China's Internet of Things
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Paths to Our Digital Future Table of Contents
INTERNET SOCIETY GLOBAL INTERNET REPORT Paths to Our Digital Future Table of Contents Foreword by Kathy Brown, Executive summary Introduction President and CEO, 5–13 14–16 Internet Society 3–4 How we see the Internet Drivers of Change Drivers of Change 16–19 & Areas of Impact 24–61 21–23 Areas of Impact What if? Recommendations 62–84 85–103 104–110 Conclusion Methodology Acknowledgements 111–113 114–117 118–119 internetsociety.org 2 Foreword Foreword by Kathy Brown, President and CEO, Internet Society The Internet Society’s history is inseparably tied to The Internet Society’s fourth annual Global Internet the history of the Internet itself. We were founded Report — Paths to Our Digital Future — explores in 1992 by Internet pioneers Bob Kahn and Vint Cerf, this important question. This comprehensive report along with numerous other visionary individuals brings together insights from across our diverse and organisations. These early Internet luminaries global community to inspire all who engage with the believed that ‘a society would emerge from the Internet to think differently and to prepare for the idea that is the Internet’. And they were right. The opportunities and challenges on the horizon. Internet has come a long way since its inception, and is now part of our social fabric — essential to how No one knows exactly how the Internet will evolve, we connect, communicate, create and collaborate. but we do know it will require new thinking, new approaches and new tools for this rapidly changing 2017 marks a significant milestone for the Internet world around us. Society. -

Lista Telefona Koji Podrzavaju Mbanking
Spisak mobilnih uređaja koje podržava mBanking Sparkasse Bank Proizvođać Model Proizvođać Model Acer Liquid MT Dell 101DL Acer E350 Dell Streak Acer S500 Dell Dell Venue Acer Z110 Enspert vanitysmart Acer E330 Enspert orion Acer AT390 Enspert CINK SLIM Acer E310 Enspert CINK KING Acer E350 Foxconn Boston Acer Liquid Foxconn International vizio VP800 Holdings Limited Acer S300 Foxconn International XOLO Acer Acer E320-orange Holdings Limited Anydata Philips W632 Foxconn International SHARP SH631W Anydata Philips W626 Holdings Limited Anydata Philips W832 Foxconn International ViewPhone3 Holdings Limited Anydata Philips W336 Foxconn International XOLO_X1000 Anydata Philips W536 Holdings Limited Archos Archos 97 Xenon Foxconn International Changhong H5018 Asus ASUS Transformer Pad Infinity Holdings Limited Asus PadFone Foxconn International MUSN COUPLE Holdings Limited Asus ME171 Foxconn International SH530U Asus PadFone Infinity Holdings Limited Asus PadFone 2 Foxconn International WellcoM-A99 Cellon HW-W820 Holdings Limited Coolpad Coolpad 5010 Foxconn International Axioo-VIGO410 Holdings Limited Coolpad MTS-SP150 Foxconn International SHARP SH630E Coolpad 801E Holdings Limited Coolpad Coolpad 7019 Foxconn International ViewSonic-V350 Coolpad 5860E Holdings Limited Coolpad PAP4000 Foxconn International Commtiva-HD710 Holdings Limited Coolpad 7266 Foxconn International WellcoM-A800 Coolpad 8180 Holdings Limited Coolpad 5860 Foxconn International SHARP SH837W Coolpad Coolpad 5210 Holdings Limited Coolpad 9120 Foxconn International CSL-MI410 -

The Open Internet
The Open Internet What it is, and how to avoid mistaking it for something else. SEPTEMBER 2014 Introduction1 It is not by chance that we have enjoyed the extraordinary success of the Internet as a global engine of economic, political, cultural, and social progress. Fundamental principles embedded in the architecture of the Internet as a collaboration among designers, builders, providers, and users led directly to this success. Sustaining it will require a commitment by today’s policy makers to understand and respect those principles—not because they are honored by time or tradition, but because they confer tangible present and future benefits. The term "Open Internet" has been used so often and so freely that everyone knows what it means—or thinks they know what it means, and assumes that everyone else means the same thing when they use it. After all, the core enabling principle of the Internet as a system that includes users, applications, and infrastructure is openness, which infuses every aspect of the modern Internet—technical, economic, political, and social. But depending on the context in which it is used, the word open conveys different meanings, particularly when subtle (or not–so–subtle) variations are introduced by translation from one language to another; and because “openness” has become an important issue in many Internet political debates, defining what it means has become part of those debates. As is usually the case when people understand the terms and concepts of a debate differently, it will be difficult for us to resolve important issues of Internet policy until we reconcile our different understandings of open and openness in principle and in practice. -

Press Release May 25, 2021
Press Release May 25, 2021 NEW PAN-INDUSTRY ECO RATING SCHEME LAUNCHED FOR MOBILE PHONES • Deutsche Telekom, Orange, Telefónica, Telia Company and Vodafone unveil new consumer labelling to identify more sustainable mobile phones • Eco Rating to roll out across Europe from June 2021, including phones from 12 vendors Five of Europe’s leading mobile operators have joined forces to update and launch a new pan- industry Eco Rating labelling scheme that will help consumers identify and compare the most sustainable mobile phones and encourage suppliers to reduce the environmental impact of their devices. The Eco Rating initiative has been created jointly by Deutsche Telekom, Orange, Telefónica (operating under the O2 and Movistar brands), Telia Company and Vodafone to provide consistent, accurate information at retail on the environmental impact of producing, using, transporting and disposing of smartphones and feature phones. Eco Rating will enable operators and their customers to encourage wider rating of phones and demonstrate the demand for more sustainable electronics. A range of new consumer phones from 12 mobile phone brands will be assessed by the Eco Rating initiative, with others expected to be announced in the future. Launch partners include Bullitt Group – Home of CAT and Motorola rugged phones, Doro, HMD Global - Home of Nokia Phones, Huawei, MobiWire, Motorola / Lenovo, OnePlus, OPPO, Samsung Electronics, TCL / Alcatel, Xiaomi and ZTE. Starting from June 2021, the mobile operators will begin to introduce the distinct Eco Rating labelling at point of sale across 24 countries in Europe where they are present. Customers can learn more about the initiative and see how the rating is calculated by visiting a new website at www.ecoratingdevices.com and www.teliacompany.com/ecorating Following a detailed assessment, each mobile phone handset will be given an overall Eco Rating score out of a maximum of 100 to signal the environmental performance of the device across its entire life cycle. -

2018 International Student Handbook.Pdf
2018 LCC International Students Guidebook 1. OVERVIEW OF LINGANG ....................................... 2 2. APPLICATION SYSTEM LOG-IN ................................. 3 3. REGISTRATION ................................................ 4 4. TUITION PAYMENT ............................................. 6 5. ACCOMMODATION ............................................. 7 6. FOOD ......................................................... 10 7. SHOPPING ..................................................... 13 8. TRANSPORT ................................................... 14 9. HEALTH INSURANCE .......................................... 20 10. VISA AFFAIRS ................................................. 25 11. SCHOLARSHIP STUDENT ISSUES ............................... 28 12. BANKING ..................................................... 32 13. SIM Card Purchase in Mainland China ............................. 33 14. ABOUT SJTU .................................................. 34 15. TOP ATTRACTIONS IN SHANGHAI ............................. 34 16. CITIES NEARBY ............................................... 37 17. USEFUL APPS ................................................. 39 18. USEFUL WEBSITES ............................................ 40 19. CONTACT US ................................................. 41 China-UK Low Carbon College No3, Yinlian Road, Pudong New District, Shanghai 1 1. OVERVIEW OF LINGANG Lingang is located at the southeast tip of continental Shanghai. It is 75 km away from the City Centre of Shanghai. Standing at the -

Prohibited Agreements with Huawei, ZTE Corp, Hytera, Hangzhou Hikvision, Dahua and Their Subsidiaries and Affiliates
Prohibited Agreements with Huawei, ZTE Corp, Hytera, Hangzhou Hikvision, Dahua and their Subsidiaries and Affiliates. Code of Federal Regulations (CFR), 2 CFR 200.216, prohibits agreements for certain telecommunications and video surveillance services or equipment from the following companies as a substantial or essential component of any system or as critical technology as part of any system. • Huawei Technologies Company; • ZTE Corporation; • Hytera Communications Corporation; • Hangzhou Hikvision Digital Technology Company; • Dahua Technology company; or • their subsidiaries or affiliates, Entering into agreements with these companies, their subsidiaries or affiliates (listed below) for telecommunications equipment and/or services is prohibited, as doing so could place the university at risk of losing federal grants and contracts. Identified subsidiaries/affiliates of Huawei Technologies Company Source: Business databases, Huawei Investment & Holding Co., Ltd., 2017 Annual Report • Amartus, SDN Software Technology and Team • Beijing Huawei Digital Technologies, Co. Ltd. • Caliopa NV • Centre for Integrated Photonics Ltd. • Chinasoft International Technology Services Ltd. • FutureWei Technologies, Inc. • HexaTier Ltd. • HiSilicon Optoelectronics Co., Ltd. • Huawei Device Co., Ltd. • Huawei Device (Dongguan) Co., Ltd. • Huawei Device (Hong Kong) Co., Ltd. • Huawei Enterprise USA, Inc. • Huawei Global Finance (UK) Ltd. • Huawei International Co. Ltd. • Huawei Machine Co., Ltd. • Huawei Marine • Huawei North America • Huawei Software Technologies, Co., Ltd. • Huawei Symantec Technologies Co., Ltd. • Huawei Tech Investment Co., Ltd. • Huawei Technical Service Co. Ltd. • Huawei Technologies Cooperative U.A. • Huawei Technologies Germany GmbH • Huawei Technologies Japan K.K. • Huawei Technologies South Africa Pty Ltd. • Huawei Technologies (Thailand) Co. • iSoftStone Technology Service Co., Ltd. • JV “Broadband Solutions” LLC • M4S N.V. • Proven Honor Capital Limited • PT Huawei Tech Investment • Shanghai Huawei Technologies Co., Ltd. -
Android Devices
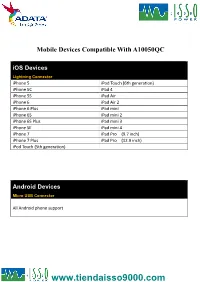
Mobile Devices Compatible With A10050QC iOS Devices Lightning Connector iPhone 5 iPod Touch (6th generation) iPhone 5C iPad 4 iPhone 5S iPad Air iPhone 6 iPad Air 2 iPhone 6 Plus iPad mini iPhone 6S iPad mini 2 iPhone 6S Plus iPad mini 3 iPhone SE iPad mini 4 iPhone 7 iPad Pro (9.7 inch) iPhone 7 Plus iPad Pro (12.9 inch) iPod Touch (5th generation) Android Devices Micro USB Connector All Android phone support Smartphone With Quick Charge 3.0 Technology Type-C Connector Asus ZenFone 3 LG V20 TCL Idol 4S Asus ZenFone 3 Deluxe NuAns NEO VIVO Xplay6 Asus ZenFone 3 Ultra Nubia Z11 Max Wiley Fox Swift 2 Alcatel Idol 4 Nubia Z11miniS Xiaomi Mi 5 Alcatel Idol 4S Nubia Z11 Xiaomi Mi 5s General Mobile GM5+ Qiku Q5 Xiaomi Mi 5s Plus HP Elite x3 Qiku Q5 Plus Xiaomi Mi Note 2 LeEco Le MAX 2 Smartisan M1 Xiaomi MIX LeEco (LeTV) Le MAX Pro Smartisan M1L ZTE Axon 7 Max LeEco Le Pro 3 Sony Xperia XZ ZTE Axon 7 Lenovo ZUK Z2 Pro TCL Idol 4-Pro Smartphone With Quick Charge 3.0 Technology Micro USB Connector HTC One A9 Vodafone Smart platinum 7 Qiku N45 Wiley Fox Swift Sugar F7 Xiaomi Mi Max Compatible With Quick Charge 3.0 Technology Micro USB Connector Asus Zenfone 2 New Moto X by Motorola Sony Xperia Z4 BlackBerry Priv Nextbit Robin Sony Xperia Z4 Tablet Disney Mobile on docomo Panasonic CM-1 Sony Xperia Z5 Droid Turbo by Motorola Ramos Mos1 Sony Xperia Z5 Compact Eben 8848 Samsung Galaxy A8 Sony Xperia Z5 Premium (KDDI Japan) EE 4GEE WiFi (MiFi) Samsung Galaxy Note 4 Vertu Signature Touch Fujitsu Arrows Samsung Galaxy Note 5 Vestel Venus V3 5070 Fujitsu -

TCL 科技集团股份有限公司 TCL Technology Group Corporation
TCL Technology Group Corporation Annual Report 2019 TCL 科技集团股份有限公司 TCL Technology Group Corporation ANNUAL REPORT 2019 31 March 2020 1 TCL Technology Group Corporation Annual Report 2019 Table of Contents Part I Important Notes, Table of Contents and Definitions .................................................. 8 Part II Corporate Information and Key Financial Information ........................................... 11 Part III Business Summary .........................................................................................................17 Part IV Directors’ Report .............................................................................................................22 Part V Significant Events ............................................................................................................51 Part VI Share Changes and Shareholder Information .........................................................84 Part VII Directors, Supervisors, Senior Management and Staff .......................................93 Part VIII Corporate Governance ..............................................................................................113 Part IX Corporate Bonds .......................................................................................................... 129 Part X Financial Report............................................................................................................. 138 2 TCL Technology Group Corporation Annual Report 2019 Achieve Global Leadership by Innovation and Efficiency Chairman’s -

Lu Zhiqiang China Oceanwide
08 Investment.FIN.qxp_Layout 1 14/9/16 12:21 pm Page 81 Week in China China’s Tycoons Investment Lu Zhiqiang China Oceanwide Oceanwide Holdings, its Shenzhen-listed property unit, had a total asset value of Rmb118 billion in 2015. Hurun’s China Rich List He is the key ranked Lu as China’s 8th richest man in 2015 investor behind with a net worth of Rmb83 billlion. Minsheng Bank and Legend Guanxi Holdings A long-term ally of Liu Chuanzhi, who is known as the ‘godfather of Chinese entrepreneurs’, Oceanwide acquired a 29% stake in Legend Holdings (the parent firm of Lenovo) in 2009 from the Chinese Academy of Social Sciences for Rmb2.7 billion. The transaction was symbolic as it marked the dismantling of Legend’s SOE status. Lu and Liu also collaborated to establish the exclusive Taishan Club in 1993, an unofficial association of entrepreneurs named after the most famous mountain in Shandong. Born in Shandong province in 1951, Lu In fact, according to NetEase Finance, it was graduated from the elite Shanghai university during the Taishan Club’s inaugural meeting – Fudan. His first job was as a technician with hosted by Lu in Shandong – that the idea of the Shandong Weifang Diesel Engine Factory. setting up a non-SOE bank was hatched and the proposal was thereafter sent to Zhu Getting started Rongji. The result was the establishment of Lu left the state sector to become an China Minsheng Bank in 1996. entrepreneur and set up China Oceanwide. Initially it focused on education and training, Minsheng takeover? but when the government initiated housing Oceanwide was one of the 59 private sector reform in 1988, Lu moved into real estate. -

Memory Lane and a Look Down the Road: China Progressing in NAND but Hurdles Remain
21 July 2019 | 12:06PM EDT Made in the USA or China Memory lane and a look down the road: China progressing in NAND but hurdles remain Mark Delaney, CFA +1(212)357-0535 | [email protected] Goldman Sachs & Co. LLC Allen Chang +852-2978-2930 | [email protected] Goldman Sachs (Asia) L.L.C. We believe that China’s efforts to enter the global DRAM and NAND markets merit a Daiki Takayama +81(3)6437-9870 | deeper dive into how the memory industries have evolved over time, what impact [email protected] Goldman Sachs Japan Co., Ltd. China’s entry into other commodity tech industries (such as LEDs and solar) has had Toshiya Hari on fundamentals, where we believe the leading China-based memory companies +1(646)446-1759 | [email protected] Goldman Sachs & Co. LLC stand at present with their efforts to enter the market (and the challenges that still Satoru Ogawa +81(3)6437-4061 | exist for entering the market — with GlobalFoundries as an example that [email protected] leading-edge semi production is difficult even for well-funded efforts), and what we Goldman Sachs Japan Co., Ltd. Alexander Duval believe all this means for the stocks of the established memory, drive, and semi +44(20)7552-2995 | [email protected] equipment companies. Goldman Sachs International Timothy Sweetnam, CFA With over $150 bn of semiconductors shipped to China in 2018, per the +1(212)357-7956 | [email protected] Semiconductor Industry Association (SIA), and China domestic semi firms having Goldman Sachs & Co. -

Corporate Profile
Public Listing: Hong Kong Stock Exchange main board (HK: 03396) CORPORATE PROFILE Overview Founded in 1984, Legend Holdings is a leading diversified investment holding group. Headquartered in Beijing, China and listed on the Hong Kong Stock Exchange, the Company has built an innovative ‘two-wheel-drive’ business model which combines both strategic and financial investments. Under the Chairmanship of the Company’s Founder, Mr Liu Chuanzhi, Legend Holdings has grown over the past 33 years into a globally respected, trusted and influential investment group. It has a track record of cultivating a number of leading companies across various industries, both in China and overseas. Strategic Investments Legend Holdings is committed to generating long-term value Support includes stewardship, with an emphasis on compliant creation through its strategic investments. The company aims governance, risk control and supervision. It also includes to invest in and develop a diverse global portfolio of large-scale, leveraging Legend Holdings’ broad international experience industry-leading companies that have sustainable and stable and deep understanding of global markets to offer advice long-term growth potential. It does this through a consistent and guidance, particularly in terms of international expansion approach that involves taking a controlling shareholding position strategies. The company is also committed to providing in order to provide long-term orientated value-added services. financial support to its portfolio companies to support growth plans and to assure corporate stability and resilience. The company does not seek to involve itself in the daily operations of its portfolio companies. Instead, Legend Holdings The company’s strategic investments are primarily targeted at aims to act primarily as a highly supportive shareholder four different target industry segments: through taking an active role on the Board of Directors to Financial Services. -

Flora and Mary Beard Travel to China to Teach in the Peking Area. Flora Is 45 Years Old and Mary Is 32
1914 August -Flora and Mary Beard travel to China to teach in the Peking area. Flora is 45 years old and Mary is 32. Rise of Japanese power in China (through 1918) WWI begins Panama Canal opens Ernest Shackleton begins his Antarctic expedition and does not return until 1917. Willard is living in Foochow, China while Ellen and the children remain in the U.S. and live in Putnam, CT Willard is 49 years old, Ellen- 46, Phebe- 19, Gould- 18, Geraldine- 16, Dorothy- 13, Marjorie- 8, Kathleen- 6. 50th Wedding Anniversary invitation for Oliver Gould and Nancy Maria Beard. [From the collection of Virginia Beard Van Andel.] Oliver Gould Beard and Nancy Maria Nichols 50th Wedding anniversary 1914 [Photos from the collection of John and Nancy Butte.] ***** [This letter dated March 15, 1914 was written from Foochow, China by Willard to his 8 year old daughter, Marjorie. He tells about a Chinese family that lost their 2 daughters to a sudden illness and how Mr. and Mrs. Christian has to be quarantined in Willard’s house because of it. He will have a Mrs. and Miss Pitcher as boarders in his mountain house this summer. Letter donated to Yale by family in 2006.] American Board of Commissioners for Foreign Missions Foochow College President‟s Office Foochow, China March 15th 1914. Dear- to whom shall I address this- nothing came from Putnam this last week-let me see whose turn it is to have the letter according to my correspondence register.- it‟s Marjorie‟s turn so here it goes.