Systematic Discovery of Android Customization Hazards
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

FIT to WORK: IMPROVING the SECURITY of MONITORED EMPLOYEES' HEALTH DATA Elizabeth A. Brown INTRODUCTION Imagine Coming to Work
FIT TO WORK: IMPROVING THE SECURITY OF MONITORED EMPLOYEES' HEALTH DATA Elizabeth A. Brown1 INTRODUCTION Imagine coming to work one day and finding that your employer has given everyone in the company a wearable FitBit health monitor, free of charge. You pop the FitBit on, grateful for another bit of help in managing the health concerns that nag at you persistently but which never quite rise to the top of your priority list. At your next performance review, your supervisor expresses concern about your anxiety levels. Although your work output is slightly off, she notes, there has been a correlation in your lack of sleep and exercise, and she suspects you are depressed. You wonder how your employer might know these things, whether or not they are true, and then you remember the FitBit. Your supervisor then tells you that the promotion you had wanted is going to a colleague who is “better equipped to handle the demands of the job.” You interview for another job, and are asked to provide the password to the HealthDrive account that centralizes the fitness data all the apps on your iPhone collect about you during the day. Similar scenarios are playing out now in workplaces across the country, and will do so more frequently as the personal health sensor market and employee monitoring trends continue to grow. Employers are making key decisions based on employees’ biometric data, collected from specialized devices like a FitBit or the health-related apps installed on mobile phones. BP, for example, adjusts its employees’ health care premiums depending on how much physical activity their wearable FitBit devices monitor – devices that BP provides to thousands of employees, their spouses, and retirees for free. -

Your Voice Assistant Is Mine: How to Abuse Speakers to Steal Information and Control Your Phone ∗ †
Your Voice Assistant is Mine: How to Abuse Speakers to Steal Information and Control Your Phone ∗ y Wenrui Diao, Xiangyu Liu, Zhe Zhou, and Kehuan Zhang Department of Information Engineering The Chinese University of Hong Kong {dw013, lx012, zz113, khzhang}@ie.cuhk.edu.hk ABSTRACT General Terms Previous research about sensor based attacks on Android platform Security focused mainly on accessing or controlling over sensitive compo- nents, such as camera, microphone and GPS. These approaches Keywords obtain data from sensors directly and need corresponding sensor invoking permissions. Android Security; Speaker; Voice Assistant; Permission Bypass- This paper presents a novel approach (GVS-Attack) to launch ing; Zero Permission Attack permission bypassing attacks from a zero-permission Android application (VoicEmployer) through the phone speaker. The idea of 1. INTRODUCTION GVS-Attack is to utilize an Android system built-in voice assistant In recent years, smartphones are becoming more and more popu- module – Google Voice Search. With Android Intent mechanism, lar, among which Android OS pushed past 80% market share [32]. VoicEmployer can bring Google Voice Search to foreground, and One attraction of smartphones is that users can install applications then plays prepared audio files (like “call number 1234 5678”) in (apps for short) as their wishes conveniently. But this convenience the background. Google Voice Search can recognize this voice also brings serious problems of malicious application, which have command and perform corresponding operations. With ingenious been noticed by both academic and industry fields. According to design, our GVS-Attack can forge SMS/Email, access privacy Kaspersky’s annual security report [34], Android platform attracted information, transmit sensitive data and achieve remote control a whopping 98.05% of known malware in 2013. -

User Guide Guía Del Usuario Del Guía GH68-43542A Printed in USA SMARTPHONE
User Guide User Guide GH68-43542A Printed in USA Guía del Usuario del Guía SMARTPHONE User Manual Please read this manual before operating your device and keep it for future reference. Legal Notices Warning: This product contains chemicals known create source code from the software. No title to or to the State of California to cause cancer and ownership in the Intellectual Property is transferred to reproductive toxicity. For more information, please call you. All applicable rights of the Intellectual Property 1-800-SAMSUNG (726-7864). shall remain with SAMSUNG and its suppliers. Intellectual Property Open Source Software Some software components of this product All Intellectual Property, as defined below, owned by incorporate source code covered under GNU General or which is otherwise the property of Samsung or its Public License (GPL), GNU Lesser General Public respective suppliers relating to the SAMSUNG Phone, License (LGPL), OpenSSL License, BSD License and including but not limited to, accessories, parts, or other open source licenses. To obtain the source code software relating there to (the “Phone System”), is covered under the open source licenses, please visit: proprietary to Samsung and protected under federal http://opensource.samsung.com. laws, state laws, and international treaty provisions. Intellectual Property includes, but is not limited to, inventions (patentable or unpatentable), patents, trade secrets, copyrights, software, computer programs, and Disclaimer of Warranties; related documentation and other works of authorship. -

Understanding and Mitigating Security Risks of Voice-Controlled Third-Party Functions on Virtual Personal Assistant Systems
Dangerous Skills: Understanding and Mitigating Security Risks of Voice-Controlled Third-Party Functions on Virtual Personal Assistant Systems Nan Zhang∗, Xianghang Mi∗, Xuan Fengy∗, XiaoFeng Wang∗, Yuan Tianz and Feng Qian∗ ∗Indiana University, Bloomington Email: fnz3, xmi, xw7, [email protected] yBeijing Key Laboratory of IOT Information Security Technology, Institute of Information Engineering, CAS, China Email: [email protected] zUniversity of Virginia Email: [email protected] Abstract—Virtual personal assistants (VPA) (e.g., Amazon skills by Amazon and actions by Google1) to offer further Alexa and Google Assistant) today mostly rely on the voice helps to the end users, for example, order food, manage bank channel to communicate with their users, which however is accounts and text friends. In the past year, these ecosystems known to be vulnerable, lacking proper authentication (from the user to the VPA). A new authentication challenge, from the VPA are expanding at a breathtaking pace: Amazon claims that service to the user, has emerged with the rapid growth of the VPA already 25,000 skills have been uploaded to its skill market to ecosystem, which allows a third party to publish a function (called support its VPA (including the Alexa service running through skill) for the service and therefore can be exploited to spread Amazon Echo) [1] and Google also has more than one thousand malicious skills to a large audience during their interactions actions available on its market for its Google Home system with smart speakers like Amazon Echo and Google Home. In this paper, we report a study that concludes such remote, large- (powered by Google Assistant). -
SAMSUNG GALAXY S6 USER GUIDE Table of Contents
SAMSUNG GALAXY S6 USER GUIDE Table of Contents Basics 55 Camera 71 Gallery 4 Read me first 73 Smart Manager 5 Package contents 75 S Planner 6 Device layout 76 S Health 8 SIM or USIM card 79 S Voice 10 Battery 81 Music 14 Turning the device on and off 82 Video 15 Touchscreen 83 Voice Recorder 18 Home screen 85 My Files 24 Lock screen 86 Memo 25 Notification panel 86 Clock 28 Entering text 88 Calculator 31 Screen capture 89 Google apps 31 Opening apps 32 Multi window 37 Device and data management 41 Connecting to a TV Settings 43 Sharing files with contacts 91 Introduction 44 Emergency mode 91 Wi-Fi 93 Bluetooth 95 Flight mode Applications 95 Mobile hotspot and tethering 96 Data usage 45 Installing or uninstalling apps 97 Mobile networks 46 Phone 97 NFC and payment 49 Contacts 100 More connection settings 51 Messages 102 Sounds and notifications 53 Internet 103 Display 54 Email 103 Motions and gestures 2 Table of Contents 104 Applications 104 Wallpaper 105 Themes 105 Lock screen and security 110 Privacy and safety 113 Easy mode 113 Accessibility 114 Accounts 115 Backup and reset 115 Language and input 116 Battery 116 Storage 117 Date and time 117 User manual 117 About device Appendix 118 Accessibility 133 Troubleshooting 3 Basics Read me first Please read this manual before using the device to ensure safe and proper use. • Descriptions are based on the device’s default settings. • Some content may differ from your device depending on the region, service provider, model specifications, or device’s software. -
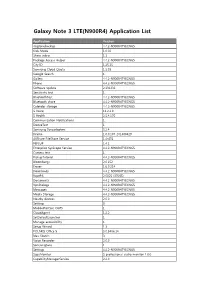
Galaxy Note 3 LTE(N900R4) Application List
Galaxy Note 3 LTE(N900R4) Application List Application Version ringtonebackup 4.4.2-N900R4TYECNG5 Kids Mode 1.0.02 Share video 1.1 Package Access Helper 4.4.2-N900R4TYECNG5 City ID 1.25.15 Samsung Cloud Quota 1.5.03 Google Search 1 Gallery 4.4.2-N900R4TYECNG5 Phone 4.4.2-N900R4TYECNG5 Software update 2.131231 Sensitivity test 1 BluetoothTest 4.4.2-N900R4TYECNG5 Bluetooth share 4.4.2-N900R4TYECNG5 Calendar storage 4.4.2-N900R4TYECNG5 S Voice 11.2.2.0 S Health 2.5.4.170 Communication Notifications 1 DeviceTest 1 Samsung Syncadapters 5.2.4 Drama 1.0.0.107_201400429 AllShare FileShare Service 1.4r476 PEN.UP 1.4.1 Enterprise SysScope Service 4.4.2-N900R4TYECNG5 Camera test 1 PickupTutorial 4.4.2-N900R4TYECNG5 Bloomberg+ 2.0.152 Eraser 1.6.0.214 Downloads 4.4.2-N900R4TYECNG5 RootPA 2.0025 (37085) Documents 4.4.2-N900R4TYECNG5 VpnDialogs 4.4.2-N900R4TYECNG5 Messages 4.4.2-N900R4TYECNG5 Media Storage 4.4.2-N900R4TYECNG5 Nearby devices 2.0.0 Settings 3 MobilePrintSvc_CUPS 1 CloudAgent 1.2.2 SetDefaultLauncher 1 Manage accessibility 1 Setup Wizard 1.3 POLARIS Office 5 5.0.3406.14 Idea Sketch 3 Voice Recorder 2.0.0 SamsungSans 1 Settings 4.4.2-N900R4TYECNG5 SapaMonitor S professional audio monitor 1.0.0 CapabilityManagerService 2.4.0 S Note 3.1.0 Samsung Link 1.8.1904 Samsung WatchON Video 14062601.1.21.78 Street View 1.8.1.2 Alarm 1 PageBuddyNotiSvc 1 Favorite Contacts 4.4.2-N900R4TYECNG5 Google Search 3.4.16.1149292.arm KNOX 2.0.0 Exchange services 4.2 GestureService 1 Weather 140211.01 Samsung Print Service Plugin 1.4.140410 Tasks provider 4.4.2-N900R4TYECNG5 -

Samsung Galaxy A8
SM-A530F SM-A530F/DS SM-A730F SM-A730F/DS User Manual English (LTN). 12/2017. Rev.1.0 www.samsung.com Table of Contents Basics Apps and features 4 Read me first 52 Installing or uninstalling apps 6 Device overheating situations and 54 Bixby solutions 70 Phone 10 Device layout and functions 75 Contacts 14 Battery 79 Messages 17 SIM or USIM card (nano-SIM card) 82 Internet 23 Memory card (microSD card) 84 Email 27 Turning the device on and off 85 Camera 28 Initial setup 100 Gallery 30 Samsung account 106 Always On Display 31 Transferring data from your previous 108 Multi window device 113 Samsung Pay 35 Understanding the screen 117 Samsung Members 47 Notification panel 118 Samsung Notes 49 Entering text 119 Calendar 120 Samsung Health 124 S Voice 126 Voice Recorder 127 My Files 128 Clock 129 Calculator 130 Radio 131 Game Launcher 134 Dual Messenger 135 Samsung Connect 139 Sharing content 140 Google apps 2 Table of Contents Settings 182 Google 182 Accessibility 142 Introduction 183 General management 142 Connections 184 Software update 143 Wi-Fi 185 User manual 146 Bluetooth 185 About phone 148 Data saver 148 NFC and payment 151 Mobile Hotspot and Tethering 152 SIM card manager (dual SIM Appendix models) 186 Troubleshooting 152 More connection settings 155 Sounds and vibration 156 Notifications 157 Display 158 Blue light filter 158 Changing the screen mode or adjusting the display color 160 Screensaver 160 Wallpapers and themes 161 Advanced features 163 Device maintenance 165 Apps 166 Lock screen and security 167 Face recognition 169 Fingerprint recognition 173 Smart Lock 173 Samsung Pass 176 Secure Folder 180 Cloud and accounts 181 Backup and restore 3 Basics Read me first Please read this manual before using the device to ensure safe and proper use. -

Remote Connect 2016
The Convenience of Remote Connect 2016 TOYOTA APP SMARTWATCH GOOGLE AMAZON Remote Connect As a Companion of the Smartphone ASSISTANT ALEXA Toyota Action Toyota Skill Toyota offers an incredible array of convenience and connectivity features. These features now includeGoogle Assistant and Amazon Alexa3 capability – as well as smartwatch integration – for 2018 and later models equipped with Remote Connect². KEY FOB WITH REMOTE FUNCTIONALITY Vehicles equipped with Remote Connect² have key fob13 compatibility for Remote Start1. Connected Services registration will be required to use the complete suite of Remote Connect services, which include Smartphone, Smartwatch, and smart home devices. Audio Plus vehicle key fob functionality is available for up to 3 years. Beyond 3 years requires a subscription. Applicable for select Model Year 2018 through 2020 Remote Connect capable vehicles. Select Model Year 2020 Remote Connect capable vehicles will have functionality for up to 10 years. Premium Audio vehicle key fob functionality is available for up to 10 years. Beyond 10 years requires a subscription. Applicable for select Model Year 2018 through 2020 Remote Connect capable vehicles. Using the key fob to remote start my Toyota: 1. Press the LOCK button on the remote. 2. Press the LOCK button a second time within 1 second. 3. Press the LOCK button again, this time holding it for 3 seconds. The engine will start. Note: Key Fob Remote Start will not function if Connected Services are waived. REMOTE CONNECT EQUIPPED VEHICLES BUILT BEFORE 11/12/18 Remote Connect equipped vehicles built before 11/12/18 were required to have an active Remote Connect trial or paid subscription for the key fob to perform remote start functionality. -

Samsung Galaxy Note 5 N920R6 User Manual
SMART PHONE User Manual Please read this manual before operating your device and keep it for future reference. Legal Notices Warning: This product contains chemicals known to Disclaimer of Warranties; the State of California to cause cancer, birth defects, or other reproductive harm. For more information, Exclusion of Liability please call 1-800-SAMSUNG (726-7864). EXCEPT AS SET FORTH IN THE EXPRESS WARRANTY CONTAINED ON THE WARRANTY PAGE ENCLOSED WITH THE PRODUCT, THE Intellectual Property PURCHASER TAKES THE PRODUCT “AS IS”, AND All Intellectual Property, as defined below, owned SAMSUNG MAKES NO EXPRESS OR IMPLIED by or which is otherwise the property of Samsung WARRANTY OF ANY KIND WHATSOEVER WITH or its respective suppliers relating to the SAMSUNG RESPECT TO THE PRODUCT, INCLUDING BUT Phone, including but not limited to, accessories, NOT LIMITED TO THE MERCHANTABILITY OF THE parts, or software relating there to (the “Phone PRODUCT OR ITS FITNESS FOR ANY PARTICULAR System”), is proprietary to Samsung and protected PURPOSE OR USE; THE DESIGN, CONDITION OR under federal laws, state laws, and international QUALITY OF THE PRODUCT; THE PERFORMANCE treaty provisions. Intellectual Property includes, OF THE PRODUCT; THE WORKMANSHIP OF THE but is not limited to, inventions (patentable or PRODUCT OR THE COMPONENTS CONTAINED unpatentable), patents, trade secrets, copyrights, THEREIN; OR COMPLIANCE OF THE PRODUCT software, computer programs, and related WITH THE REQUIREMENTS OF ANY LAW, RULE, documentation and other works of authorship. You SPECIFICATION OR CONTRACT PERTAINING may not infringe or otherwise violate the rights THERETO. NOTHING CONTAINED IN THE secured by the Intellectual Property. Moreover, INSTRUCTION MANUAL SHALL BE CONSTRUED you agree that you will not (and will not attempt TO CREATE AN EXPRESS OR IMPLIED WARRANTY to) modify, prepare derivative works of, reverse OF ANY KIND WHATSOEVER WITH RESPECT TO engineer, decompile, disassemble, or otherwise THE PRODUCT. -

Digital Forensic Analysis of Smart Watches
TALLINN UNIVERSITY OF TECHNOLOGY School of Information Technologies Kehinde Omotola Adebayo (174449IVSB) DIGITAL FORENSIC ANALYSIS OF SMART WATCHES Bachelor’s Thesis Supervisor: Hayretdin Bahsi Research Professor Tallinn 2020 TALLINNA TEHNIKAÜLIKOOL Infotehnoloogia teaduskond Kehinde Omotola Adebayo (174449IVSB) NUTIKELLADE DIGITAALKRIMINALISTIKA Bachelor’s Thesis Juhendaja: Hayretdin Bahsi Research Professor Tallinn 2020 Author’s declaration of originality I hereby certify that I am the sole author of this thesis. All the used materials, references to the literature and the work of others have been referred to. This thesis has not been presented for examination anywhere else. Author: Kehinde Omotola Adebayo 30.04.2020 3 Abstract As wearable technology is becoming increasingly popular amongst consumers and projected to continue to increase in popularity they become probable significant source of digital evidence. One category of wearable technology is smart watches and they provide capabilities to receive instant messaging, SMS, email notifications, answering of calls, internet browsing, fitness tracking etc. which can be a great source of digital artefacts. The aim of this thesis is to analyze Samsung Gear S3 Frontier and Fitbit Versa Smartwatches, after which we present findings alongside the limitations encountered. Our result shows that we can recover significant artefacts from the Samsung Gear S3 Frontier, also more data can be recovered from Samsung Gear S3 Frontier than the accompanying mobile phone. We recovered significant data that can serve as digital evidence, we also provided a mapping that would enable investigators and forensic examiners work faster as they are shown where to look for information in the course of an investigation. We also presented the result of investigating Fitbit Versa significant artefacts like Heart rate, sleep, exercise and personal data like age, weight and height of the user of the device, this shows this device contains artefacts that might prove useful for forensic investigators and examiners. -

Adattester: Secure Online Mobile Advertisement Attestation Using Trustzone
AdAttester: Secure Online Mobile Advertisement Attestation Using TrustZone Wenhao Li, Haibo Li, Haibo Chen, Yubin Xia Institute of Parallel and Distributed Systems Shanghai Jiao Tong University ABSTRACT 1billiondollarsin2013duetothesefraudsandaroundonethird Mobile advertisement (ad for short) is a major financial pillar for of mobile ad clicks may constitute click-spam [18]. The most re- developers to provide free mobile apps. However, it is frequently cent research study [33] shows that, one of the largest click fraud thwarted by ad fraud, where rogue code tricks ad providers by forg- botnets, called ZeroAccess, induces advertising losses on the or- ing ad display or user clicks, or both. With the mobile ad market der of $100,000 per day. Ad frauds can typically be characterized growing drastically (e.g., from $8.76 billion in 2012 to $17.96 bil- into two types [26]: (1) Bot-driven frauds employ bot networks to lion in 2013), it is vitally important to provide a verifiable mobile initiate forged ad impressions and clicks; (2) Interaction frauds ma- ad framework to detect and prevent ad frauds. Unfortunately,this nipulate visual layouts of ads to trigger ad impressions and unaware is notoriously hard as mobile ads usually run in an execution envi- clicks from the end users. ronment with a huge TCB. Because of the urgent need to detecting mobile ad frauds, prior This paper proposes a verifiable mobile ad framework called approaches have made important first steps by using an offline- AdAttester, based on ARM’s TrustZone technology. AdAttester based approach [16, 26]. Specifically, they trigger the execution provides two novel security primitives, namely unforgeable clicks of mobile apps in a controlled environment to observe deviated and verifiable display.Thetwoprimitivesattestthatad-relatedop- behavior to detect ad frauds. -

AT&T Samsung Galaxy S II
Review: AT&T Samsung Galaxy S II 27 October 2011, By Matthew Fortner This also makes it pleasantly light. Despite having a larger screen and larger dimensions than my iPhone 4S, the Galaxy S II is lighter. Smartphone ergonomics can be subjective, but I felt more confident handling the Samsung. This surprised me since I thought the iPhone's smaller size would give it a handling edge. Users among those who actually make calls will appreciate the good and distortion-free call quality. Those moving from 3G will notice data transfer speeds over AT&T's HSPA+ network to be consistently faster, but not as fast as LTE. There has been a lot of talk about smartphone cameras lately. This new Galaxy S has an 8-megapixel back- illuminated sensor camera aided by a single-LED flash. It can record 1080p video at 30 frames per second. There is also a fixed focus front-facing Android is on fire, and Samsung is stoking the 2-megapixel camera that can also record VGA flames with the Galaxy S II. It's the fastest selling video at 640x480. Android device with 10 million units sold worldwide. Is the Galaxy S II the best current Android phone? There a have been a number of image Maybe. AT&T Wireless sent us theirs to try out. comparisons online. Some give the edge to Samsung, and some to Apple. I found both to be Android fans may have the forthcoming Motorola capable with distinctly different characteristics that Droid RAZR and Samsung Galaxy Nexus in their will appeal to different users.