ZANGO, INC V. KASPERSKY LAB, INC. COUNSEL
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

A Simple Malware Test Environment
International Journal of Computer and Information Technology (ISSN: 2279 – 0764) Volume 02– Issue 04, July 2013 A Simple Malware Test Environment Sam Lundie and Daniel Rolf School of Computing and Information Systems University of Tasmania Launceston, Tasmania, Australia e-mail: {slundie, Daniel.Rolf} @utas.edu.au Abstract— Malware does not need to compromise the operating not-present fraud increased by 38% for the calendar year system kernel in order to provide an untrustworthy browsing 2010, with 35.6 cents in every $1,000 dollars falling victim experience for the user. This paper describes a simple, virtual to fraud [1]. However, similar figures for fraud perpetrated machine-based, malware test environment built using freeware against Online Banking are much harder to obtain as banks and open source software. The system was designed to allow are seemingly reluctant to divulge loss figures. The the high-level behaviour of a piece of malware to be studied quickly and conveniently by monitoring network, process and Symantec Corporation has claimed that cybercrime has file activity. The system proved effective when trialled against surpassed illegal drug trafficking as a criminal money- different samples of the well-known malware Zeus and was maker [2]. verified further by tests conducted with the commercially available anti-malware products PC-Tools and Trusteer. It has been estimated that Zeus is guilty of approximately Although tests were conducted with variants of the Zeus 44% of all banking malware infections [3]. In August 2009 malware, the techniques discussed in this paper are equally Gunter Ollmann the VP for research at Damaballa [4] applicable to any other malware and can be used to quickly positioned the Zeus malware as the number one botnet assess the effectiveness of potential anti-malware solutions. -

Hostscan 4.8.01064 Antimalware and Firewall Support Charts
HostScan 4.8.01064 Antimalware and Firewall Support Charts 10/1/19 © 2019 Cisco and/or its affiliates. All rights reserved. This document is Cisco public. Page 1 of 76 Contents HostScan Version 4.8.01064 Antimalware and Firewall Support Charts ............................................................................... 3 Antimalware and Firewall Attributes Supported by HostScan .................................................................................................. 3 OPSWAT Version Information ................................................................................................................................................. 5 Cisco AnyConnect HostScan Antimalware Compliance Module v4.3.890.0 for Windows .................................................. 5 Cisco AnyConnect HostScan Firewall Compliance Module v4.3.890.0 for Windows ........................................................ 44 Cisco AnyConnect HostScan Antimalware Compliance Module v4.3.824.0 for macos .................................................... 65 Cisco AnyConnect HostScan Firewall Compliance Module v4.3.824.0 for macOS ........................................................... 71 Cisco AnyConnect HostScan Antimalware Compliance Module v4.3.730.0 for Linux ...................................................... 73 Cisco AnyConnect HostScan Firewall Compliance Module v4.3.730.0 for Linux .............................................................. 76 ©201 9 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public. -

A Systematic Empirical Analysis of Unwanted Software Abuse, Prevalence, Distribution, and Economics
UNIVERSIDAD POLITECNICA´ DE MADRID ESCUELA TECNICA´ SUPERIOR DE INGENIEROS INFORMATICOS´ A Systematic Empirical Analysis of Unwanted Software Abuse, Prevalence, Distribution, and Economics PH.D THESIS Platon Pantelis Kotzias Copyright c 2019 by Platon Pantelis Kotzias iv DEPARTAMENTAMENTO DE LENGUAJES Y SISTEMAS INFORMATICOS´ E INGENIERIA DE SOFTWARE ESCUELA TECNICA´ SUPERIOR DE INGENIEROS INFORMATICOS´ A Systematic Empirical Analysis of Unwanted Software Abuse, Prevalence, Distribution, and Economics SUBMITTED IN PARTIAL FULFILLMENT OF THE REQUIREMENTS FOR THE DEGREE OF: Doctor of Philosophy in Software, Systems and Computing Author: Platon Pantelis Kotzias Advisor: Dr. Juan Caballero April 2019 Chair/Presidente: Marc Dasier, Professor and Department Head, EURECOM, France Secretary/Secretario: Dario Fiore, Assistant Research Professor, IMDEA Software Institute, Spain Member/Vocal: Narseo Vallina-Rodriguez, Assistant Research Professor, IMDEA Networks Institute, Spain Member/Vocal: Juan Tapiador, Associate Professor, Universidad Carlos III, Spain Member/Vocal: Igor Santos, Associate Research Professor, Universidad de Deusto, Spain Abstract of the Dissertation Potentially unwanted programs (PUP) are a category of undesirable software that, while not outright malicious, can pose significant risks to users’ security and privacy. There exist indications that PUP prominence has quickly increased over the last years, but the prevalence of PUP on both consumer and enterprise hosts remains unknown. Moreover, many important aspects of PUP such as distribution vectors, code signing abuse, and economics also remain unknown. In this thesis, we empirically and sys- tematically analyze in both breadth and depth PUP abuse, prevalence, distribution, and economics. We make the following four contributions. First, we perform a systematic study on the abuse of Windows Authenticode code signing by PUP and malware. -

Torward: DISCOVERY, BLOCKING, and TRACEBACK of MALICIOUS TRAFFIC OVER Tor 2517
IEEE TRANSACTIONS ON INFORMATION FORENSICS AND SECURITY, VOL. 10, NO. 12, DECEMBER 2015 2515 TorWard: Discovery, Blocking, and Traceback of Malicious Traffic Over Tor Zhen Ling, Junzhou Luo, Member, IEEE,KuiWu,Senior Member, IEEE, Wei Yu, and Xinwen Fu Abstract— Tor is a popular low-latency anonymous communi- I. INTRODUCTION cation system. It is, however, currently abused in various ways. OR IS a popular overlay network that provides Tor exit routers are frequently troubled by administrative and legal complaints. To gain an insight into such abuse, we designed Tanonymous communication over the Internet for and implemented a novel system, TorWard, for the discovery and TCP applications and helps fight against various Internet the systematic study of malicious traffic over Tor. The system censorship [1]. It serves hundreds of thousands of users and can avoid legal and administrative complaints, and allows the carries terabyte of traffic daily. Unfortunately, Tor has been investigation to be performed in a sensitive environment such abused in various ways. Copyrighted materials are shared as a university campus. An intrusion detection system (IDS) is used to discover and classify malicious traffic. We performed through Tor. The black markets (e.g., Silk Road [2], an comprehensive analysis and extensive real-world experiments to online market selling goods such as pornography, narcotics validate the feasibility and the effectiveness of TorWard. Our or weapons1) can be deployed through Tor hidden service. results show that around 10% Tor traffic can trigger IDS alerts. Attackers also run botnet Command and Control (C&C) Malicious traffic includes P2P traffic, malware traffic (e.g., botnet servers and send spam over Tor. -

A Glance Into the Eye Pyramid Technical Article V2
A glance into the Eye Pyramid RĂZVAN OLTEANU Security Reasercher We keep you safe and we keep it simple. 01 Introduction On January 11, 2017 Italian news agency AGI, published a court order regarding cyber-attacks against high ranking Italian government members and Italian institutions. The attacks were conducted by two Italian brothers to get financial information that would help them gain an advantage when trading on financial markets. Overview The campaign was carried out over several years starting in 2008 and continuing into 2010, 2011, 2012 and 2014. The mechanism the brothers used to distribute their malware was simple; targeted spear-phishing emails aimed at victims who had already been selected. The emails con- tained a malware attachment, which once opened harvested information from the victims’ computers. This information consisted of pictures, documents, archives, presenta- tions, email contacts, email bodies, usernames, passwords, keystrokes, web pages content and databases. Technical details The malware was written in VisualBasic.net and was obfuscated twice using common obfuscators: Dotfuscator and Skater .NET which can be easily reversed. The malware stored its sensitive data – license keys, URLs and paths – by encrypting with the Triple DES algorithm using the MD5 of a provided password as key and SHA256 of the pass- word as initialization vector. A glance into the Eye Pyramid 01 02 Figure 1 Security applications To remain unnoticed, it tried to disable any security application installed on the victim’s computer. Targeted -

Spyware and Adware Continue to Present Substantial Harms to Internet Users and to the Internet As a Whole
Testimony of Benjamin Edelman before the United States Senate Committee on Commerce, Science and Transportation June 11, 2008 Benjamin Edelman Baker Library 445 Assistant Professor 1 Soldier’s Field Rd Harvard Business School Boston, MA 02163 Chairman Inouye, Senator Pryor, Members of the Committee: My name is Benjamin Edelman. I am an assistant professor at the Harvard Business School, where my research focuses on the design of electronic marketplaces, including designing online marketplaces to assure safety, reliability, and efficiency. My full biography and publication list are at http://www.benedelman.org/bio and http://www.benedelman.org/publications . Today the committee considers the important problems of Internet spyware and deceptive adware – scourges that threaten the reliability, trustworthiness, and overall utility of many users’ Internet’s access. My bottom line: Despite some recent progress, spyware and adware continue to present substantial harms to Internet users and to the Internet as a whole. Many improper practices are already prohibited under existing statutes including the FTC Act, state consumer protection statutes, and state anti-spyware legislation. These statutes have given rise to a series of cases, both public and private, that have somewhat reined in the problems of spyware and adware. Tough Federal legislation could assist in bringing spyware and adware purveyors to justice, and in further deterring creation and support of this noxious software. But the bill at hand addresses only a portion of the problem, while in some ways reducing the effectiveness of existing efforts. By prohibiting specific individual practices, the bill invites perpetrators to comply with the letter of the law while continuing to harm and deceive consumers. -
Firewall Software for Windows Xp
Firewall software for windows xp Windows Free Download. Windows 10/8/7, Vista and XP. Block unwanted traffic. Become "ZoneAlarm remains an Editor's Choice for firewall protection. It does. The best protection for Windows XP. Select the antivirus protection that suits you best: ZoneAlarm Pro Antivirus & Firewall for XP, Download >. ZoneAlarm. COMODO offers Free Firewall download for Windows. A multi-layered Live Expert help; Firewall Protection; Antivirus Software 10 / 8 / 7 / Vista / XP SP2. Get award winning free firewall software from Comodo. Download World's #1 Free Firewall that finds threats and protects your PC Supported OS: XP 32bit, Vista/Win7/Win8/Win/Win10 32 bit & 64 bit / MB RAM / MB space. License: Free; OS: Windows XP Windows Vista Windows Windows Windows 10 Firewall Control is a program that has been developed by. Windows 10 Firewall Control is a program that has been developed by License: Free; OS: Windows XP Windows Vista Windows 7 Windows 8. The firewall that Microsoft introduced with the Windows XP SP2 service pack provides a basic level of protection from external attacks: it blocks. AVS Firewall works in Windows 8, 7, Vista, and XP. Note: During setup, AVS Firewall will install their registry cleaner software if you don't deselect it manually. Freeware - Download free Firewall software programs. OS: Windows XP//Vista//7, Linux, MacOS. In: Security/Privacy >. If you are using Windows 7 or Windows 8, you can use the built-in Windows firewall program. Windows XP and Vista firewall was not that great but Microsoft has. Windows has an effective built-in firewall, your home network adds that included firewall protection goes all the way back to Windows XP? Firewall programs to protect your PC. -

Benchmarking of Parental Control Tools for the Online Protection of Children
The study aims to benchmark the main functionalities, effectiveness and usability of most currently used filtering software from a technical and ‘fit-for-purpose’ point of view, without any commercial or profit-related concern. The European Union, the European Commission or any person acting on their behalf are not responsible for the accurateness, completeness, use of the information contained in this Study, nor shall they be liable for any loss, including consequential loss, that might derive from such use or from the findings of the Study themselves. The opinions expressed in this study are those of the authors and do not necessarily reflect the views of the European Commission. Although the authors exercised all reasonable efforts to ensure the accuracy and the quality of the contents of this publication, the Consortium assumes no liability for any inadvertent error or omission that may appear in this publication. Product and company names mentioned herein are trademarks or registered trademarks of their respective owners. The readers are hereby advised and notified that they are under obligation to understand and know the same, and ensure due compliance as required. Please acknowledge that in the tables reporting the testing results, tools name may be shorten for ease of reading. The full name, author and version are provided within the TOOL LIST section. Copyrights: the findings of the study, the report and its content and all the complement material is the sole and exclusive property of the European Commission. Main references -

Downloadable Libraries That Need to Be Installed in Order to Enable Complete Functionality in Terms of Placing a Proper 3G-H324M Call Over the ISDN Network
Advances in Networks, Computing and Communications 6 Proceedings of the MSc/MRes Programmes from the School of Computing, Communications and Electronics 2007 - 2008 Editors Dr Paul S Dowland Prof Steven M Furnell School of Computing, Communications & Electronics University of Plymouth ISBN: 978-1-84102-258-1 © 2009 University of Plymouth All rights reserved Printed in the United Kingdom No part of this book may be reproduced, stored in a retrieval system, or transmitted in any form or by any means – electronic, mechanical, photocopy, recording or otherwise, without the prior written permission of the publisher or distributor. Preface This book is the sixth in a series presenting research papers arising from MSc/MRes research projects undertaken by students of the School of Computing, Communications and Electronics at the University of Plymouth. These one year masters courses include a significant period of full-time project activity, and students are assessed on the basis of an MSc or MRes thesis, plus an accompanying research paper. The publications in this volume are based upon research projects that were undertaken during the 2007/08 academic year. A total of 35 papers are presented, covering many aspects of modern networking and communication technology, including security, mobility, coding schemes and quality measurement. The expanded topic coverage compared to earlier volumes in this series reflects the broadening of our range of MSc programmes. Specifically contributing programmes are: Network Systems Engineering, Information Systems Security, Web Technologies and Security, Communications Engineering and Signal Processing, Computer Applications, Computing, Robotics, and Interactive Intelligent Systems The authorship of the papers is credited to the MSc/MRes student in each case (appearing as the first named author), with other authors being the academic supervisors that had significant input into the projects. -
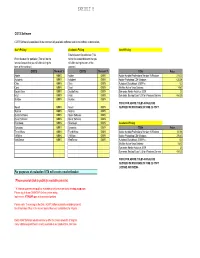
Dell VITA RFP- Revised COTS Pricing 12-17-08
COTS Software COTS Software is considered to be commercially available software read to run without customization, Gov't Pricing Academic Pricing Gov't Pricing Enter discount for publisher (This Enter discount for publisher (This will be the will be the lowest discount that you lowest discount that you will offer during the will offer during the term of the term of the contract) contract) COTS Discount % COTS Discount % Title Price Adobe 0.00% Adobe 0.00% Adobe Acrobat Professional Version 9 Windows 218.33 Autodesk 0.00% Autodesk 0.00% Adobe Photoshop CS4 Windows 635.24 Citrix 0.00% Citrix 0.00% Autodesk Sketchbook 2009 Pro 120 Corel 0.00% Corel 0.00% McAfee Active Virus Defense 14.87 DoubleTake 0.00% DoubleTake 0.00% Symantec Norton Antivirus 2009 25 Intuit 0.00% Intuit 0.00% Symantec Backup Exec 12.5 for Windows Servers 454.25 McAfee 0.00% McAfee 0.00% PRICE FOR ABOVE TITLES SHOULD BE Novell 0.00% Novell 0.00% QUOTED FOR PURCHASE OF ONE (1) COPY Nuance 0.00% Nuance 0.00% Quark Software 0.00% Quark Software 0.00% Quest Software 0.00% Quest Software 0.00% Riverdeep 0.00% Riverdeep 0.00% Academic Pricing Symantec 0.00% Symantec 0.00% Title Price Trend Micro 0.00% Trend Micro 0.00% Adobe Acrobat Professional Version 9 Windows 131.03 VMWare 0.00% VMWare 0.00% Adobe Photoshop CS4 Windows 276.43 WebSense 0.00% WebSense 0.00% Autodesk Sketchbook 2009 Pro 120 McAfee Active Virus Defense 14.87 Symantec Norton Antivirus 2009 25 Symantec Backup Exec 12.5 for Windows Servers 454.25 PRICE FOR ABOVE TITLES SHOULD BE QUOTED FOR PURCHASE OF ONE (1) COPY LICENSE AND MEDIA For purposes of evaluation VITA will create a market basket. -

Ethical Hacking and Countermeasures Version 6
Ethical Hacking and Countermeasures Version 6 Modu le LX Firewall Technologies News Source: http://www.internetnews.com/ Copyright © by EC-Council EC-Council All Rights Reserved. Reproduction is Strictly Prohibited Module Objective This modu le will fam iliar ize you wihith: • Firewalls • Hardware Firewalls • Software Firewalls • Mac OS X Firewall • LINUX Firewall • Windows Firewall Copyright © by EC-Council EC-Council All Rights Reserved. Reproduction is Strictly Prohibited Module Flow Firewalls Mac OS X Firewall Hardware Firewalls LINUX Firewall Software Firewalls Windows Firewall Copyright © by EC-Council EC-Council All Rights Reserved. Reproduction is Strictly Prohibited Firewalls: Introduction A firewall is a program or hardware device that protects the resources of a private netw ork from users of other networks It is responsible for the traffic to be allowed to pass, block, or refuse Firewall also works with the proxy server It helps in the protection of the private network from the users of the different network Copyright © by EC-Council EC-Council All Rights Reserved. Reproduction is Strictly Prohibited Hardware Firewalls Copyright © by EC-Council EC-Council All Rights Reserved. Reproduction is Strictly Prohibited Hardware Firewall Har dware Firewa lls are place d in the perime ter of the networ k It employs a technique of packet filtering It reads the header of a packet to find out the source and destination address The information is then compared with the set of predefined and/orand/ or user created rules that determine whether the packet is forwarded or dropped Copyright © by EC-Council EC-Council All Rights Reserved. Reproduction is Strictly Prohibited Netgear Firewall Features: • ItInterne t shar ing broa dbddband router and 4-port switch • 2x the speed and 4x times the coverage of a Wireless-G router • Configurable for private networks and public hotspots • Double Firewall protection from external hackers attacks • Touchless WiFi Security makes it easy to secure your network Copyright © by EC-Council EC-Council All Rights Reserved. -

Windows Antivirus Support Chart for Hostscan 3.1.06073 Product Name
Windows Antivirus Support Chart for HostScan 3.1.06073 Marketing Product Data File Engine Live Version Check RTP Set RTP Language Alias Name Time Version Update Names 360Safe.co m 360 1.x ✔ ✔ ✔ ✔ ✔ English 360杀毒 Antivirus 360 3.x ✔ ✘ ✔ ✘ ✘ English Antivirus 360 Total 4.x ✔ ✔ ✔ ✘ ✘ English Security Chinese 360 360杀毒 1.x ✔ ✔ ✔ ✘ ✘ Simplified Antivirus Chinese 360 360杀毒 2.x ✔ ✔ ✔ ✘ ✘ Simplified Antivirus Chinese 360杀毒 3.x ✘ ✘ ✔ ✘ ✘ Simplified Chinese 360 360杀毒 4.x ✘ ✘ ✔ ✘ ✘ Simplified Antivirus Chinese 360 360杀毒 5.x ✘ ✘ ✔ ✘ ✘ Simplified Antivirus Other 360Safe.co x ✘ ✘ ✘ ✘ ✘ English m Antivirus AEC, spol. s r.o. TrustPort 2.x ✘ ✘ ✔ ✔ ✘ English Antivirus Other AEC, spol. s r.o. x ✘ ✘ ✘ ✘ ✘ English Antivirus Agnitum Ltd. Outpost Antivirus 7.x ✔ ✔ ✔ ✔ ✘ English Pro Outpost Antivirus 8.x ✔ ✔ ✔ ✔ ✘ English Pro Outpost Antivirus 9.x ✔ ✔ ✔ ✔ ✔ English Pro Outpost Outpost Security Antivirus 6.x ✔ ✔ ✔ ✔ ✘ English Suite Pro Pro 2009 2009 Outpost Security 7.x ✘ ✘ ✔ ✘ ✘ English Suite Free Outpost Security 7.x ✔ ✔ ✔ ✔ ✘ English Suite Pro Outpost Security 8.x ✔ ✔ ✔ ✔ ✔ English Suite Pro Outpost Security 9.x ✔ ✔ ✔ ✔ ✔ English Suite Pro Other Agnitum x ✘ ✘ ✘ ✘ ✘ English Ltd. Antivirus AhnLab, Inc. AhnLab Security 2.x ✔ ✔ ✘ ✔ ✘ English Pack AhnLab V3 Internet 7.x ✔ ✔ ✔ ✔ ✘ English Security 2007 AhnLab V3 Internet Security 7.x ✔ ✔ ✔ ✔ ✘ English 2007 Platinum AhnLab V3 Internet Security 7.x ✔ ✔ ✔ ✔ ✘ English 2008 Platinum AhnLab V3 Internet Security 7.x ✔ ✔ ✔ ✔ ✔ English 2009 Platinum AhnLab V3 Internet Security 7.0 7.x ✔ ✔ ✔ ✔ ✘ English Platinum Enterprise AhnLab V3 Internet 8.x ✔ ✔ ✔ ✔ ✔ English Security 8.0 AhnLab V3 Internet 9.x ✔ ✔ ✔ ✔ ✔ English Security 9.0 AhnLab V3 VirusBlock Internet 7.x ✔ ✔ ✘ ✔ ✘ English Security 2007 AhnLab V3 VirusBlock Internet Security 7.x ✔ ✔ ✔ ✘ ✔ English 2007 Platinum Enterprise V3 Click 1.x ✔ ✘ ✘ ✘ ✘ English V3 Lite 1.x ✔ ✔ ✔ ✔ ✔ Korean V3 Lite 3.x ✔ ✔ ✔ ✘ ✘ Korean V3 VirusBlock 6.x ✔ ✔ ✘ ✘ ✘ English 2005 V3 ウイルスブ NA ✔ ✔ ✘ ✔ ✘ Japanese ロック V3Pro 2004 6.x ✔ ✔ ✔ ✔ ✘ English Other AhnLab, x ✘ ✘ ✘ ✘ ✘ English Inc.