Benchmarking of Parental Control Tools for the Online Protection of Children
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

A Simple Malware Test Environment
International Journal of Computer and Information Technology (ISSN: 2279 – 0764) Volume 02– Issue 04, July 2013 A Simple Malware Test Environment Sam Lundie and Daniel Rolf School of Computing and Information Systems University of Tasmania Launceston, Tasmania, Australia e-mail: {slundie, Daniel.Rolf} @utas.edu.au Abstract— Malware does not need to compromise the operating not-present fraud increased by 38% for the calendar year system kernel in order to provide an untrustworthy browsing 2010, with 35.6 cents in every $1,000 dollars falling victim experience for the user. This paper describes a simple, virtual to fraud [1]. However, similar figures for fraud perpetrated machine-based, malware test environment built using freeware against Online Banking are much harder to obtain as banks and open source software. The system was designed to allow are seemingly reluctant to divulge loss figures. The the high-level behaviour of a piece of malware to be studied quickly and conveniently by monitoring network, process and Symantec Corporation has claimed that cybercrime has file activity. The system proved effective when trialled against surpassed illegal drug trafficking as a criminal money- different samples of the well-known malware Zeus and was maker [2]. verified further by tests conducted with the commercially available anti-malware products PC-Tools and Trusteer. It has been estimated that Zeus is guilty of approximately Although tests were conducted with variants of the Zeus 44% of all banking malware infections [3]. In August 2009 malware, the techniques discussed in this paper are equally Gunter Ollmann the VP for research at Damaballa [4] applicable to any other malware and can be used to quickly positioned the Zeus malware as the number one botnet assess the effectiveness of potential anti-malware solutions. -

Hostscan 4.8.01064 Antimalware and Firewall Support Charts
HostScan 4.8.01064 Antimalware and Firewall Support Charts 10/1/19 © 2019 Cisco and/or its affiliates. All rights reserved. This document is Cisco public. Page 1 of 76 Contents HostScan Version 4.8.01064 Antimalware and Firewall Support Charts ............................................................................... 3 Antimalware and Firewall Attributes Supported by HostScan .................................................................................................. 3 OPSWAT Version Information ................................................................................................................................................. 5 Cisco AnyConnect HostScan Antimalware Compliance Module v4.3.890.0 for Windows .................................................. 5 Cisco AnyConnect HostScan Firewall Compliance Module v4.3.890.0 for Windows ........................................................ 44 Cisco AnyConnect HostScan Antimalware Compliance Module v4.3.824.0 for macos .................................................... 65 Cisco AnyConnect HostScan Firewall Compliance Module v4.3.824.0 for macOS ........................................................... 71 Cisco AnyConnect HostScan Antimalware Compliance Module v4.3.730.0 for Linux ...................................................... 73 Cisco AnyConnect HostScan Firewall Compliance Module v4.3.730.0 for Linux .............................................................. 76 ©201 9 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public. -

A Glance Into the Eye Pyramid Technical Article V2
A glance into the Eye Pyramid RĂZVAN OLTEANU Security Reasercher We keep you safe and we keep it simple. 01 Introduction On January 11, 2017 Italian news agency AGI, published a court order regarding cyber-attacks against high ranking Italian government members and Italian institutions. The attacks were conducted by two Italian brothers to get financial information that would help them gain an advantage when trading on financial markets. Overview The campaign was carried out over several years starting in 2008 and continuing into 2010, 2011, 2012 and 2014. The mechanism the brothers used to distribute their malware was simple; targeted spear-phishing emails aimed at victims who had already been selected. The emails con- tained a malware attachment, which once opened harvested information from the victims’ computers. This information consisted of pictures, documents, archives, presenta- tions, email contacts, email bodies, usernames, passwords, keystrokes, web pages content and databases. Technical details The malware was written in VisualBasic.net and was obfuscated twice using common obfuscators: Dotfuscator and Skater .NET which can be easily reversed. The malware stored its sensitive data – license keys, URLs and paths – by encrypting with the Triple DES algorithm using the MD5 of a provided password as key and SHA256 of the pass- word as initialization vector. A glance into the Eye Pyramid 01 02 Figure 1 Security applications To remain unnoticed, it tried to disable any security application installed on the victim’s computer. Targeted -
Firewall Software for Windows Xp
Firewall software for windows xp Windows Free Download. Windows 10/8/7, Vista and XP. Block unwanted traffic. Become "ZoneAlarm remains an Editor's Choice for firewall protection. It does. The best protection for Windows XP. Select the antivirus protection that suits you best: ZoneAlarm Pro Antivirus & Firewall for XP, Download >. ZoneAlarm. COMODO offers Free Firewall download for Windows. A multi-layered Live Expert help; Firewall Protection; Antivirus Software 10 / 8 / 7 / Vista / XP SP2. Get award winning free firewall software from Comodo. Download World's #1 Free Firewall that finds threats and protects your PC Supported OS: XP 32bit, Vista/Win7/Win8/Win/Win10 32 bit & 64 bit / MB RAM / MB space. License: Free; OS: Windows XP Windows Vista Windows Windows Windows 10 Firewall Control is a program that has been developed by. Windows 10 Firewall Control is a program that has been developed by License: Free; OS: Windows XP Windows Vista Windows 7 Windows 8. The firewall that Microsoft introduced with the Windows XP SP2 service pack provides a basic level of protection from external attacks: it blocks. AVS Firewall works in Windows 8, 7, Vista, and XP. Note: During setup, AVS Firewall will install their registry cleaner software if you don't deselect it manually. Freeware - Download free Firewall software programs. OS: Windows XP//Vista//7, Linux, MacOS. In: Security/Privacy >. If you are using Windows 7 or Windows 8, you can use the built-in Windows firewall program. Windows XP and Vista firewall was not that great but Microsoft has. Windows has an effective built-in firewall, your home network adds that included firewall protection goes all the way back to Windows XP? Firewall programs to protect your PC. -
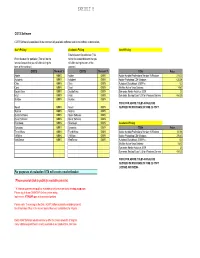
Dell VITA RFP- Revised COTS Pricing 12-17-08
COTS Software COTS Software is considered to be commercially available software read to run without customization, Gov't Pricing Academic Pricing Gov't Pricing Enter discount for publisher (This Enter discount for publisher (This will be the will be the lowest discount that you lowest discount that you will offer during the will offer during the term of the term of the contract) contract) COTS Discount % COTS Discount % Title Price Adobe 0.00% Adobe 0.00% Adobe Acrobat Professional Version 9 Windows 218.33 Autodesk 0.00% Autodesk 0.00% Adobe Photoshop CS4 Windows 635.24 Citrix 0.00% Citrix 0.00% Autodesk Sketchbook 2009 Pro 120 Corel 0.00% Corel 0.00% McAfee Active Virus Defense 14.87 DoubleTake 0.00% DoubleTake 0.00% Symantec Norton Antivirus 2009 25 Intuit 0.00% Intuit 0.00% Symantec Backup Exec 12.5 for Windows Servers 454.25 McAfee 0.00% McAfee 0.00% PRICE FOR ABOVE TITLES SHOULD BE Novell 0.00% Novell 0.00% QUOTED FOR PURCHASE OF ONE (1) COPY Nuance 0.00% Nuance 0.00% Quark Software 0.00% Quark Software 0.00% Quest Software 0.00% Quest Software 0.00% Riverdeep 0.00% Riverdeep 0.00% Academic Pricing Symantec 0.00% Symantec 0.00% Title Price Trend Micro 0.00% Trend Micro 0.00% Adobe Acrobat Professional Version 9 Windows 131.03 VMWare 0.00% VMWare 0.00% Adobe Photoshop CS4 Windows 276.43 WebSense 0.00% WebSense 0.00% Autodesk Sketchbook 2009 Pro 120 McAfee Active Virus Defense 14.87 Symantec Norton Antivirus 2009 25 Symantec Backup Exec 12.5 for Windows Servers 454.25 PRICE FOR ABOVE TITLES SHOULD BE QUOTED FOR PURCHASE OF ONE (1) COPY LICENSE AND MEDIA For purposes of evaluation VITA will create a market basket. -

Ethical Hacking and Countermeasures Version 6
Ethical Hacking and Countermeasures Version 6 Modu le LX Firewall Technologies News Source: http://www.internetnews.com/ Copyright © by EC-Council EC-Council All Rights Reserved. Reproduction is Strictly Prohibited Module Objective This modu le will fam iliar ize you wihith: • Firewalls • Hardware Firewalls • Software Firewalls • Mac OS X Firewall • LINUX Firewall • Windows Firewall Copyright © by EC-Council EC-Council All Rights Reserved. Reproduction is Strictly Prohibited Module Flow Firewalls Mac OS X Firewall Hardware Firewalls LINUX Firewall Software Firewalls Windows Firewall Copyright © by EC-Council EC-Council All Rights Reserved. Reproduction is Strictly Prohibited Firewalls: Introduction A firewall is a program or hardware device that protects the resources of a private netw ork from users of other networks It is responsible for the traffic to be allowed to pass, block, or refuse Firewall also works with the proxy server It helps in the protection of the private network from the users of the different network Copyright © by EC-Council EC-Council All Rights Reserved. Reproduction is Strictly Prohibited Hardware Firewalls Copyright © by EC-Council EC-Council All Rights Reserved. Reproduction is Strictly Prohibited Hardware Firewall Har dware Firewa lls are place d in the perime ter of the networ k It employs a technique of packet filtering It reads the header of a packet to find out the source and destination address The information is then compared with the set of predefined and/orand/ or user created rules that determine whether the packet is forwarded or dropped Copyright © by EC-Council EC-Council All Rights Reserved. Reproduction is Strictly Prohibited Netgear Firewall Features: • ItInterne t shar ing broa dbddband router and 4-port switch • 2x the speed and 4x times the coverage of a Wireless-G router • Configurable for private networks and public hotspots • Double Firewall protection from external hackers attacks • Touchless WiFi Security makes it easy to secure your network Copyright © by EC-Council EC-Council All Rights Reserved. -

Windows Antivirus Support Chart for Hostscan 3.1.06073 Product Name
Windows Antivirus Support Chart for HostScan 3.1.06073 Marketing Product Data File Engine Live Version Check RTP Set RTP Language Alias Name Time Version Update Names 360Safe.co m 360 1.x ✔ ✔ ✔ ✔ ✔ English 360杀毒 Antivirus 360 3.x ✔ ✘ ✔ ✘ ✘ English Antivirus 360 Total 4.x ✔ ✔ ✔ ✘ ✘ English Security Chinese 360 360杀毒 1.x ✔ ✔ ✔ ✘ ✘ Simplified Antivirus Chinese 360 360杀毒 2.x ✔ ✔ ✔ ✘ ✘ Simplified Antivirus Chinese 360杀毒 3.x ✘ ✘ ✔ ✘ ✘ Simplified Chinese 360 360杀毒 4.x ✘ ✘ ✔ ✘ ✘ Simplified Antivirus Chinese 360 360杀毒 5.x ✘ ✘ ✔ ✘ ✘ Simplified Antivirus Other 360Safe.co x ✘ ✘ ✘ ✘ ✘ English m Antivirus AEC, spol. s r.o. TrustPort 2.x ✘ ✘ ✔ ✔ ✘ English Antivirus Other AEC, spol. s r.o. x ✘ ✘ ✘ ✘ ✘ English Antivirus Agnitum Ltd. Outpost Antivirus 7.x ✔ ✔ ✔ ✔ ✘ English Pro Outpost Antivirus 8.x ✔ ✔ ✔ ✔ ✘ English Pro Outpost Antivirus 9.x ✔ ✔ ✔ ✔ ✔ English Pro Outpost Outpost Security Antivirus 6.x ✔ ✔ ✔ ✔ ✘ English Suite Pro Pro 2009 2009 Outpost Security 7.x ✘ ✘ ✔ ✘ ✘ English Suite Free Outpost Security 7.x ✔ ✔ ✔ ✔ ✘ English Suite Pro Outpost Security 8.x ✔ ✔ ✔ ✔ ✔ English Suite Pro Outpost Security 9.x ✔ ✔ ✔ ✔ ✔ English Suite Pro Other Agnitum x ✘ ✘ ✘ ✘ ✘ English Ltd. Antivirus AhnLab, Inc. AhnLab Security 2.x ✔ ✔ ✘ ✔ ✘ English Pack AhnLab V3 Internet 7.x ✔ ✔ ✔ ✔ ✘ English Security 2007 AhnLab V3 Internet Security 7.x ✔ ✔ ✔ ✔ ✘ English 2007 Platinum AhnLab V3 Internet Security 7.x ✔ ✔ ✔ ✔ ✘ English 2008 Platinum AhnLab V3 Internet Security 7.x ✔ ✔ ✔ ✔ ✔ English 2009 Platinum AhnLab V3 Internet Security 7.0 7.x ✔ ✔ ✔ ✔ ✘ English Platinum Enterprise AhnLab V3 Internet 8.x ✔ ✔ ✔ ✔ ✔ English Security 8.0 AhnLab V3 Internet 9.x ✔ ✔ ✔ ✔ ✔ English Security 9.0 AhnLab V3 VirusBlock Internet 7.x ✔ ✔ ✘ ✔ ✘ English Security 2007 AhnLab V3 VirusBlock Internet Security 7.x ✔ ✔ ✔ ✘ ✔ English 2007 Platinum Enterprise V3 Click 1.x ✔ ✘ ✘ ✘ ✘ English V3 Lite 1.x ✔ ✔ ✔ ✔ ✔ Korean V3 Lite 3.x ✔ ✔ ✔ ✘ ✘ Korean V3 VirusBlock 6.x ✔ ✔ ✘ ✘ ✘ English 2005 V3 ウイルスブ NA ✔ ✔ ✘ ✔ ✘ Japanese ロック V3Pro 2004 6.x ✔ ✔ ✔ ✔ ✘ English Other AhnLab, x ✘ ✘ ✘ ✘ ✘ English Inc. -

Cisco Identity Services Engine Release 1.2 Supported Windows
Cisco Identity Services Engine Supported Windows AV/AS Products Compliance Module Version 3.5.6317.2 This document provides Windows 8/7/Vista/XP AV/AS support information on the Cisco NAC Agent version 4.9.0.x and later. For other support information and complete release updates, refer to the Release Notes for Cisco Identity Services Engine corresponding to your Cisco Identity Services Engine release version. Supported Windows AV/AS Product Summary Added New AV Definition Support: COMODO Antivirus 5.x COMODO Internet Security 3.5.x COMODO Internet Security 3.x COMODO Internet Security 4.x Kingsoft Internet Security 2013.x Added New AV Products Support: V3 Click 1.x avast! Internet Security 8.x avast! Premier 8.x avast! Pro Antivirus 8.x Gen-X Total Security 1.x K7UltimateSecurity 13.x Kaspersky Endpoint Security 10.x Kaspersky PURE 13.x Norman Security Suite 10.x Supported Windows AntiVirus Products Product Name Product Version Installation Virus Definition Live Update 360Safe.com 360 Antivirus 1.x 4.9.0.28 / 3.4.21.1 4.9.0.28 / 3.4.21.1 yes 360 Antivirus 3.x 4.9.0.29 / 3.5.5767.2 4.9.0.29 / 3.5.5767.2 - 360杀毒 1.x 4.9.0.28 / 3.4.21.1 4.9.0.28 / 3.4.21.1 - 360杀毒 2.x 4.9.0.29 / 3.4.25.1 4.9.0.29 / 3.4.25.1 - 360杀毒 3.x 4.9.0.29 / 3.5.2101.2 - Other 360Safe.com Antivirus x 4.9.0.29 / 3.5.2101.2 - AEC, spol. -

AV-Comparatives Summary Report 2011 Review Section
Anti‐Virus Comparative – Summary Report 2011 ‐ December 2011 www.av‐comparatives.org Anti-Virus Comparative Summary Report 2011 Awards, winners, comments Language: English December 2011 Last Revision: 22nd December 2011 www.av-comparatives.org ‐ 1 ‐ Anti‐Virus Comparative – Summary Report 2011 ‐ December 2011 www.av‐comparatives.org Table of Contents Introduction 2 Overview of levels reached during 2011 3 Winners 4 Overall winner of 2011 (Product of the Year) 4 Top Rated Products 2011 5 On-Demand Malware Detection winners 6 Proactive On-Demand Detection winners 7 False Positives winners 8 On-Demand Scanning Speed winners 9 Overall Performance (Low-System-Impact) winners 10 Malware Removal winners 11 Whole-Product Dynamic Protection winners 12 Review Section 13 ‐ 2 ‐ Anti‐Virus Comparative – Summary Report 2011 ‐ December 2011 www.av‐comparatives.org Introduction At the end of every year, AV-Comparatives releases a summary report to comment on the various anti- virus products tested over the year, and to mention again the high-scoring products of the various tests. Please bear in mind that this report looks at all the comparative tests of 2011, i.e. not only the latest ones. Comments and conclusions are based on the results shown in the various comparative test reports of AV-Comparatives, as well as from observations made during the tests (http://www.av- comparatives.org/comparativesreviews). Overview of levels reached during 2011 It is important that readers understand that the STANDARD level/award is already a good score, since it requires a program to reach a certain standard of quality. Additionally, all the products tested are security programs from reputable and reliable manufacturers. -

Insight Manufacturers, Publishers and Suppliers by Product Category
Manufacturers, Publishers and Suppliers by Product Category 2/15/2021 10/100 Hubs & Switch ASANTE TECHNOLOGIES CHECKPOINT SYSTEMS, INC. DYNEX PRODUCTS HAWKING TECHNOLOGY MILESTONE SYSTEMS A/S ASUS CIENA EATON HEWLETT PACKARD ENTERPRISE 1VISION SOFTWARE ATEN TECHNOLOGY CISCO PRESS EDGECORE HIKVISION DIGITAL TECHNOLOGY CO. LT 3COM ATLAS SOUND CISCO SYSTEMS EDGEWATER NETWORKS INC Hirschmann 4XEM CORP. ATLONA CITRIX EDIMAX HITACHI AB DISTRIBUTING AUDIOCODES, INC. CLEAR CUBE EKTRON HITACHI DATA SYSTEMS ABLENET INC AUDIOVOX CNET TECHNOLOGY EMTEC HOWARD MEDICAL ACCELL AUTOMAP CODE GREEN NETWORKS ENDACE USA HP ACCELLION AUTOMATION INTEGRATED LLC CODI INC ENET COMPONENTS HP INC ACTI CORPORATION AVAGOTECH TECHNOLOGIES COMMAND COMMUNICATIONS ENET SOLUTIONS INC HYPERCOM ADAPTEC AVAYA COMMUNICATION DEVICES INC. ENGENIUS IBM ADC TELECOMMUNICATIONS AVOCENT‐EMERSON COMNET ENTERASYS NETWORKS IMC NETWORKS ADDERTECHNOLOGY AXIOM MEMORY COMPREHENSIVE CABLE EQUINOX SYSTEMS IMS‐DELL ADDON NETWORKS AXIS COMMUNICATIONS COMPU‐CALL, INC ETHERWAN INFOCUS ADDON STORE AZIO CORPORATION COMPUTER EXCHANGE LTD EVGA.COM INGRAM BOOKS ADESSO B & B ELECTRONICS COMPUTERLINKS EXABLAZE INGRAM MICRO ADTRAN B&H PHOTO‐VIDEO COMTROL EXACQ TECHNOLOGIES INC INNOVATIVE ELECTRONIC DESIGNS ADVANTECH AUTOMATION CORP. BASF CONNECTGEAR EXTREME NETWORKS INOGENI ADVANTECH CO LTD BELDEN CONNECTPRO EXTRON INSIGHT AEROHIVE NETWORKS BELKIN COMPONENTS COOLGEAR F5 NETWORKS INSIGNIA ALCATEL BEMATECH CP TECHNOLOGIES FIRESCOPE INTEL ALCATEL LUCENT BENFEI CRADLEPOINT, INC. FORCE10 NETWORKS, INC INTELIX -

ZANGO, INC V. KASPERSKY LAB, INC. COUNSEL
FOR PUBLICATION UNITED STATES COURT OF APPEALS FOR THE NINTH CIRCUIT ZANGO, INC., No. 07-35800 Plaintiff-Appellant, D.C. No. v. CV-07-00807-JCC KASPERSKY LAB, INC., OPINION Defendant-Appellee. Appeal from the United States District Court for the Western District of Washington John C. Coughenour, District Judge, Presiding Argued and Submitted February 2, 2009—Seattle, Washington Filed June 25, 2009 Before: Betty B. Fletcher, Pamela Ann Rymer and Raymond C. Fisher, Circuit Judges. Opinion by Judge Rymer; Concurrence by Judge Fisher 7973 7976 ZANGO, INC v. KASPERSKY LAB, INC. COUNSEL Michael Rosenberger, Gordon Tilden Thomas & Cordell LLP, Seattle, Washington, for the plaintiff-appellant. Erik Paul Belt, Bromberg & Sunstein LLP, Boston, Massa- chusetts, for the defendant-appellee. OPINION RYMER, Circuit Judge: We must decide whether a distributor of Internet security software is entitled to immunity under the safe harbor provi- sion of the Communications Decency Act of 1996, 47 U.S.C. § 230, from a suit claiming that its software interfered with the use of downloadable programs by customers of an online media company. Zango, Inc. (Zango) is an Internet company that provides access to a catalog of online videos, games, music, tools, and utilities to consumers who agree to view advertisements while they browse the Internet. It brought this action against Kaspersky Lab, Inc., (Kaspersky) which distributes software that helps filter and block potentially malicious software, for improperly blocking Zango’s software. Kaspersky invoked the protection of § 230(c)(2)(B)1 for “good samaritan” block- ing and screening of offensive material. The district court granted summary judgment in Kaspersky’s favor, holding that it is a provider of an “interactive computer service” entitled to immunity for actions taken to make available to others the technical means to restrict access to objectionable material. -

How Do I Get and Install the Safe•Connect Policy Key?
What is Safe•Connect and why is it being used? Safe•Connect is part of TAMUK's effort to help keep computers on its network as free as possible from viruses, spyware, and operating system security holes. Machines protected in this way generally perform much better and require much less downtime due to damage caused by malicious software. Also, the Safe•Connect Policy Key can help to ensure that the average user has the fastest possible browsing experience while connected to the TAMUK network. It does this by ensuring that communication from malicious software does not flood TAMUK’s internet connection, resulting in slower connections for legitimate users or by restricting certain applications that would otherwise consume an unfairly large share of the total available bandwidth, again resulting in a slower connection for the majority of users. Safe•Connect will require users to authenticate with a username and password before allowing them to access the Texas A&M University Kingsville wireless network. When you authenticate, the system records which network address you were assigned and how long you used it. Your username and password are your keys to the network; don't share them with anyone. You are responsible for all acts performed using your account, including copyright violations. If you are concerned that someone may be able to use your account, change your password immediately. What do I need to do? First and foremost, you must know your TAMUK userid (such as “KUABC000”) and password. Your password should be kept secret. Do not write it down and do not share it with anyone.