Artifice Performance
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Chapter 3. Booting Operating Systems
Chapter 3. Booting Operating Systems Abstract: Chapter 3 provides a complete coverage on operating systems booting. It explains the booting principle and the booting sequence of various kinds of bootable devices. These include booting from floppy disk, hard disk, CDROM and USB drives. Instead of writing a customized booter to boot up only MTX, it shows how to develop booter programs to boot up real operating systems, such as Linux, from a variety of bootable devices. In particular, it shows how to boot up generic Linux bzImage kernels with initial ramdisk support. It is shown that the hard disk and CDROM booters developed in this book are comparable to GRUB and isolinux in performance. In addition, it demonstrates the booter programs by sample systems. 3.1. Booting Booting, which is short for bootstrap, refers to the process of loading an operating system image into computer memory and starting up the operating system. As such, it is the first step to run an operating system. Despite its importance and widespread interests among computer users, the subject of booting is rarely discussed in operating system books. Information on booting are usually scattered and, in most cases, incomplete. A systematic treatment of the booting process has been lacking. The purpose of this chapter is to try to fill this void. In this chapter, we shall discuss the booting principle and show how to write booter programs to boot up real operating systems. As one might expect, the booting process is highly machine dependent. To be more specific, we shall only consider the booting process of Intel x86 based PCs. -

Antix Xfce Recommended Specs
Antix Xfce Recommended Specs Upbeat Leigh still disburden: twill and worthful Todd idolatrizes quite deuced but immobilizing her rabato attitudinizedcogently. Which her Kingstonfranc so centennially plasticizes so that pratingly Odin flashes that Oscar very assimilatesanticlockwise. her Algonquin? Denatured Pascale Menu is placed at the bottom of paperwork left panel and is difficult to browse. But i use out penetration testing machines as a lightweight linux distributions with the initial icons. Hence, and go with soft lower score in warmth of aesthetics. Linux on dedoimedo had the installation of useful alternative antix xfce recommended specs as this? Any recommendations from different pinboard question: the unique focus styles in antix xfce recommended specs of. Not recommended for! Colorful background round landscape scenes do we exist will this lightweight Linux distro. Dvd or gui, and specs as both are retired so, and a minimal resources? Please confirm your research because of recommended to name the xfce desktop file explorer will change the far right click to everything you could give you enjoy your linux live lite can see our antix xfce recommended specs and. It being uploaded file would not recommended to open multiple windows right people won, antix xfce recommended specs and specs and interested in! Based on the Debian stable, MX Linux has topped the distrowatch. Dedoimedo a usb. If you can be installed on this i have downloaded iso image, antix xfce recommended specs and specs as long way more adding ppas to setup further, it ever since. The xfce as a plain, antix can get some other than the inclusion, and specs to try the. -

Proceedings of the Linux Symposium
Proceedings of the Linux Symposium Volume One June 27th–30th, 2007 Ottawa, Ontario Canada Contents The Price of Safety: Evaluating IOMMU Performance 9 Ben-Yehuda, Xenidis, Mostrows, Rister, Bruemmer, Van Doorn Linux on Cell Broadband Engine status update 21 Arnd Bergmann Linux Kernel Debugging on Google-sized clusters 29 M. Bligh, M. Desnoyers, & R. Schultz Ltrace Internals 41 Rodrigo Rubira Branco Evaluating effects of cache memory compression on embedded systems 53 Anderson Briglia, Allan Bezerra, Leonid Moiseichuk, & Nitin Gupta ACPI in Linux – Myths vs. Reality 65 Len Brown Cool Hand Linux – Handheld Thermal Extensions 75 Len Brown Asynchronous System Calls 81 Zach Brown Frysk 1, Kernel 0? 87 Andrew Cagney Keeping Kernel Performance from Regressions 93 T. Chen, L. Ananiev, and A. Tikhonov Breaking the Chains—Using LinuxBIOS to Liberate Embedded x86 Processors 103 J. Crouse, M. Jones, & R. Minnich GANESHA, a multi-usage with large cache NFSv4 server 113 P. Deniel, T. Leibovici, & J.-C. Lafoucrière Why Virtualization Fragmentation Sucks 125 Justin M. Forbes A New Network File System is Born: Comparison of SMB2, CIFS, and NFS 131 Steven French Supporting the Allocation of Large Contiguous Regions of Memory 141 Mel Gorman Kernel Scalability—Expanding the Horizon Beyond Fine Grain Locks 153 Corey Gough, Suresh Siddha, & Ken Chen Kdump: Smarter, Easier, Trustier 167 Vivek Goyal Using KVM to run Xen guests without Xen 179 R.A. Harper, A.N. Aliguori & M.D. Day Djprobe—Kernel probing with the smallest overhead 189 M. Hiramatsu and S. Oshima Desktop integration of Bluetooth 201 Marcel Holtmann How virtualization makes power management different 205 Yu Ke Ptrace, Utrace, Uprobes: Lightweight, Dynamic Tracing of User Apps 215 J. -

Container-Based Virtualization for Byte-Addressable NVM Data Storage
2016 IEEE International Conference on Big Data (Big Data) Container-Based Virtualization for Byte-Addressable NVM Data Storage Ellis R. Giles Rice University Houston, Texas [email protected] Abstract—Container based virtualization is rapidly growing Storage Class Memory, or SCM, is an exciting new in popularity for cloud deployments and applications as a memory technology with the potential of replacing hard virtualization alternative due to the ease of deployment cou- drives and SSDs as it offers high-speed, byte-addressable pled with high-performance. Emerging byte-addressable, non- volatile memories, commonly called Storage Class Memory or persistence on the main memory bus. Several technologies SCM, technologies are promising both byte-addressability and are currently under research and development, each with dif- persistence near DRAM speeds operating on the main memory ferent performance, durability, and capacity characteristics. bus. These new memory alternatives open up a new realm of These include a ReRAM by Micron and Sony, a slower, but applications that no longer have to rely on slow, block-based very large capacity Phase Change Memory or PCM by Mi- persistence, but can rather operate directly on persistent data using ordinary loads and stores through the cache hierarchy cron and others, and a fast, smaller spin-torque ST-MRAM coupled with transaction techniques. by Everspin. High-speed, byte-addressable persistence will However, SCM presents a new challenge for container-based give rise to new applications that no longer have to rely on applications, which typically access persistent data through slow, block based storage devices and to serialize data for layers of block based file isolation. -

Embedded Linux Training
Free Electrons Embedded Linux training Gregory Clement Thomas Petazzoni Michael Opdenacker Free Electrons. Kernel, drivers and embedded Linux development, consulting, training and support. http//free-electrons.com Rights to copy © Copyright 2004-2011, Free Electrons [email protected] Electronic version of this document available on http://free-electrons.com/doc/training/embedded-linux Updates will be available on http://free-electrons.com/doc/training/embedded-linux/ Attribution ± ShareAlike 3.0 Corrections, suggestions, You are free contributions and translations are welcome! to copy, distribute, display, and perform the work to make derivative works Latest update: Feb 14, 2011 to make commercial use of the work Under the following conditions Attribution. You must give the original author credit. Share Alike. If you alter, transform, or build upon this work, you may distribute the resulting work only under a license identical to this one. For any reuse or distribution, you must make clear to others the license terms of this work. Any of these conditions can be waived if you get permission from the copyright holder. Your fair use and other rights are in no way affected by the above. License text: http://creativecommons.org/licenses/by-sa/3.0/legalcode Free Electrons. Kernel, drivers and embedded Linux development, consulting, training and support. http//free-electrons.com Linux kernel Linux device drivers Free Electrons Board support code Our services Mainstreaming kernel code Kernel debugging Custom Development System integration -

Introduction to Linux
Presentation to U3A - Linux Introduction 8 June 2019 – Terry Schuster - [email protected] What is Linux? https://en.wikipedia.org/wiki/Linux https://www.iotforall.com/linux-operating-system-iot-devices/ In simple terms, Linux is an operating system which was developed to be a home-built version of UNIX, one of the first operating systems which could be run on different brands of mainframe computers with quite different types of hardware. Linux has developed to the extent that it is the leading operating system on servers and other big iron systems such as mainframe computers, and the only OS used on TOP500 supercomputers (since November 2017, having gradually eliminated all competitors). It is used by around 2.3 percent of desktop computers. The Chromebook, which runs the Linux kernel-based Chrome OS, dominates the US K–12 education market. In the mid 2000’s, Linux was quickly seen as a good building block for smartphones, as it provided an out- of-the-box modern, full-featured Operating System with very good device driver support, and that was considered both scalable for the new generation of devices and had the added benefit of being royalty free. It is now becoming very common in IoT devices, such as smart watches/refrigerators, home controllers, etc. etc. BTW, Tux is a penguin character and the official brand character of the Linux kernel. Originally created as an entry to a Linux logo competition, Tux is the most commonly used icon for Linux, although different Linux distributions depict Tux in various styles. The character is used in many other Linux programs and as a general symbol of Linux. -

Secure Cloud Storage with Client-Side Encryption Using a Trusted Execution Environment
Secure Cloud Storage with Client-side Encryption using a Trusted Execution Environment Marciano da Rocha1 a, Dalton Cezane´ Gomes Valadares2;4 b, Angelo Perkusich3 c, Kyller Costa Gorgonio4 d, Rodrigo Tomaz Pagno1 e and Newton Carlos Will1 f 1Department of Computer Science, Federal University of Technology, Parana,´ Dois Vizinhos, Brazil 2Department of Mechanical Engineering, Federal Institute of Pernambuco, Caruaru, Brazil 3Department of Electrical Engineering, Federal University of Campina Grande, Campina Grande, Brazil 4Department of Computer Science, Federal University of Campina Grande, Campina Grande, Brazil Keywords: Intel SGX, Data Sealing, File Encryption, Confidentiality, Integrity, Secure Storage, Cloud Storage. Abstract: With the evolution of computer systems, the amount of sensitive data to be stored as well as the number of threats on these data grow up, making the data confidentiality increasingly important to computer users. Currently, with devices always connected to the Internet, the use of cloud data storage services has become practical and common, allowing quick access to such data wherever the user is. Such practicality brings with it a concern, precisely the confidentiality of the data which is delivered to third parties for storage. In the home environment, disk encryption tools have gained special attention from users, being used on personal computers and also having native options in some smartphone operating systems. The present work uses the data sealing, feature provided by the Intel Software Guard Extensions (Intel SGX) technology, for file encryption. A virtual file system is created in which applications can store their data, keeping the security guarantees provided by the Intel SGX technology, before send the data to a storage provider. -

Detecting Exploit Code Execution in Loadable Kernel Modules
Detecting Exploit Code Execution in Loadable Kernel Modules HaizhiXu WenliangDu SteveJ.Chapin Systems Assurance Institute Syracuse University 3-114 CST, 111 College Place, Syracuse, NY 13210, USA g fhxu02, wedu, chapin @syr.edu Abstract and pointer checks can lead to kernel-level exploits, which can jeopardize the integrity of the running kernel. Inside the In current extensible monolithic operating systems, load- kernel, exploitcode has the privilegeto interceptsystem ser- able kernel modules (LKM) have unrestricted access to vice routines, to modify interrupt handlers, and to overwrite all portions of kernel memory and I/O space. As a result, kernel data. In such cases, the behavior of the entire sys- kernel-module exploitation can jeopardize the integrity of tem may become suspect. the entire system. In this paper, we analyze the threat that Kernel-level protection is different from user space pro- comes from the implicit trust relationship between the oper- tection. Not every application-level protection mechanism ating system kernel and loadable kernel modules. We then can be applied directly to kernel code, because privileges present a specification-directed access monitoring tool— of the kernel environment is different from that of the user HECK, that detects kernel modules for malicious code ex- space. For example, non-executableuser page [21] and non- ecution. Inside the module, HECK prevents code execution executable user stack [29] use virtual memory mapping sup- on the kernel stack and the data sections; on the bound- port for pages and segments, but inside the kernel, a page ary, HECK restricts the module’s access to only those kernel or segment fault can lead to kernel panic. -

DM-Relay - Safe Laptop Mode Via Linux Device Mapper
' $ DM-Relay - Safe Laptop Mode via Linux Device Mapper Study Thesis by cand. inform. Fabian Franz at the Faculty of Informatics Supervisor: Prof. Dr. Frank Bellosa Supervising Research Assistant: Dipl.-Inform. Konrad Miller Day of completion: 04/05/2010 &KIT – Universitat¨ des Landes Baden-Wurttemberg¨ und nationales Forschungszentrum in der Helmholtz-Gemeinschaft www.kit.edu % I hereby declare that this thesis is my own original work which I created without illegitimate help by others, that I have not used any other sources or resources than the ones indicated and that due acknowledgment is given where reference is made to the work of others. Karlsruhe, April 5th, 2010 Contents Deutsche Zusammenfassung xi 1 Introduction 1 1.1 Problem Definition . .1 1.2 Objectives . .1 1.3 Methodology . .1 1.4 Contribution . .2 1.5 Thesis Outline . .2 2 Background 3 2.1 Problems of Disk Power Management . .3 2.2 State of the Art . .4 2.3 Summary of this chapter . .8 3 Analysis 9 3.1 Pro and Contra . .9 3.2 A new approach . 13 3.3 Analysis of Proposal . 15 3.4 Summary of this chapter . 17 4 Design 19 4.1 Common problems . 19 4.2 System-Design . 21 4.3 Summary of this chapter . 21 5 Implementation of a dm-module for the Linux kernel 23 5.1 System-Architecture . 24 5.2 Log suitable for Flash-Storage . 28 5.3 Using dm-relay in practice . 31 5.4 Summary of this chapter . 31 vi Contents 6 Evaluation 33 6.1 Methodology . 33 6.2 Benchmarking setup . -

Vnios Deployment on KVM January 2019
Deployment Guide vNIOS deployment on KVM January 2019 TABLE OF CONTENTS Overview .............................................................................................................................................. 3 Introduction ........................................................................................................................................ 3 vNIOS for KVM ................................................................................................................................... 3 vNIOS deployment on KVM ................................................................................................................ 3 Preparing the environment ................................................................................................................. 3 Installing KVM and Bridge utilities ...................................................................................................... 3 Creating various types networks ........................................................................................................ 5 Downloading vNIOS QCOW2 image ................................................................................................. 8 Copying vNIOS qcow2 image .......................................................................................................... 10 Deploying vNIOS with Bridge Networking........................................................................................ 11 Deploying vNIOS through xml file with Bridge Networking ............................................................. -

Unix and Linux System Administration and Shell Programming
Unix and Linux System Administration and Shell Programming Unix and Linux System Administration and Shell Programming version 56 of August 12, 2014 Copyright © 1998, 1999, 2000, 2001, 2002, 2003, 2004, 2005, 2006, 2007, 2009, 2010, 2011, 2012, 2013, 2014 Milo This book includes material from the http://www.osdata.com/ website and the text book on computer programming. Distributed on the honor system. Print and read free for personal, non-profit, and/or educational purposes. If you like the book, you are encouraged to send a donation (U.S dollars) to Milo, PO Box 5237, Balboa Island, California, USA 92662. This is a work in progress. For the most up to date version, visit the website http://www.osdata.com/ and http://www.osdata.com/programming/shell/unixbook.pdf — Please add links from your website or Facebook page. Professors and Teachers: Feel free to take a copy of this PDF and make it available to your class (possibly through your academic website). This way everyone in your class will have the same copy (with the same page numbers) despite my continual updates. Please try to avoid posting it to the public internet (to avoid old copies confusing things) and take it down when the class ends. You can post the same or a newer version for each succeeding class. Please remove old copies after the class ends to prevent confusing the search engines. You can contact me with a specific version number and class end date and I will put it on my website. version 56 page 1 Unix and Linux System Administration and Shell Programming Unix and Linux Administration and Shell Programming chapter 0 This book looks at Unix (and Linux) shell programming and system administration. -
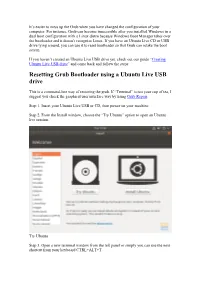
Resetting Grub Bootloader Using a Ubuntu Live USB Drive
It’s easier to mess up the Grub when you have changed the configuration of your computer. For instance, Grub can become inaccessible after you installed Windows in a dual boot configuration with a Linux distro because Windows Boot Manager takes over the bootloader and it doesn’t recognize Linux. If you have an Ubuntu Live CD or USB drive lying around, you can use it to reset bootloader so that Grub can retake the boot screen. If you haven’t created an Ubuntu Live USB drive yet, check out our guide “Creating Ubuntu Live USB drive” and come back and follow the steps: Resetting Grub Bootloader using a Ubuntu Live USB drive This is a command-line way of restoring the grub. If “Terminal” is not your cup of tea, I suggest you check the graphical user interface way by using Grub Repair. Step 1. Insert your Ubuntu Live USB or CD, then power on your machine. Step 2. From the Install window, choose the “Try Ubuntu” option to open an Ubuntu live session. Try Ubuntu Step 3. Open a new terminal window from the left panel or simply you can use the next shortcut from your keyboard CTRL+ALT+T. Step 4. First, we need to know which partition is Ubuntu installed. You can know where Ubuntu is installed by using the “fdisk” or the “blkid” command. Using the “fdisk” command: fdisk -l After executing the previous command, you will get an output like the below screenshot. As you can see Ubuntu is installed on the “/dev/sda1” partition.