Open Source Licenses
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Webinar PPT/Slides
3/16/2021 Child Trauma, Parenting, & Challenging Behaviors Melissa Bernstein, PhD 1 The impact of trauma on parenting Functional Assessment- what’s going on?! Overview The importance of relationships Strategies to shape behavior 2 THE IMPACT OF TRAUMA ON PARENTING 3 1 3/16/2021 BEHAVIOR PROBLEMS AND CHILDREN What are the most disruptive child behaviors? 4 What Does Ideal Parenting Look Like? Nurturing Appropriate Interactions Limits 5 What Can Happen to Balance after Trauma? High Nurturing Low Limits 6 2 3/16/2021 What Can Happen to Balance after Trauma? High Limits Low Nurturing 7 THE IMPORTANCE OF ASSESSMENT IN MANAGING CHALLENGING BEHAVIOR 8 • The body’s ‘alarm’ system is broken after a trauma Trauma Reactions • The body responds in one of three ways to promote and Misbehavior ‘survival’ • This makes it harder for children to regulate their behavior FightFlight Freeze 9 3 3/16/2021 Clues That a Child is Stuck in Fight/Flight/Freeze • Extreme emotions • Behavior feels like its out of the blue • Big response over very minor issue • Happens quickly (0 to 60) • Child is unable to calm down • Doesn’t respond to reasoning • Distress may last a long time • Apologetic later 10 What is the function of this behavior? 11 Applying Skills to Trauma Reactions Create Reflect Offer Allow Create a Briefly reflect Offer to do a Allow child sense of emotion favorite time to calm safety • Tell child you can coping skill • This means back • Stand a few feet see he/she/they together away and be away from child is feeling upset quiet! Less and you are • -

CA Gen Integration Consuming REST Services – C Edition
CA Gen Integration Consuming REST Services – C Edition Christian Kersters Broadcom Limited Web: www.broadcom.com Corporate Headquarters: San Jose, CA Broadcom Proprietary. © 2020 Broadcom. All rights reserved. Consuming REST Services – C Edition Revision History Revision Date Change Description V0.9 2020/11/12 Initial version V1.0 2020/11/17 Revised edition (integration of C. Jamar suggestions) Broadcom Proprietary. © 2020 Broadcom. All rights reserved. 1 Consuming REST Services – C Edition References CA Gen Integration Solutions, Christian Kersters, Broadcom, August 2017 https://community.broadcom.com/HigherLogic/System/DownloadDocumentFile.ashx?Docum entFileKey=4a401797-4dfe-4230-a031-273b908e57d3&forceDialog=0 Hello world: getting started with REST APIs https://www.genivia.com/dev.html#how-rest gSOAP User Guide https://www.genivia.com/doc/guide/html/index.html Richardson Maturity Model https://restfulapi.net/richardson-maturity-model/ Broadcom Proprietary. © 2020 Broadcom. All rights reserved. 2 Consuming REST Services – C Edition Contents Revision History ......................................................................................................................... 1 References ................................................................................................................................. 2 Contents ..................................................................................................................................... 3 1. Introduction ........................................................................................................................ -

Python 2.6.2 License 04.11.09 14:37
Python 2.6.2 license 04.11.09 14:37 Download > Releases > License Python 2.6.2 license This is the official license for the Python 2.6.2 release: A. HISTORY OF THE SOFTWARE ========================== Python was created in the early 1990s by Guido van Rossum at Stichting Mathematisch Centrum (CWI, see http://www.cwi.nl) in the Netherlands as a successor of a language called ABC. Guido remains Python's principal author, although it includes many contributions from others. In 1995, Guido continued his work on Python at the Corporation for National Research Initiatives (CNRI, see http://www.cnri.reston.va.us) in Reston, Virginia where he released several versions of the software. In May 2000, Guido and the Python core development team moved to BeOpen.com to form the BeOpen PythonLabs team. In October of the same year, the PythonLabs team moved to Digital Creations (now Zope Corporation, see http://www.zope.com). In 2001, the Python Software Foundation (PSF, see http://www.python.org/psf/) was formed, a non-profit organization created specifically to own Python-related Intellectual Property. Zope Corporation is a sponsoring member of the PSF. All Python releases are Open Source (see http://www.opensource.org for the Open Source Definition). Historically, most, but not all, Python releases have also been GPL-compatible; the table below summarizes the various releases. Release Derived Year Owner GPL- from compatible? (1) 0.9.0 thru 1.2 1991-1995 CWI yes 1.3 thru 1.5.2 1.2 1995-1999 CNRI yes 1.6 1.5.2 2000 CNRI no 2.0 1.6 2000 BeOpen.com no 1.6.1 -
Cisco Telepresence TC Software Licensing Information (TC4.1)
Cisco TelePresence TC Software License information guide TC Software FEBRUARY 2011 Legal information and third party copyright and licenses For Cisco TelePresence products using TC software D14767.02 License Information for products using TC Software, TC4 February 2011. 1 © 2010-2011 Cisco Systems, Inc. All rights reserved. www.cisco.com Cisco TelePresence TC Software License information guide ipcalc-1.3, ipcalc-license ...................................................................................... 16 TA - ToC - Hidden Table of Contents iproute-2.6.26, GPLv2 .......................................................................................16 What’stext anchor in iptables-1.4.28, GPLv2......................................................................................16 About this guide ..............................................................................................................4 iputils-s20071127, iputils-bsd-license .................................................... 16 The products covered by this guide: .....................................................4 jpeg lib, jpeg-license ................................................................................................ 17 this guide? User documentation .............................................................................................4 Kmod-*, GPLv2 ........................................................................................................19 Software download ................................................................................................4 -

Ironpython in Action
IronPytho IN ACTION Michael J. Foord Christian Muirhead FOREWORD BY JIM HUGUNIN MANNING IronPython in Action Download at Boykma.Com Licensed to Deborah Christiansen <[email protected]> Download at Boykma.Com Licensed to Deborah Christiansen <[email protected]> IronPython in Action MICHAEL J. FOORD CHRISTIAN MUIRHEAD MANNING Greenwich (74° w. long.) Download at Boykma.Com Licensed to Deborah Christiansen <[email protected]> For online information and ordering of this and other Manning books, please visit www.manning.com. The publisher offers discounts on this book when ordered in quantity. For more information, please contact Special Sales Department Manning Publications Co. Sound View Court 3B fax: (609) 877-8256 Greenwich, CT 06830 email: [email protected] ©2009 by Manning Publications Co. All rights reserved. No part of this publication may be reproduced, stored in a retrieval system, or transmitted, in any form or by means electronic, mechanical, photocopying, or otherwise, without prior written permission of the publisher. Many of the designations used by manufacturers and sellers to distinguish their products are claimed as trademarks. Where those designations appear in the book, and Manning Publications was aware of a trademark claim, the designations have been printed in initial caps or all caps. Recognizing the importance of preserving what has been written, it is Manning’s policy to have the books we publish printed on acid-free paper, and we exert our best efforts to that end. Recognizing also our responsibility to conserve the resources of our planet, Manning books are printed on paper that is at least 15% recycled and processed without the use of elemental chlorine. -

OSS Disclosure
Tape Automation Scalar i500, Firmware Release I8.2.2 (645G) Open Source Software Licenses Open Source Software (OSS) Licenses for: Scalar i500 Firmware Release I8.2.2 (645G). The firmware/software contained in the Scalar i500 is an aggregate of vendor proprietary pro- grams as well as third party programs, including Open Source Software (OSS). Use of OSS is subject to designated license terms and the following OSS license disclosure lists all open source components and applicable licenses that are part of the tape library firmware. All software that is designated as OSS may be copied, distributed, and/or modified in accordance with the terms and conditions of its respective license(s). Additionally, for some OSS you are entitled to obtain the corresponding OSS source files as required by the respective and applicable license terms. While GNU General Public License ("GPL") and GNU Lesser General Public Li- cense ("LGPL") licensed OSS requires that the sources be made available, Quantum makes all tape library firmware integrated OSS source files, whether licensed as GPL, LGPL or otherwise, available upon request. Please refer to the Scalar i500 Open Source License CD (part number 3- 03679-xx) when making such request. For contact information, see Getting More Information. LTO tape drives installed in the library may also include OSS components. For a complete list- ing of respective OSS packages and applicable OSS license information included in LTO tape drives, as well as instructions to obtain source files pursuant to applicable license requirements, please reference the Tape Automation disclosure listings under the Open Source Information link at www.quantum.com/support. -

PV204: Disk Encryption Lab
PV204: Disk encryption lab May 12, 2016, Milan Broz <[email protected]> Introduction Encryption can provide confidentiality and authenticity of user data. It can be implemented on several different layes, including application, file system or storage device. Application encryption examples are PGP or ZIP compression with password. Encryption of files (inside filesystem or through independent layer like Linux eCryptfs) provides more generic solution. Yet some parts (like filesystem metadata) are still unencrypted. However this solution provides encrypted data with private key per user. (Every user can have own directory encrypted by own key.) Encryption of the low-level storage (disk) is called Full Disk Encryption (FDE). It is completely transparent to the user (no need to choose what to encrypt – the whole disk is encrypted). The encrypted disk behaves as the same as a disk without encryption. The major disadvantage is that everyone who knows the password can read the whole disk. Often we combine FDE with another encryption layer. The primary use of FDE is to provide data confidentiality in power-down mode (stolen laptop does not leak user data). Once the disk is unlocked, the main encryption key remains in system, usually directly in system RAM. Exercise II will show how easy is to get this key from memory image of system. Another disadvantage of FDE is that it usually cannot guarantee integrity of data. Encryption is fully transparent and length-preserving, the ciphertext and plaintext device are of the same size. There is no space to store any integrity information. This allows attacks by direct modification of ciphertext. -

Vxworks Third Party Software Notices
Wind River® VxWorks® 7 Third Party License Notices This document contains third party intellectual property (IP) notices for the BUSINESS INTERRUPTION) HOWEVER CAUSED AND ON ANY Wind River® VxWorks® 7 distribution. Certain licenses and license notices THEORY OF LIABILITY, WHETHER IN CONTRACT, STRICT LIABILITY, may appear in other parts of the product distribution in accordance with the OR TORT (INCLUDING NEGLIGENCE OR OTHERWISE) ARISING IN license requirements. ANY WAY OUT OF THE USE OF THIS SOFTWARE, EVEN IF ADVISED OF THE POSSIBILITY OF SUCH DAMAGE. Trademarks All company, product and service names used in this software are for ACPICA identification purposes only. Version: 20170303 Component(s): Runtime Wind River and VxWorks are registered trademarks of Wind River Systems. Description: Provides code to implement ACPI specification in VxWorks. UNIX is a registered trademark of The Open Group. IBM and Bluemix are registered trademarks of the IBM Corporation. NOTICES: All other third-party trademarks are the property of their respective owners. 1. Copyright Notice Some or all of this work - Copyright (c) 1999 - 2016, Intel Corp. All rights reserved. Third Party Notices 2. License 2.1. This is your license from Intel Corp. under its intellectual property rights. You may have additional license terms from the party that provided you this software, covering your right to use that party's intellectual property rights. 64-Bit Dynamic Linker Version: 2.2. Intel grants, free of charge, to any person ("Licensee") obtaining a copy Component(s): Runtime of the source code appearing in this file ("Covered Code") an irrevocable, Description: The dynamic linker is used to load shared libraries. -

Single-Node CUCM Single-Node IMP 10.201.203.76 10.201.203.75 10.201.203.67 10.201.203.72
#CLUS CCIE Collaboration Techtorial Ben Ng, Exam PM, L@C, Cisco CX Ishan Sambhi, CSE, Cisco CX TECCCIE-3503 #CLUS Agenda • Session 1: CCIE® Program Overview • Session 2: CCIE Collaboration Overview • Session 3: CCIE Collaboration Modular Lab Exams • Session 4: Lab Exam Diagnostic Module with Case Studies • Session 5: Lab Exam Troubleshooting Module with Case Studies • Session 6: Lab Exam Configuration Module with Case Studies • Session 7: Exam Preparation Tips, In-Lab Strategies, and Q&A #CLUS TECCCIE-3503 © 2019 Cisco and/or its affiliates. All rights reserved. Cisco Public 3 Cisco Webex Teams Questions? Use Cisco Webex Teams to chat with the speaker after the session How 1 Find this session in the Cisco Live Mobile App 2 Click “Join the Discussion” 3 Install Webex Teams or go directly to the team space 4 Enter messages/questions in the team space Webex Teams will be moderated cs.co/ciscolivebot#TECCCIE-3503 by the speaker until June 16, 2019. #CLUS © 2019 Cisco and/or its affiliates. All rights reserved. Cisco Public 4 Session 1: CCIE Program Overview Cisco CCIE Certifications CCIE Track Major Skills R&S Configure and troubleshoot complex converged networks Security Configure complex, end-to-end secure networks, troubleshoot environments, and anticipate and respond to network attacks Service Provider Configure and troubleshoot advanced technologies to support service provider networks Collaboration Design, implement, integrate, and troubleshoot complex collaboration networks Wireless Plan, design, implement, operate, and troubleshoot wireless network and mobility infrastructure Data Center Configure and troubleshoot Cisco Data Center technologies including DC infrastructure, compute and virtualization. #CLUS TECCCIE-3503 © 2019 Cisco and/or its affiliates. -
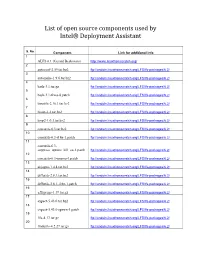
List of Open Source Components Used by Intel® Deployment Assistant
List of open source components used by Intel® Deployment Assistant S. No Component Link for additional info 1 ALFS 6.1 (Gerard Beekmans) http://www.linuxfromscratch.org/ 2 autoconf-2.59.tar.bz2 ftp://anduin.linuxfromscratch.org/LFS/lfs-packages/6.2/ 3 automake-1.9.6.tar.bz2 ftp://anduin.linuxfromscratch.org/LFS/lfs-packages/6.2/ 4 bash-3.1.tar.gz ftp://anduin.linuxfromscratch.org/LFS/lfs-packages/6.2/ 5 bash-3.1-fixes-8.patch ftp://anduin.linuxfromscratch.org/LFS/lfs-packages/6.2/ 6 binutils-2.16.1.tar.bz2 ftp://anduin.linuxfromscratch.org/LFS/lfs-packages/6.2/ 7 bison-2.2.tar.bz2 ftp://anduin.linuxfromscratch.org/LFS/lfs-packages/6.2/ 8 bzip2-1.0.3.tar.bz2 ftp://anduin.linuxfromscratch.org/LFS/lfs-packages/6.2/ 9 coreutils-6.3.tar.bz2 ftp://anduin.linuxfromscratch.org/LFS/lfs-packages/6.2/ 10 coreutils-6.3-i18n-1.patch ftp://anduin.linuxfromscratch.org/LFS/lfs-packages/6.2/ 11 coreutils-6.3- suppress_uptime_kill_su-1.patch ftp://anduin.linuxfromscratch.org/LFS/lfs-packages/6.2/ 12 coreutils-6.3-uname-1.patch ftp://anduin.linuxfromscratch.org/LFS/lfs-packages/6.2/ 13 dejagnu-1.4.4.tar.bz2 ftp://anduin.linuxfromscratch.org/LFS/lfs-packages/6.2/ 14 diffutils-2.8.1.tar.bz2 ftp://anduin.linuxfromscratch.org/LFS/lfs-packages/6.2/ 15 diffutils-2.8.1-i18n-1.patch ftp://anduin.linuxfromscratch.org/LFS/lfs-packages/6.2/ 16 e2fsprogs-1.39.tar.gz ftp://anduin.linuxfromscratch.org/LFS/lfs-packages/6.2/ 17 expect-5.43.0.tar.bz2 ftp://anduin.linuxfromscratch.org/LFS/lfs-packages/6.2/ 18 expect-5.43.0-spawn-1.patch ftp://anduin.linuxfromscratch.org/LFS/lfs-packages/6.2/ -

Version 7.8-Systemd
Linux From Scratch Version 7.8-systemd Created by Gerard Beekmans Edited by Douglas R. Reno Linux From Scratch: Version 7.8-systemd by Created by Gerard Beekmans and Edited by Douglas R. Reno Copyright © 1999-2015 Gerard Beekmans Copyright © 1999-2015, Gerard Beekmans All rights reserved. This book is licensed under a Creative Commons License. Computer instructions may be extracted from the book under the MIT License. Linux® is a registered trademark of Linus Torvalds. Linux From Scratch - Version 7.8-systemd Table of Contents Preface .......................................................................................................................................................................... vii i. Foreword ............................................................................................................................................................. vii ii. Audience ............................................................................................................................................................ vii iii. LFS Target Architectures ................................................................................................................................ viii iv. LFS and Standards ............................................................................................................................................ ix v. Rationale for Packages in the Book .................................................................................................................... x vi. Prerequisites -

Mcafee Foundstone Fsl Update
2016-AUG-18 FSL version 7.5.841 MCAFEE FOUNDSTONE FSL UPDATE To better protect your environment McAfee has created this FSL check update for the Foundstone Product Suite. The following is a detailed summary of the new and updated checks included with this release. NEW CHECKS 20369 - Splunk Enterprise Multiple Vulnerabilities (SP-CAAAPQM) Category: General Vulnerability Assessment -> NonIntrusive -> Web Server Risk Level: High CVE: CVE-2013-0211, CVE-2015-2304, CVE-2016-1541, CVE-2016-2105, CVE-2016-2106, CVE-2016-2107, CVE-2016-2108, CVE- 2016-2109, CVE-2016-2176 Description Multiple vulnerabilities are present in some versions of Splunk Enterprise. Observation Splunk Enterprise is an operational intelligence solution Multiple vulnerabilities are present in some versions of Splunk Enterprise. The flaws lie in multiple components. Successful exploitation by a remote attacker could lead to the information disclosure of sensitive information, cause denial of service or execute arbitrary code. 20428 - (HT206899) Apple iCloud Multiple Vulnerabilities Prior To 5.2.1 Category: Windows Host Assessment -> Miscellaneous (CATEGORY REQUIRES CREDENTIALS) Risk Level: High CVE: CVE-2016-1684, CVE-2016-1836, CVE-2016-4447, CVE-2016-4448, CVE-2016-4449, CVE-2016-4483, CVE-2016-4607, CVE- 2016-4608, CVE-2016-4609, CVE-2016-4610, CVE-2016-4612, CVE-2016-4614, CVE-2016-4615, CVE-2016-4616, CVE-2016-4619 Description Multiple vulnerabilities are present in some versions of Apple iCloud. Observation Apple iCloud is a manager for the Apple's could based storage service. Multiple vulnerabilities are present in some versions of Apple iCloud. The flaws lie in several components. Successful exploitation could allow an attacker to retrieve sensitive data, cause a denial of service condition or have other unspecified impact on the target system.