Packet Sniffer – a Comparative Characteristic Evaluation Study
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

A Decryption Process for Android Database Forensics
International Journal of Computer Sciences and Engineering Open Access Research Paper Vol.-7, Issue-3, March 2019 E-ISSN: 2347-2693 A Decryption Process for Android Database Forensics Nibedita Chakraborty1*, Krishna Punwar2 1,2Dept. of Information Technology and Telecommunication, Raksha Shakti University, Ahmedabad, India *Corresponding Author: [email protected], Tel.: 7980118774 DOI: https://doi.org/10.26438/ijcse/v7i3.2326 | Available online at: www.ijcseonline.org Accepted: 18/Mar/2019, Published: 31/Mar/2019 Abstract— Nowadays, Databases are mostly usable in business applications and financial transactions in Banks. Most of the database servers stores confidential and sensitive information of a mobile device. Database forensics is the part of digital forensics especially for the investigation of different databases and the sensitive information stored on a database. Mobile databases are totally different from the major database and are very platform independent as well. Even if they are not attached to the central database, they can still linked with the major database to drag and change the information stored on this. SQLite Database is mostly needed by Android application development. SQLite is a freely available database management system which is specially used to perform relational functional and it comes inbuilt with android to perform database functions on android appliance. This paper will show how a message can be decrypted by using block cipher modes and which mode is more secured and fast. Keywords—Database Forensics,Mobile Device ,Android,SQLite, Modes, Tools I. INTRODUCTION In android mobile phone device, SQLite is mainly based on ACID properties docile relational database management Database is an assemble form of interrelated data which is system. -

Implementing Cisco Cyber Security Operations
2019 CLUS Implementing Cisco Cyber Security Operations Paul Ostrowski / Patrick Lao / James Risler Cisco Security Content Development Engineers LTRCRT-2222 2019 CLUS Cisco Webex Teams Questions? Use Cisco Webex Teams to chat with the speaker after the session How 1 Find this session in the Cisco Live Mobile App 2 Click “Join the Discussion” 3 Install Webex Teams or go directly to the team space 4 Enter messages/questions in the team space Webex Teams will be moderated cs.co/ciscolivebot#LTRCRT-2222 by the speaker until June 16, 2019. 2019 CLUS © 2019 Cisco and/or its affiliates. All rights reserved. Cisco Public 3 Agenda • Goals and Objectives • Prerequisite Knowledge & Skills (PKS) • Introduction to Security Onion • SECOPS Labs and Topologies • Access SECFND / SECOPS eLearning Lab Training Environment • Lab Evaluation • Cisco Cybersecurity Certification and Education Offerings 2019 CLUS LTRCRT-2222 © 2019 Cisco and/or its affiliates. All rights reserved. Cisco Public 4 Goals and Objectives: • Today's organizations are challenged with rapidly detecting cybersecurity breaches in order to effectively respond to security incidents. Cybersecurity provides the critical foundation organizations require to protect themselves, enable trust, move faster, add greater value and grow. • Teams of cybersecurity analysts within Security Operations Centers (SOC) keep a vigilant eye on network security monitoring systems designed to protect their organizations by detecting and responding to cybersecurity threats. • The goal of Cisco’s CCNA Cyber OPS (SECFND / SECOPS) courses is to teach the fundamental skills required to begin a career working as an associate/entry-level cybersecurity analyst within a threat centric security operations center. • This session will provide the student with an understanding of Security Onion as an open source network security monitoring tool (NSM). -

Virtualization of the RIOT Operating System
Computer Systems and Telematics — Distributed, Embedded Systems Diploma Thesis Virtualization of the RIOT Operating System Ludwig Ortmann Matr. 3914103 Supervisor: Dr. Emmanuel Baccelli Assisting Supervisor: Prof. Dr.-Ing. Jochen Schiller Institute of Computer Science, Freie Universität Berlin, Germany March 2, 2015 iii I hereby declare to have written this thesis on my own. I have used no other literature and resources than the ones referenced. All text passages that are literal or logical copies from other publications have been marked accordingly. All figures and pictures have been created by me or their sources are referenced accordingly. This thesis has not been submitted in the same or a similar version to any other examination board. Berlin, March 2, 2015 (Ludwig Ortmann) Abstract Abstract Software developers in the growing field of the Internet of Things face many hurdles which arise from the limitations of embedded systems and wireless networking. The employment of hardware and network virtualization promises to allow developers to test and debug hard- ware independent code without being affected by these limitations. This thesis presents RIOT native, a hardware and network emulation implementation for the RIOT operating system, which enables developers to compile and run RIOT as a process in their host operat- ing system. Running the operating system as a process allows for the use of debugging tools and techniques only available on desktop computers otherwise, the integration of common network analysis tools, and the emulation of arbitrary network topologies. By enabling the use of these tools and techniques for the development of software for distributed embedded systems, the hurdles they impose on the development process are significantly reduced. -

TCPDUMP Caution
TCPDUMP q Refer to book ”Open Source Network Administration” m Online sample chapter: http://www.phptr.com/articles/article.asp?p=170902&seqNum=4 q Some tools are not based directly on the data being transmitted on a network, but information related to that data. m For example, network bandwidth values m System logs on network equipment q Sometimes needs to examine the packets themselves. m Diagnose some particularly tricky network problems q Widely used open source tool for directly analyzing packets: tcpdump m http://www.tcpdump.org/ Network Analyzer 1-1 Caution q Before you use tcpdump or other analyzer: m Will be able to see some private data m Consult/research Legal implication first m Respect the privacy of other users Network Analyzer 1-2 1 What Tcpdump can do for you q View the entire data portion of an Ethernet frame or other link layer protocol m An IP packet m An ARP packet m Or any protocol at a higher layer than Ethernet. q Very useful m Tcpdump is to a network administrator like a microscope to a biologist. m Give a very clear picture of a specific part of your network m Can be used when the problem is simply that something is not working properly. Network Analyzer 1-3 What tcpdump can do for you? q Case1 : Web browser can not load pages from a server – it hangs. m Problem with client? Server? Or between? m Run tcpdump while loading • Watch every stage to see the following – DNS query – HTTP request to server – Server respond q Case 2: help debug denial of service attacks. -

Hands-On Network Forensics, FIRST 2015
2015-04-30 WWW.FORSVARSMAKTEN.SE Hands-on Network Forensics Workshop Preparations: 1. Unzip the virtual machine from NetworkForensics_ VirtualBox.zip on your EXTENSIVE USE OF USB thumb drive to your local hard drive COMMAND LINE 2. Start VirtualBox and run the Security Onion VM IN THIS WORKSHOP 3. Log in with: user/password 1 FM CERT 2015-04-30 WWW.FORSVARSMAKTEN.SE Hands-on Network Forensics Erik Hjelmvik, Swedish Armed Forces CERT FIRST 2015, Berlin 2 FM CERT 2015-04-30 WWW.FORSVARSMAKTEN.SE Hands-on Network Forensics Workshop Preparations: 1. Unzip the virtual machine from NetworkForensics_ VirtualBox.zip on your EXTENSIVE USE OF USB thumb drive to your local hard drive COMMAND LINE 2. Start VirtualBox and run the Security Onion VM IN THIS WORKSHOP 3. Log in with: user/password 3 FM CERT 2015-04-30 WWW.FORSVARSMAKTEN.SE ”Password” Ned 4 FM CERT 2015-04-30 WWW.FORSVARSMAKTEN.SE SysAdmin: Homer 5 FM CERT 2015-04-30 WWW.FORSVARSMAKTEN.SE PR /Marketing: Krusty the Clown 6 FM CERT 2015-04-30 WWW.FORSVARSMAKTEN.SE Password Ned AB = pwned.se 7 FM CERT 2015-04-30 WWW.FORSVARSMAKTEN.SE pwned.se Network [INTERNET] | Default Gateway 192.168.0.1 PASSWORD-NED-XP www.pwned.se | 192.168.0.53 192.168.0.2 [TAP]--->Security- | | | Onion -----+------+---------+---------+----------------+------- | | Homer-xubuntu Krustys-PC 192.168.0.51 192.168.0.54 8 FM CERT 2015-04-30 WWW.FORSVARSMAKTEN.SE Security Onion 9 FM CERT 2015-04-30 WWW.FORSVARSMAKTEN.SE Paths (also on Cheat Sheet) • PCAP files: /nsm/sensor_data/securityonion_eth1/dailylogs/ • Argus files: -

Passive Asset Discovery and Operating System Fingerprinting in Industrial Control System Networks
Eindhoven University of Technology MASTER Passive asset discovery and operating system fingerprinting in industrial control system networks Mavrakis, C. Award date: 2015 Link to publication Disclaimer This document contains a student thesis (bachelor's or master's), as authored by a student at Eindhoven University of Technology. Student theses are made available in the TU/e repository upon obtaining the required degree. The grade received is not published on the document as presented in the repository. The required complexity or quality of research of student theses may vary by program, and the required minimum study period may vary in duration. General rights Copyright and moral rights for the publications made accessible in the public portal are retained by the authors and/or other copyright owners and it is a condition of accessing publications that users recognise and abide by the legal requirements associated with these rights. • Users may download and print one copy of any publication from the public portal for the purpose of private study or research. • You may not further distribute the material or use it for any profit-making activity or commercial gain Department of Mathematics and Computer Science Passive Asset Discovery and Operating System Fingerprinting in Industrial Control System Networks Master Thesis Chris Mavrakis Supervisors: prof.dr. S. Etalle dr. T. Oz¸celebi¨ dr. E. Costante Eindhoven, October 2015 Abstract Maintaining situational awareness in networks of industrial control systems is challenging due to the sheer number of devices involved, complex connections between subnetworks and the delicate nature of industrial processes. While current solutions for automatic discovery of devices and their operating system are lacking, plant operators need to have accurate information about the systems to be able to manage them effectively and detect, prevent and mitigate security and safety incidents. -

I3: Maximizing Packet Capture Performance
I3: Maximizing Packet Capture Performance Andrew Brown Agenda • Why do captures drop packets, how can you tell? • Software considerations • Hardware considerations • Potential hardware improvements • Test configurations/parameters • Performance results Sharkfest 2014 What is a drop? • Failure to capture a packet that is part of the traffic in which you’re interested • Dropped packets tend to be the most important • Capture filter will not necessarily help Sharkfest 2014 Why do drops occur? • Applications don’t know that their data is being captured • Result: Only one chance to capture a packet • What can go wrong? Let’s look at the life of a packet Sharkfest 2014 Internal packet flow • Path of a packet from NIC to application (Linux) • Switch output queue drops • Interface drops • Kernel drops Sharkfest 2014 Identifying drops • Software reports drops • L4 indicators (TCP ACKed lost segment) • L7 indicators (app-level sequence numbers revealed by dissector) Sharkfest 2014 When is (and isn’t) it necessary to take steps to maximize capture performance? • Not typically necessary when capturing traffic of <= 1G end device • More commonly necessary when capturing uplink traffic from a TAP or SPAN port • Some sort of action is almost always necessary at 10G • Methods described aren’t always necessary • Methods focus on free solutions Sharkfest 2014 Software considerations - Windows • Quit unnecessary programs • Avoid Wireshark for capturing ˗ Saves to TEMP ˗ Additional processing for packet statistics • Uses CPU • Uses memory over time, can lead -
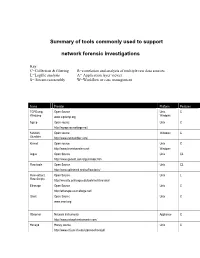
Network Forensic Tools Sidebar
Summary of tools commonly used to support network forensic investigations Key: C=Collection & filtering R=correlation and analysis of multiple raw data sources L=Logfile analysis A= Application layer viewer S= Stream reassembly W=Workflow or case management Name Provider Platform Features TCPDump, Open Source Unix, C Windump www.tcpdump.org Windows Ngrep Open source Unix C http://ngrep.sourceforge.net/ Network Open source Windows C Stumbler http://www.netstumbler.com/ Kismet Open source Unix C http://www.kismetwireless.net Windows Argus Open Source Unix CL http://www.qosient.com/argus/index.htm Flow-tools Open Source Unix CL http://www.splintered.net/sw/flow-tools/ Flow-extract, Open Source Unix L Flow Scripts http://security.uchicago.edu/tools/net-forensics/ Etherape Open Source Unix C http://etherape.sourceforge.net/ Snort Open Source Unix C www.snort.org Observer Network Instruments Appliance C http://www.networkinstruments.com/ Honeyd Honey source Unix C http://www.citi.umich.edu/u/provos/honeyd/ Ethereal Open Source Windows CLS www.Ethereal.com Unix Etherpeek Wild Packets, Inc. Windows CLS www.wildpackets.com SecureNet Intrusion Inc. Windows with CS http://www.intrusion.com collector appliance FLAG Open Source Unix L Forensic and http://www.dsd.gov.au/library/software/flag/ Log Analysis GUI ACID Analysis Console for Intrusion Databases Unix L http://www.andrew.cmu.edu/~rdanyliw/snort/snortacid.html Shadow http://www.nswc.navy.mil/ISSEC/CID/index.html Unix LS DeepNines and http://www.deepnines.com/sleuth9.html Unix CSR Sleuth9 Infinistream -

PROGRAMMING ESSENTIALS in PYTHON | PCAP Certification
PROGRAMMING ESSENTIALS IN PYTHON | PCAP Certification Programming Essentials in Python course covers all the basics of programming in Python, as well as general computer programming concepts and techniques. The course also familiarizes the student with the object-oriented approach. The course will prepare the student for jobs/careers connected with widely understood software development, which includes not only creating the code itself as a junior developer, but also computer system design and software testing. It could be a stepping-stone to learning any other programming language, and to explore technologies using Python as a foundation (e.g., Django, SciPy). This course is distinguished by its affordability, friendliness, and openness to the student. It starts from the absolute basics, guiding the student step by step to complex problems, making her/him a responsible software creator able to take on different challenges in many positions in the IT industry. TARGET AUDIENCE Programming Essentials in Python curriculum is designed for students with little or no prior knowledge of programming. TARGET CERTIFICATION Programming Essentials in Python curriculum helps students prepare for the PCAP | Python Certified Associate Programmer certification exam. PCAP is a professional certification that measures the student’s ability to accomplish coding tasks related to the basics of programming in the Python language, and the fundamental notions and techniques used in object-oriented programming. PCAP – COURSE MODULES & OBJECTIVES Module 1: Familiarize the student with the basic methods offered by Python of formatting and outputting data, together with the primary kinds of data and numerical operators, their mutual relations and bindings. Introduce the concept of variables and variable naming conventions. -
![LIST of NOSQL DATABASES [Currently 150]](https://docslib.b-cdn.net/cover/8918/list-of-nosql-databases-currently-150-418918.webp)
LIST of NOSQL DATABASES [Currently 150]
Your Ultimate Guide to the Non - Relational Universe! [the best selected nosql link Archive in the web] ...never miss a conceptual article again... News Feed covering all changes here! NoSQL DEFINITION: Next Generation Databases mostly addressing some of the points: being non-relational, distributed, open-source and horizontally scalable. The original intention has been modern web-scale databases. The movement began early 2009 and is growing rapidly. Often more characteristics apply such as: schema-free, easy replication support, simple API, eventually consistent / BASE (not ACID), a huge amount of data and more. So the misleading term "nosql" (the community now translates it mostly with "not only sql") should be seen as an alias to something like the definition above. [based on 7 sources, 14 constructive feedback emails (thanks!) and 1 disliking comment . Agree / Disagree? Tell me so! By the way: this is a strong definition and it is out there here since 2009!] LIST OF NOSQL DATABASES [currently 150] Core NoSQL Systems: [Mostly originated out of a Web 2.0 need] Wide Column Store / Column Families Hadoop / HBase API: Java / any writer, Protocol: any write call, Query Method: MapReduce Java / any exec, Replication: HDFS Replication, Written in: Java, Concurrency: ?, Misc: Links: 3 Books [1, 2, 3] Cassandra massively scalable, partitioned row store, masterless architecture, linear scale performance, no single points of failure, read/write support across multiple data centers & cloud availability zones. API / Query Method: CQL and Thrift, replication: peer-to-peer, written in: Java, Concurrency: tunable consistency, Misc: built-in data compression, MapReduce support, primary/secondary indexes, security features. -

STUDY and SURVEY of BIG DATA for INDUSTRY Surbhi Verma*, Sai Rohit
ISSN: 2277-9655 [Verma* et al., 5(11): November, 2016] Impact Factor: 4.116 IC™ Value: 3.00 CODEN: IJESS7 IJESRT INTERNATIONAL JOURNAL OF ENGINEERING SCIENCES & RESEARCH TECHNOLOGY STUDY AND SURVEY OF BIG DATA FOR INDUSTRY Surbhi Verma*, Sai Rohit DOI: 10.5281/zenodo.166840 ABSTRACT Now-a-days we rarely observe any company or any industry who don’t have any database. Industries with huge amounts of data are finding it difficult to manage. They all are in search of some technology which can make their work easy and fast. The primary purpose of this paper is to provide an in-depth analysis of different platforms available for performing big data over local data and how they differ with each other. This paper surveys different hardware platforms available for big data and local data and assesses the advantages and drawbacks of each of these platforms. KEYWORDS: Big data, Local data, HadoopBase, Clusterpoint, Mongodb, Couchbase, Database. INTRODUCTION This is an era of Big Data. Big Data is making radical changes in traditional data analysis platforms. To perform any kind of analysis on such huge and complex data, scaling up the hardware platforms becomes imminent and choosing the right hardware/software platforms becomes very important. In this research we are showing how big data has been improvising over the local databases and other technologies. Present day, big data is making a huge turnaround in technological world and so to manage and access data there must be some kind of linking between big data and local data which is not done yet. -

Guide to Computer Forensics and Investigations Fourth Edition
Guide to Computer Forensics and Investigations Fourth Edition Chapter 11 Virtual Machines, Network Forensics, and Live Acquisitions Objectives • Describe primary concerns in conducting forensic examinations of virtual machines • Describe the importance of network forensics • Explain standard procedures for performing a live acquisition • Explain standard procedures for network forensics • Describe the use of network tools Guide to Computer Forensics and Investigations 2 Virtual Machines Overview • Virtual machines are important in today’s networks. • Investigators must know how to detect a virtual machine installed on a host, acquire an image of a virtual machine, and use virtual machines to examine malware. Virtual Machines Overview (cont.) • Check whether virtual machines are loaded on a host computer. • Check Registry for clues that virtual machines have been installed or uninstalled. Network Forensics Overview • Network forensics – Systematic tracking of incoming and outgoing traffic • To ascertain how an attack was carried out or how an event occurred on a network • Intruders leave trail behind • Determine the cause of the abnormal traffic – Internal bug – Attackers Guide to Computer Forensics and Investigations 5 Securing a Network • Layered network defense strategy – Sets up layers of protection to hide the most valuable data at the innermost part of the network • Defense in depth (DiD) – Similar approach developed by the NSA – Modes of protection • People • Technology • Operations Guide to Computer Forensics and Investigations