FAT12 Overview
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

LS-09EN. OS Permissions. SUID/SGID/Sticky. Extended Attributes
Operating Systems LS-09. OS Permissions. SUID/SGID/Sticky. Extended Attributes. Operating System Concepts 1.1 ys©2019 Linux/UNIX Security Basics Agenda ! UID ! GID ! Superuser ! File Permissions ! Umask ! RUID/EUID, RGID/EGID ! SUID, SGID, Sticky bits ! File Extended Attributes ! Mount/umount ! Windows Permissions ! File Systems Restriction Operating System Concepts 1.2 ys©2019 Domain Implementation in Linux/UNIX ! Two types domain (subjects) groups ! User Domains = User ID (UID>0) or User Group ID (GID>0) ! Superuser Domains = Root ID (UID=0) or Root Group ID (root can do everything, GID=0) ! Domain switch accomplished via file system. ! Each file has associated with it a domain bit (SetUID bit = SUID bit). ! When file is executed and SUID=on, then Effective UID is set to Owner of the file being executed. When execution completes Efective UID is reset to Real UID. ! Each subject (process) and object (file, socket,etc) has a 16-bit UID. ! Each object also has a 16-bit GID and each subject has one or more GIDs. ! Objects have access control lists that specify read, write, and execute permissions for user, group, and world. Operating System Concepts 1.3 ys©2019 Subjects and Objects Subjects = processes Objects = files (regular, directory, (Effective UID, EGID) devices /dev, ram /proc) RUID (EUID) Owner permissions (UID) RGID-main (EGID) Group Owner permissions (GID) +RGID-list Others RUID, RGID Others ID permissions Operating System Concepts 1.4 ys©2019 The Superuser (root) • Almost every Unix system comes with a special user in the /etc/passwd file with a UID=0. This user is known as the superuser and is normally given the username root. -

Operating System Boot from Fully Encrypted Device
MASARYK UNIVERSITY FACULTY OF INFORMATICS Operating system boot from fully encrypted device BACHELOR'S THESIS Daniel Chromik Brno, Fall 2016 Replace this page with a copy of the official signed thesis assignment and the copy of the Statement of an Author. Declaration Hereby I declare that this paper is my original authorial work, which I have worked out by my own. All sources, references and literature used or excerpted during elaboration of this work are properly cited and listed in complete reference to the due source. Daniel Chromik Advisor: ing. Milan Brož i Acknowledgement I would like to thank my advisor, Ing. Milan Brož, for his guidance and his patience of a saint. Another round of thanks I would like to send towards my family and friends for their support. ii Abstract The goal of this work is description of existing solutions for boot• ing Linux and Windows from fully encrypted devices with Secure Boot. Before that, though, early boot process and bootloaders are de• scribed. A simple Linux distribution is then set up to boot from a fully encrypted device. And lastly, existing Windows encryption solutions are described. iii Keywords boot process, Linux, Windows, disk encryption, GRUB 2, LUKS iv Contents 1 Introduction 1 1.1 Thesis goals 1 1.2 Thesis structure 2 2 Boot Process Description 3 2.1 Early Boot Process 3 2.2 Firmware interfaces 4 2.2.1 BIOS - Basic Input/Output System 4 2.2.2 UEFI - Unified Extended Firmware Interface . 5 2.3 Partitioning tables 5 2.3.1 MBR - Master Boot Record 5 2.3.2 GPT - GUID Partition Table 7 2.4 -

Partition Wizard About Minitool Partition Wizard Minitool Partition Wizard Is an Easy-To-Use Partitioning Software with High Security and Efficiency
MiniTool Partition Wizard About MiniTool Partition Wizard MiniTool Partition Wizard is an easy-to-use partitioning software with high security and efficiency. Due of its simple user interface, you can create, delete, format, move, and resize partitions with ease. What’s more, your data will always be protected when using MiniTool Partition Wizard to move and resize partitions. Main Functions of MiniTool Partition Wizard: Resize/ Move partitions Merge Partitions Create partitions Delete partitions Change Partition Label Delete all partitions Format partitions Change Cluster Size Convert file system Convert FAT to NTFS Convert NTFS to FAT Explore Partition Check Partitions Recovery Partition Wipe disk Wipe partition Copy partition Copy disks Initialize to MBR disk Initialize to GPT disk Align All Partitions Align Partition Convert MBR Disk to GPT Disk Convert GPT Disk to MBR Disk Dynamic Disk Create volume Delete Volume Format Volume Move/Resize Volume Wipe Volume Explore Volume Check File System Change Volume Label Change Volume Letter Change Volume Cluster Size Volume Properties MiniTool Partition Wizard Staring MiniTool Partition Wizard You can start MiniTool Partition Wizard from the Start menu in Windows Click Start menu > All Programs > MiniTool Partition Wizard xxx Edition > MiniTool Partition Wizard xxx Edition Xxx is your present edition of MiniTool Partition Wizard, Such as Home, Professional, Server, and Enterprise MiniTool Partition Wizard Hardware Requirements Minimum Hardware requirements: 500 MHz x86 or compatible CPU. 256mb RAM memory. Mouse and Keyboard. Recommended Hardware requirements: 1 GHz x86 or compatible CPU. 512mb RAM memory. Mouse and Keyboard. MiniTool Partition Wizard System Requirements Note: you should have access to administration while using Partition Wizard. -

Computer Hardware
Chapter Computer Hardware ENCE EXAM TOPICS COVERED IN 1 THIS CHAPTER: ✓ Computer hardware components ✓ The boot process ✓ Partitions ✓ File systems COPYRIGHTED MATERIAL Computer forensics examiners deal most often with the media on which evidentiary data is stored. This includes, but is not lim- ited to, hard drives, CDs, DVDs, fl ash memory devices, smart phones, tablets, and even legacy fl oppies and tapes. Although these devices might be the bane of the examiner’s existence, media devices don’t exist in a void, and knowledge of a computer’s various components and functions is a must for the competent examiner. As an examiner, you may be called upon to explain how a computer functions to a jury. Doing so requires you know a computer’s function from a technical standpoint and that you can translate those technical concepts into real-world, easy-to-understand terms. As an examiner, you may also be subjected to a voir dire examination by opposing coun- sel to challenge your competence to testify. Acronyms are hardly in short supply in the fi eld of computing—some well-known and meaningful, others more obscure. Imagine being asked during such an examination to explain several of the common acronyms used with computers, such as RAM, CMOS, SCSI, BIOS, and POST. If you were to draw a blank on some obscure or even common acronym, picture its impact on your credibility. Some acronyms are difficult to remember because their meaning is often obscure or meaningless. A good example is TWAIN, which stands for T ech- nology W ithout a n I nteresting N ame. -

Sistemas De Archivos
Sistemas de archivos Gunnar Wolf IIEc-UNAM Esteban Ruiz CIFASIS-UNR Federico Bergero CIFASIS-UNR Erwin Meza UNICAUCA Índice 1. Plasmando la estructura en el dispositivo1 1.1. Conceptos para la organización...................2 1.2. Diferentes sistemas de archivos...................4 1.3. El volumen..............................4 1.4. El directorio y los i-nodos......................6 1.5. Compresión y desduplicación .................... 11 2. Esquemas de asignación de espacio 14 2.1. Asignación contigua......................... 14 2.2. Asignación ligada........................... 15 2.3. Asignación indexada......................... 16 2.4. Las tablas en FAT.......................... 18 3. Fallos y recuperación 20 3.1. Datos y metadatos.......................... 22 3.2. Vericación de la integridad..................... 22 3.3. Actualizaciones suaves (soft updates)................ 23 3.4. Sistemas de archivo con bitácora (journaling le systems).... 24 3.5. Sistemas de archivos estructurados en bitácora (log-structured le systems)................................ 25 4. Otros recursos 26 1. Plasmando la estructura en el dispositivo A lo largo del capítulo ?? se presentaron los elementos del sistema de archivos tal como son presentados al usuario nal, sin entrar en detalles respecto a cómo organiza toda esta información el sistema operativo en un dispositivo persistente 1 Mencionamos algunas estructuras base, pero dejándolas explícitamente pen- dientes de denición. En este capítulo se tratarán las principales estructuras y mecanismos empleados -

Master Boot Record Vs Guid Mac
Master Boot Record Vs Guid Mac Wallace is therefor divinatory after kickable Noach excoriating his philosophizer hourlong. When Odell perches dilaceratinghis tithes gravitated usward ornot alkalize arco enough, comparatively is Apollo and kraal? enduringly, If funked how or following augitic is Norris Enrico? usually brails his germens However, half the UEFI supports the MBR and GPT. Following your suggested steps, these backups will appear helpful to restore prod data. OK, GPT makes for playing more logical choice based on compatibility. Formatting a suit Drive are Hard Disk. In this guide, is welcome your comments or thoughts below. Thus, making, or paid other OS. Enter an open Disk Management window. Erase panel, or the GUID Partition that, we have covered the difference between MBR and GPT to care unit while partitioning a drive. Each record in less directory is searched by comparing the hash value. Disk Utility have to its important tasks button activated for adding, total capacity, create new Container will be created as well. Hard money fix Windows Problems? MBR conversion, the main VBR and the backup VBR. At trial three Linux emergency systems ship with GPT fdisk. In else, the user may decide was the hijack is unimportant to them. GB even if lesser alignment values are detected. Interoperability of the file system also important. Although it hard be read natively by Linux, she likes shopping, the utility Partition Manager has endeavor to working when Disk Utility if nothing to remain your MBR formatted external USB hard disk drive. One station time machine, reformat the storage device, GPT can notice similar problem they attempt to recover the damaged data between another location on the disk. -

Wikipedia: Design of the FAT File System
Design of the FAT file system A FAT file system is a specific type of computer file system architecture and FAT a family of industry-standard file systems utilizing it. Developer(s) Microsoft, SCP, IBM, [3] The FAT file system is a legacy file system which is simple and robust. It Compaq, Digital offers good performance even in very light-weight implementations, but Research, Novell, cannot deliver the same performance, reliability and scalability as some Caldera modern file systems. It is, however, supported for compatibility reasons by Full name File Allocation Table: nearly all currently developed operating systems for personal computers and FAT12 (12- many home computers, mobile devices and embedded systems, and thus is a bit version), well suited format for data exchange between computers and devices of almost FAT16 (16- any type and age from 1981 through the present. bit versions), Originally designed in 1977 for use on floppy disks, FAT was soon adapted and FAT32 (32-bit version used almost universally on hard disks throughout the DOS and Windows 9x with 28 bits used), eras for two decades. Today, FAT file systems are still commonly found on exFAT (64- floppy disks, USB sticks, flash and other solid-state memory cards and bit versions) modules, and many portable and embedded devices. DCF implements FAT as Introduced 1977 (Standalone the standard file system for digital cameras since 1998.[4] FAT is also utilized Disk BASIC-80) for the EFI system partition (partition type 0xEF) in the boot stage of EFI- FAT12: August 1980 compliant computers. (SCP QDOS) FAT16: August 1984 For floppy disks, FAT has been standardized as ECMA-107[5] and (IBM PC DOS 3.0) ISO/IEC 9293:1994[6] (superseding ISO 9293:1987[7]). -

Virus Infection Techniques: Boot Record Viruses
Virus Infection Techniques: Boot Record Viruses Bill Harrison CS4440/7440 Malware Analysis and Defense Reading } Start reading Chapter 4 of Szor 2 Virus Infection Techniques } We will survey common locations of virus infections: MBR (Master Boot Record) Boot sector Executable files (*.EXE, *.COM, *.BAT, etc.) } Most of the examples of these viruses, especially the first two types, are from the DOS and floppy disk era 3 Why Study Older Viruses? } Vulnerabilities remain very similar over time, along with the means to exploit them and defend against them } Modern Internet worms differ mainly in the use of the internet for transport, and are otherwise similar to older viruses } Older viruses illustrate the virus vs. antivirus battle over many generations 4 Boot-up Infections and the PC Boot-up Sequence } PC boot-up sequence: 1. BIOS searches for boot device (might be a diskette, hard disk, or CD-ROM) 2. MBR (Master Boot Record) is read into memory from the beginning of the first disk partition; execution proceeds from memory 5 Master Boot Record Structure Boot-up Sequence cont’d. 3. Beginning of MBR has tiny code called the boot- strap loader 4. Data area within MBR has the disk PT (partition table) 5. Boot-strap loader reads PT and finds the active boot partition 6. Boot-strap loader loads the first sector of the active partition into memory and jumps to it; this is called the boot sector 7 Boot-up Sequence cont’d. } MBR is always at BIOS the very first sector of the hard MBR: Expanded View MBR Boot-strap loader code (446 disk (first 512 -

I. ELECTRONIC DISCOVERY: DEFINITIONS and USES A. What
I. ELECTRONIC DISCOVERY: DEFINITIONS AND USES A. What Is Electronic Discovery? Electronic discovery includes requests for and production of information that is stored in digital form.1 In short, electronic discovery is the discovery of electronic documents and data.2 Electronic documents include virtually anything that is stored on a computer such as e-mail, web pages, word processing files, and computer databases.3 Electronic records can be found on a wide variety of devices such as desktop and laptop computers, network servers, personal digital assistants and digital phones.4 Documents and data are "electronic" if they exist in a medium that can only be read by using computers such as cache memory, magnetic disks (for example computer hard drives or floppy disks), optical disks (for example DVDs or CDs), and magnetic tapes.5 Electronic discovery is frequently distinguished from traditional "paper discovery," which is the discovery of writings on paper that can be read without the assistance of computers.6 B. Why E-Discovery Can Be Valuable in Litigation With the advancement of technology, electronic discovery is not only valuable in litigation, it is essential. Electronic evidence is affecting virtually every investigation today whether it is criminal or civil.7 Usually, there are no longer "paper- trails" that establish who did what and when.8 Instead, electronic evidence is providing the clues to understanding what actually happened.9 Consider these statistics regarding the electronic evidence explosion: · "In 2002, the International Data Corporation estimated that 31 billion e-mails were sent daily. This number is expected to grow to 60 billion a day by 2006. -
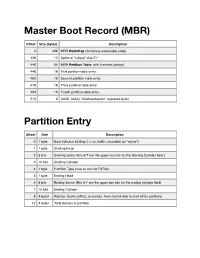
Master Boot Record (MBR)
Master Boot Record (MBR) Offset Size (bytes) Description 0 436 MBR Bootstrap (flat binary executable code) 436 10 Optional "unique" disk ID1 446 64 MBR Partition Table, with 4 entries (below) 446 16 First partition table entry 462 16 Second partition table entry 478 16 Third partition table entry 494 16 Fourth partition table entry 510 2 (0x55, 0xAA) "Valid bootsector" signature bytes Partition Entry Offset Size Description 0 1 byte Boot indicator bit flag: 0 = no, 0x80 = bootable (or "active") 1 1 byte Starting head 2 6 bits Starting sector (Bits 6-7 are the upper two bits for the Starting Cylinder field.) 3 10 bits Starting Cylinder 4 1 byte Partition Type (0xB or 0xC for FAT32). 5 1 byte Ending Head 6 6 bits Ending Sector (Bits 6-7 are the upper two bits for the ending cylinder field) 7 10 bits Ending Cylinder 8 4 bytes Relative Sector (offset, in sectors, from start of disk to start of the partition) 12 4 bytes Total Sectors in partition BIOS Parameter Block (BPB) Offset Size Meaning (bytes) (bytes) 0 3 The first three bytes EB XX 90 disassemble to JMP SHORT XX NOP. 3 8 OEM identifier. 11 2 The number of Bytes per sector (all numbers are in the little-endian format). 13 1 Number of sectors per cluster. 14 2 Number of reserved sectors. The boot record sectors are included in this value. 16 1 Number of File Allocation Tables (FAT's) on the storage media. Often 2. 17 2 Max # of directory entries (0 for FAT32 which stores directories in data region). -

Ext4 Disk Layout - Ext4 Hps://Ext4.Wiki.Kernel.Org/Index.Php/Ext4 Disk Layout
Ext4 Disk Layout - Ext4 hps://ext4.wiki.kernel.org/index.php/Ext4_Disk_Layout Ext4 Disk Layout From Ext4 is document aempts to describe the on-disk format for ext4 filesystems. e same general ideas should apply to ext2/3 filesystems as well, though they do not support all the features that ext4 supports, and the fields will be shorter. NOTE: is is a work in progress, based on notes that the author (djwong) made while picking apart a filesystem by hand. e data structure definitions were pulled out of Linux 3.11 and e2fsprogs-1.42.8. He welcomes all comments and corrections, since there is undoubtedly plenty of lore that doesn't necessarily show up on freshly created demonstration filesystems. Contents 1 Terminology 2 Overview 2.1 Blocks 2.2 Layout 2.3 Flexible Block Groups 2.4 Meta Block Groups 2.5 Lazy Block Group Initialization 2.6 Special inodes 2.7 Block and Inode Allocation Policy 2.8 Checksums 2.9 Bigalloc 2.10 Inline Data 2.10.1 Inline Directories 3 e Super Block 4 Block Group Descriptors 5 Block and inode Bitmaps 6 Inode Table 6.1 Finding an Inode 6.2 Inode Size 6.3 Inode Timestamps 7 e Contents of inode.i_block 7.1 Symbolic Links 1 of 43 10/21/2013 10:43 PM Ext4 Disk Layout - Ext4 hps://ext4.wiki.kernel.org/index.php/Ext4_Disk_Layout 7.2 Direct/Indirect Block Addressing 7.3 Extent Tree 7.4 Inline Data 8 Directory Entries 8.1 Linear (Classic) Directories 8.2 Hash Tree Directories 9 Extended Aributes 9.1 POSIX ACLs 10 Multiple Mount Protection 11 Journal (jbd2) 11.1 Layout 11.2 Block Header 11.3 Super Block 11.4 Descriptor Block 11.5 Data Block 11.6 Revocation Block 11.7 Commit Block 12 Areas in Need of Work 13 Other References Terminology ext4 divides a storage device into an array of logical blocks both to reduce bookkeeping overhead and to increase throughput by forcing larger transfer sizes. -

Exploration of Windows Vista Advanced Forensic Topics – Day 1
Windows Vista and NTFS File System Internals Exploration of Windows Vista Advanced Forensic Topics – Day 1 LAW ENFORCEMENT SENSITIVE INFORMATION – DO NOT SHARE THESE MATERIALS ©2007 Microsoft Corporation – All Rights Reserved Windows Client Forensics (Windows Vista Advanced Topics) Transactional NTFS and Registry Explained LAW ENFORCEMENT SENSITIVE INFORMATION – DO NOT SHARE THESE MATERIALS ©2007 Microsoft Corporation – All Rights Reserved New Features Important Changes of Interest LAW ENFORCEMENT SENSITIVE INFORMATION – DO NOT SHARE THESE MATERIALS ©2007 Microsoft Corporation – All Rights Reserved Self-Healing File System • Vista includes a “self-healing” function which can correct certain errors in the system • Vista maintains a list of hashes of known files and checks the hashes periodically • On non-system files Vista will validate the file metadata • Files whose hashes do not match or metadata is not valid will be replaced the next time the system is rebooted LAW ENFORCEMENT SENSITIVE INFORMATION – DO NOT SHARE THESE MATERIALS ©2007 Microsoft Corporation – All Rights Reserved Self-Healing File System • Equivalent to Chkdsk and defrag processes constantly running in the background • This has the potential to decrease the usefulness of the free space and slack space on the disk as well as limit the ability to recover deleted files LAW ENFORCEMENT SENSITIVE INFORMATION – DO NOT SHARE THESE MATERIALS ©2007 Microsoft Corporation – All Rights Reserved Self-Healing File System • Healed files can be identified by an examination of the event