Aspect Weaving in Standard Java Class Libraries
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

A Brief Introduction to Aspect-Oriented Programming
R R R A Brief Introduction to Aspect-Oriented Programming" R R Historical View Of Languages" R •# Procedural language" •# Functional language" •# Object-Oriented language" 1 R R Acknowledgements" R •# Zhenxiao Yang" •# Gregor Kiczales" •# Eclipse website for AspectJ (www.eclipse.org/aspectj) " R R Procedural Language" R •# Also termed imperative language" •# Describe" –#An explicit sequence of steps to follow to produce a result" •# Examples: Basic, Pascal, C, Fortran" 2 R R Functional Language" R •# Describe everything as a function (e.g., data, operations)" •# (+ 3 4); (add (prod 4 5) 3)" •# Examples" –# LISP, Scheme, ML, Haskell" R R Logical Language" R •# Also termed declarative language" •# Establish causal relationships between terms" –#Conclusion :- Conditions" –#Read as: If Conditions then Conclusion" •# Examples: Prolog, Parlog" 3 R R Object-Oriented Programming" R •# Describe " –#A set of user-defined objects " –#And communications among them to produce a (user-defined) result" •# Basic features" –#Encapsulation" –#Inheritance" –#Polymorphism " R R OOP (cont$d)" R •# Example languages" –#First OOP language: SIMULA-67 (1970)" –#Smalltalk, C++, Java" –#Many other:" •# Ada, Object Pascal, Objective C, DRAGOON, BETA, Emerald, POOL, Eiffel, Self, Oblog, ESP, POLKA, Loops, Perl, VB" •# Are OOP languages procedural? " 4 R R We Need More" R •# Major advantage of OOP" –# Modular structure" •# Potential problems with OOP" –# Issues distributed in different modules result in tangled code." –# Example: error logging, failure handling, performance -

Weaving Ontology Aspects Using a Catalog of Structural Ontology Design Patterns
Weaving Ontology Aspects Using a Catalog of Structural Ontology Design Patterns Ralph Schäfermeier and Adrian Paschke Corporate Semantic Web Group, Institute of Computer Science, Freie Universität Berlin, Germany {schaef,paschke}@inf.fu-berlin.de http://www.csw.inf.fu-berlin.de Abstract. Modular development of ontologies proves beneficial at dif- ferent stages of the ontology lifecycle. In our previous work, we proposed aspect-oriented ontology development as a flexible approach to modular ontology development and a-posteriori modularization of existing mono- lithic ontologies, inspired by aspect-oriented programming and based on so called cross-cutting concerns. Similar to other formalisms for mod- ular ontologies (e.g. E-Connections), aspect-oriented ontologies rely on an extension of the used ontology language. This derivation from the standard in turn requires specially adapted tools in order to use these ontologies in applications. In this paper, we present an approach to the recombination of aspect-oriented ontology modules to standard OWL 2 ontologies by using an aspect-weaving service. The weaving service relies on a preconfigured catalog of structural ontology design patterns. We show that the use of the weaving service yields syntactically correct and semantically complete ontologies while still allowing ontology developers to fully benefit from modular ontology development. Keywords: Aspect-Oriented Ontology Development, Aspect-Oriented Programming, Ontology Modularization, Ontology Design Patterns 1 Introduction Modular ontology development has proved beneficial when it comes to improve- ment of reasoning and query result retrieval performance, scalability for ontol- ogy evolution and maintenance, complexity management, amelioration of un- derstandability, reuse, context-awareness, and personalization [17]. A significant amount of research work has been dedicated in the field of ontology modular- ization, and various kinds of approaches tackle the problem from different per- spectives. -

Actors at Work Issue Date: 2016-12-15 Actors at Work Behrooz Nobakht
Cover Page The handle http://hdl.handle.net/1887/45620 holds various files of this Leiden University dissertation Author: Nobakht, Behrooz Title: Actors at work Issue Date: 2016-12-15 actors at work behrooz nobakht 2016 Leiden University Faculty of Science Leiden Institute of Advanced Computer Science Actors at Work Actors at Work Behrooz Nobakht ACTORS AT WORK PROEFSCHRIFT ter verkrijging van de graad van doctor aan de Universiteit Leiden op gezag van de Rector Magnificus prof. dr. C. J. J. M. Stolker, volgens besluit van het College voor Promoties te verdedigen op donderdag 15 december 2016 klokke 11.15 uur door Behrooz Nobakht geboren te Tehran, Iran, in 1981 Promotion Committee Promotor: Prof. Dr. F.S. de Boer Co-promotor: Dr. C. P. T. de Gouw Other members: Prof. Dr. F. Arbab Dr. M.M. Bonsangue Prof. Dr. E. B. Johnsen University of Oslo, Norway Prof. Dr. M. Sirjani Reykjavik University, Iceland The work reported in this thesis has been carried out at the Center for Mathematics and Computer Science (CWI) in Amsterdam and Leiden Institute of Advanced Computer Science at Leiden University. This research was supported by the European FP7-231620 project ENVISAGE on Engineering Virtualized Resources. Copyright © 2016 by Behrooz Nobakht. All rights reserved. October, 2016 Behrooz Nobakht Actors at Work Actors at Work, October, 2016 ISBN: 978-94-028-0436-2 Promotor: Prof. Dr. Frank S. de Boer Cover Design: Ehsan Khakbaz <[email protected]> Built on 2016-11-02 17:00:24 +0100 from 397717ec11adfadec33e150b0264b0df83bdf37d at https://github.com/nobeh/thesis using: This is pdfTeX, Version 3.14159265-2.6-1.40.16 (TeX Live 2015/Debian) kpathsea version 6.2.1 Leiden University Leiden Institute of Advanced Computer Science Faculty of Science Niels Bohrweg 1 2333 CA and Leiden Contents I Introduction1 1 Introduction 3 1.1 Objectives and Architecture . -

Aspectj in Action, Second Edition
Introducing AspectJ This chapter covers ■ Writing an AspectJ “Hello, world!” application ■ Becoming familiar with the AspectJ language ■ Weaving mechanisms ■ Integrating with Spring In chapter 1, we focused on general concepts in AOP. With those behind us, we can now look at one specific AOP implementation: AspectJ. AspectJ is an aspect- oriented extension to the Java programming language. Like any AOP implementa- tion, AspectJ consists of two parts: the language specification, which defines the grammar and semantics of the language; and the language implementation, which includes weavers that take various forms such as a compiler and a linker. A weaver produces byte code that conforms to the Java byte-code specification, allowing any compliant Java virtual machine (VM) to execute those class files. The language implementation also offers support for integrated development environments (IDEs), to simplify building and debugging applications. AspectJ started and initially grew as a special language that extends the Java lan- guage with new keywords. It also provided a special compiler that could understand those extensions. But recently, a lot has changed in its form as a language, as well as 27 Licensed to Manning Marketing <[email protected]> 28 CHAPTER 2 Introducing AspectJ in the weaver. First, AspectJ offers an alternative syntax based on the Java annotation facil- ity to express crosscutting constructs. This lets you use a plain Java compiler instead of the special compiler. Second, AspectJ offers new options for weaving classes with aspects. Finally, it has gained a strong foothold in the Spring Framework with several integration options. All these changes have made adoption of AspectJ easier than ever before. -

Aspect-Oriented Software Development for Real-Time and Internet Applications
International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056 Volume: 05 Issue: 09 | Sep 2018 www.irjet.net p-ISSN: 2395-0072 Aspect-Oriented Software Development for Real-Time and Internet Applications Ogbonna J. C.1, Nwokoma F. O.2, Nwala K. T.3, Nwandu I. C.4 1,3Reseacher, Dept. of Computer Science, Clifford University Owerrinta, Abia State Nigeria 2,4Reseacher, Dept. of Computer Science, Federal University of Technology Owerri, Imo State Nigeria ---------------------------------------------------------------------***--------------------------------------------------------------------- Abstract - Software development evolution has introduced and increasing the reusability of a software product, which a number of useful software development methods. Efficient in turns results in better software development. modularization of program artifacts that cut across multiple AOP is based on the idea that computer systems are better locations during software development called crosscutting programmed by separately specifying the various concerns concerns have been a major drawback for these software (properties or areas of interest) of a system and some development methods including the almighty Object-Oriented description of their relationships, and then relying on Software Development method. Concerns like recovery, mechanisms in the underlying AOP environment to weave or synchronization, logging, encryption, authentication, compose them together into a coherent program (Elrad, authorization, validation, verification, -

Model-Based Aspect Weaver Construction
Model-based Aspect Weaver Construction Suman Roychoudhury1, Frédéric Jouault2,1, and Jeff Gray1 1 University of Alabama at Birmingham, Birmingham, AL 35294 {roychous, gray}@cis.uab.edu 2 ATLAS group (INRIA & LINA), University of Nantes, France [email protected] Abstract. This paper describes an approach that combines model engineering with program transformation techniques to construct aspect weavers for general-purpose programming languages. The front-end of the weaver uses a high-level language (i.e., an aspect language) to specify aspects and is designed with a metamodel-based approach using the AMMA toolsuite. The back-end of the weaver uses transformation rules, which are generated from these high-level aspect specifications, to perform the actual low-level weaving. Both the aspect specification (front-end) and transformation rules (back-end) are captured as models within the AMMA platform. The translation from source aspect model to target transformation model is achieved using ATL, which is a model transformation language. Keywords: model transformation, program transformation, model engineering, aspect-oriented-programming, software engineering. 1 Introduction Program transformation systems have been used in the past to construct aspect weavers for programming languages [1]. Program transformation engines (PTEs) such as the Design Maintenance System (DMS) [2], or ASF+SDF [3], provide direct availability of scalable parsers and an underlying low-level transformation framework to modify source programs. This low-level transformation framework (that generally uses term-rewriting or graph-rewriting techniques to modify base code) can form the basis of constructing aspect weavers [4]. In our previous research, we demonstrated how a term-rewriting PTE like DMS can be used to construct an aspect weaver for a general-purpose programming language (GPL) like ObjectPascal [1]. -

Java Optimizations Using Bytecode Templates
FACULDADE DE ENGENHARIA DA UNIVERSIDADE DO PORTO Java Optimizations Using Bytecode Templates Rubén Ramos Horta Mestrado Integrado em Engenharia Informática e Computação Supervisor: Professor Doutor João Manuel Paiva Cardoso July 28, 2016 c Rubén Ramos Horta, 2016 Java Optimizations Using Bytecode Templates Rubén Ramos Horta Mestrado Integrado em Engenharia Informática e Computação July 28, 2016 Resumo Aplicações móveis e embebidas funcionam em ambientes com poucos recursos e que estão sujeitos a constantes mudanças no seu contexto operacional. Estas características dificultam o desenvolvi- mento deste tipo de aplicações pois a volatilidade e as limitações de recursos levam muitas vezes a uma diminuição do rendimento e a um potencial aumento do custo computacional. Além disso, as aplicações que têm como alvo ambientes móveis e embebidos (por exemplo, Android) necessitam de adaptações e otimizações para fiabilidade, manutenção, disponibilidade, segurança, execução em tempo real, tamanho de código, eficiência de execução e também consumo de energia. Esta dissertação foca-se na otimização, em tempo de execução, de programas Java, com base na aplicação de otimizações de código baseadas na geração de bytecodes em tempo de execução, usando templates. Estes templates, fornecem geração de bytecodes usando informação apenas disponível em tempo de execução. Este artigo propõe uma estratégia para o desenvolvimento desses templates e estuda o seu impacto em diferentes plataformas. i ii Resumen Las aplicaciones móviles y embedded trabajan en entornos limitados de recursos y están sujetas a constantes cambios de escenario. Este tipo de características desafían el desarrollo de este tipo de aplicaciones en términos de volatibilidad y limitación de recursos que acostumbran a afec- tar al rendimiento y también producen un incremento significativo en el coste computacional. -
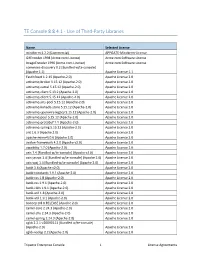
TE Console 8.8.4.1 - Use of Third-Party Libraries
TE Console 8.8.4.1 - Use of Third-Party Libraries Name Selected License mindterm 4.2.2 (Commercial) APPGATE-Mindterm-License GifEncoder 1998 (Acme.com License) Acme.com Software License ImageEncoder 1996 (Acme.com License) Acme.com Software License commons-discovery 0.2 [Bundled w/te-console] (Apache 1.1) Apache License 1.1 FastInfoset 1.2.15 (Apache-2.0) Apache License 2.0 activemQ-broker 5.15.12 (Apache-2.0) Apache License 2.0 activemQ-camel 5.15.12 (Apache-2.0) Apache License 2.0 activemQ-client 5.13.2 (Apache-2.0) Apache License 2.0 activemQ-client 5.15.12 (Apache-2.0) Apache License 2.0 activemQ-jms-pool 5.15.12 (Apache-2.0) Apache License 2.0 activemQ-kahadb-store 5.15.12 (Apache-2.0) Apache License 2.0 activemQ-openwire-legacy 5.15.12 (Apache-2.0) Apache License 2.0 activemQ-pool 5.15.12 (Apache-2.0) Apache License 2.0 activemQ-protobuf 1.1 (Apache-2.0) Apache License 2.0 activemQ-spring 5.15.12 (Apache-2.0) Apache License 2.0 ant 1.6.3 (Apache 2.0) Apache License 2.0 apache-mime4j 0.6 (Apache 2.0) Apache License 2.0 avalon-framework 4.2.0 (Apache v2.0) Apache License 2.0 awaitility 1.7.0 (Apache-2.0) Apache License 2.0 axis 1.4 [Bundled w/te-console] (Apache v2.0) Apache License 2.0 axis-jaxrpc 1.4 [Bundled w/te-console] (Apache 2.0) Apache License 2.0 axis-saaj 1.4 [Bundled w/te-console] (Apache 2.0) Apache License 2.0 batik 1.6 (Apache v2.0) Apache License 2.0 batik-constants 1.9.1 (Apache-2.0) Apache License 2.0 batik-css 1.8 (Apache-2.0) Apache License 2.0 batik-css 1.9.1 (Apache-2.0) Apache License 2.0 batik-i18n 1.9.1 (Apache-2.0) -

Full-Graph-Limited-Mvn-Deps.Pdf
org.jboss.cl.jboss-cl-2.0.9.GA org.jboss.cl.jboss-cl-parent-2.2.1.GA org.jboss.cl.jboss-classloader-N/A org.jboss.cl.jboss-classloading-vfs-N/A org.jboss.cl.jboss-classloading-N/A org.primefaces.extensions.master-pom-1.0.0 org.sonatype.mercury.mercury-mp3-1.0-alpha-1 org.primefaces.themes.overcast-${primefaces.theme.version} org.primefaces.themes.dark-hive-${primefaces.theme.version}org.primefaces.themes.humanity-${primefaces.theme.version}org.primefaces.themes.le-frog-${primefaces.theme.version} org.primefaces.themes.south-street-${primefaces.theme.version}org.primefaces.themes.sunny-${primefaces.theme.version}org.primefaces.themes.hot-sneaks-${primefaces.theme.version}org.primefaces.themes.cupertino-${primefaces.theme.version} org.primefaces.themes.trontastic-${primefaces.theme.version}org.primefaces.themes.excite-bike-${primefaces.theme.version} org.apache.maven.mercury.mercury-external-N/A org.primefaces.themes.redmond-${primefaces.theme.version}org.primefaces.themes.afterwork-${primefaces.theme.version}org.primefaces.themes.glass-x-${primefaces.theme.version}org.primefaces.themes.home-${primefaces.theme.version} org.primefaces.themes.black-tie-${primefaces.theme.version}org.primefaces.themes.eggplant-${primefaces.theme.version} org.apache.maven.mercury.mercury-repo-remote-m2-N/Aorg.apache.maven.mercury.mercury-md-sat-N/A org.primefaces.themes.ui-lightness-${primefaces.theme.version}org.primefaces.themes.midnight-${primefaces.theme.version}org.primefaces.themes.mint-choc-${primefaces.theme.version}org.primefaces.themes.afternoon-${primefaces.theme.version}org.primefaces.themes.dot-luv-${primefaces.theme.version}org.primefaces.themes.smoothness-${primefaces.theme.version}org.primefaces.themes.swanky-purse-${primefaces.theme.version} -

Static and Dynamic Approaches to Weaving
5th Slovakian-Hungarian Joint Symposium on Applied Machine Intelligence and Informatics January 25-26, 2007 ░ Poprad, Slovakia Static and Dynamic Approaches to Weaving Michal Forgáč, Ján Kollár Department of Computers and Informatics, Faculty of Electrical Engineering and Informatics, Technical University of Košice, Letná 9, 042 00 Košice, Slovakia [email protected], [email protected] Abstract: In this paper we present current state of principles and applications in static and dynamic weaving. We are concentrating on static weaving in AspectJ and dynamic weaving in PROSE - PROgrammable extenSions of sErvice. The contribution of this paper is in analyses of both approaches to weaving which we aim to apply as essential mechanisms when constructing software systems by automatic evolution. Keywords: Aspect oriented programming, systems engineering, weaving mechanisms, AspectJ, PROSE1 1 Introduction As a complexity of software systems grows, the need for advanced methods and tools of their specification and the development is the task of the high importance. Object oriented programming (OOP) has increased the productivity of systems rapidly. Benefits of object orientation include support for modular design, code sharing, and extensibility [15]. Object orientation has enabled using inheritance and polymorphism in sence of Strachey's original definition of polymorphism [16]. However, the key issue in application of object approach is that it is not sufficient for crosscutting concerns. One of the fundamental principles of the software engineering is a principle of separation of concerns. A concern is a particular goal, concept, or area of interest, it means that it is in substance semantical concern. From the structural point of view a concern may appear in source code as [4]: This work has been supported by the Scientific grant agency project (VEGA) No. -

Efficient Runtime Aspect Weaving for Java Applications
Efficient Runtime Aspect Weaving for Java Applications Oscar Rodriguez-Prietoa, Francisco Ortina,∗, Donna O'Sheab aUniversity of Oviedo, Computer Science Department, Calvo Sotelo s/n, 33007, Oviedo, Spain bCork Institute of Technology, Department of Computer Science, Rossa Avenue, Bishopstown, Cork, Ireland Abstract Context: The aspect-oriented paradigm is aimed at solving the code scattering and tangling problem, providing new mechanisms to support better separation of concerns. For specific scenarios where high runtime adaptability is an important requirement, dynamic Aspect-Oriented Programming (AOP) represents a useful tool. With dynamic AOP, components and aspects can be woven and unwoven at runtime, enabling appli- cations greater responsiveness when dealing with different or changing requirements. However, this responsiveness typically incurs a cost in terms of runtime performance and memory consumption. Objective: Build an efficient dynamic aspect weaver for Java that provides the best runtime performance compared to the existing approaches, minimum memory overhead consumption, and similar functionalities to the widespread runtime weavers. Method: We design and implement weaveJ, a dynamic aspect weaver for Java. This dynamic weaver leverages the invokedynamic opcode introduced in Java 7, which allows dynamic relinkage of method and field access. We compare the functionalities of weaveJ with the existing dynamic weavers for Java, and evaluate their runtime performance and memory consumption. Results: weaveJ shows the best runtime performance for all benchmarks and real applications executed. Method interception with invokedynamic is at least 142% faster than the techniques used by the existing runtime weavers. The average cost of dynamic weaving using invokedynamic is only 2.2% for short running programs, and 1.5% for long running applications. -

Comprehensive Aspect Weaving for Java
Science of Computer Programming 76 (2011) 1015–1036 Contents lists available at ScienceDirect Science of Computer Programming journal homepage: www.elsevier.com/locate/scico Comprehensive aspect weaving for Java Alex Villazón ∗, Walter Binder, Philippe Moret, Danilo Ansaloni Faculty of Informatics, University of Lugano, CH-6900 Lugano, Switzerland article info a b s t r a c t Article history: Aspect-oriented programming (AOP) has been successfully applied to application code Received 20 July 2009 thanks to techniques such as Java bytecode instrumentation. Unfortunately, with existing Received in revised form 19 October 2009 AOP frameworks for Java such as AspectJ, aspects cannot be woven into the standard Java Accepted 2 December 2009 class library. This restriction is particularly unfortunate for aspects that would benefit Available online 29 April 2010 from comprehensive aspect weaving with complete method coverage, such as profiling or debugging aspects. In this article we present MAJOR, a new tool for comprehensive aspect Keywords: weaving, which ensures that aspects are woven into all classes loaded in a Java Virtual Aspect-oriented programming Aspect weaving Machine, including those in the standard Java class library. MAJOR includes the pluggable Bytecode instrumentation module CARAJillo, which supports efficient access to a complete and customizable calling Profiling context representation. We validate our approach with three case studies. Firstly, we Debugging weave existing profiling aspects with MAJOR which otherwise would generate incomplete Detecting memory leaks profiles. Secondly, we introduce an aspect for memory leak detection that also benefits Recreating crashing conditions from comprehensive weaving. Thirdly, we present an aspect subsuming the functionality Java Virtual Machine of ReCrash, an existing tool based on low-level bytecode instrumentation techniques that generates unit tests to reproduce program failures.