARKATULLAH VISHWAVIDYALAYA YEAR 1990 Reg. Name & Address of Reg. Name & Address of No. Registered Graduate No. Registered Graduate 1. Mohd. Sharif Khan 2. Suniti Mohan Datta C/o Shri Akhlak Ahmed 69 N-2, C-Sector, Piplani P.O. Salamatpur, Distt. Raisen BHEL, Bhopal-21 3. Gambhir Mal Jain 4. Mohd. Azhar Qureshi Advocate, Ganj Basoda M.P. Allied Traders, Moti Masjid, Bhopal 5. Smt. Malati Saxena 6. Gulab Chand Jain C/o Shri M.C. Saxena, Advocate, Ganj Basoda Asstt. Prof. Govt College, Ganj Basoda 7. Uttam Chand Issrani 8. Radhe Shyam Sharma Advocate, 19-20, 134/2, Prof. Colony, Berasia Marg, Bhopal Bhopal-2 9. Subhash Ramchand Satarker 10. Jai Mal Atri Shiv Bhavan Berkhera, Bhopal Modha-Ki-Bagiya, Itwara, Bhopal 11. Laxmi Narain Sharma 12. Surendra Kumar Arun Chhola Road, Bhopal Madhya Pradesh Pustak Prakashan 4, Hamidia Raod Bhopal 13. Rama Kant Chaturvedi 14. Ramsewak Sharma C/o Shri Ambadatta Bhorti Shri L B S, College. Patrakar, Khajauch Line, Sehore Ganj Basoda 15. Brij Kumar Kapoor 16. Dr. Bhgwati Prasad Shukla Asstt. Professor of Hindi Professor of Hamidia Arts & Govt College, Ganj Basoda Com. College Bhopal 17. Mahesh Chandra saxena 18. Rajendra kumar jain Asst. professor of English, Advocate, Savarkar Chowk, Govt. college ganj basoda. Ganj Basoda. Barkatullah Vishwavidyalaya, Bhopal ELECTORAL ROLL FOR THE ELECTION TO COURT FROM AMONGST THE REGISTERED GRADUATES OF BARKATULLAH VISHWAVIDYALAYA YEAR 1990 Reg. Name & Address of Reg. Name & Address of No. Registered Graduate No. Registered Graduate 19. -

State of Cyber Security and Surveillance in India a Review of the Legal Landscape
State of Cyber Security and Surveillance in India A Review of the Legal Landscape Introduction The issue of cyber security and surveillance, especially unauthorised surveillance, though traditionally unprioritised, has recently gained much traction due to the increasing number of news reports regarding various instances of unauthorised surveillance and cyber crimes. In the case of unauthorised surveillance, more than the frequency of the instances, it is their sheer magnitude that has shocked civil society and especially civil rights groups. In the background of this ever increasing concern regarding surveillance as well as increasing concerns regarding cyber security due to the increased pervasiveness of technology in our society, this paper tries to discuss the legal and regulatory landscape regarding surveillance as well as cyber security. The paper starts with an overview of the right to privacy, which forms one of the fundamental elements of any challenge to illegal surveillance. It then discusses the legal provisions dealing with interception under the two main legislations utilised for surveillance as well as some of the minor statutes, and tries to highlight the conditions imposed and incorporated into the law to avoid unauthorised interception. The paper then discusses the provisions relevant to interception and surveillance incorporated in the License Agreements for Internet Service Providers (ISPs), Telecom Service Providers (TSPs) as well as the Unified Access Service (UAS) License. It then discusses the major provisions dealing with cyber security by elaborating on the relevant provisions in the Information Technology Act, 2000 as well as the Rules framed under it before exploring the connect between privacy and transparency and dealing with the provisions of the Right to Information Act, 2005 insofar as they are relevant to this discussion. -

High Court of Delhi Advance Cause List
HIGH COURT OF DELHI ADVANCE CAUSE LIST LIST OF BUSINESS FOR th WEDNESDAY, THE 10 JULY, 2019 INDEX PAGES 1. APPELLATE JURISDICTION 01 TO 61 2. COMPANY JURISDICTION 62 TO 64 3. ORIGINAL JURISDICTION 65 TO 75 4. REGISTRAR GENERAL/ 76 TO 88 REGISTRAR (APPLT.)/ REGISTRAR (LISTING)/ REGISTRAR(ORGL.)/ JOINT REGISTRARS(ORGL). 10.07.2019 1 (APPELLATE JURISDICTION) 10.07.2019 [Note : Unless otherwise specified, before all appellate side courts, fresh matters shown in the supplementary lists will be taken up first.] COURT NO. 1 (DIVISION BENCH-I) HON'BLE THE CHIEF JUSTICE HON'BLE MR. JUSTICE C.HARI SHANKAR FRESH MATTERS & APPLICATIONS ______________________________ 1. W.P.(C) 2826/2019 STANLEY FERNANDES VIKRAM SINGH CM APPL. 13174/2019 Vs. COMMISSIONER OF CUSTOMS ( EXPORT) 2. W.P.(C) 6847/2019 ADITYA YADAV AND ANR. ADITYA YADAV CM APPL. 28554/2019 Vs. UNIVERISTY OF DELHI CM APPL. 28555/2019 FOR ADMISSION _______________ 3. CM APPL. 24188/2019 FIROZ BAKHT AHMED M. ATYAB SIDDIQUI,SRIPARNA In W.P.(C) 7612/2015 Vs. GOVERNMENT OF NATIONAL CHATTERJEE,SANJAY GHOSE,ARJUN CAPITAL TERRITORY OF DELHI & PANT,RAJIV BANSAL,MANOJ ORS RANJAN SINHA,DIWAN SINGH CHAUHAN,MONIKA ARORA & ASSOCIATES,WAJEEH SHAFIQ,MONIKA ARORA (Disposed-off Case) 4. W.P.(C) 12794/2018 VIRENDER KUMAR SHIV CHARAN GARG & Vs. NORTH DELHI MUNICIPAL ASSOCIATES,PUJA KALRA CORPORATION & ORS AFTER NOTICE MISC. MATTERS ____________________________ 5. LPA 128/2019 M/S JAGDAMBA SALES R K GOEL,GAUTAM NARAYAN CM APPL. 9189/2019 CORPORATION CM APPL. 9191/2019 Vs. STATE (GNCT OF DELHI ) & ORS 6. SERTA 6/2019 M/S AVADH ENTERPRISES, RUCHIR BHATIA CM APPL.